Research
For a walkthrough on how to interact with SnapAttack's Research categories, check out our tutorial below.
SnapAttack's Research tab, as the name suggests, provides a dedicated space for collated research collections. After clicking on the "Research" drop-down, you will see that various sub-categories are listed. Each landing page has a specific research focus, as outlined below:
-
ATT&CK Techniques: Collections on MITRE ATT&CK techniques (e.g., T1566: Phishing)
-
Threat Actors: Threat groups (e.g., APT28)
-
Software: Malware/tools used for adversarial tradecraft (e.g., MIMIKATZ)
-
Vulnerabilities: Notable vulnerabilities (e.g., CVE-2021-44228)
-
Collections: Collections that are not tied to a specific top-level category; custom collections (e.g., CISA - Known Exploited Vulnerabilities)
-
Intelligence: Repository of open-source intelligence articles (e.g., "Proxy Trojan Targets macOS Users for Traffic Redirection")
Common Use Cases
-
Threat Intelligence: Included in the Research tab is the Intelligence tab, so CTI analysts can easily access the open-source intelligence feeds that are part of the repository. Additionally, intelligence objects are included in collection landing pages to provide a contextual element to the topic of choice.
-
Detection Engineering: Detection engineers can use collections to manage various workflows, like a collection of backlogged intelligence or red team threats that need new detections created, or a collection of detections that need tuning. Additionally, the recommendation engine provides a one-click deploy feature for top content, streamlining the deployment process.
-
Threat Hunting: Hunters can create hunt plans around specific tradecraft and activity, making it easy to re-run a hunt from the collection in the future. On top of that, the recommended hunt opportunities provide an "easy button" for threat hunting efforts.
