Settings
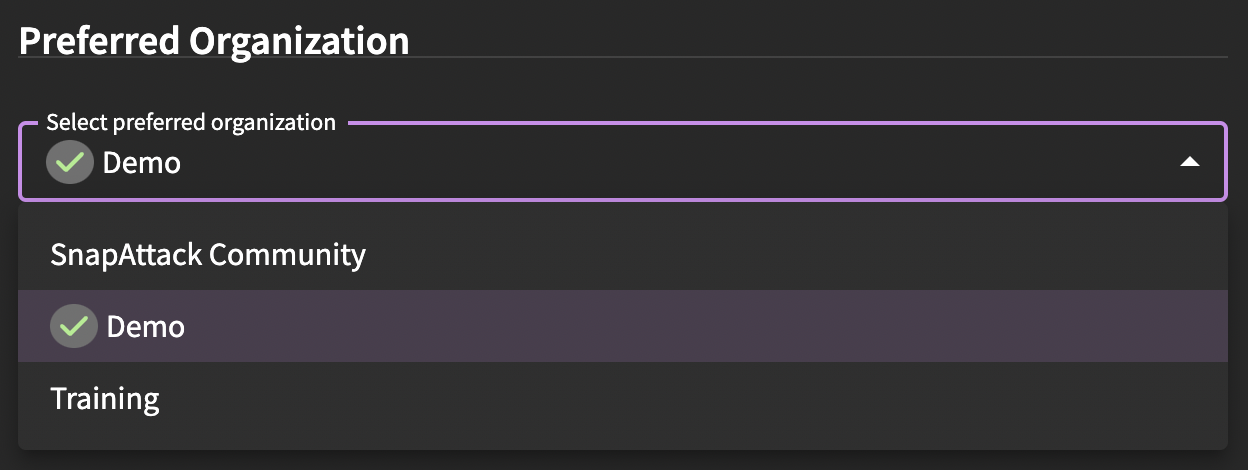
Preferred Organization
An organization is a group of common users. Enterprise subscribers have their own private organization, as well as access to other organizations for subscription content. All platform users have access to the community organization, which grants access to community content. Generally speaking, most users will not have to change this setting.
For users with access to multiple organizations, you can set a preferred organization. This affects what a user sees and how you interact with the platform:
- The default organization for publishing new content
- Integrations and languages you see for detection translations
- Detection confidence and severity values, if they have been overridden for that organization
- Detection workflow and deployment state
- Dashboard and reporting values, such as the detection dashboard
There ia also a special Training organization. This is an isolated sandbox where threats can be uploaded and detections can be written without affecting other organizations.
