Frequently Asked Questions (FAQ)
General
I'm new to the platform. Where do you suggest I start after logging in?
We generally suggest using the search bar to kick off your investigation. Note that there are pre-populated trending terms available to you, but you can run any key word you like.
Once you have run a search, you can apply filters (available on the left-hand side of every page) to help further tailor your search results (the three most actionable filters are Detection Confidence, Validation Status, and Supported Language).
If you need to run another search, the search bar is available in the upper right-hand corner of the page.
Note: If you have a specific use case in mind (detection engineering or threat hunting, for example), you can jump to the appropriate tab upon your first log-in (Detect – Detection Engineering, Hunt – Threat Hunting, Sandbox – Red Teaming, etc.).
What does "Severity" mean?
Severity level references the impact of the threat on your environment.
What does "Detection Confidence" mean?
Detection confidence is calculated based on the number of expected or actual hits the detection will have in your environment. SnapAttack uses an algorithm to calculate the confidence level unique to your environment. Otherwise, the confidence level that is presented is a global average.
What does "Validation Status" mean?
We track the relationship between labeled attacks and detection hits as validation status. Our attack library is used to validate detection content since there is a connected relationship between threat activity and behavioral detections that trigger on them.
What about "Supported Language"?
Detections can be filtered by compatible language, which ensures that the resulting detection content is most relevant to your tooling. Some examples are CrowdStrike, Chronicle EDR, or Splunk.
Where do I find my API key?
Your API keys are available under Settings. Note that they are tied to your user account. You may consider creating a service account user if using API keys for integrations.
Does it matter which scope I assign to my API key?
Yes! There are currently four types of scopes that you can assign to your key:
- Detection Deployment: You would use this scope when you are deploying detection rules to your environment through your configured integrations (SentinelOne, for example).
- Attack Simulations: You would use this scope to perform automated attack simulations of SnapAttack threats in your own environment using the SnapAttack validation agent.
- Local Threat Capture: You would use this scope to utilize SnapAttack's CapAttack Agent to capture logs, videos, and keystrokes from threats you run in your own environment
- REST: You would use the REST API to interact with SnapAttack via API instead of through the GUI. API documentation is available at https://app.snapattack.com/api/docs.
Where can I add/remove users from my org?
If you have admin privileges, you can control who is part of your organization's user group by clicking on "User Management". Either click "Add user" in the right-hand corner or "Remove user" after clicking on the gear icon next to the user you would like to remove.
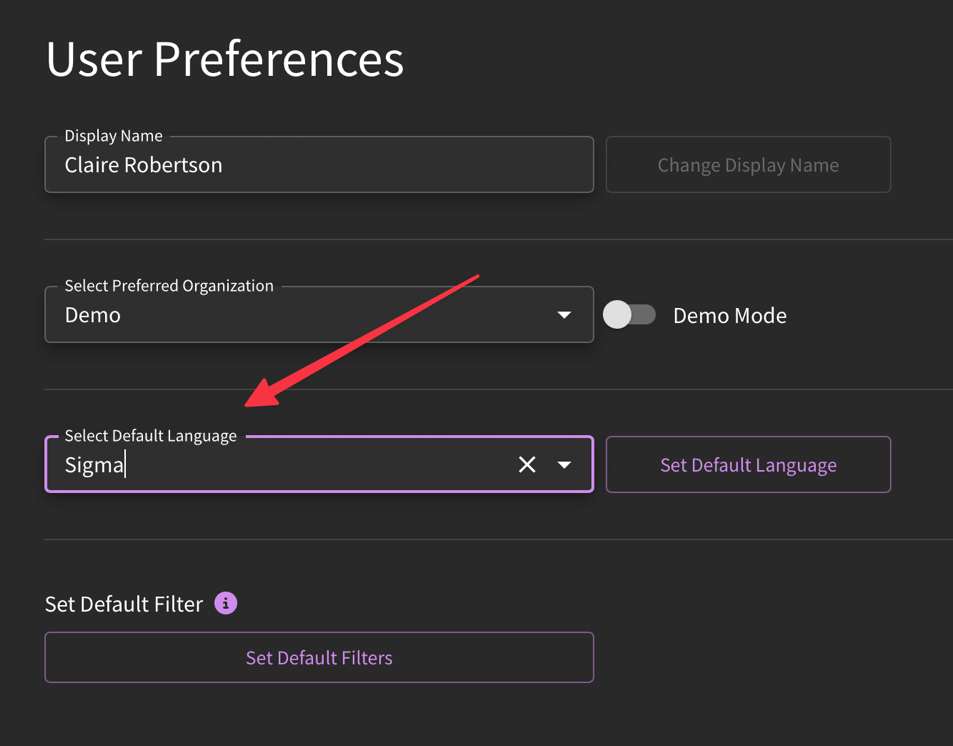
My team uses CrowdStrike. Can I set up a default detection language?
You sure can! Click on "Preferences" and then choose your detection language from the "Default Language" drop-down menu. The example shown is Sigma, but you can select from the available list based on your specific tooling.
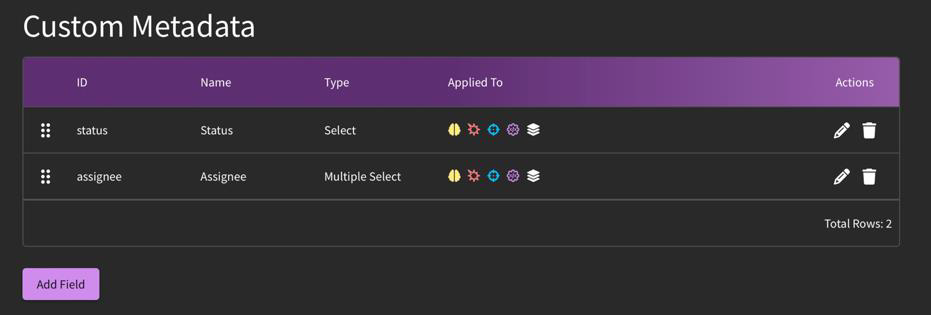
What is Metadata?
Located under "Settings", users can create custom fields to add notations to their content using Metadata. This information is private to your organization. Some major use cases for custom metadata are:
- Jira-like project management (e.g., Assignee: Adam, Bob, Charlie)
- Internal tracking (e.g., GUID: 62170c2b-34d2-434d-9fc9-b4448675bdc3)
- Workflow state (e.g., Backlog, In Progress, In Review, Completed)
- Related resources/note taking (e.g., git links, further research, etc.)
- Custom tags
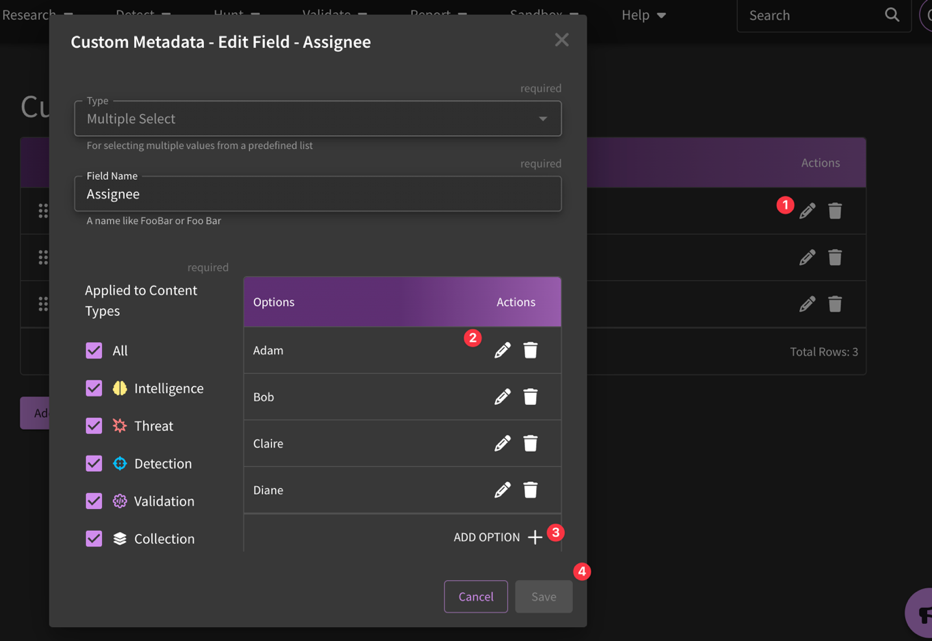
How can I edit my metadata fields?
Under Metadata in Settings, click into whichever field you would like to edit by selecting the pencil icon. From there, you can either edit existing options (step 2) or add an additional option (step 3). Then, click "Save".
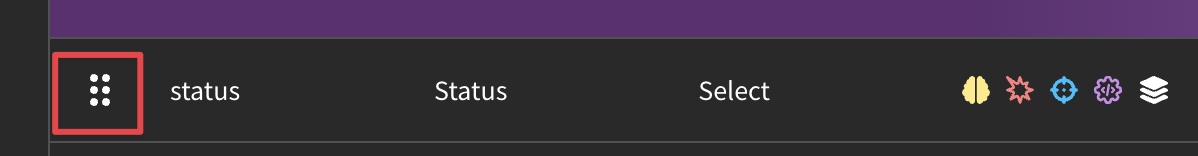
You can also rearrange the order of tags by clicking and dragging on the handle. This will affect the order in which your fields appear on the content pages.
Where can I go to submit a feature request or bug?
Click on the megaphone icon ![]() to submit a feature/content request or identified bug. Where possible, we recommend including a quick video or screenshot of the matter to provide as much detail as possible for our team.
to submit a feature/content request or identified bug. Where possible, we recommend including a quick video or screenshot of the matter to provide as much detail as possible for our team.
Do you have documentation on how to set up my EDR/SIEM integration?
SnapAttack supports various EDR/SIEM tools. Please reach out to your SnapAttack Customer Success Manager for specific documentation through email, Slack, or Teams.