-
Red Teaming: Red teams can memorialize tradecraft, then collate this information into a collection for detection engineers to build upon potential detection opportunities. As with detection and hunt content, the recommendation engine provides red teamers with recommended attack scripts to run to simulate threat activity.
-
Purple Teaming: Collections can organize red and blue team activity, track which threats have detections, and which ones need to be created.
Other Features
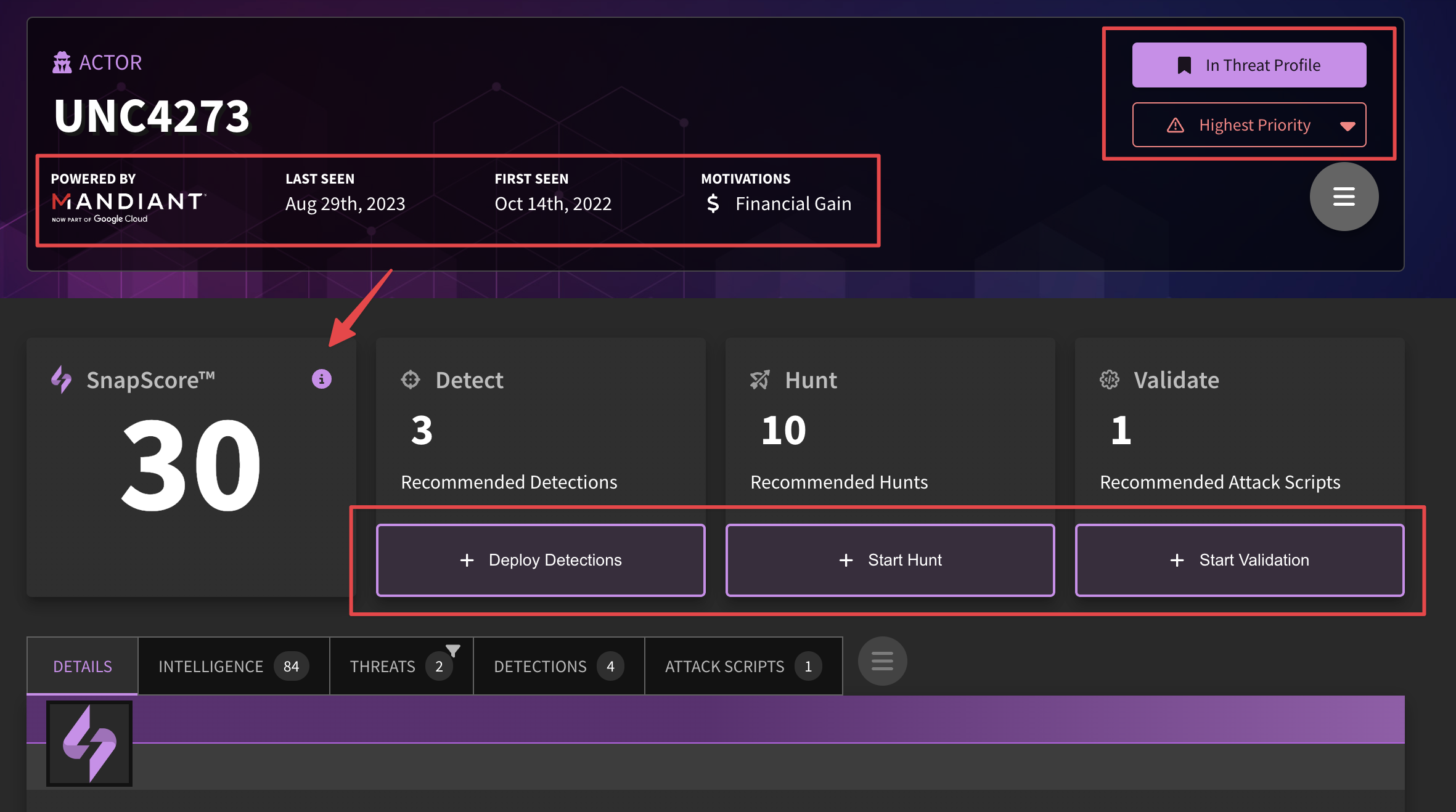
Threat Profile
When clicking into a topic's page, you may notice that it is consider "In Threat Profile" or not, and it has a default priority assigned to it. Under "Settings", you will see that you can choose which content is most relevant to your organization (see threat profiles for more information). Anything that matches these criteria will be included in your Threat Profile, thus assigning the automatic "In Threat Profile" flag. Of course, if you'd like to manually include or exclude content from your profile, you may check/uncheck the box. Similarly, if the priority assigned to a particular item is not appropriate, you may adjust as needed.
Recommended Actions & SnapScore
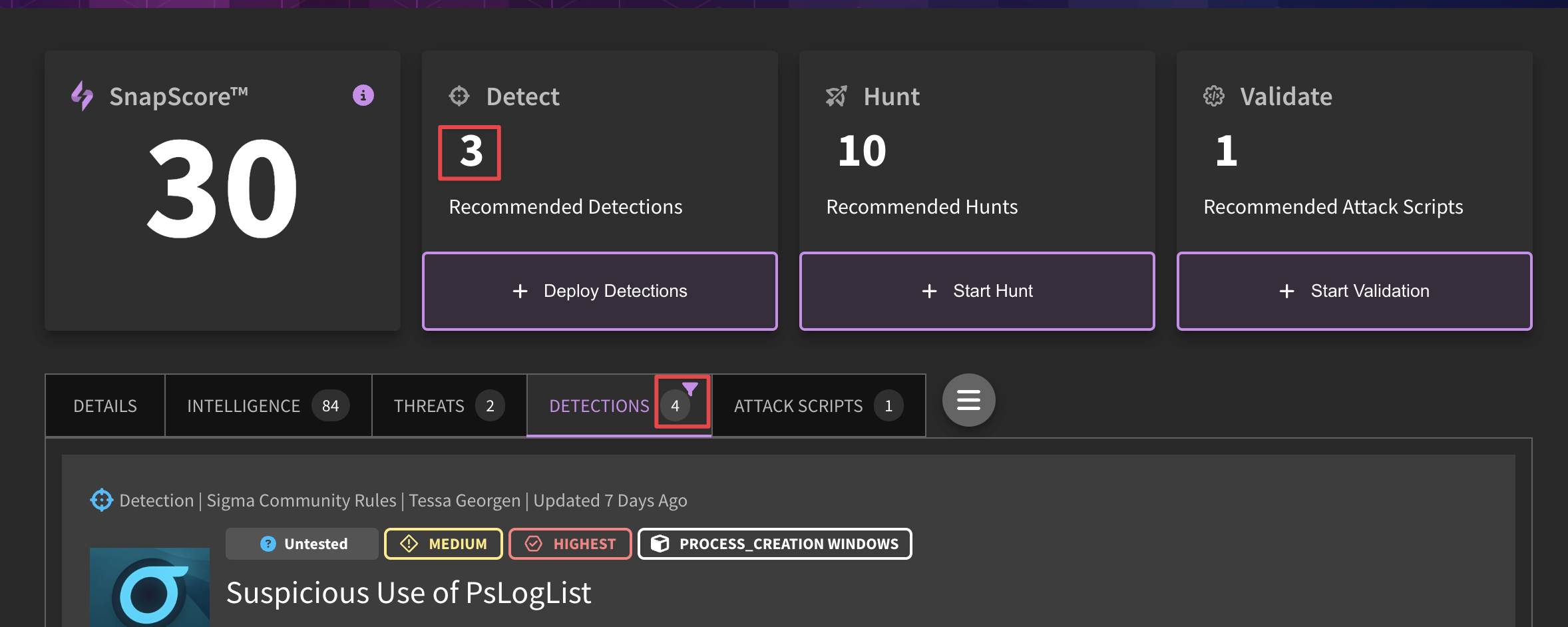
You may have noticed that the SnapAttack platform has a built-in recommendation engine to kick off detection deployments and threat hunts, as well as run attack scripts. These recommendations are based on an internal algorithm tied to most relevant content for your organization. As you can see in the image, there are four available detections for this particular example, though only three of them are recommended. The SnapScore to the left illustrates how well covered your organization is against this threat group, malware type, CVE, etc. The more you deploy/hunt/launch attack scripts, the better your score will be.
