Hunt
What is Hunt in SnapAttack?
While deploying detections provides users with recurring alert rules in their SIEM/EDR for all events going forward, utilizing SnapAttack's threat hunting capabilities allows users to perform retroactive hunts for activity in the past (e.g., last 30 days). From the Hunt dropdown in the navigation menu, you will see three distinct options:
- Detection Library: Detection rules that can be used used to kick off threat hunting operations
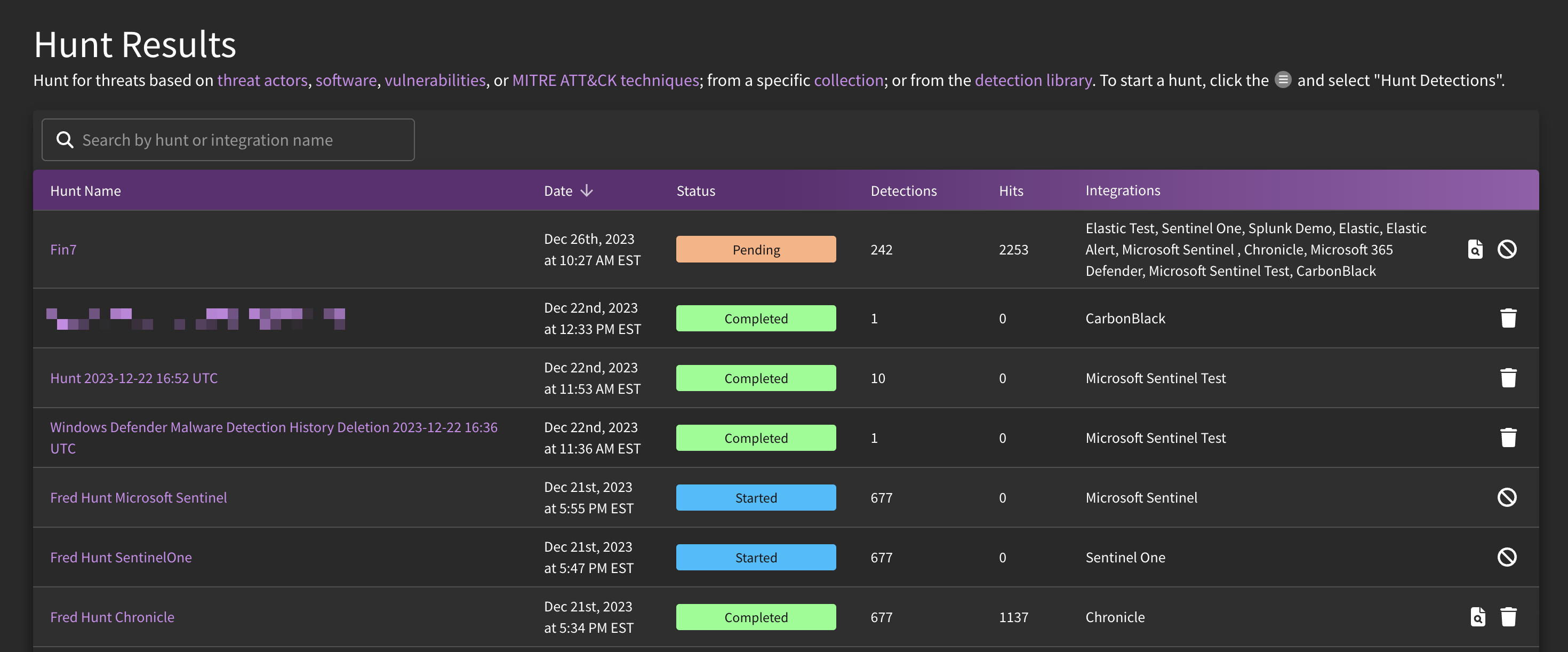
- Hunt Results: Overview of previous hunt jobs and detailed read-outs based on the threat hunts performed. Information such as job status, number of hits, and number of detections included in the threat hunt (especially salient for bulk hunt jobs), and links to Hunter's Workbench are all accessible under Hunt Results. The first iteration of this feature has been rolled out on a limited basis. To get access, please reach out to your Customer Success Manager.