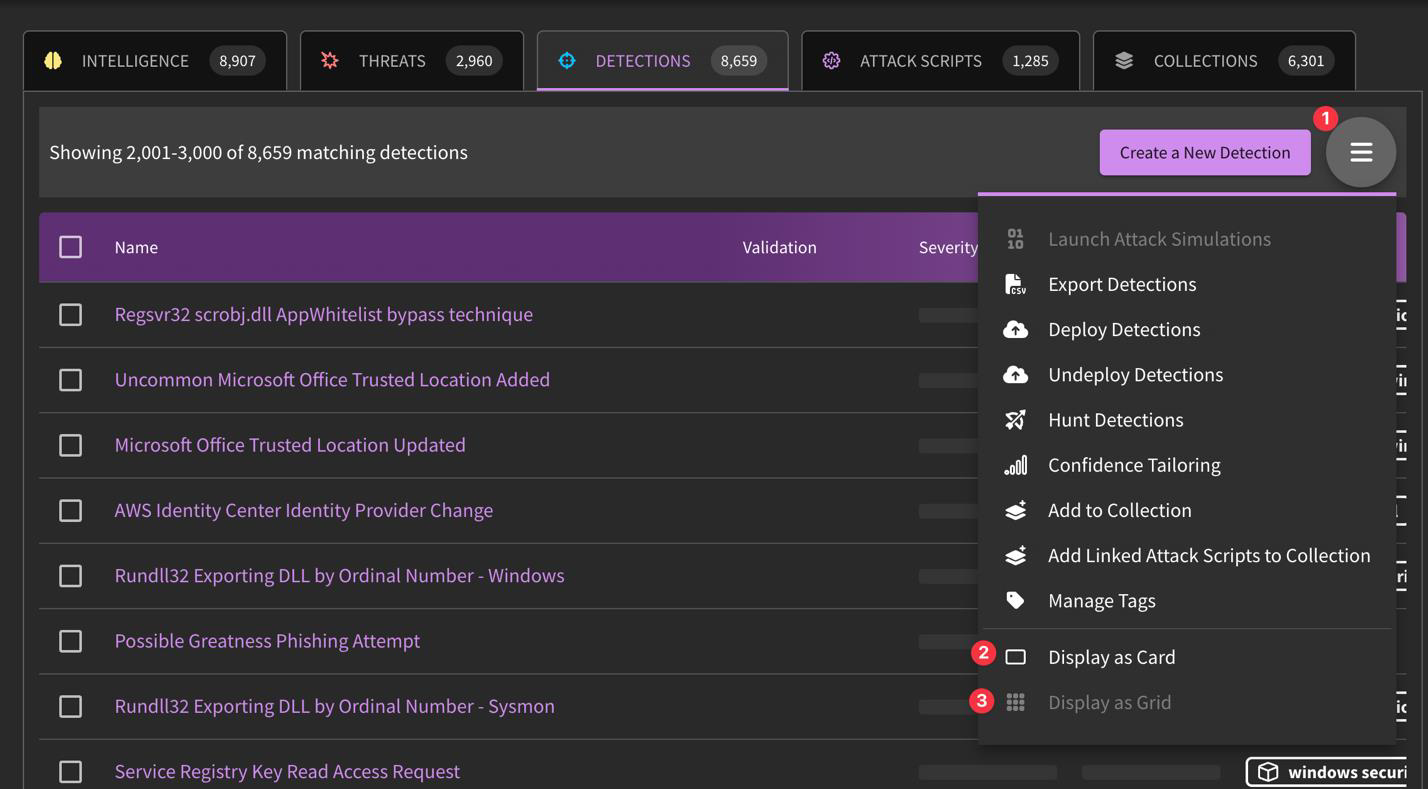
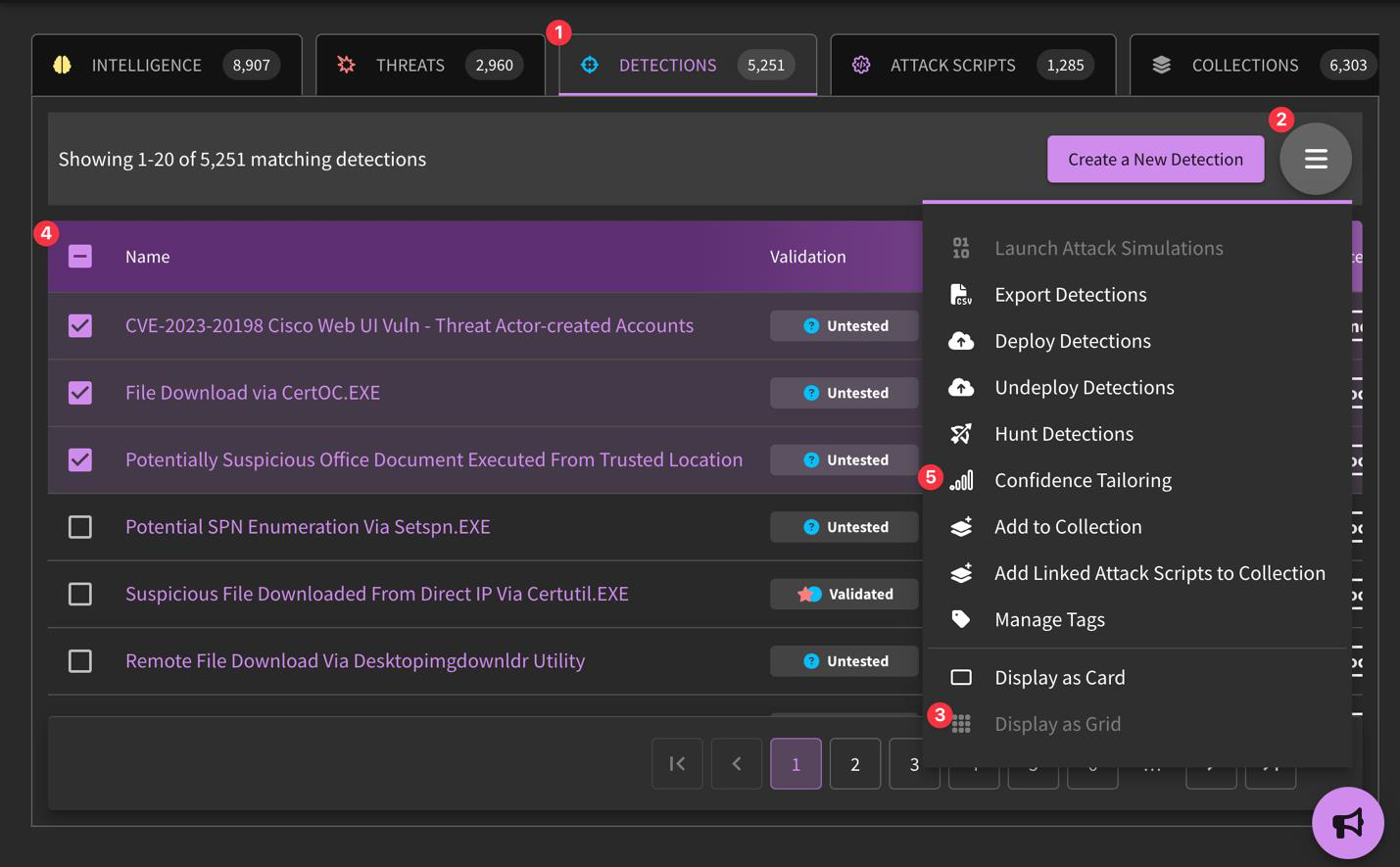
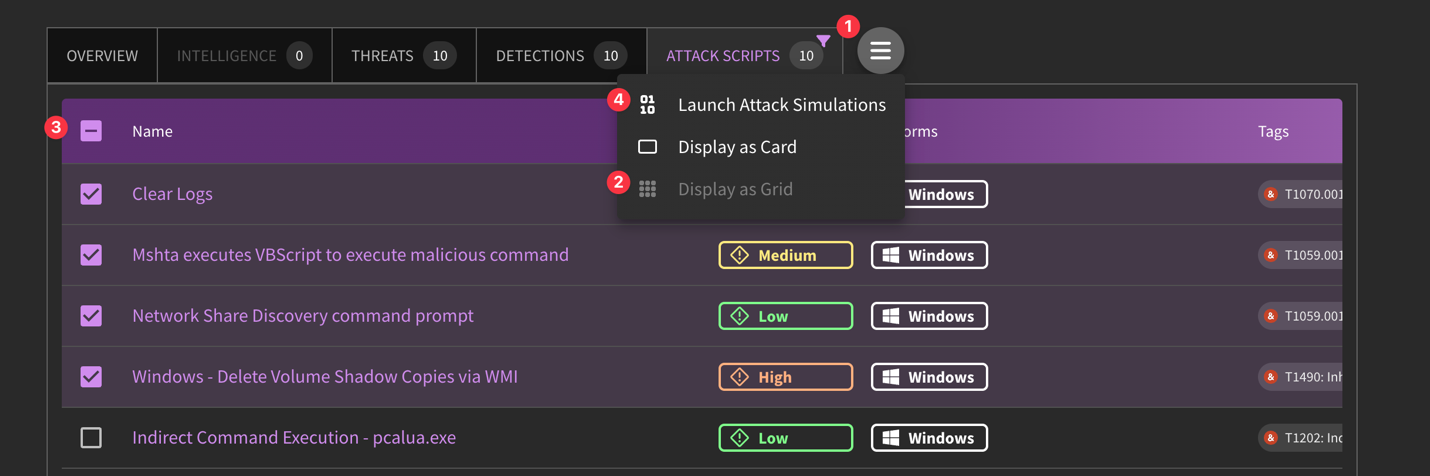
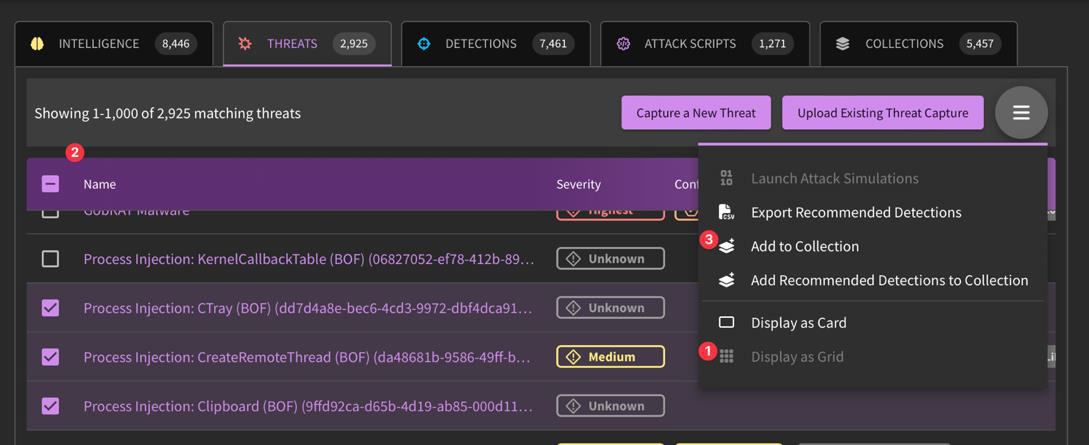
Why would I use "Grid View" over "Card View" (as listed in the hamburger menu)?
You can access content in a more data-dense format when selecting the "Grid View". This allows you to interact with content "in bulk" whether to Deploy, Hunt, Confidence Tailor, Add to Collection, or otherwise.
Research
Can I create my own intelligence products?
Absolutely! Click on "Create New Intelligence". From there, you can upload a resource (PDF or link) to pre-populate your form or manually enter in the information you'd like included. Don't forget to click "Publish"!
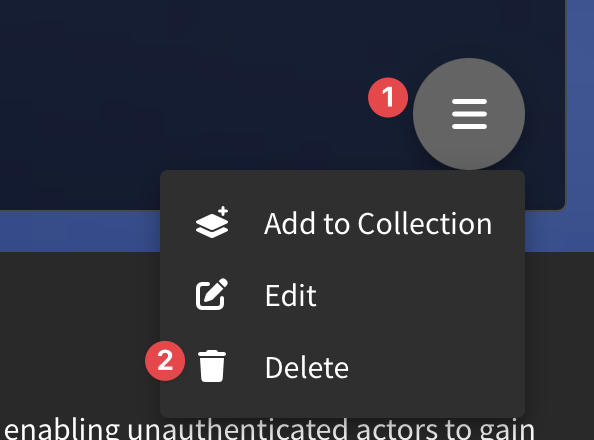
What if I need to edit my report or delete it altogether after it's published?
If you are the owner of the report, click into the report you'd like to edit/delete. Then, select the desired action from the hamburger menu in the right-hand corner.
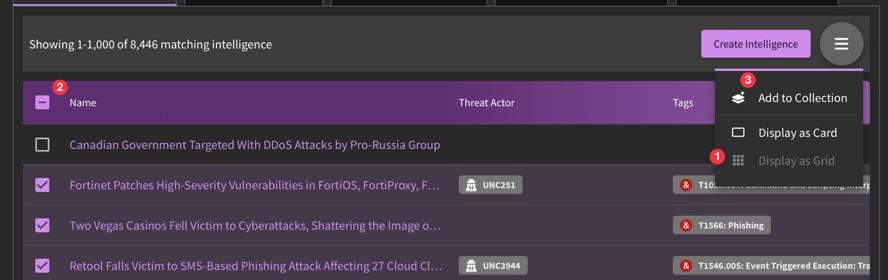
How do I add intelligence products to one of my collections?
There are a few ways to do this:
- To bulk add intel reports to a collection, click on the hamburger menu in the right-hand corner of the Intelligence tab and select "Grid View". Select the intel reports you would like to include and select "Add to Collection". From there, you will need to specify your desired collection or create a new one. Press "Save"!
OR
- To add reports individually, click on the intel report you would like to add. Select "Add to Collection" from the hamburger menu, then search for the collection you would like to add to.
What do SnapAttack customers use Collections for?
Collections can be used for a variety of reasons: attack/detection planning, research, sprint cycles, and more! It really depends on the use case, but the concepts are the same: provide a space for teams to consolidate the work they are doing for thorough information sharing.
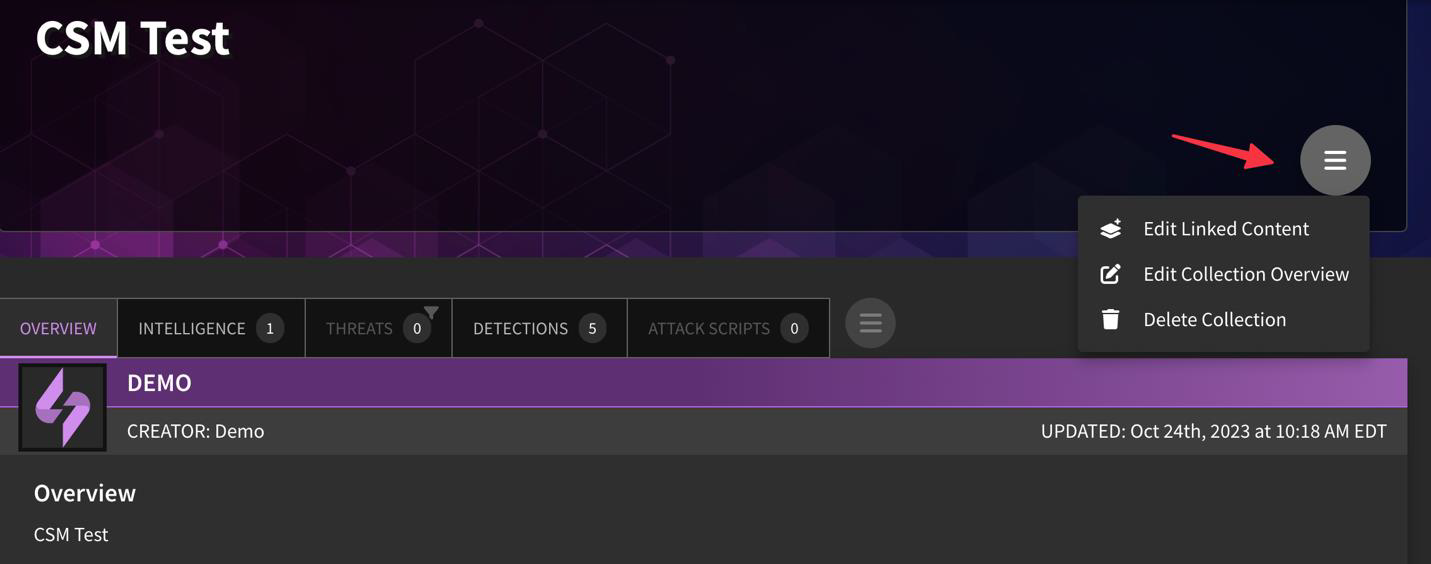
Can I edit/delete my Collection?
