Intelligence
What is Intelligence?
Threat intelligence can come from many sources. Free and open source intelligence can be derived from security bulletins, news articles, blog posts, Twitter tweets, and other resources. Private intelligence may be created internally within your organization, or shared within your industry's ISACs or other threat sharing groups. There's also commercial threat feeds that your organization can subscribe to and purchase.
SnapAttack doesn't care about the source of the intelligence. Our goal is to help make it actionable, by helping red teams capture attacker tradecraft as threats and blue teams create behavioral detections. SnapAttack automatically brings in threat intelligence from many sources, but you can also add your own to the platform.
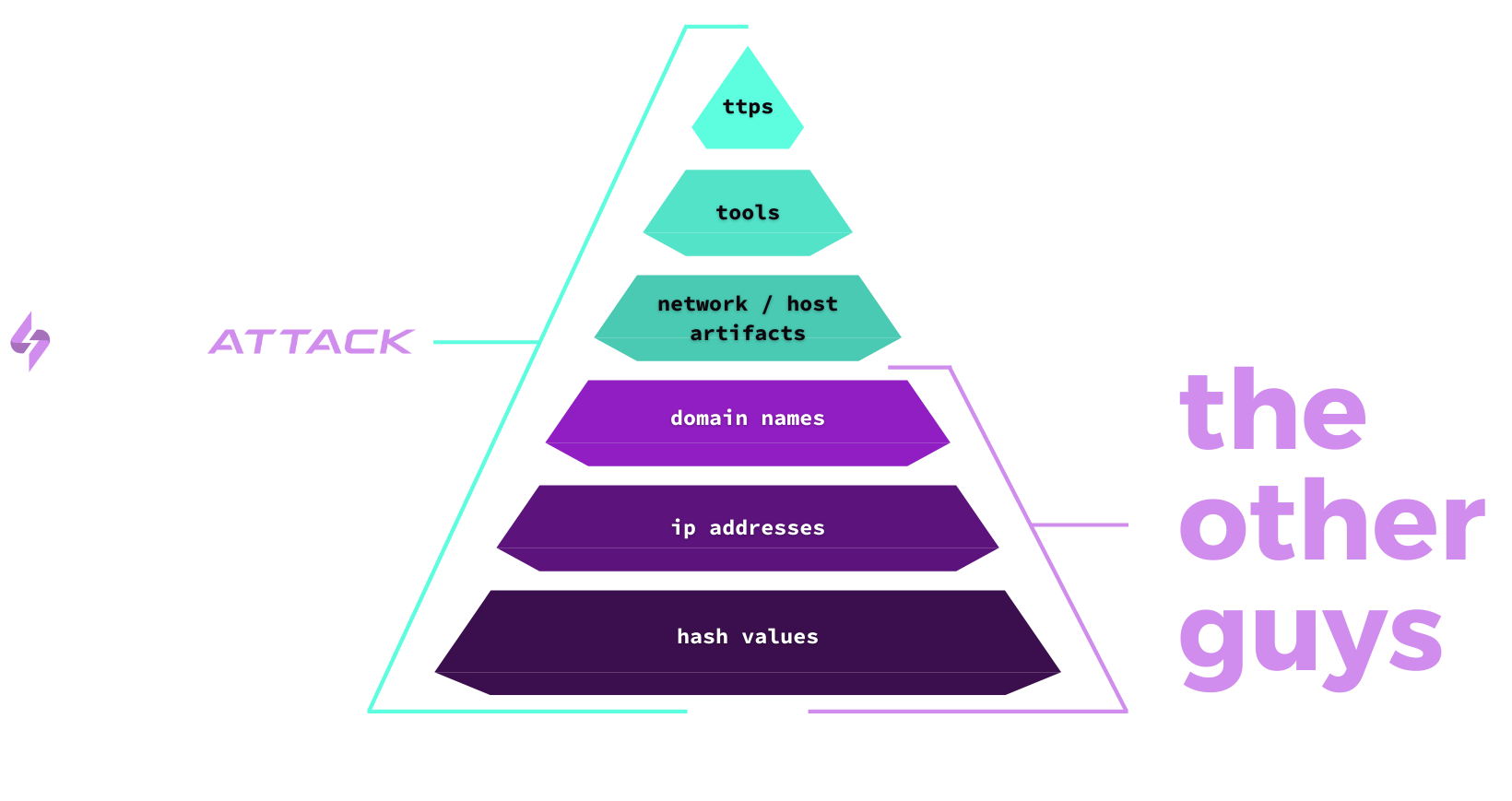
Chances are you're already familiar with the Pyramid of Pain. Most threat intelligence today is distributed as Indicators of Compromise (IOCs) — those are the domain names, IP addresses, and software file hashes used by an attacker. These work great if you want to quickly tell if an attacker was in your network, but they're only good at looking in the rear view mirror. IOCs quickly become outdated, and are trivial for an adversary to change. For targeted attacks, adversaries often have specific infrastructure and compiled malware for each target, rendering IOCs from another compromise useless. SnapAttack helps you take a more proactive stance and move up the pyramid to writing high quality, behavioral detections. These are harder and more costly for an attacker to evade.
