Threat Profiles
Cyber threat profiling plays a critical role in safeguarding businesses, especially as security leaders are asked to do more with less. By systematically analyzing and understanding the tactics, techniques, and procedures employed by malicious actors, threat profiling can proactively identify and prioritize the highest risks to the organization. This proactive approach allows for better preparedness, quicker incident response, and enhanced overall cybersecurity. Furthermore, cyber threat profiling helps in the allocation of resources and the development of tailored security strategies, enabling organizations to stay one step ahead of cybercriminals who constantly evolve their methods.
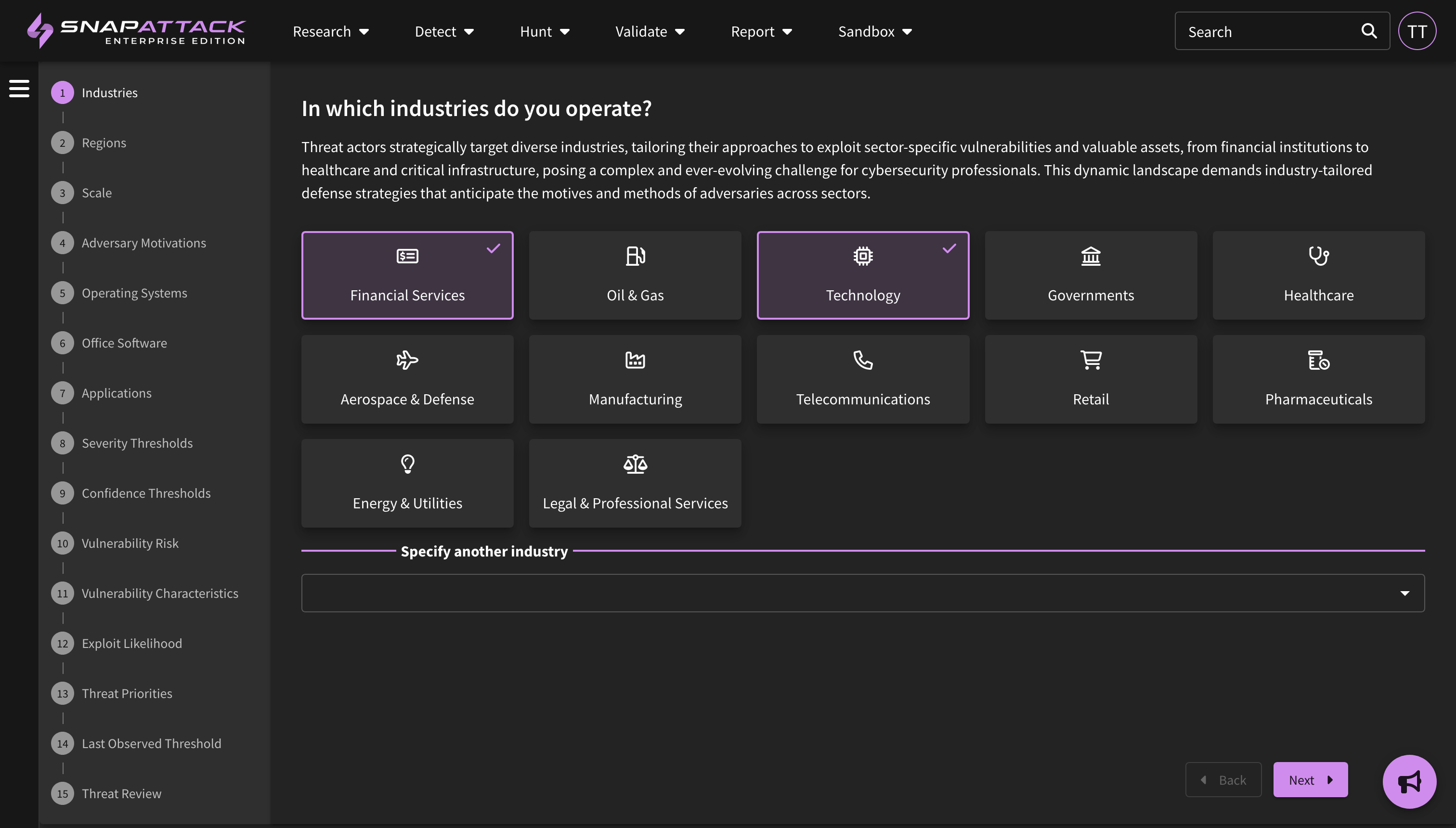
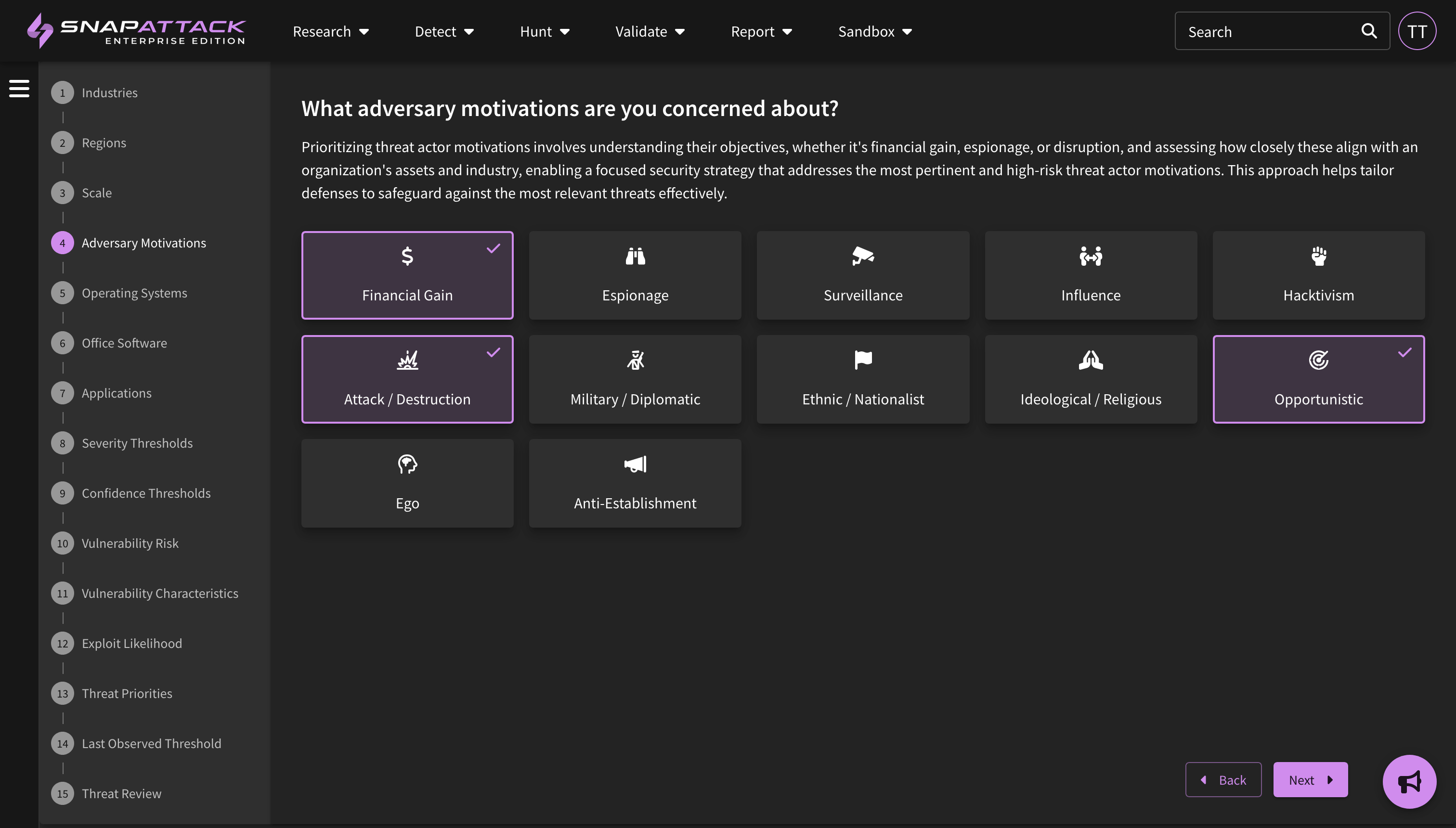
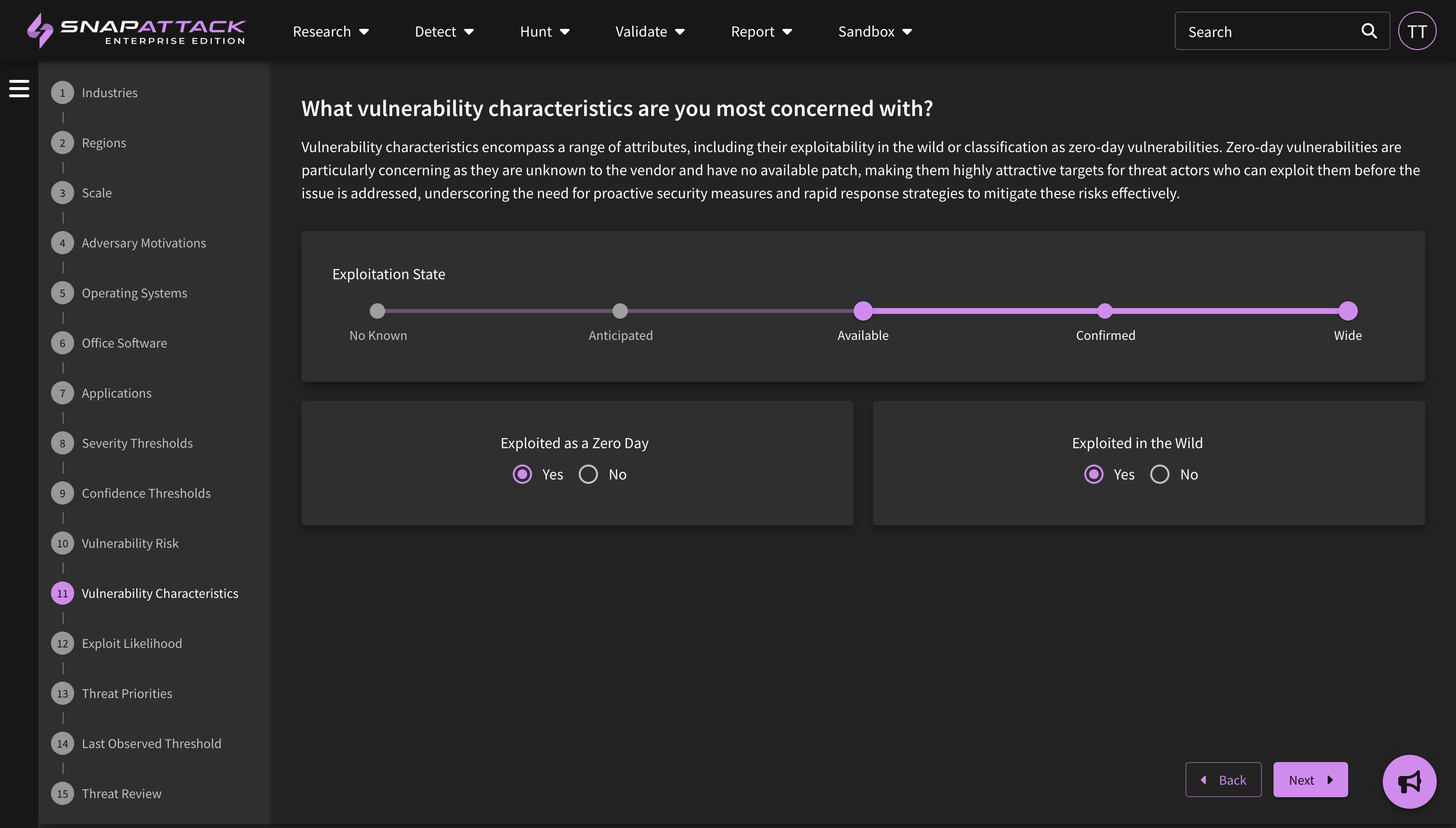
SnapAttack can help your organization stay ahead of cyberattacks with automated threat profiles based on your organization's firmographics and leading open-source threat intelligence. We combine information about your organization - such as the industry, company size, operating systems, cloud platforms, and applications used - with intelligence on threat actor motivations, the malware and techniques they commonly use, vulnerability characteristics and exploit likelihood - to create a threat profile custom tailored to your organization with the threats individually prioritized. This helps cut through the noise, as most "newsworthy" or trending intelligence isn't actionable or often relevant to most organizations.