Yes! Click on the hamburger menu on either the Collection "Overview" page to either edit the linked content (intelligence, threats, detections, or attack scripts), overall description, or delete entirely.
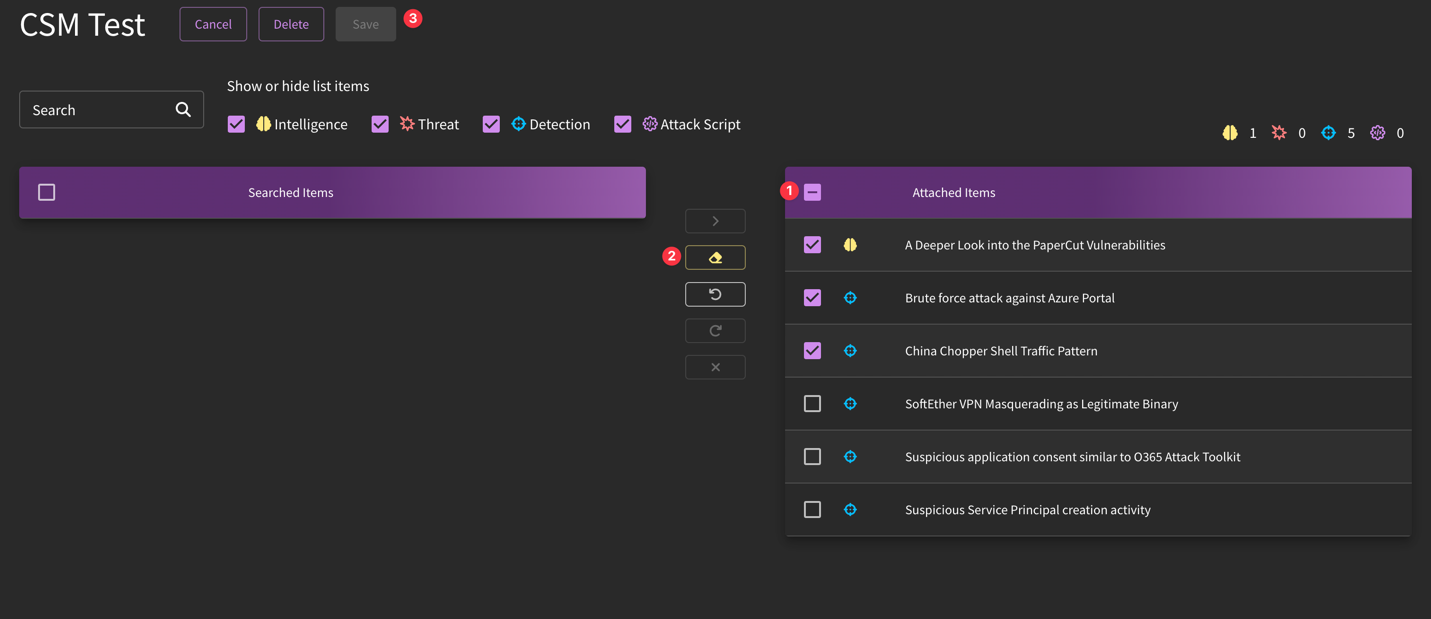
If you would like to alter the linked content available in the collection, simply click Edit Linked Content, then select the items that you would like to edit, click on the action you'd like to perform (in this case, "Remove Attached Items"), then press "Save".
Detect
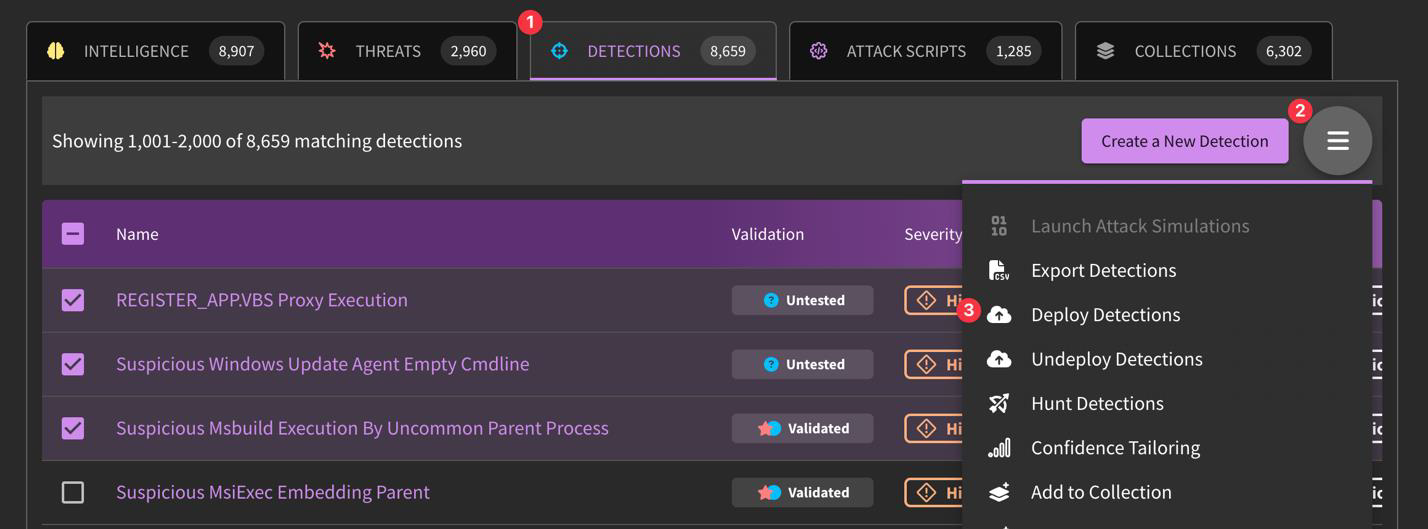
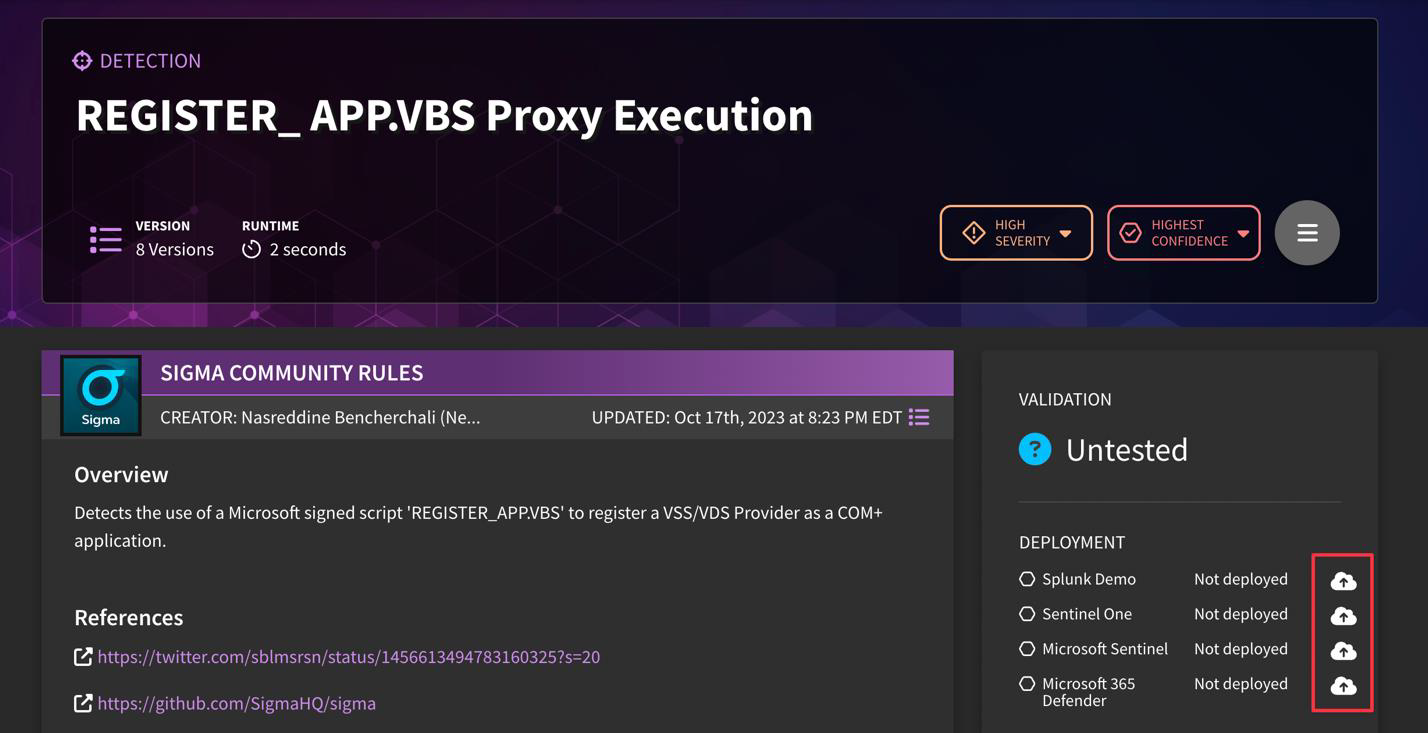
How do I deploy a detection? What about undeploy?
The easiest way to deploy a detection is by going to "Detect", then selecting detections you would like to deploy to your tooling, then clicking "Deploy Detections" within the Hamburger menu. To undeploy, simply perform the same action, but select "Undeploy Detections" instead.
Alternatively, you can deploy compatible detections individually by selecting your relevant tooling by clicking on the cloud icon.