User Management (Organization Administrators Only)
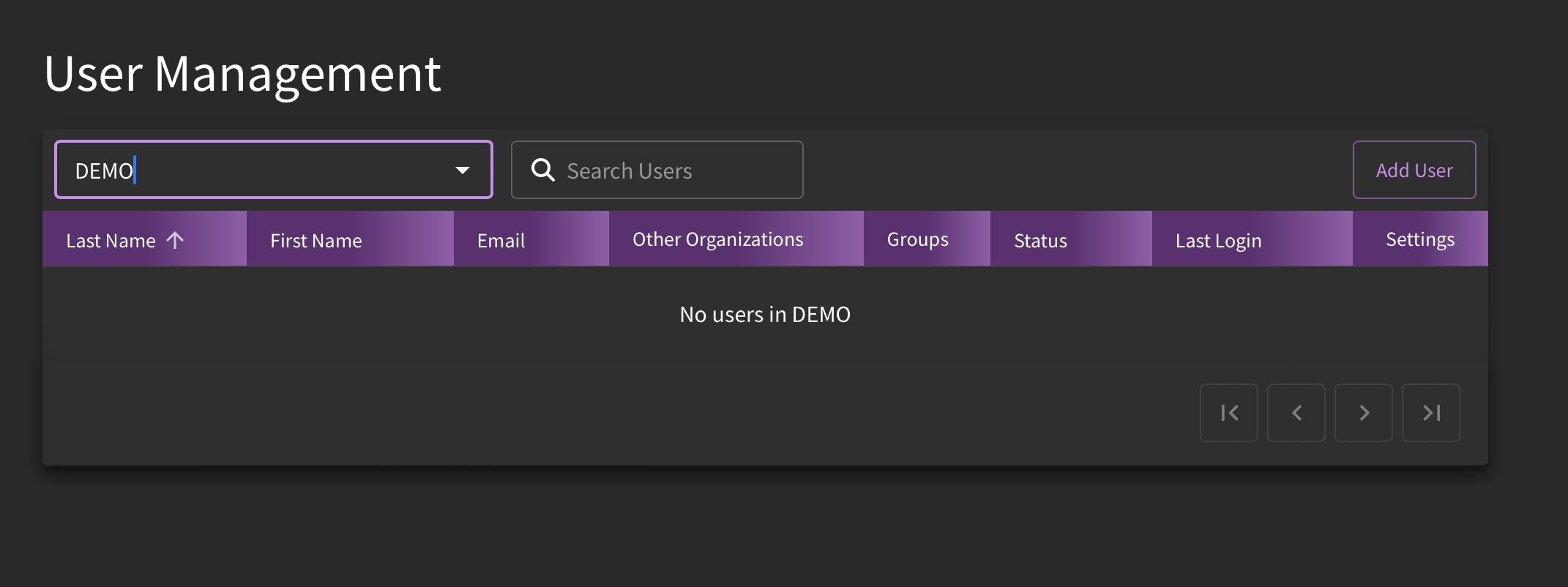
If you have organization admin privileges, you can control who is part of your organization's user group by clicking on Settings → "User Management". Either click "Add user" in the right-hand corner or "Remove user" after clicking on the gear icon next to the user you would like to remove.
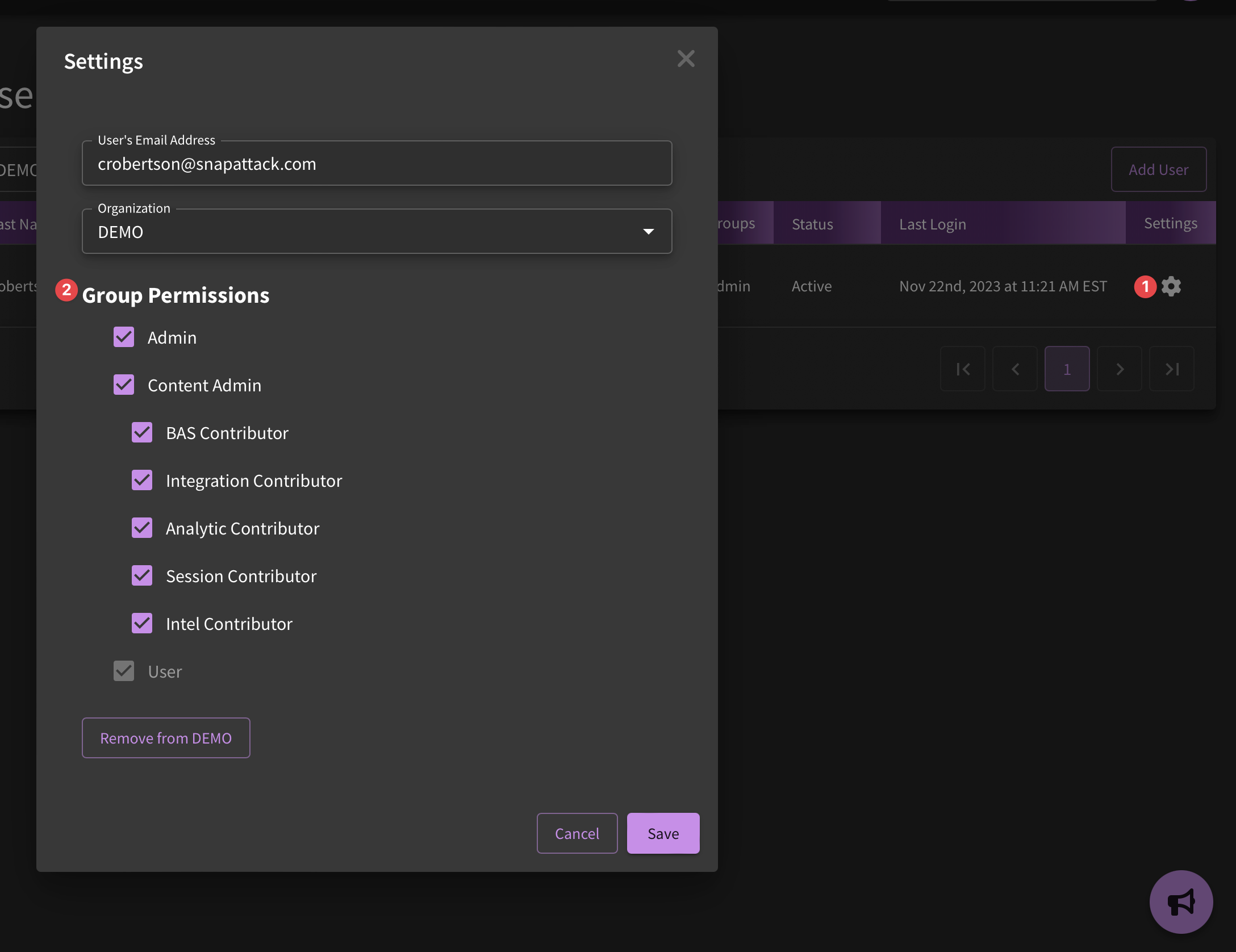
Note that there are distinct categories related to permission levels. The following defines what each level is able to do within the platform:
- Admin: Full organization administrators can add or delete users in an organization, and establish default settings at the org-level
- Content Admins: This permission level lets a user add/modify/delete any content in the system (intelligence, threats, detections, attack scripts, collections, etc.) owned by the organization.
- Content Contributors: gives a user add/modify/delete permissions over a more limited set of content items.