Viewing Intelligence
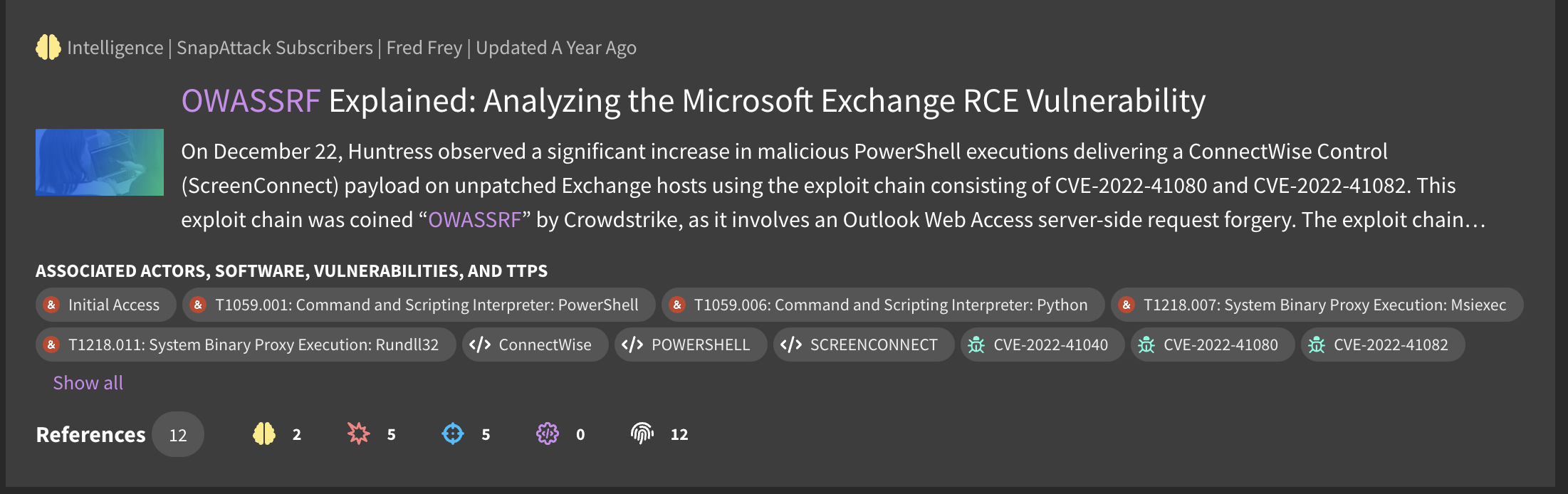
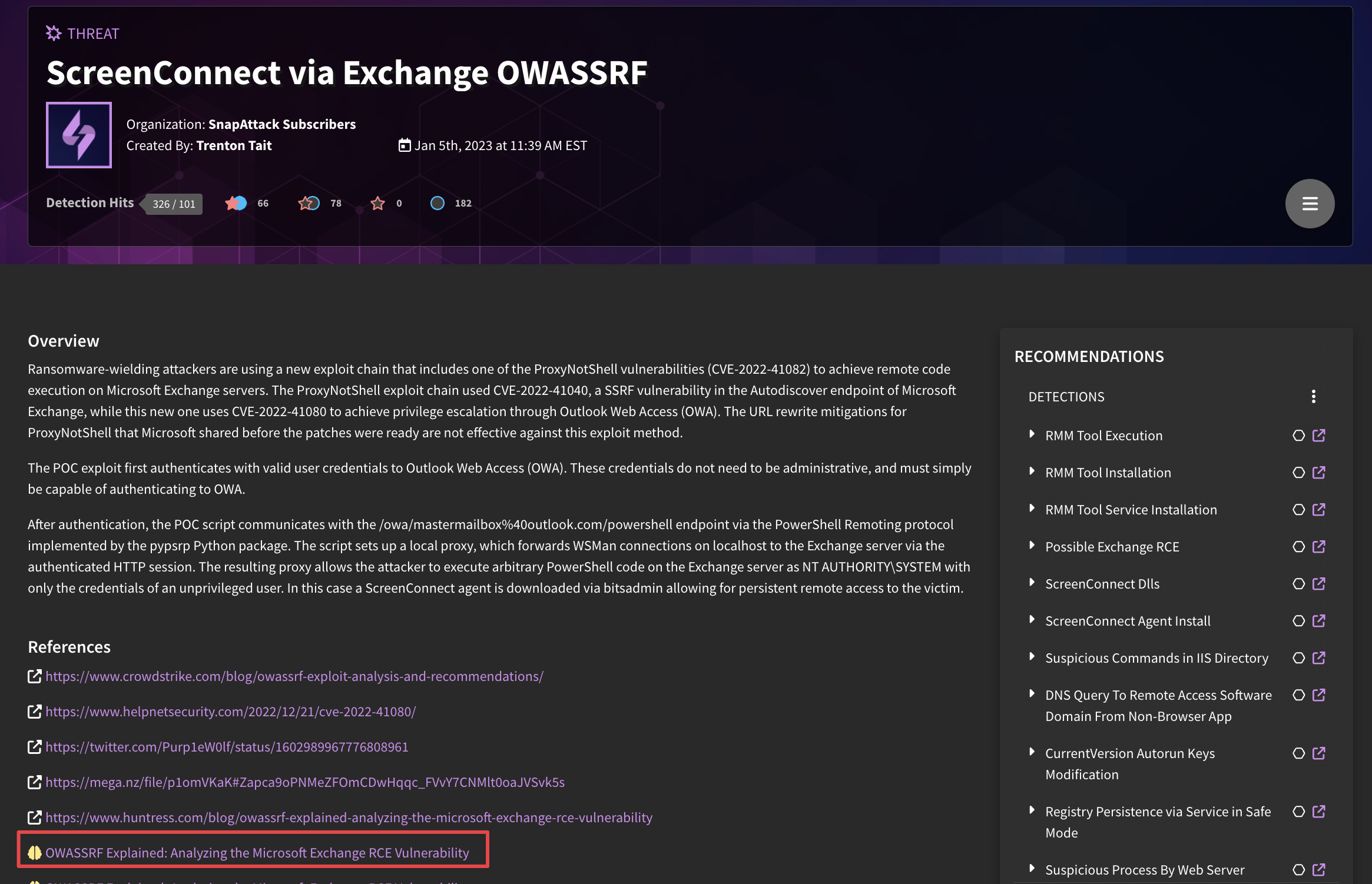
Like all content types, you can use searching and filtering to find existing intelligence in the platform. You can use the card view to quickly preview intelligence. At the top of the card, you can see the content type, the owning organization, the original author, and the date the content was last updated. The body of the card has the intelligence's title and summary description. Threat actors, ATT&CK tags, and regular tags will appear on the card. At the bottom, there is a references section which shows the number of total references to other content in the platform, as well as reference counts for each content type. In the picture below, you can see that this intelligence report has 3 linked threats, 5 linked detections, 2 linked intelligence reports, and 12 IOCs. Clicking on the card will take you to the full intelligence page.
Most of what's on the full intelligence page should be self explanatory, so we'll only clarify a few points. The references section links back to the source material — this can be an external website or an attached formal threat intelligence PDF report PDF. Intelligence can contain multiple references. We use this reference URLs to automatically link content in the platform. For example, if a reference URL for an intelligence object is also included in a threat or detection's references section, then those two content items will be automatically linked. This would appear in the linked content table on the intelligence page:
On the linked content item, the reference would link back to this intelligence page:
Creating Intelligence
For a full walkthrough on how to create/edit a intelligence objects, check out our tutorial below.