- IOC Hunter: For SnapAttack users who would like a easy-button for hunting IOCs, IOC Hunter is the man for the job! SnapAttack's IOC Hunter parses IOCs from your preferred resource, and then allows you to search them within your environment.
Common Use Cases
Detection content for the purposes of threat hunting is relevant to various teams within an organization as threat intelligence, defensive, and offensive teams play a part in the detection development lifecycle. Hypothesis-driven hunts can arise from finished intelligence, completed red team exercises, or detection alerts.
- Threat Intelligence: Understanding how the behavioral patterns (TTPs) are employed against a victim's environment will assist CTI teams in further contextualization of the threat. Intelligence containing IOAs and IOCs can be relayed to the threat hunters so that they can launch investigations against key indicators of threat activity.
- Detection Engineering: Engineers can track what detections have been deployed (and to which tooling), quickly build out new detections (using the no-code interface), and view related logs that have matched against the detection logic. Detection engineers can work alongside threat hunters to build out relevant alerting rules for proactive coverage against potential threats.
- Threat Hunters: Once detections are created (either by SnapAttack, the community, or your team), threat hunters can then kick off their searches knowing that the logic is pre-validated.
- Red Teams: Offensive teams can use the detections to hone their techniques to remain undetected, as well as identify detection opportunities from known threat activity. Information shared from red teaming exercises can be relayed to threat hunters to proactively search for IOAs which can be baked into detection rules.
Threat Hunting Operations
For a full walkthrough on how to launch a hunt and review results in Hunter's Workbench, check out our tutorial below.
Launching a Hunt