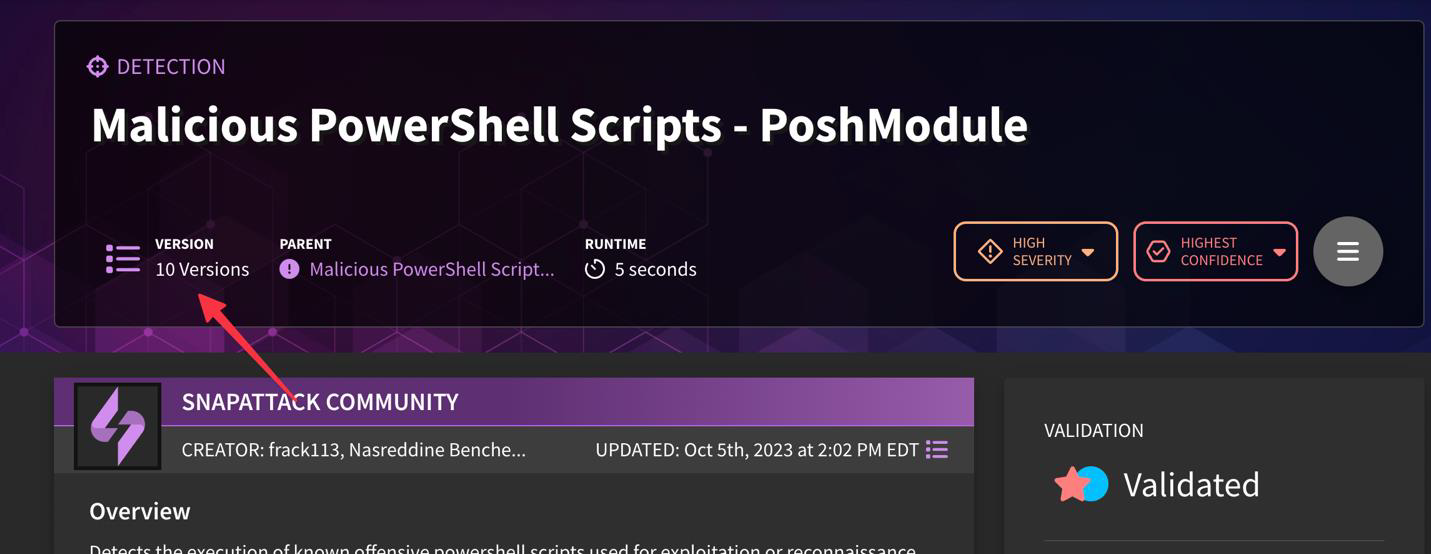
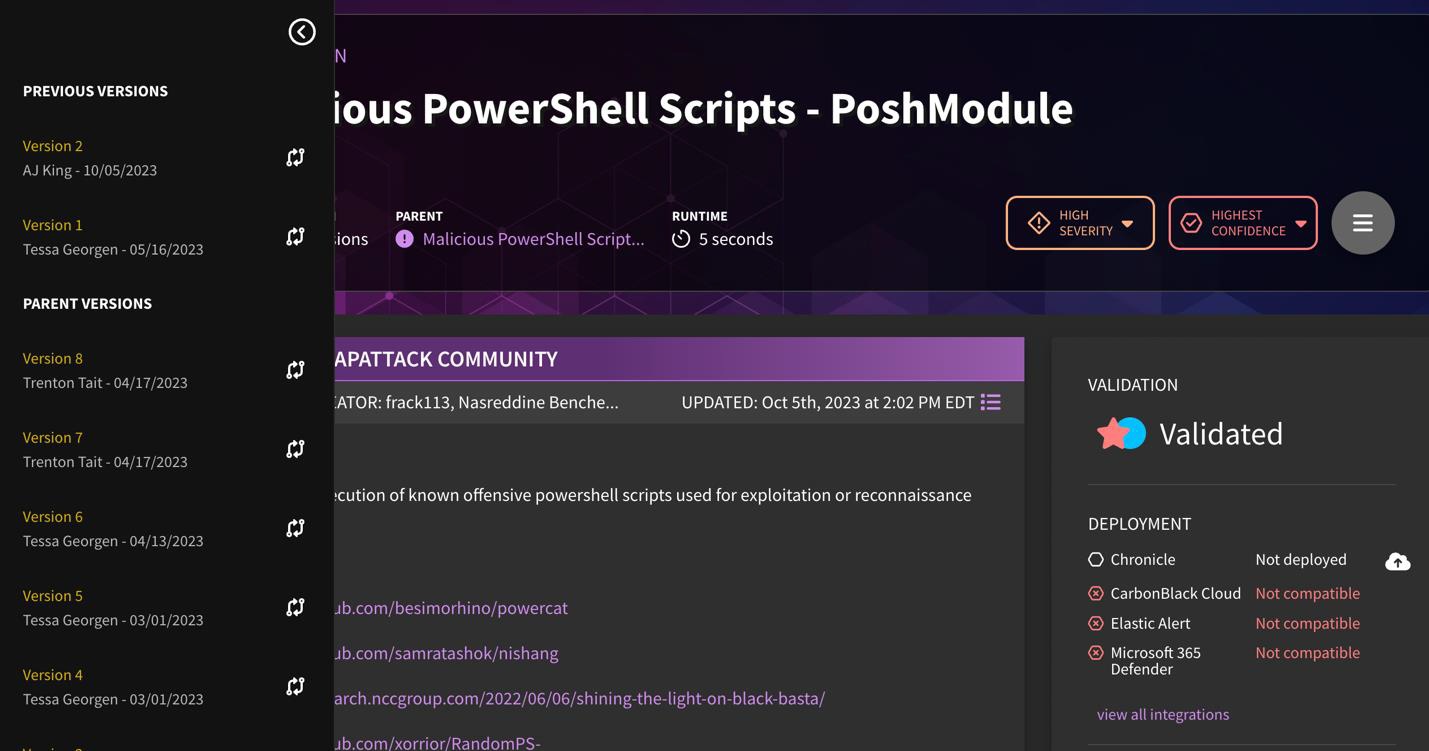
Can you track versions of detections in the platform?
Yes, detection version history and lineage has been more clearly exposed in the application, with the version number being displayed in the hero banner. If a detection was cloned from another detection in the library, that linkage is now displayed. This helps users determine if a parent detection's logic has been updated, and if they want to bring that over to their forked version. Users can use the built-in diff viewer to show changes in the detection logic across versions.
Note that the author and date of versioning is taken into account on the left-hand panel.
What operating systems/platforms do we have logs for?
SnapAttack currently has log sources originating from Windows and Linux hosts, network detections such as Zeek data, and Cloud logs. Additional log sources are constantly being added.
Where and how often do you get your CVE content from?
We sync vulnerability data from the National Vulnerability Database (NVD) and CISA every 6 hours. Generally speaking, we focus on critical and high risk vulnerabilities, though occasionally others will be imported as well.
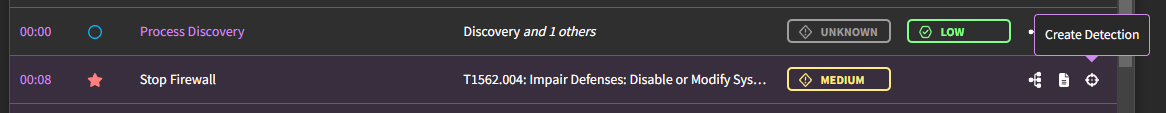
What do the symbols under detections mean?
Validated detections are true positive detection results. When a detection hit (blue circle) matches a labeled attack (red star), the icons are filled in to denote that the detection gaps are closed.
Detection gaps are likely false positive detection results that need additional review. When a detection hit (blue circle) has a nearby labeled attack (red star), but they don't match on any validation criteria, the icons are left hollow to denote that a detection gap exists.
Unvalidated detections are false positive detection results. When a detection hit (blue circle) has never had a labeled attack (red star) in close proximity, the blue circle appears hollow. These can be improved by executing and capturing a threat that would trigger the detection.
Untested detections are the red team's backlog (question mark). These are detections that have never triggered a threat in our threat library. These can be improved by executing and capturing a threat that will trigger the detection.
Undetected threats are seen in the platform as hollow red stars. When the threat is detected by a detection, it is seen as a solid red star.
Why can't I edit a detection even though it needs to be corrected or updated?
There are a few reasons behind not being able to edit:
- You are not the original owner of the content. To become an original owner, create a copy of the content ("Edit Detection" will automatically prompt a copy to be made).
- If you cannot make a copy (and therefore cannot make edits), you might have read-only permissions.
I'm trying to deploy a detection and it says "incompatible". What does that mean?
There are a few reasons why a detection is throwing an error message (e.g., "incompatible") when attempting to deploy. Navigate to the IDE (Detection Builder) to determine if it is one of the following:
-
Rule might need to be recompiled: Navigate to Settings and click on Detection Translations to recompile a detection that you own (it will be underlined). Note the purple dot indicating that a recompile can be run.
-
Field mapping might be incorrect: Click onto a detection language that you own (underlined) to access the underlining configuration for the detection language. Verify what the field naming conventions are for a target field and edit if needed. Note: If the field mappings are missing, you will see an error message highlighting the fields that need to be addressed.
-
Missing telemetry data: The selected tool your are trying to translate too might not collect that telemetry data. For example, some EDRs do not collect WMI events or named pipes, in which case the detection would never trigger due to missing telemetry data.
-
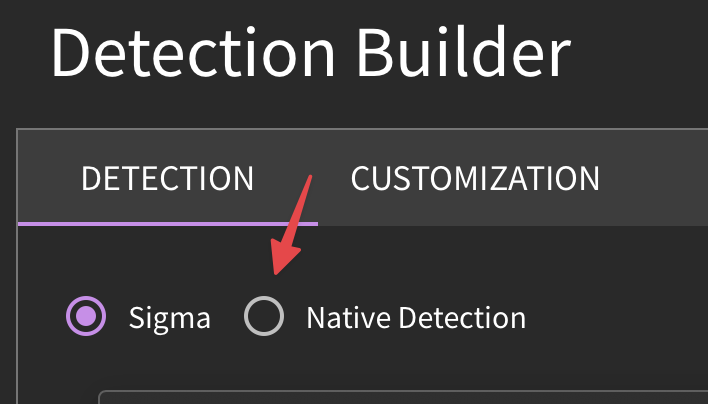
Unsupported advanced features: Some products offer advanced functionality for lookups, joins, aggregations, or transforms that are not broadly compatible. In this case, you can create a "Native Detection" in the Detection Builder - this allows you to use all features of that language, while maintaining the metadata, version control, and deployment and reporting through SnapAttack.
Can I use my own detection content?
Absolutely! Navigate to Detection Builder dashboard to input your native detections. By doing so, your organization will be credited for the threat hunting efforts that have been done (which affects your overall health score on the Detections Dashboard!).
What is the difference between "Detection" and "Customization" in the IDE?
Though the interfaces are similar, the "Customization" tab allows users to append any custom syntax changes to aid in False Positive Reduction (FPR). By doing so, users do not need to fork a detection to make alterations. Edits made under "Detection" would create a different version of the analytic, making a "forked version".
How do I create my own detection?
There are various ways you can create a detection:
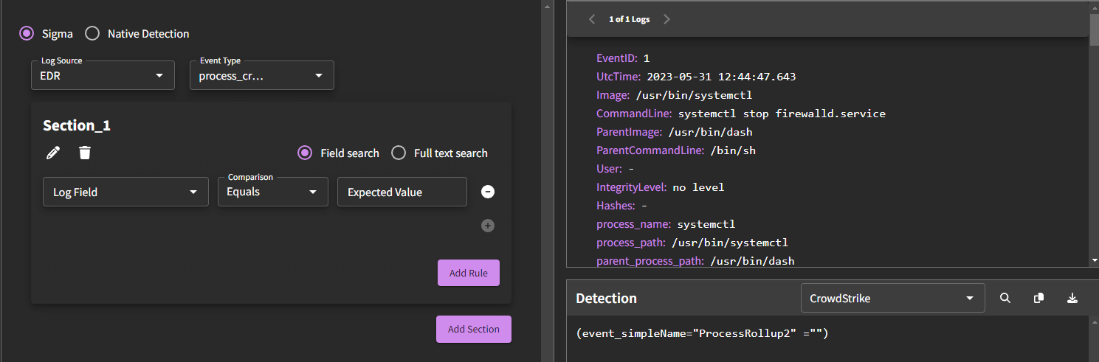
Click onto the process graph of a threat you'd like to build a detection for by clicking on a specific threat (example here). Navigate to "Create a Detection".
From there, you can alter the logic by using our no-code detection builder to specify the detection language, specific keywords you'd like the detection to search for, and more.
Select your log source, event type, and select your type aheads. Section 1 will appear which will include the fields related to the event types and keywords to search for (calc.exe, for example). Note that the output is automatically compiled on the right-hand side of the screen. Be sure to select the desired detection language and fill out the relevant details of the detection under Details (title, description, and the MITRE tags).
For a visualization of this workflow, check out our how-to video here!
I'm having trouble creating my own detection. What is going wrong?
Building detections is one of the more advanced workflows within the SnapAttack platform. If you are experiencing issues, there are a few things that could go wrong when creating a detection.
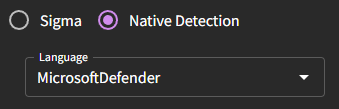
If you are attempting to input your own detection, make sure that you are using "Native Detection" and have selected the language appropriate to your environment (MicrosoftDefender, for example).
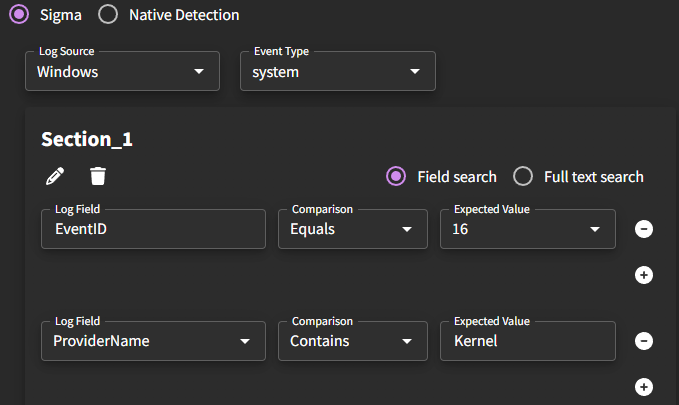
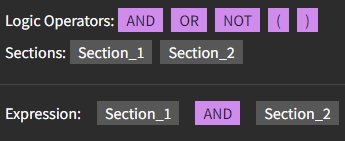
If you are using our Sigma no-code detection builder, make sure that you have selected a Log Source ("Windows", for example), Event Type ("system", for example), then determine the scope of the detection by filling out the section or sections with the rules.
If you have selected multiple sections, you will also need to determine the order of operations within the expression.
If you are still having issues in creating your detection, you may need to rework your field mappings. Please reach out to the SnapAttack team for assistance if needed.
How do I validate my detection?
The easiest way to validate a detection is to run it against an already-published threat. Look at the symbols notating (un)detected threats. If there is both a filled-in blue circle and red star, that means that your detection landed closely to the MITRE-tracked threat which means it detected that threat (and is thus, validated!)
How often are the rules from the public SigmaHQ repo sync'd with SnapAttack?
Sigma rules are synched with SnapAttack every six hours.
Can I deploy more than one detection at a time?
Yes! The easiest way to do this is switch the display view to "Grid", then select the detections you would like to deploy using the "Deploy Detections" button. There is also an "Undeploy Detections" button if that action needs to be taken.