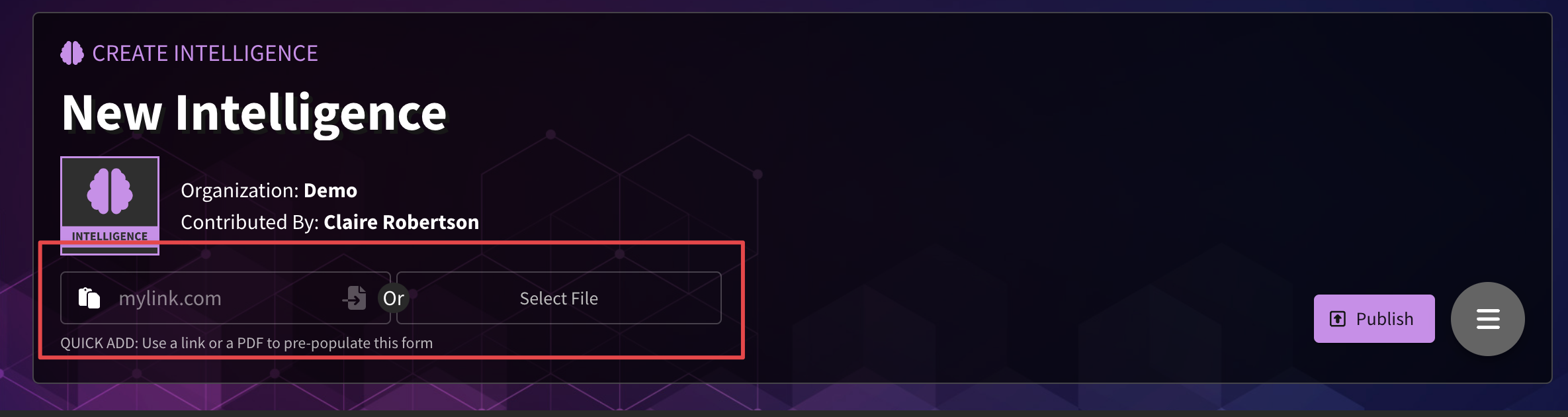
You can use the create intelligence page to add new threat intelligence into SnapAttack. This is as simple as completing the form. We encourage you to add optional fields, including MITRE ATT&CK tags and threat actors, so help make this intelligence discoverable from other parts of the application.
Quick Add Intelligence
Did you notice the "Quick Add" feature at the top of the create intellgence page? You can submit a link to the intelligence article and have SnapAttack automatically complete the form. It will attempt to summarize the article, extract the original author, ATT&Ck techniques, threat actors, and other tags from the source.
SnapAttack always links back to the original source of the intelligence. This will appear as a reference URL. You can also upload files and attach them to the intelligence object in SnapAttack. For example, this could be a Word document or PDF from an internal threat report.