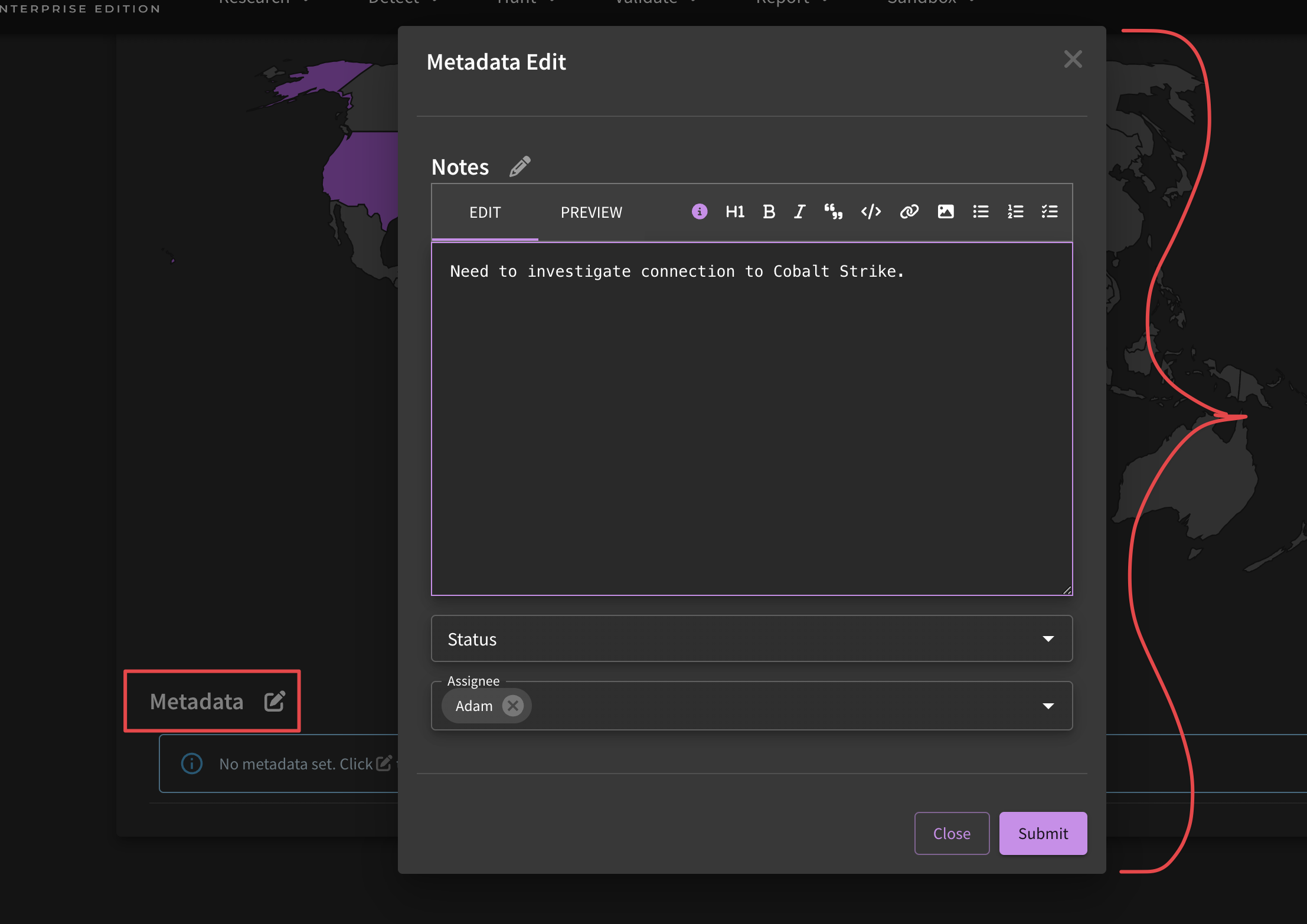
Metadata
To assist you in your workflow needs, you can include additional metadata on these research pages. A few ways in which you could use this is by assigning team members content to investigate (Jira-like workflow), embed organization-specific notes (IR Guidelines, Other Resources, etc), or even content development life cycle (In-development, Needs Review, Deployed, etc).
Tags
When you click into a topic's page, you will see associated tags. Note that the tags are drillable; you can navigate to related topics as you work through your research process.
There is also a built-in mini MITRE ATT&CK coverage map so you can visualize what techniques are related to the topic in question.