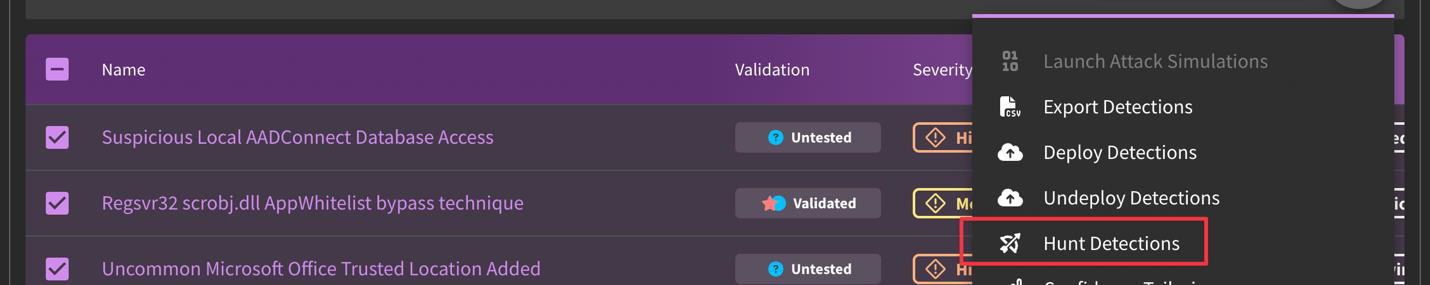
What is the difference between "Hunt" and "Deploy"?
Hunt allows you to hunt using time-based lookbacks (as oppose to point-in-time searches using magnifying glass symbol on the Detections page if you are looking at one detection). Deploying allows you to set up a repeatable detection rule that your environment will run continuously as a means of picking up on activity that matches the detection criteria.
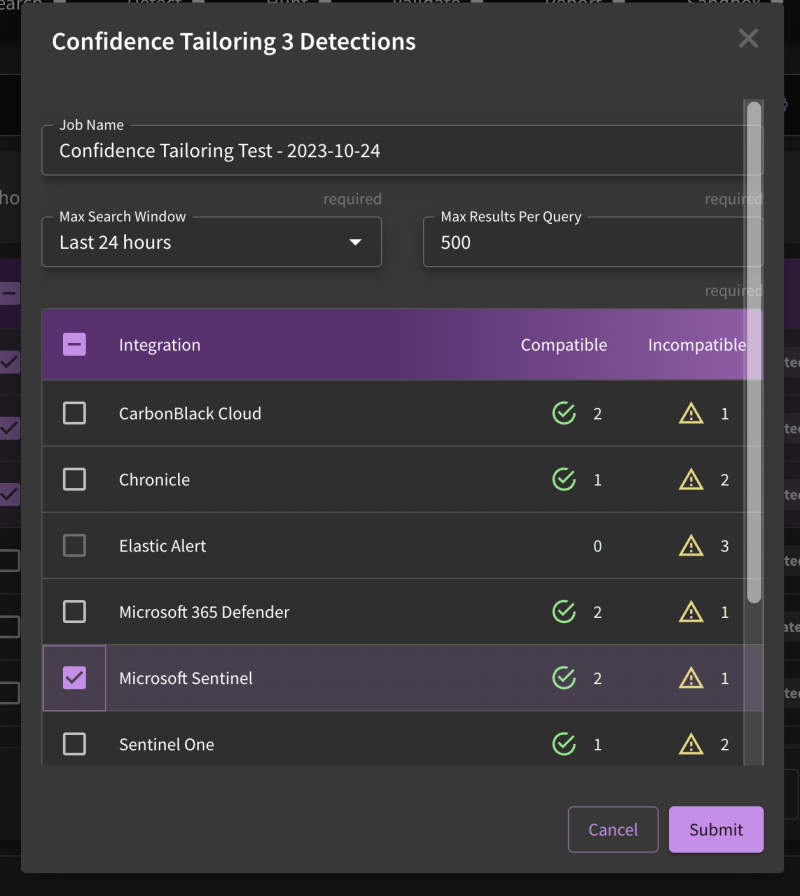
What is Confidence Tailoring and why would I use it"?
Confidence tailoring allows a SnapAttack customer to configure the ability to see only their tailored values, meaning all new detections will appear as "unknown" util the confidence has been calculated. This helps in reduce the possibility that a noisy detection could be deployed to a production environment. You can schedule confidence tailoring tasks through SnapAttack, as well.
Select your relevant tooling from the list of options. Note that the platform distinguishes between compatible and incompatible detections.
Hunt
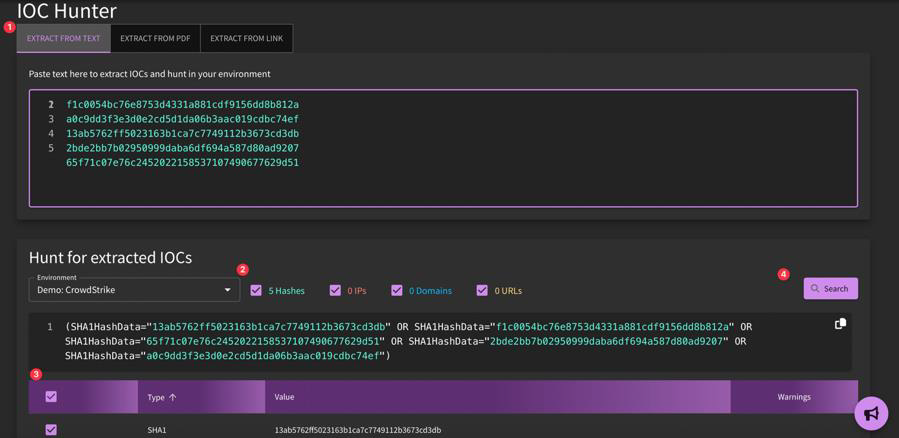
What is IOC Hunter and how do I use it?
IOC Hunter will extract IOCs either through raw text (copy and paste), from a PDF attachment or from a pasted-in hyperlink, to then hunt within your environment. After you have included your source of IOCs, select the environment in which you would like to hunt for the IOCs. You can narrow down your hunt criteria by unchecking boxes (Hashes, IPs, Domains, URLs). Click "Search" to initiate the search query.
How do I kick off a threat hunt?
You would kick off a Hunt using the same navigation as deploying detections but selecting "Hunt" instead.
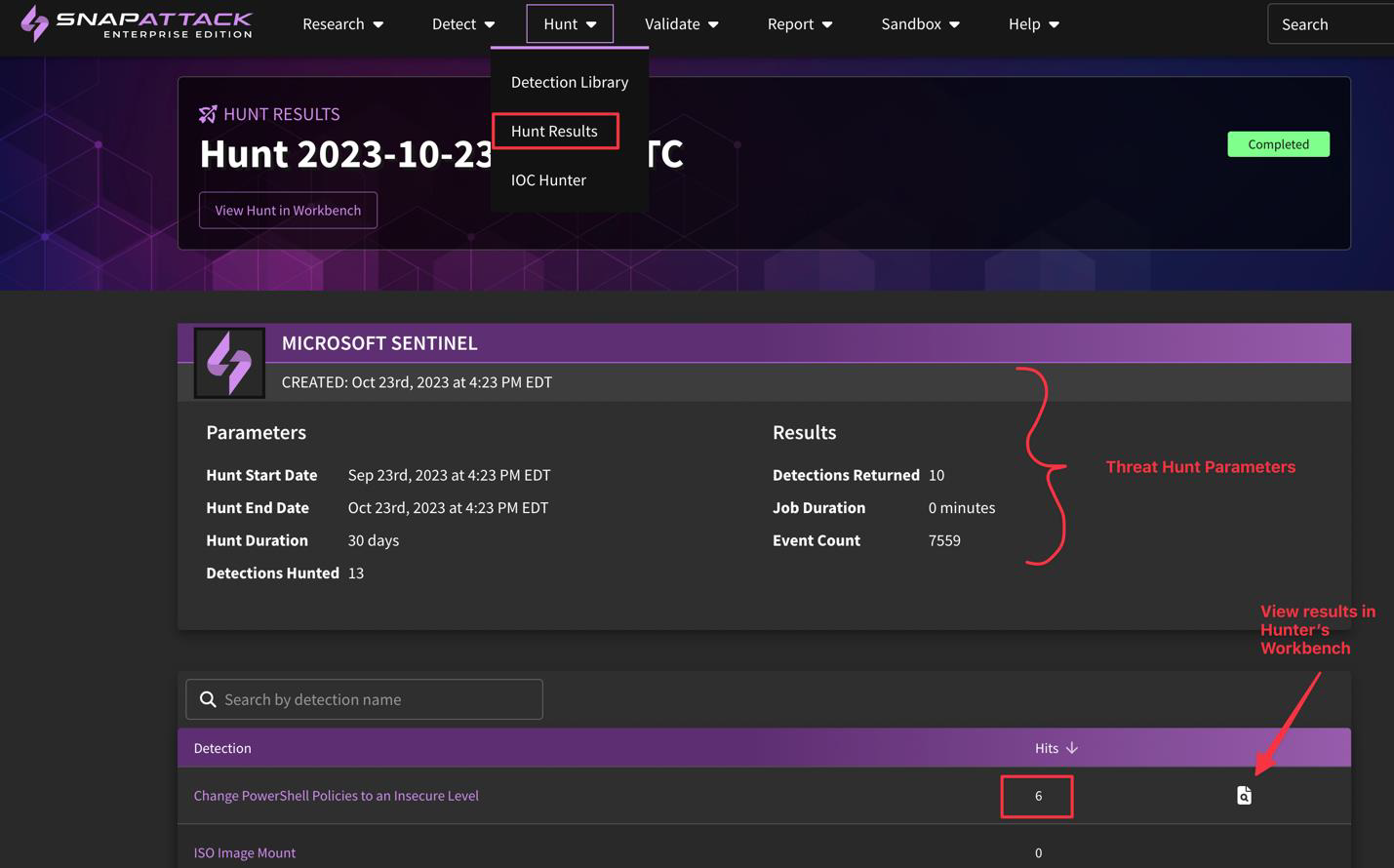
What is "Hunt Results" and how do I use it?
Though still in beta, SnapAttack users with access to Hunter's Workbench will be able to access Hunt Results, which allows users to analyze the results of a threat hunt within the SnapAttack platform.
Validate
What is Validation?
SnapAttack allows users to simulate threat activity, which can be used to scope out where detections need to be built out. Access the attack simulation dashboard here.
Note: You will need to create a separate API key - "Attack Simulation" - if you will simulate attacks in your own virtual machine.
How do I set up my validation agent?
To set up your validation agent, please refer to our Validation Agent Installation Guide here.
Under Attack Simulation Results, what is the difference between the attack status designations?
- Needs Review: The default state. The test case was run, and someone needs to look at the outcome.
- Not Tested: Some test cases have pre-requisites that must be met (an application must be installed, a computer must be joined to a domain, a specific OS version needs to exist). If that doesn't get met, we skip over the test.
- No Action: SnapAttack did not see any evidence of the attack from connected integrations (no logs or telemetry data related to the attack)
- Logged: SnapAttack saw event logs in your configured integration (SIEM/EDR) that could be used for threat hunting/alerting. No alert was generated.
- Detected: A SnapAttack-deployed detection would have triggered an alert in the integration
- Prevented: Something took an active defense that prevent the attack from completing successfully (e.g., EDR or Antivirus action).
What is the difference between "Ad Hoc Attacks" and "Attack Plans"?
Ad hoc attacks are one-off attack captures that are not necessarily grouped. Below is an example workflow demonstrating how to kick off an ad hoc attack:
Sandbox, Detect, or Validate Tab > Hamburger Menu > Launch Attack Simulation
Note: Selecting individual items to launch will only create ad-hoc attacks.