Pay attention to the organization listed at the top of the form as this is who will own this object. See the Settings section for more information.
Once the intelligence form is complete, click the publish to make it live and searchable in the system. You can also save it as a draft to continue editing it privately.
Editing Intelligence
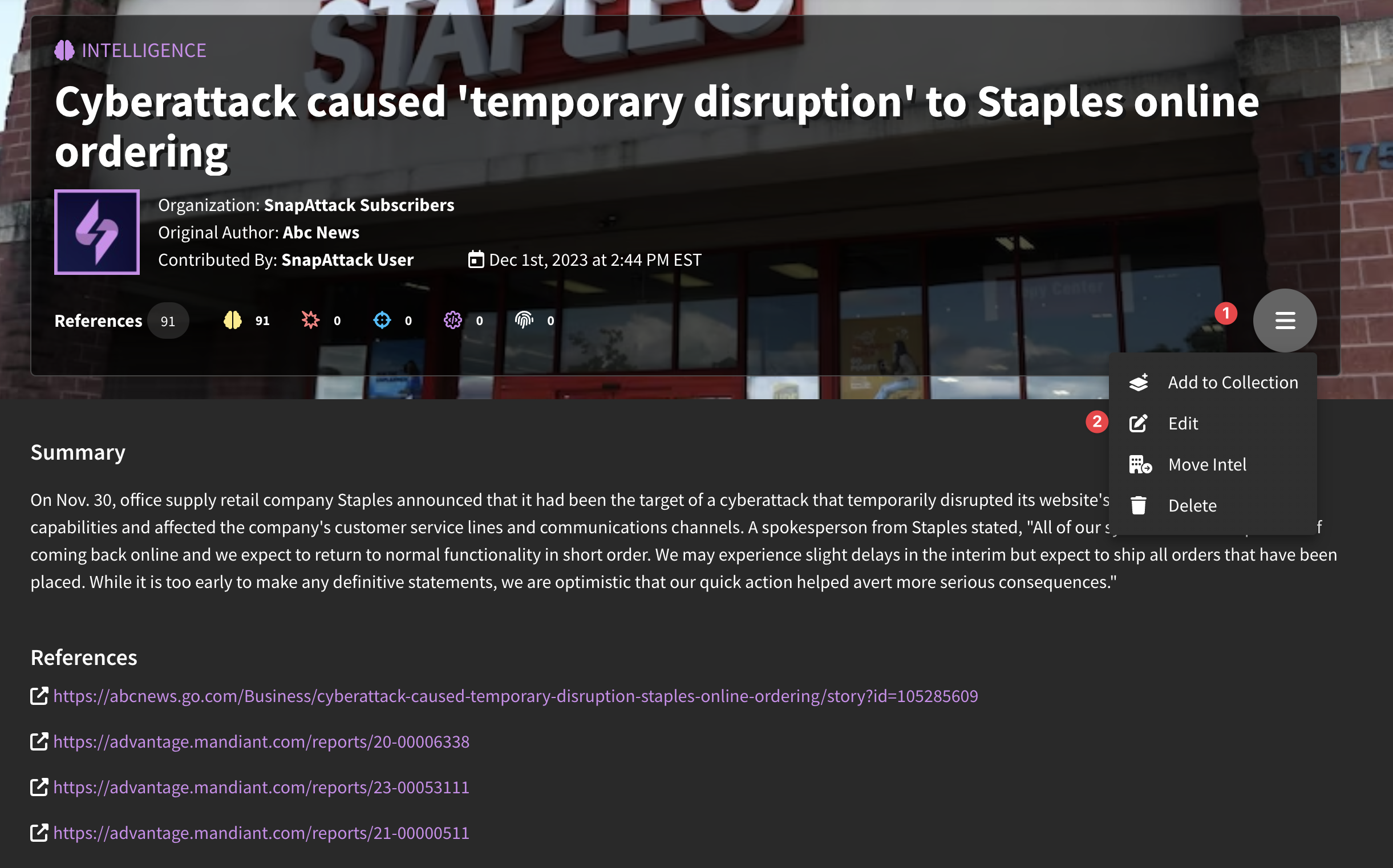
You can edit an existing intelligence object if you are the creator, or are a member of the same organization as the creator and have edit permissions. You should see an "Edit" button on the top right corner of the intelligence page after you expand the hamburger menu. Clicking this will bring you to the edit form, where you can update information about this intelligence report.
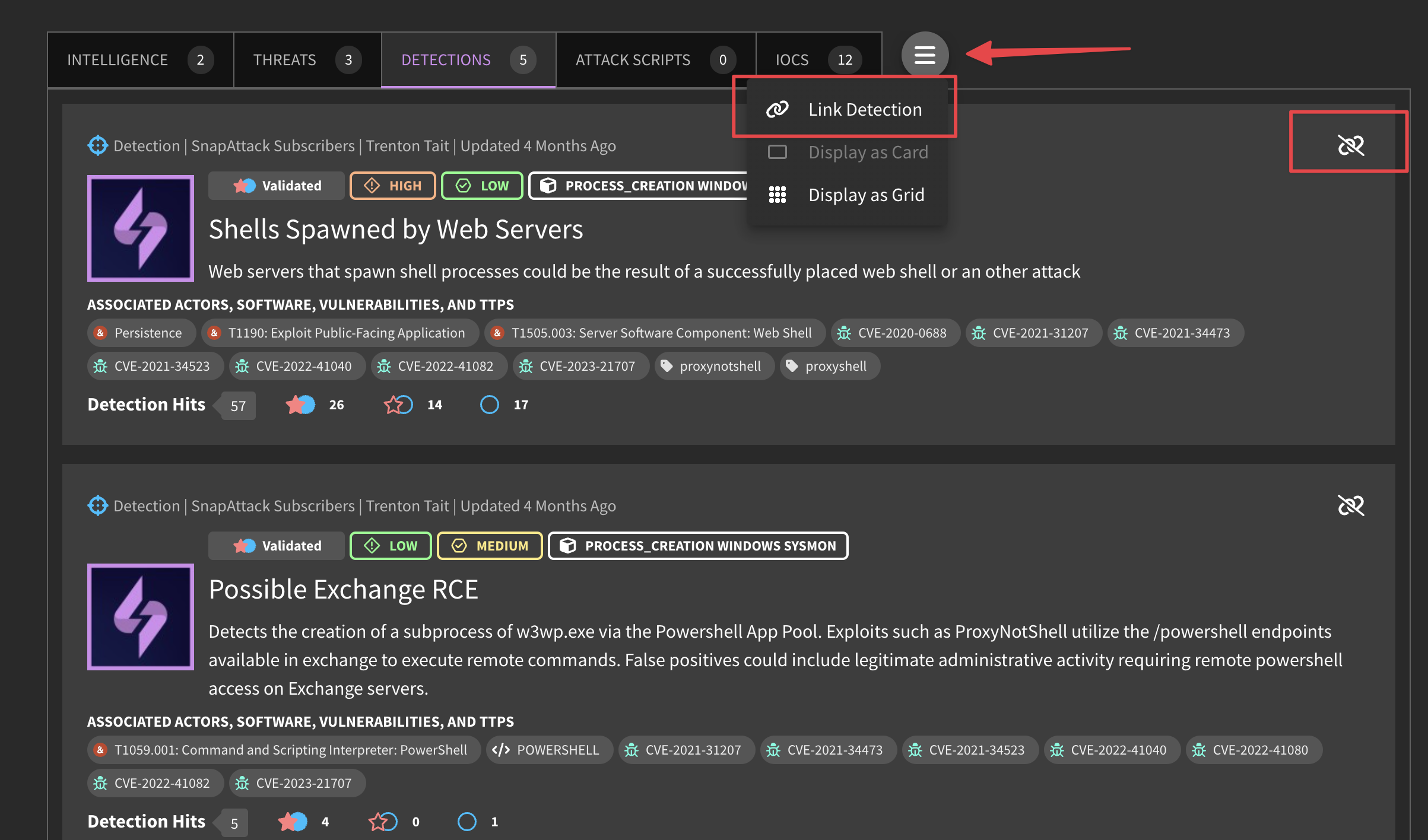
Linked content items can be added from the view page by clicking the hamburger menu on the content type, then selecting "Link [Content Type"]. This will bring up a modal