Using the Dashboard
Whenever you login to SnapAttack, the first page you'll see is the dashboard. This page provides a live overview of the content in the platform, allowing you to understand the content health and prioritize your backlog.
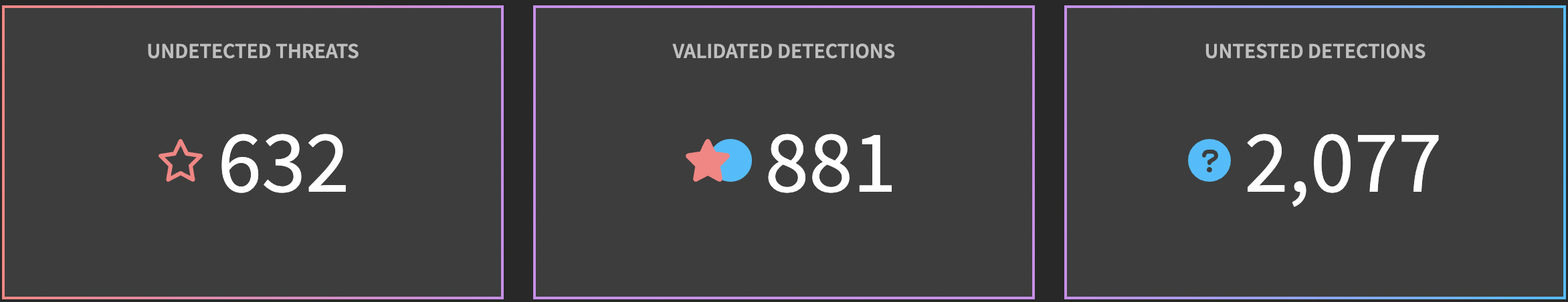
Validation Status
In this first section, we see our red and blue team inputs. SnapAttack allows red teamers to capture and label threats. When they label an threat, it appears in the system as a  red star. If there is no corresponding detection, this
red star. If there is no corresponding detection, this  red star appears hollow, and is classified as an undetected threat. These undetected threats signify weak points or gaps in detection, which become the blue team's backlog. The blue teamer would follow the workflow to create and test a detection to alert on this threat.
red star appears hollow, and is classified as an undetected threat. These undetected threats signify weak points or gaps in detection, which become the blue team's backlog. The blue teamer would follow the workflow to create and test a detection to alert on this threat.
On the other side, SnapAttack allows blue teamers to create and test detections. Detection hits appear in the system as  blue circles. If a detection has never been triggered before, it appears here as an untested detection. Testing detections against true positive threats is critical, otherwise you won't have confidence that a detection will trigger when up against a real threat. These untested detections represent the red team's backlog. The red teamer would follow the workflow to replicate a threat and label an attack that will exercise this detection.
blue circles. If a detection has never been triggered before, it appears here as an untested detection. Testing detections against true positive threats is critical, otherwise you won't have confidence that a detection will trigger when up against a real threat. These untested detections represent the red team's backlog. The red teamer would follow the workflow to replicate a threat and label an attack that will exercise this detection.
As red and blue teams work together as a purple team, their results come together in the middle section as validated detections. This is when we have a true positive, labeled threat that triggers a detection. We can confidently deploy these detections to our SIEM, EDR, or other security tools to gain immediate coverage, and we can test them in production with automated attack simulations.
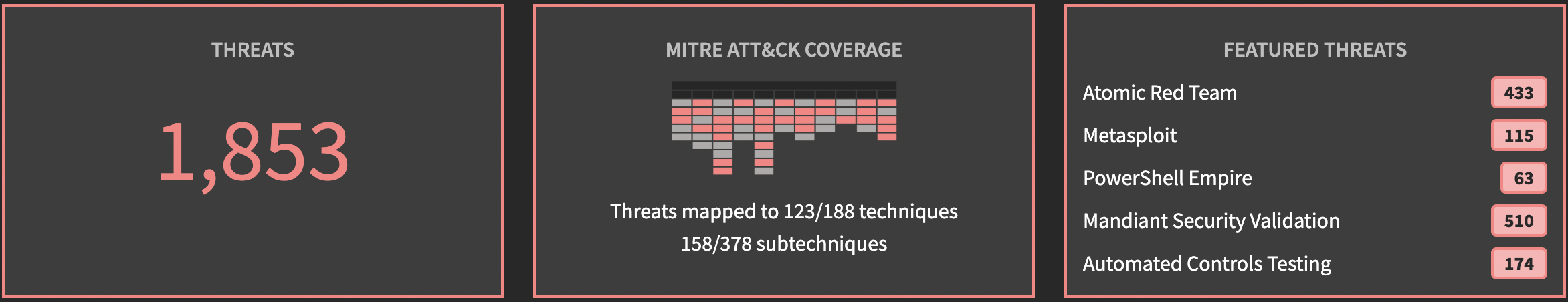
Threats
We can see the number of threats put in by the red team, how many different techniques have been exercised in the context of the MITRE ATT&CK framework, and featured threats highlighting some of the different offensive tools and frameworks.
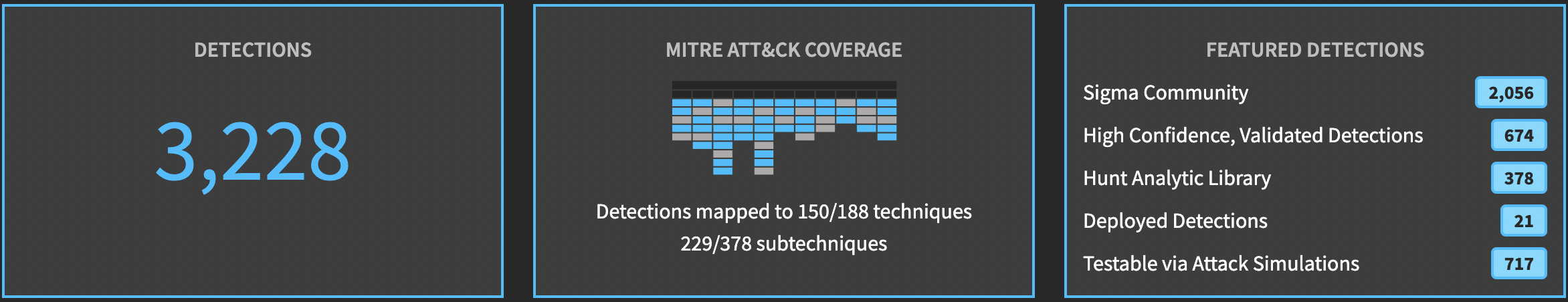
Detections
Similarly, we also have the number of detections put in by the blue team, the detection coverage in terms of the ATT&CK framework, and categories or sources of different detections.