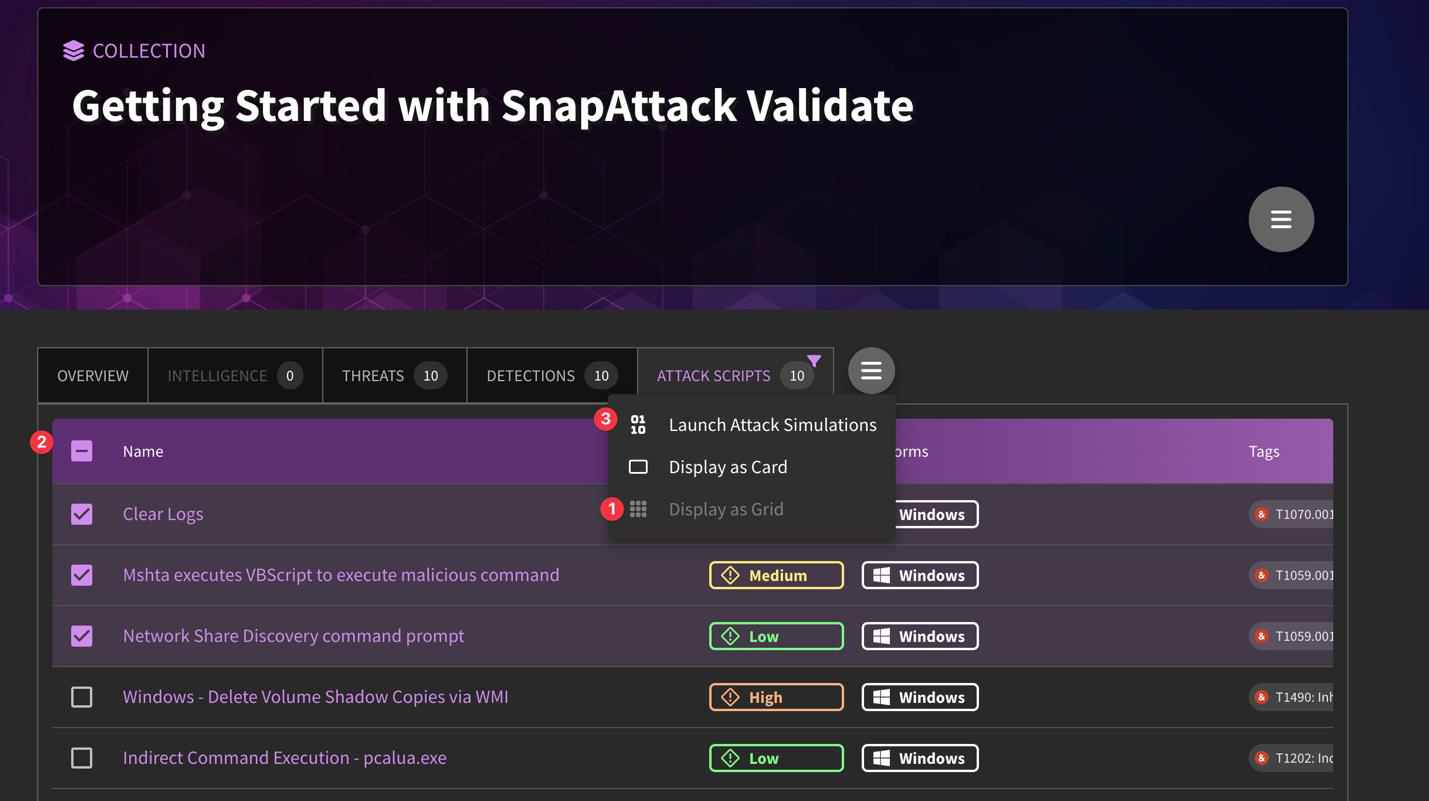
Attack plans are a grouping of executed automated attack techniques. After an attack capture has been completed, you can see the outcomes as part of the attack plan. There are a few ways in which to create an attack plan:
- Attack Plan via Collection Tab
Collection > Sandbox, Detect, or Validate Tab > Filter/Select Items > Hamburger Menu > Launch Attack Simulation
Note: This will create an attack plan if multiple options are selected. The below example is from the "Getting Started with SnapAttack Validate" Collection.
- Attack Plan via Content Feeds
Sandbox, Detect, or Validate Tab > Filter/Select Items > Hamburger Menu > Launch Attack Simulation
Note: This will create an attack plan if multiple options are selected. The below is accessed through the Threats content feed.
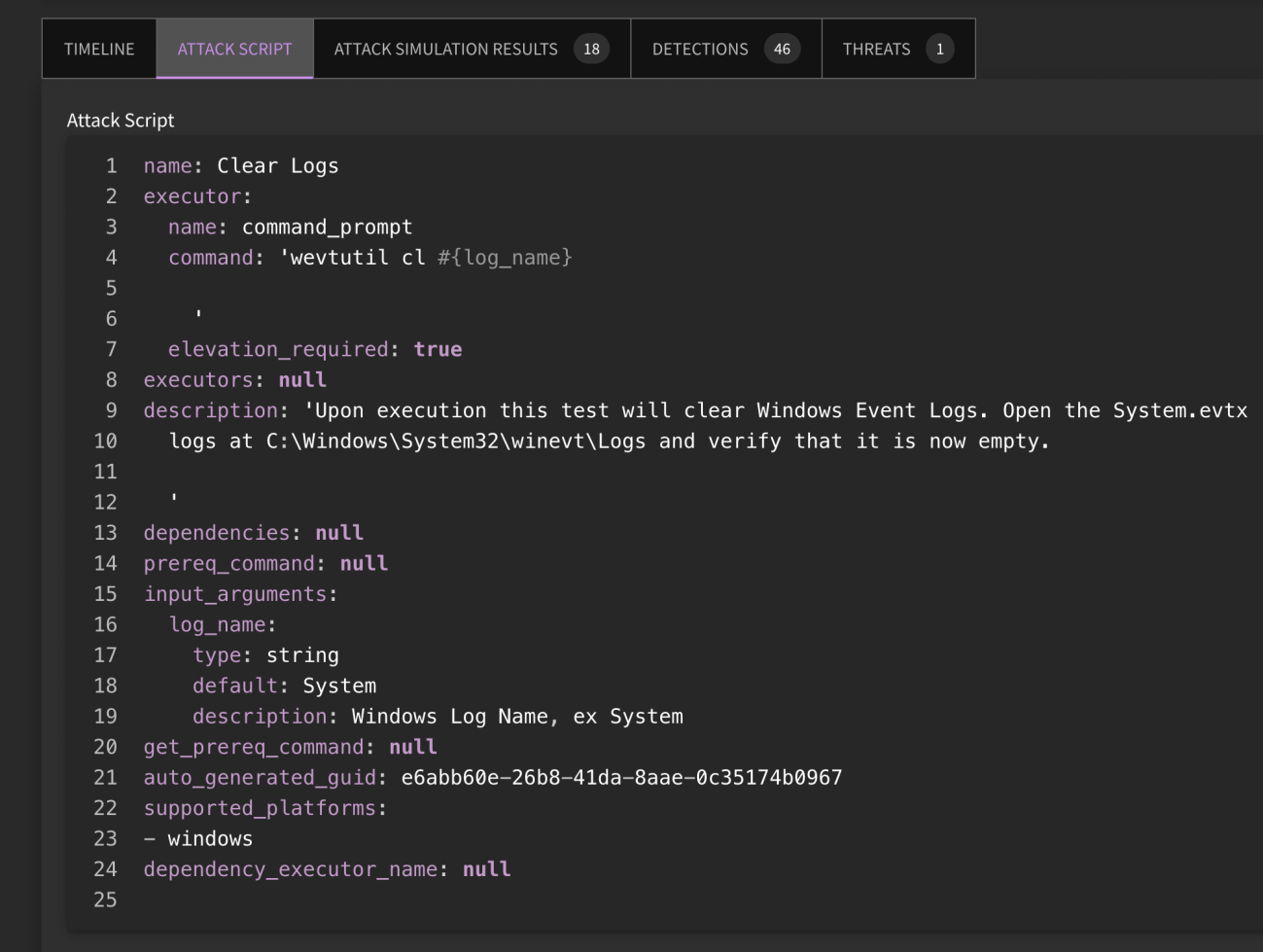
What are Attack Scripts?
The SnapAttack platform allows you to launch attack simulations using pre-coded attack scripts (attack-as-code). You can launch the scripts one at a time or as a serial attack by launching in-bulk. Scripted attacks have the benefit of being exportable, meaning that you can run them in your network as a diagnostic to measure your current coverage for that threat, or you can deploy detections and use them as a validation module for true end-to-end testing. This feature is available to all platform users, though creating and executing attack scripts are limited to subscribers. Follow along with this example.
Can I run more than one attack script at a time?
Yes! You can easily run multiple attack scripts as part of an attack plan. By clicking into "Grid View", you can select which scripts you want to run. We recommend using this introductory collection.
Report
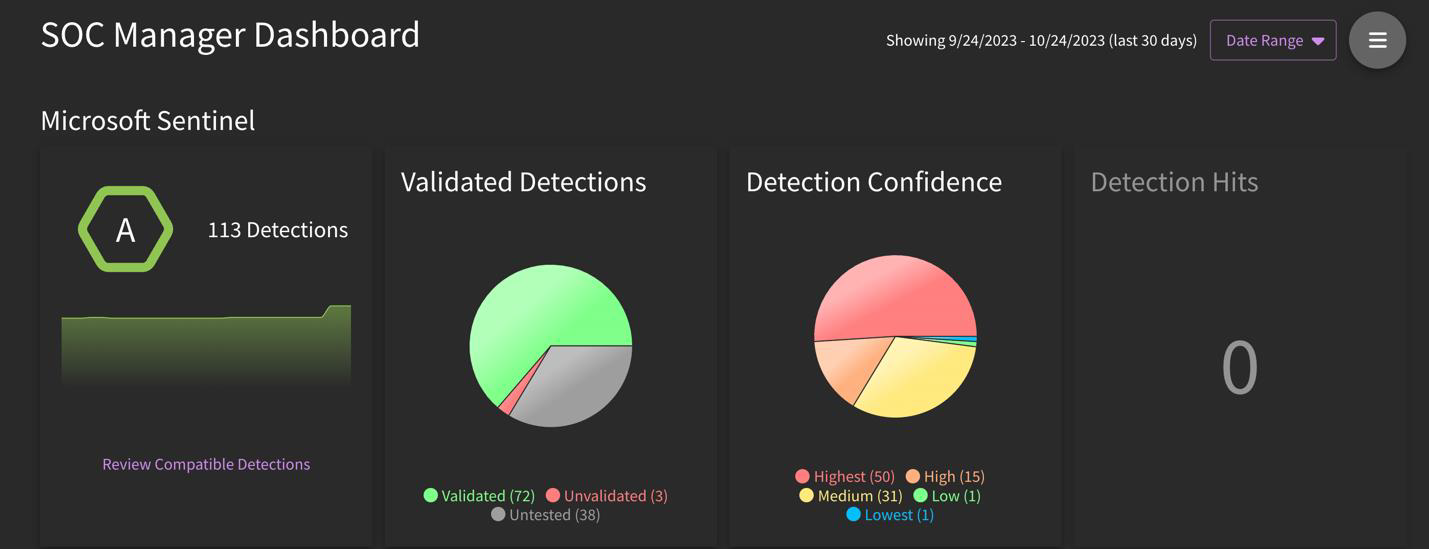
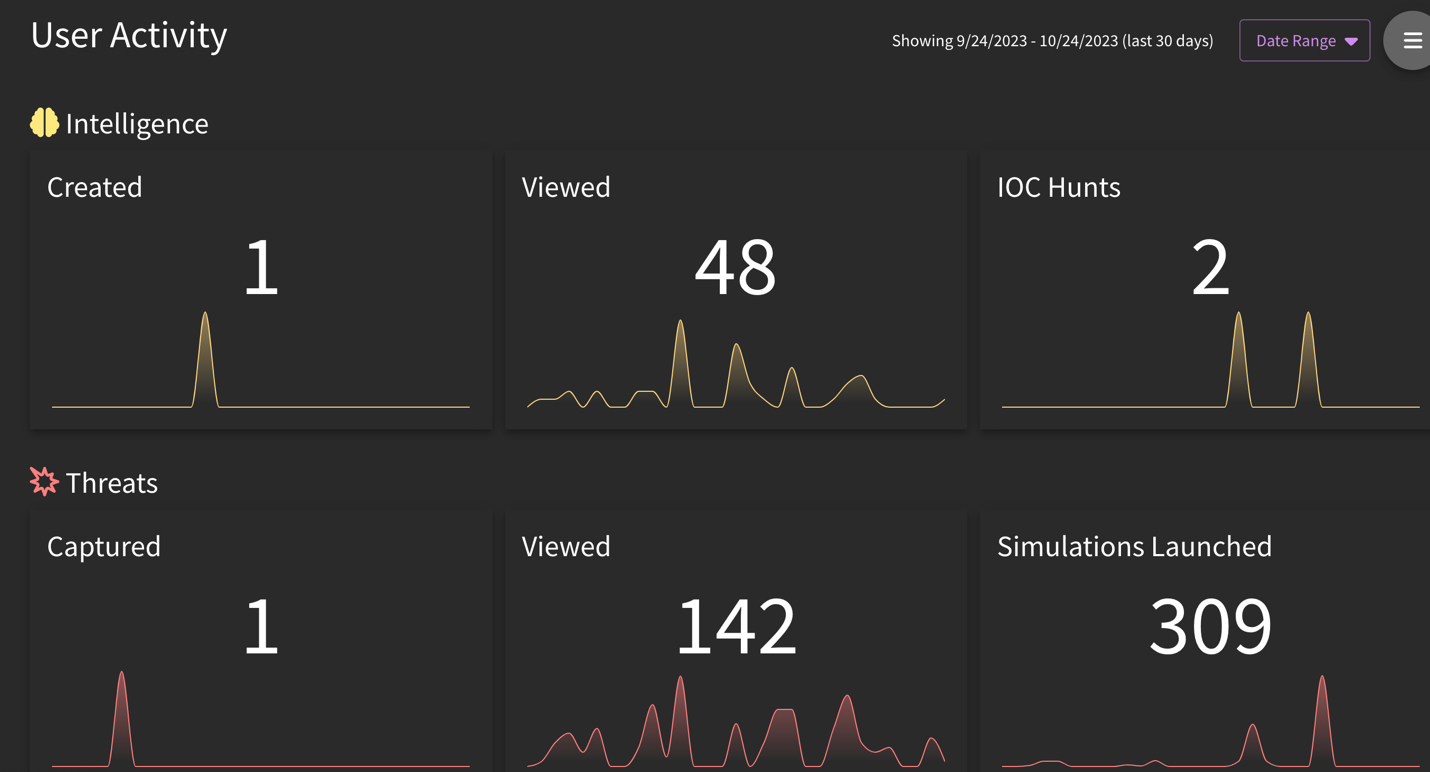
What is the SOC Manager Dashboard? And what about User Activity Dashboard?