where you can search and link content by type. In order to unlink content, you have to go to the edit intelligence page (hamburger menu at the top of the page), and click the unlink icon next to the linked object you want to remove. Note that content that is automatically linked by a shared reference URL cannot be removed.
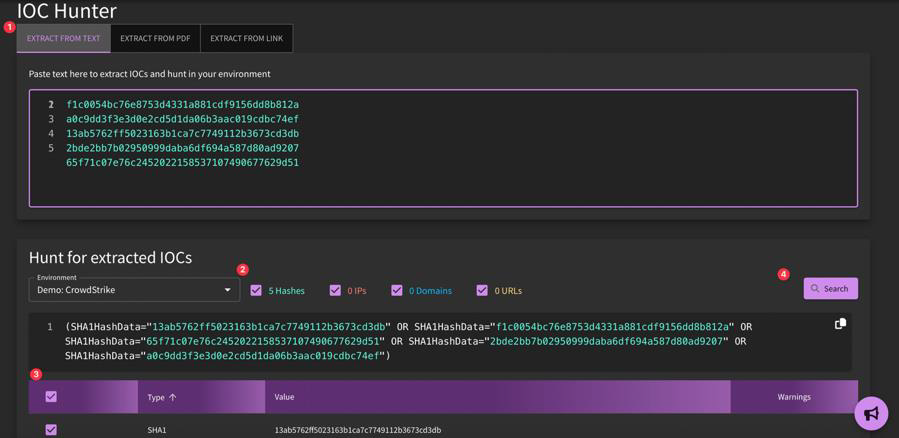
IOC Extraction via IOC Hunter
SnapAttack users can utilize IOC Hunter to automatically extract IOCs from intel whether they are a PDF, URL, or raw text. IOCs such as domain names, IP addresses, and hashes will be color-coded by type. Once the extraction process is complete, you can hunt the objects in your existing tooling.
Curated Collections
Intelligence on threat groups, malware/tooling used for adversarial purposes, vulnerabilities, and MITRE ATT&CK techniques are made available as part of SnapAttack's curated collections. Refer to Research and Collections for more on curated collection pages.