- BAS Contributor: allows a user to use our Validate agent for attack simulation activities.
- Integration Contributor: allows a user to add/modify/delete an integration and its settings.
- Analytic Contributor: allows a user to add/modify/delete detection content, change the severity or confidence level, and deploy detections through their integrations.
- Session Contributor: allows a user to use our CapAttack agent or sandbox attack range for capturing threats.
- Intel Contributor: allows a user to add/modify/delete intelligence objects.
- User: This permissions level establishes "read-only" access; that is, they will not be able to add/modify/delete content.
As illustrated in this image, there are no current users in the organization "DEMO". To add new members, click on the "Add Users" button.
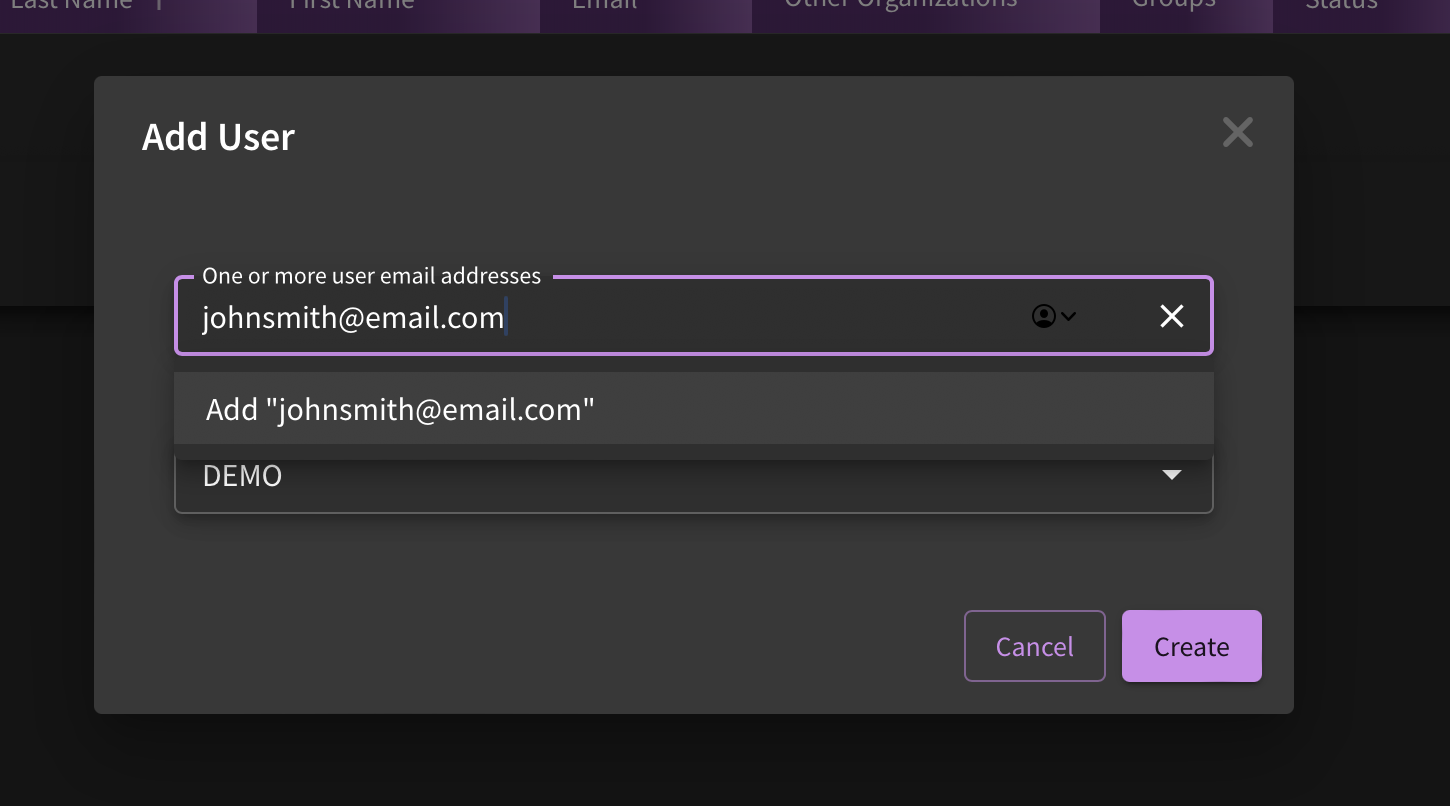
To add users, type in one more email addresses, remembering to click enter after each entry. Click "Create". This will send an automatic email notification to the member(s) added.