The SOC Manager dashboard provides executive-level summaries of integration-specific actions completed within the platform. You can drill down into specific detection languages by clicking on "Review Compatible Detections" There is also a section on confidence and severity level correlation based on the deployed detections.
The User Activity section provides user-specific metrics of activities completed within the platform.
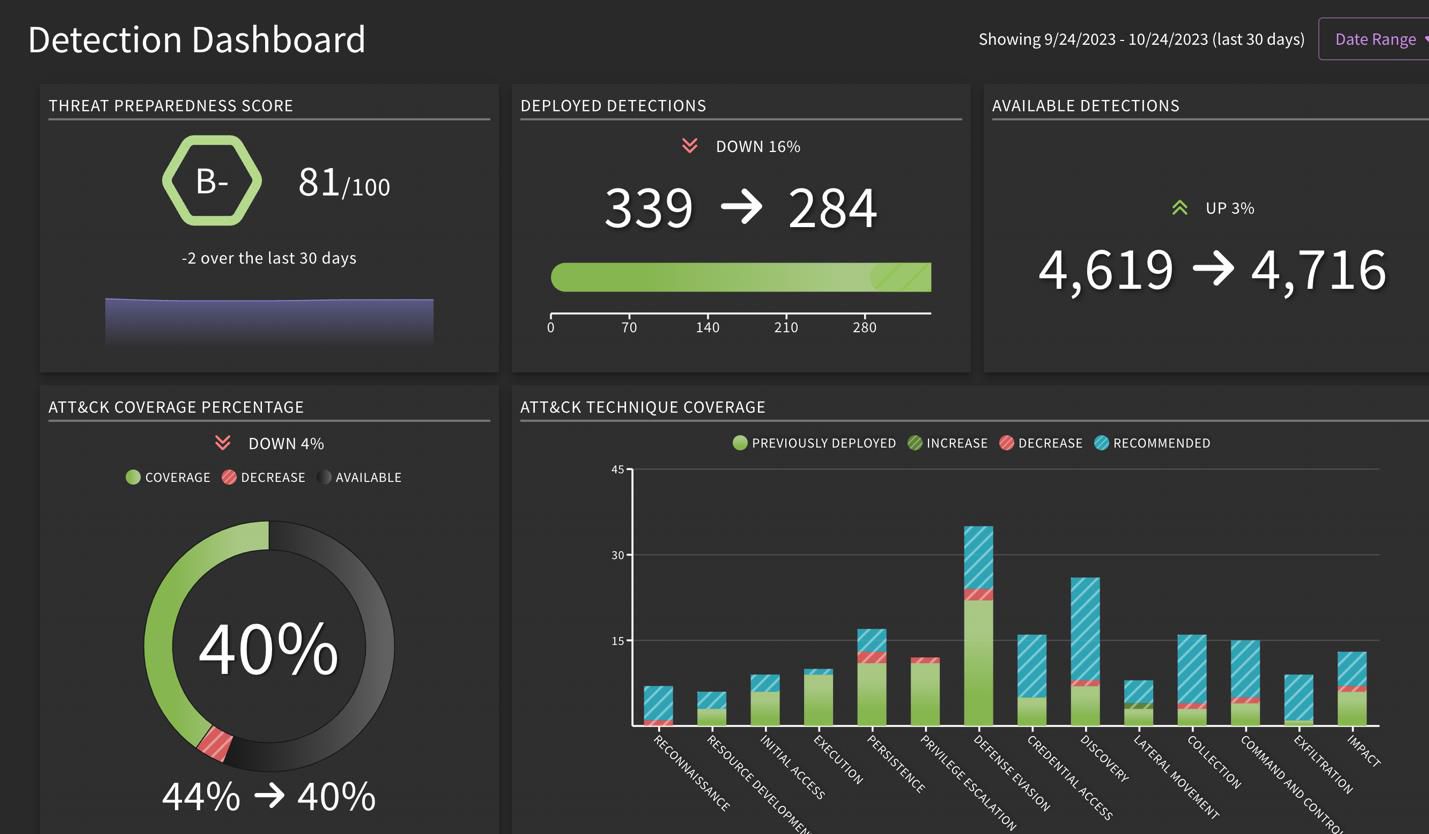
How does that differ from the Detection Dashboard?
The Detection Dashboard illustrates your organization's overall health score based on how much detection coverage has been tracked. Note that with each detection built and validated, the score increases.
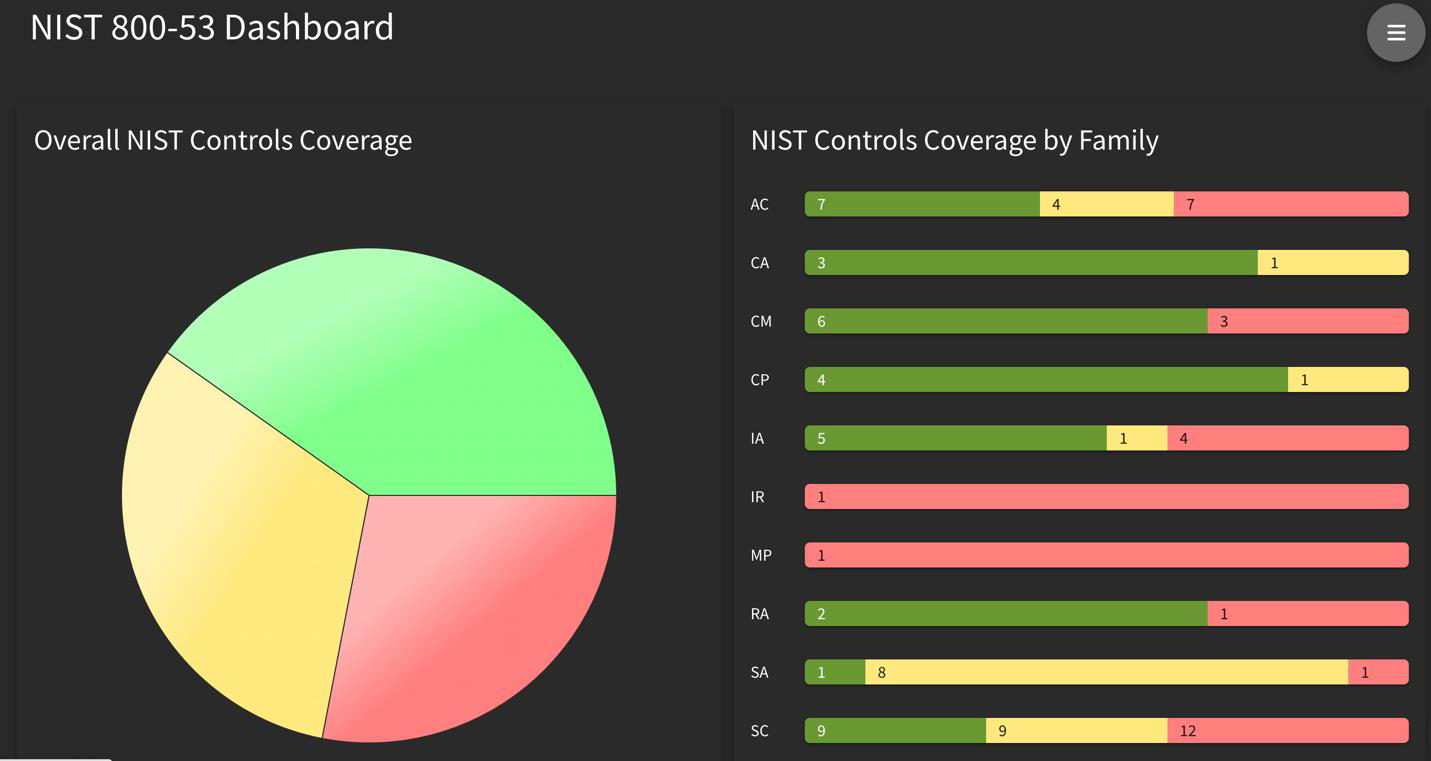
What is the NIST Dashboard, then?
The NIST Dashboard provides risk-centric insights for organizations to view their detection coverage across NIST 800-53 families and controls.
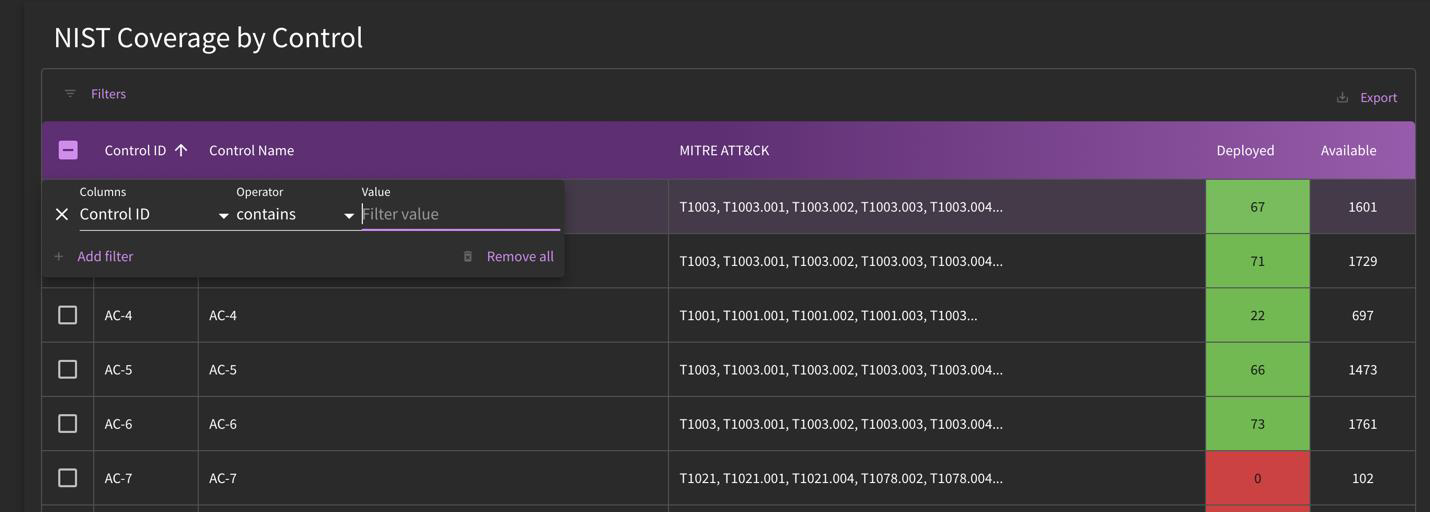
Within the NIST Dashboard, you can also access a table-view of the various controls that are related to your organization's detection coverage.