Detections can be hunted either on an individual basis or in-bulk. The workflow to perform such actions should be familiar to you if you know how to deploy detections in either method. To kick off threat hunts, simply navigate to the detections library, filter or select the content you would like to hunt in your environment, and then select "Hunt" within the Hamburger menu. Individual detections can also be hunted from the detection page. You will need to specify which integrations to target, as well as the look-back timeframe and maximum result threshold. Be sure to give your job a meaningful name such as "Rhysida Threat Hunt 2023-12-20". You can keep tabs on the job status of your threat hunt by navigating to the "Hunt Results" page.
Hunter's Workbench
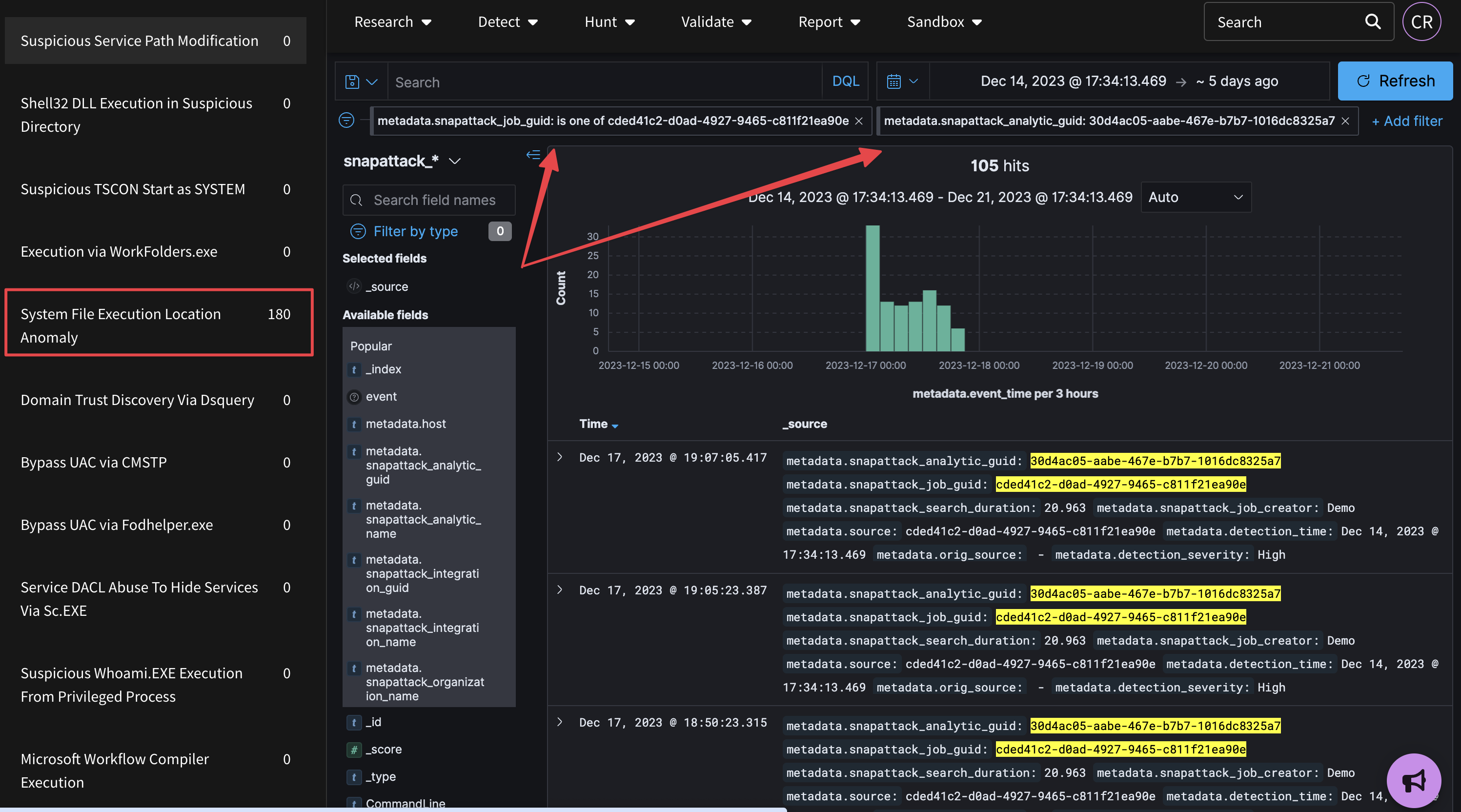
Hunter's Workbench offers an alternative to deploying detections as alerts to configured integrations, such as a SIEM or EDR. Detections can be hunted across one or more integrations, with the results returned and aggregated in SnapAttack for further analysis, correlated across multiple rules or risk-based alerting when multiple events fire for a specific hostname, IP address, user, or other entity.
Accessing the Workbench can be done by viewing the "Hunt Results" following threat hunt operations. The OpenSearch dashboard provides users with the flexibility needed to drill down into hits resulting from the hunt(s),
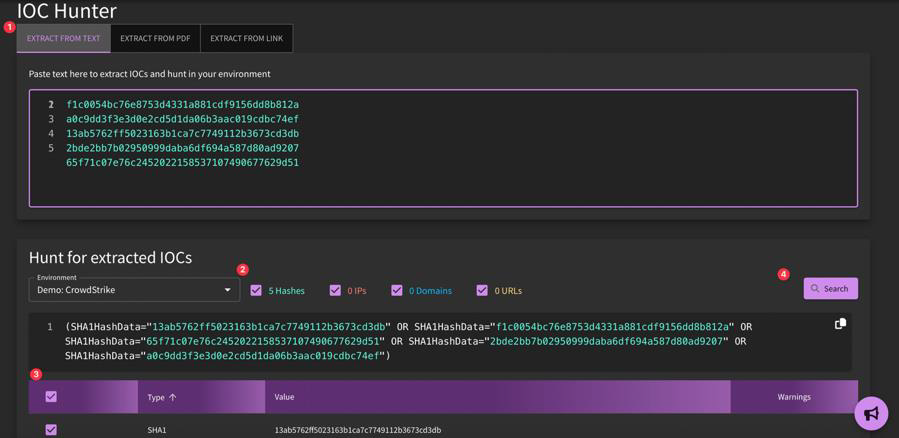
IOC Hunter
For a full walkthrough on how to use IOC Hunter, check out our tutorial below.
IOC Hunter will extract IOCs either through raw text (copy and paste), from a PDF attachment or from a pasted-in hyperlink, to then hunt within your environment. After you have included your source of IOCs, select the environment in which you would like to hunt for the IOCs. You can narrow down your hunt criteria by unchecking boxes (Hashes, IPs, Domains, URLs). Click "Search" to initiate the search query.