This image illustrates what permissions levels someone with admin-level access has. To determine what permission levels are needed for your organization, reach out to the SnapAttack Team. You will be able to set up default permission levels for new users under "Organization Management" (more on that later).
Organization Management (Organization Administrators Only)
Once again, SnapAttack users who have "administrator" level permissions for their organization will be able to manage organization-level information. This includes making changes to platform users (adding, removing) and changing their permission levels, as well as enabling up default settings such as default languages, filters, and even default permission levels for new users.
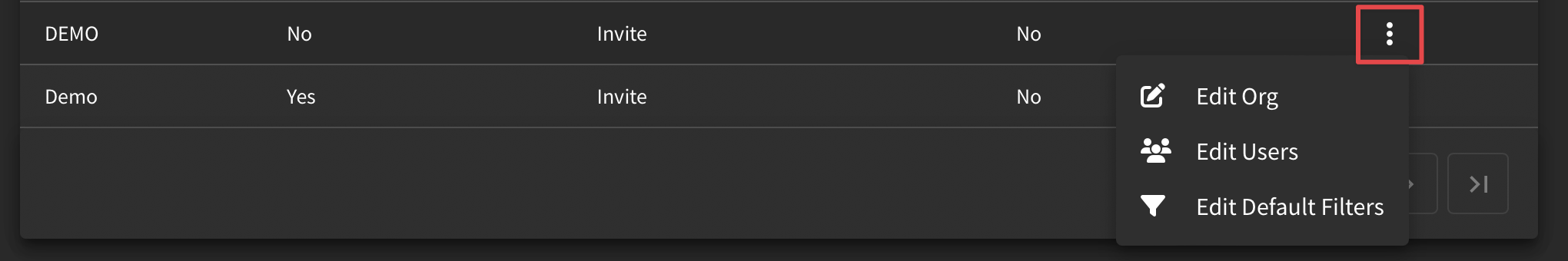
To access the Organization Management page, click Settings → Organization Management. After doing so, you will see your organization listed in the drop down menu ("DEMO" is used in this example). Take note of the three dots which will provide you with three options: "Edit Org", "Edit Users", and "Edit Default Filters".