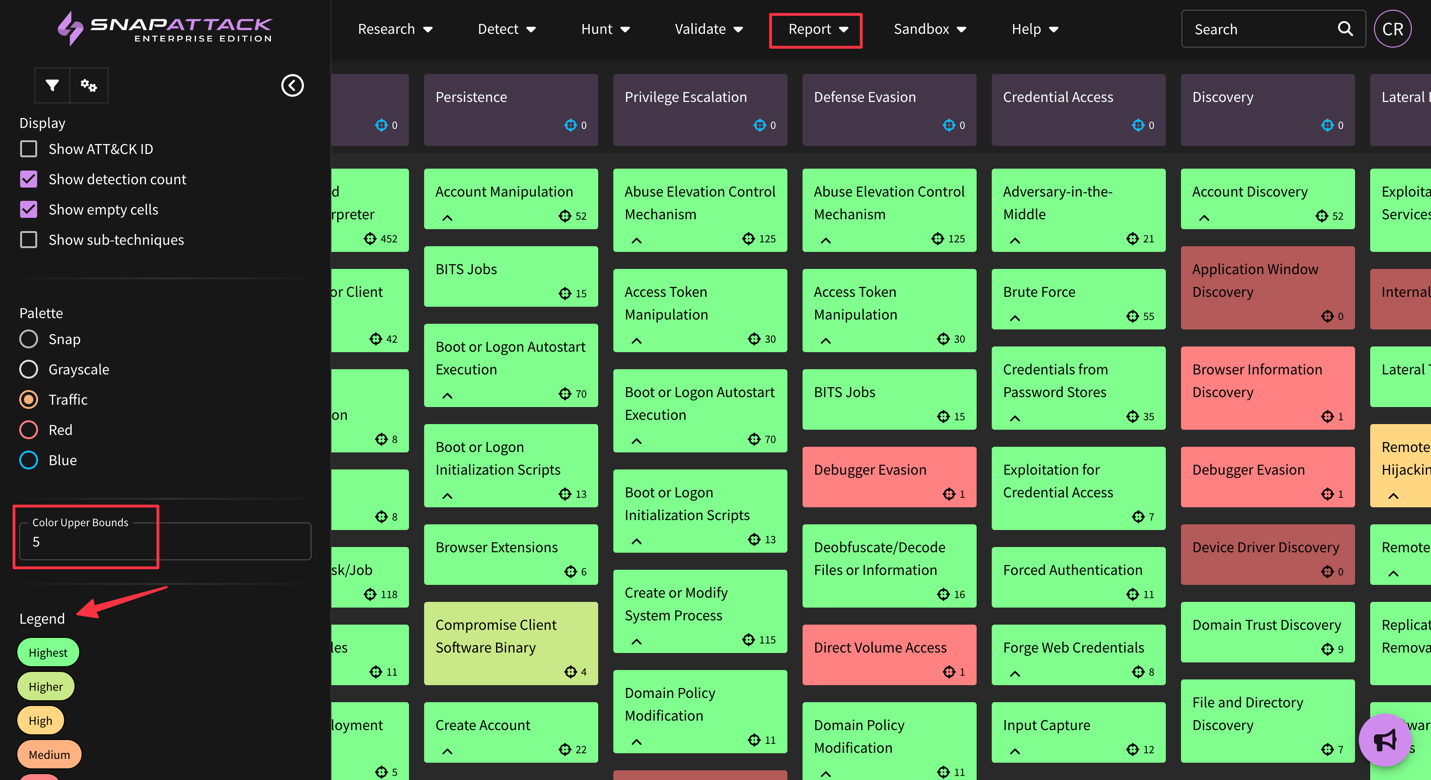
Are the filters in MITRE ATT&CK customized to my environment or general across all users?
The integrated MITRE ATT&CK map within SnapAttack platform supports confidence tailoring which provides customized rankings based on your existing environment.
Sandbox
What is included in the threat library?
SnapAttack's threat library contains memorialized adversary tradecraft that can be used for identifying detection opportunities.
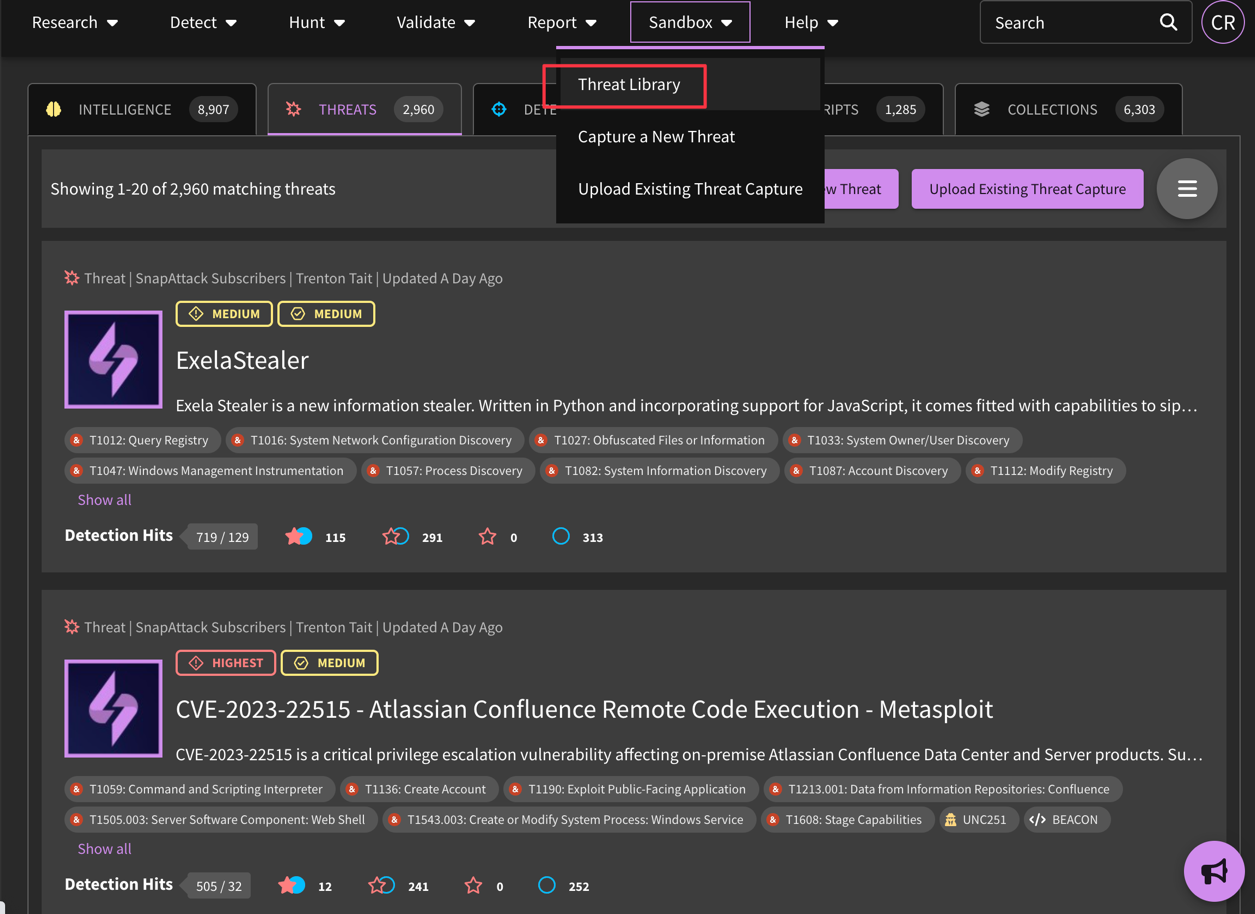
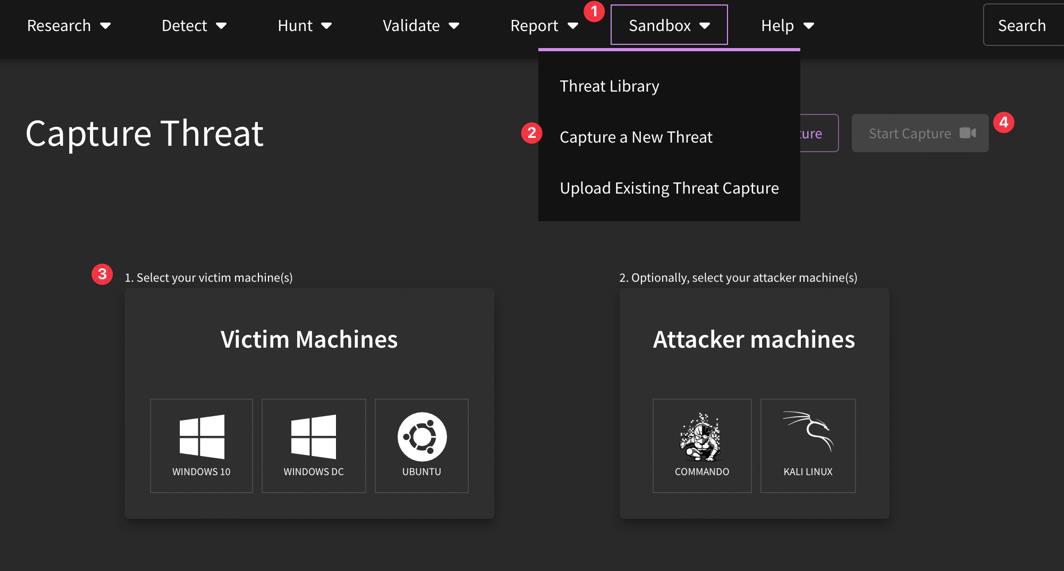
What is CapAttack?
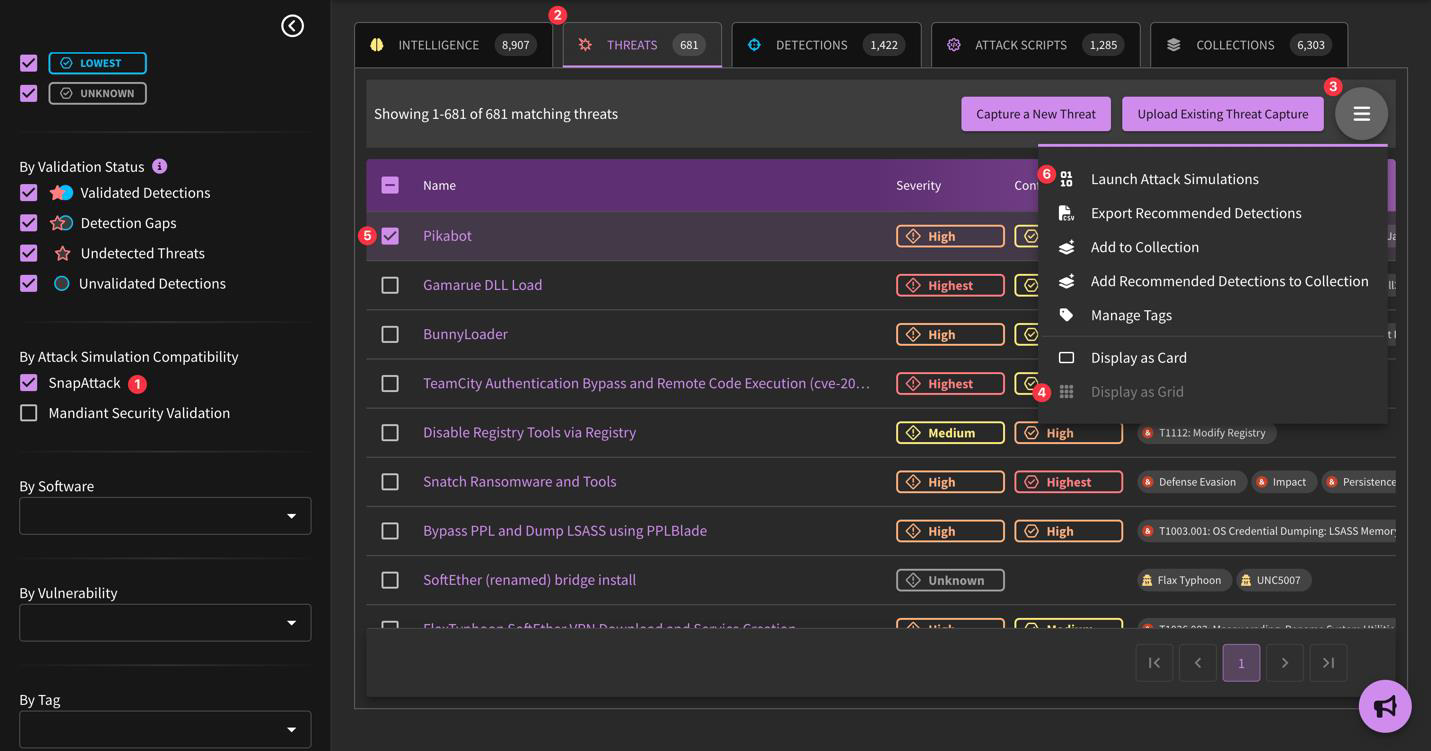
Our CapAttack engine captures new attacks and puts them into the platform. You can capture attacks either through the SnapAttack platform or locally, then upload them. To access the CapAttack environment, navigate to Sandbox, then either "Capture a New Threat" or "Upload Existing Threat Capture".
Where available, attack captures related to a specific threat can be viewed alongside recommended detections and reference material. An example can be found here.
Note: You will need to create a separate API key - "Local Threat Capture" - if you will be capturing threats on your own machines.
What can and cannot be uploaded into a sandbox threat capture?
In general, you are allowed to do anything you need to do to replicate threat activity using CapAttack. We do not have restrictions on downloading or executing malware, reaching out to known C2 servers, etc. Attacks between the attacker and victim VM are greenlit.
However, we do have some commonsense restrictions such as, "Don't attack things you do not have permission to attack", "Don't download LOIC or slowloris to DDoS third parties". Some of this is outlined in the Acceptable Use Policy: https://www.snapattack.com/acceptable-use-policy/
Is CapAttack and Attack Simulation (aka "Validation") the same thing?
Not quite – Attack Simulation ("Validation") provides a space for users to simulate attacks, while CapAttack is used to capture threat activity (emulate the threat actor) so that users can identify where their detections picked up on threat activity. If there are detection gaps, teams can act on that information to build out stronger defenses against threat activity.
Attack simulation takes certain attacks, which can originate from attack captures, on the platform and launches them.
How do I add captured threats to one of my collections?
While in the Sandbox dashboard, click on the hamburger icon in the right-hand corner and select "Grid View". Select the threats you would like to include and select "Add to Collection". From there, you will need to specify your desired collection or create a new one. Press "Save"!