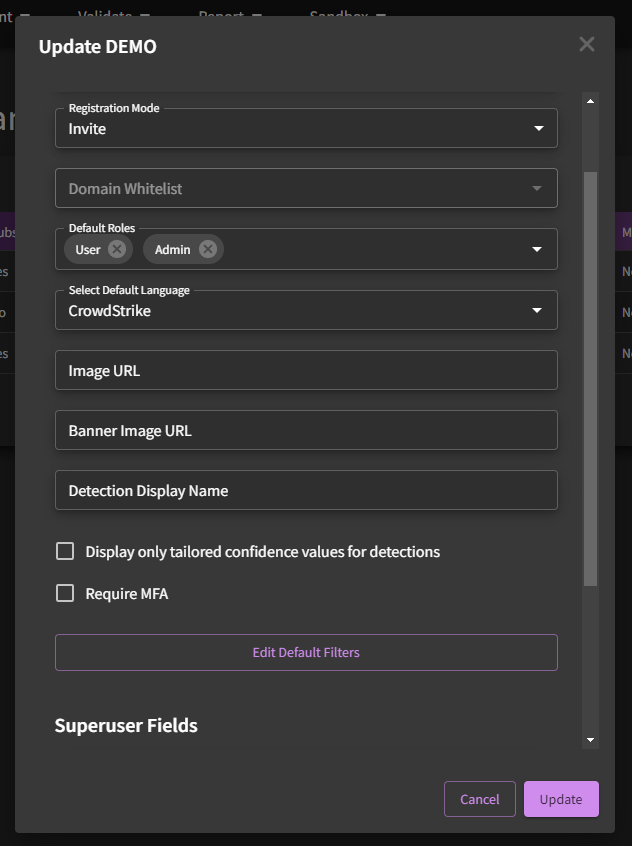
If you would like to make changes to organization-level default settings, click on "Edit Org". As illustrated below, you can enable default permission levels that will be assigned to new users upon their first login.
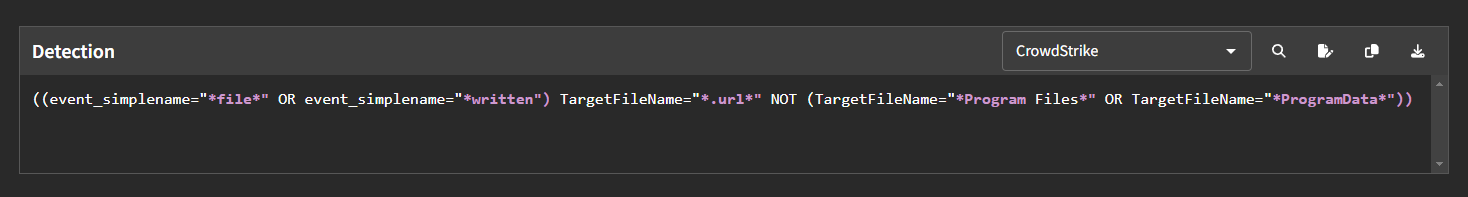
Additionally, you can set up a default detection language which will be the first detection language that our IDE or embedded no-code detection content widget that you see. You can do this by clicking on the drop-down menu under "Select Default Language". If you selected "CrowdStrike", for example, you would see the following:
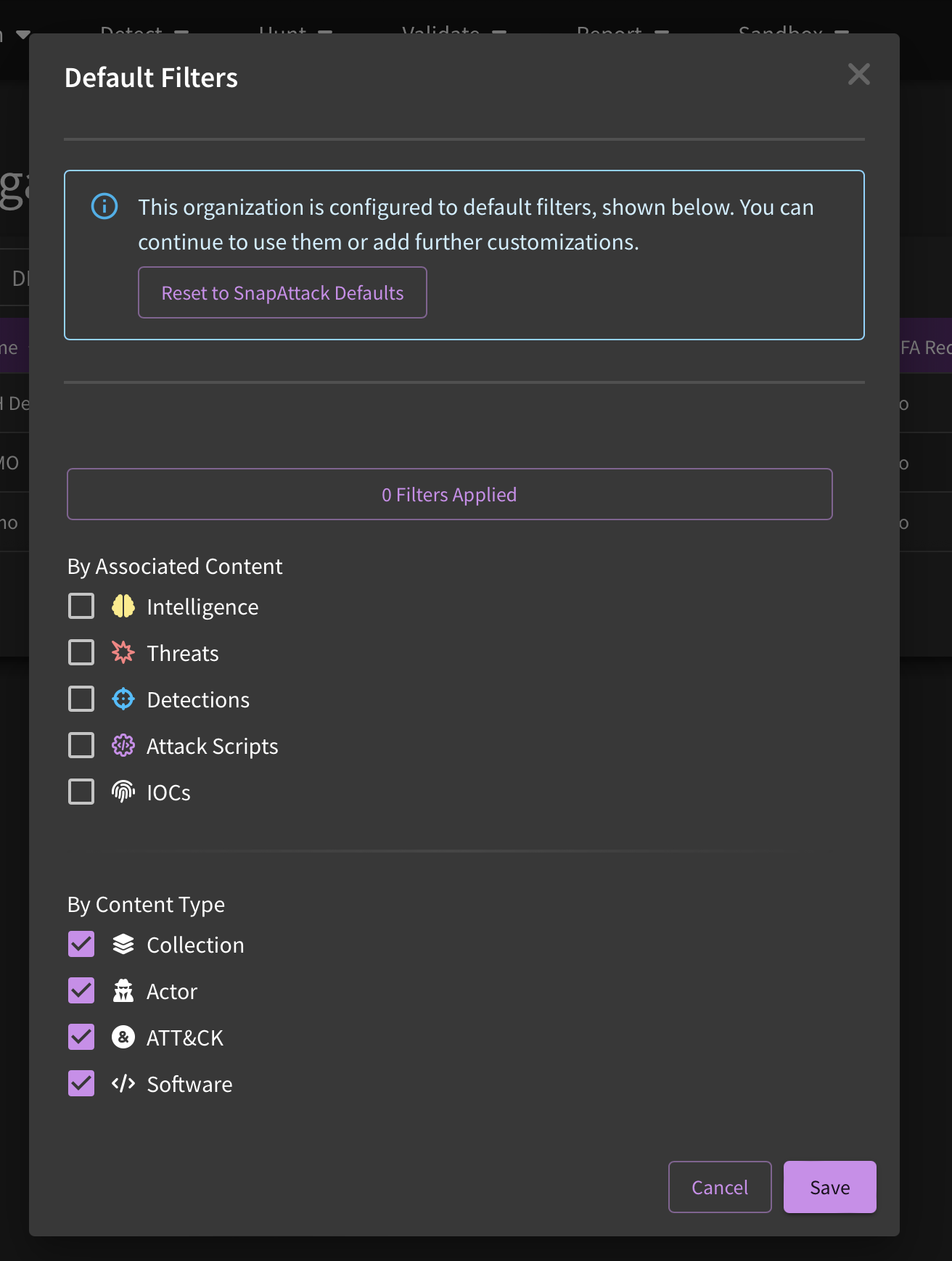
Another setting that administrators can manipulate on this page is setting up default filters. This is especially useful for those who are not interested in seeing content that isn't compatible with their tooling. Using the CrowdStrike example again, administrators can set up automatic filtering of anything not compatible with CrowdStrike, which would allow analysts to find what they need a little bit easier.
Note, also, that you can select which landing pages the default filtering will be applied to. If you would severity levels, detection confidence, detection languages, etc. to only be applied to the detection library landing page, you can designate that as needed.
API Keys
Enterprise subscribers have access to the SnapAttack API. This allows users to perform advanced actions and integrate SnapAttack with other tools. API documentation is available at https://app.snapattack.com/api/docs (authentication required). This is the basic API documentation that supports the most common platform use cases. If there are features that you are using in the platform that you don't see API endpoints for, feel free to reach out to us and we can provide additional API documentation.
To create an API key, you'll need to go to Settings → API Keys. You can select one or more scope for what permissions you want to grant the API key. Common scopes include:
- Detection Deployment - used by EDR, SIEM, and other tool integrations to manage detections from SnapAttack
- Attack Simulations - used by our BAS agent to simulate threats in your network
- Local Threat Capture - used by CapAttack to capture threats in your network and upload them to SnapAttack
- REST - access to the full REST API
To use the API keys, you'll need to set the X-API-Key HTTP header. Note that all API endpoints require a trailing slash. You may notice a redirect if you attempt to access an endpoint without a trailing slash.
Example:
curl -H "X-API-Key: <your API key>" -X GET https://app.snapattack.com/api/tags/