Creating a Threat Profile
Users are encouraged to complete the threat profile questionnaire when onboarding to the platform. This can be found in Settings → Threat Profile. This can only be configured by an organization administrator or content administrator.
At the end of this process, a threat profile is built for your organization. Relevant actors, software (malware/tools), ATT&CK techniques, and vulnerabilities are added to your threat profile and scored based on the inputs of the questionnaire. For example, if you said that you care about financially motivated actors, your organization primarily operates in the United States, and you have a Windows environment, you'll get recommendations on the for the most common tools and TTPs used by ransomware groups that fit those criteria.
Your threat profile will continuously evolve and improve. New items will added as intelligence changes; older items will reduce in priority or may drop off entirely if no longer relevant. This will happen automatically based on the criteria defined by your organization.
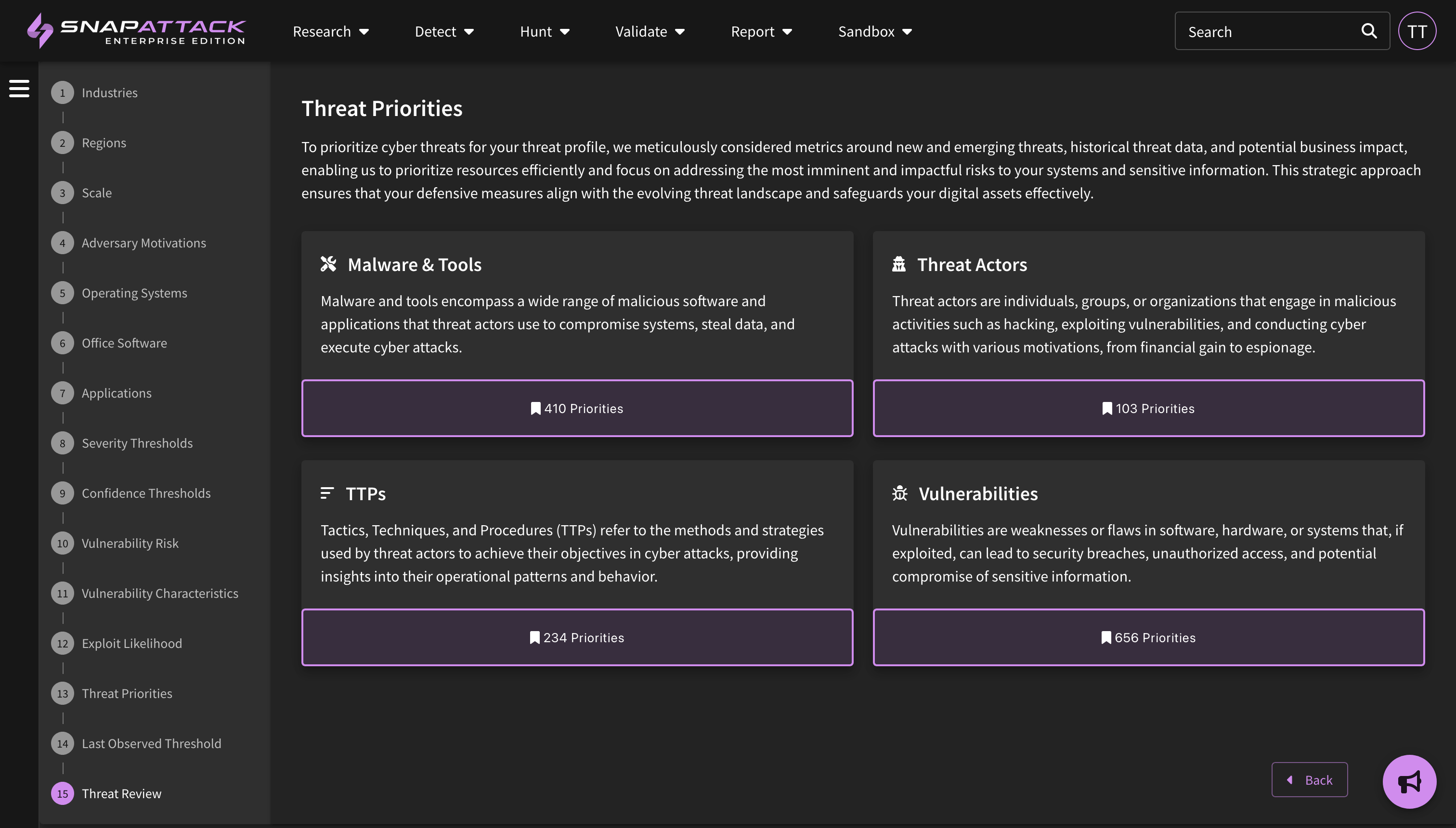
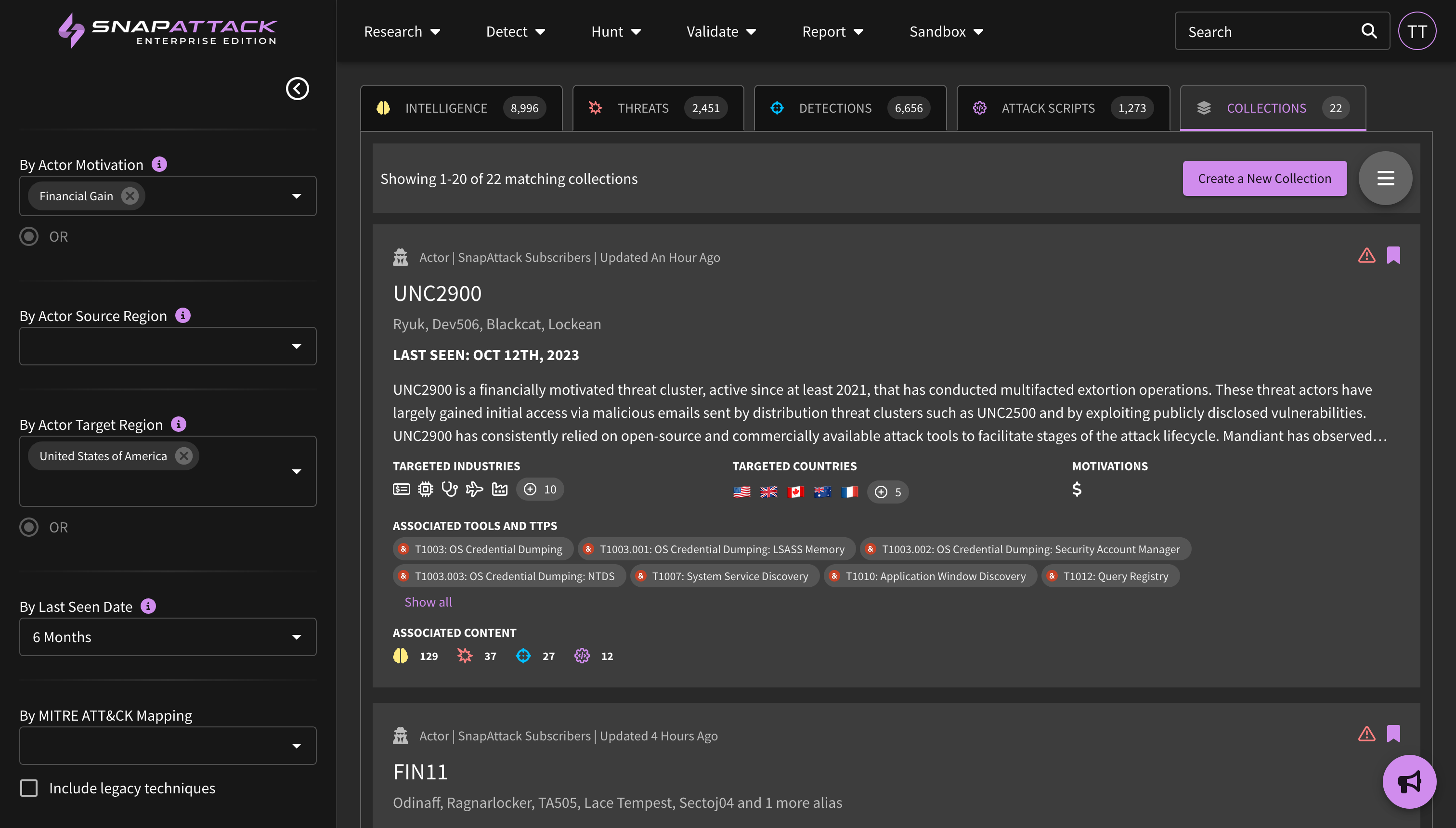
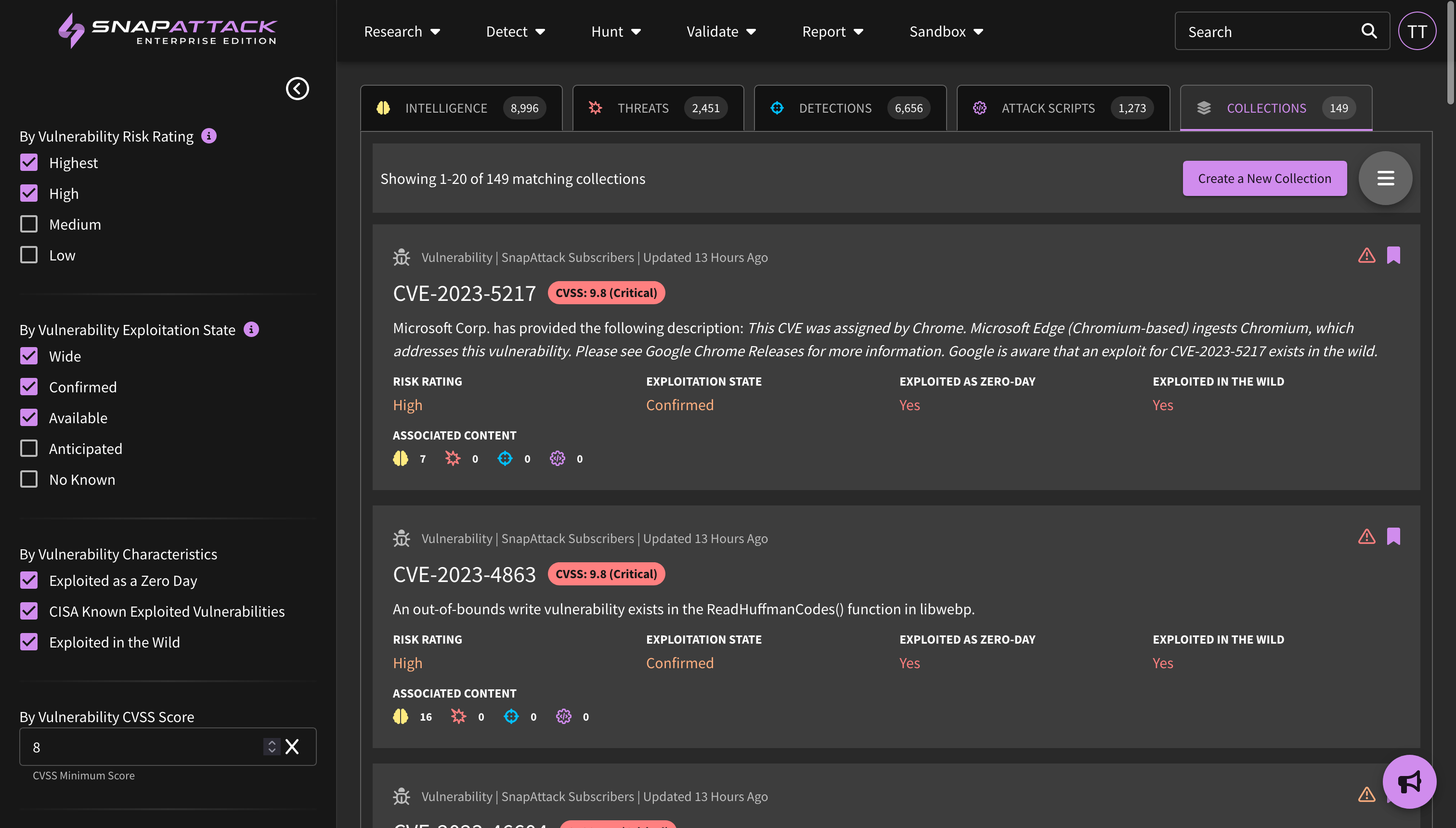
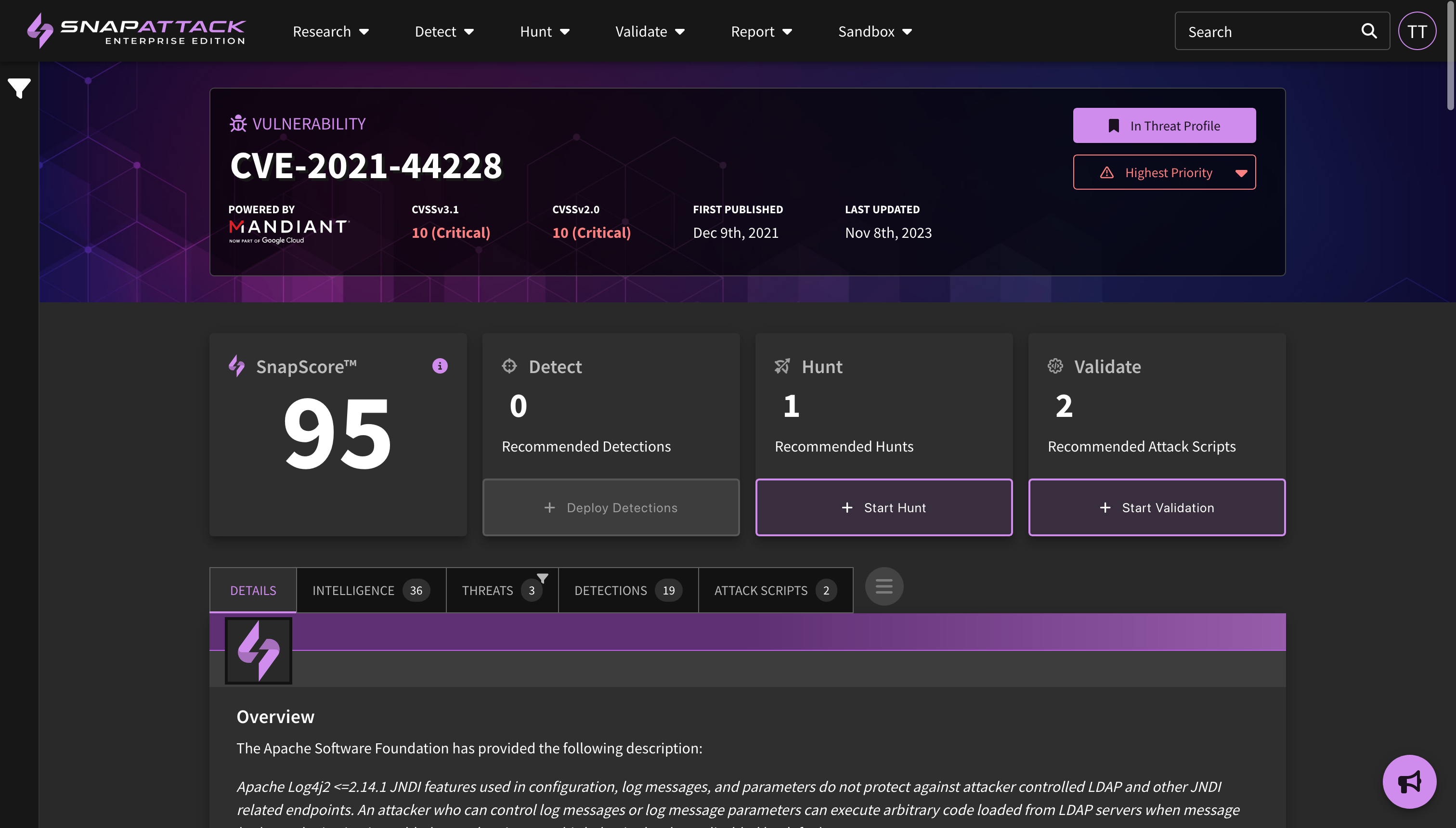
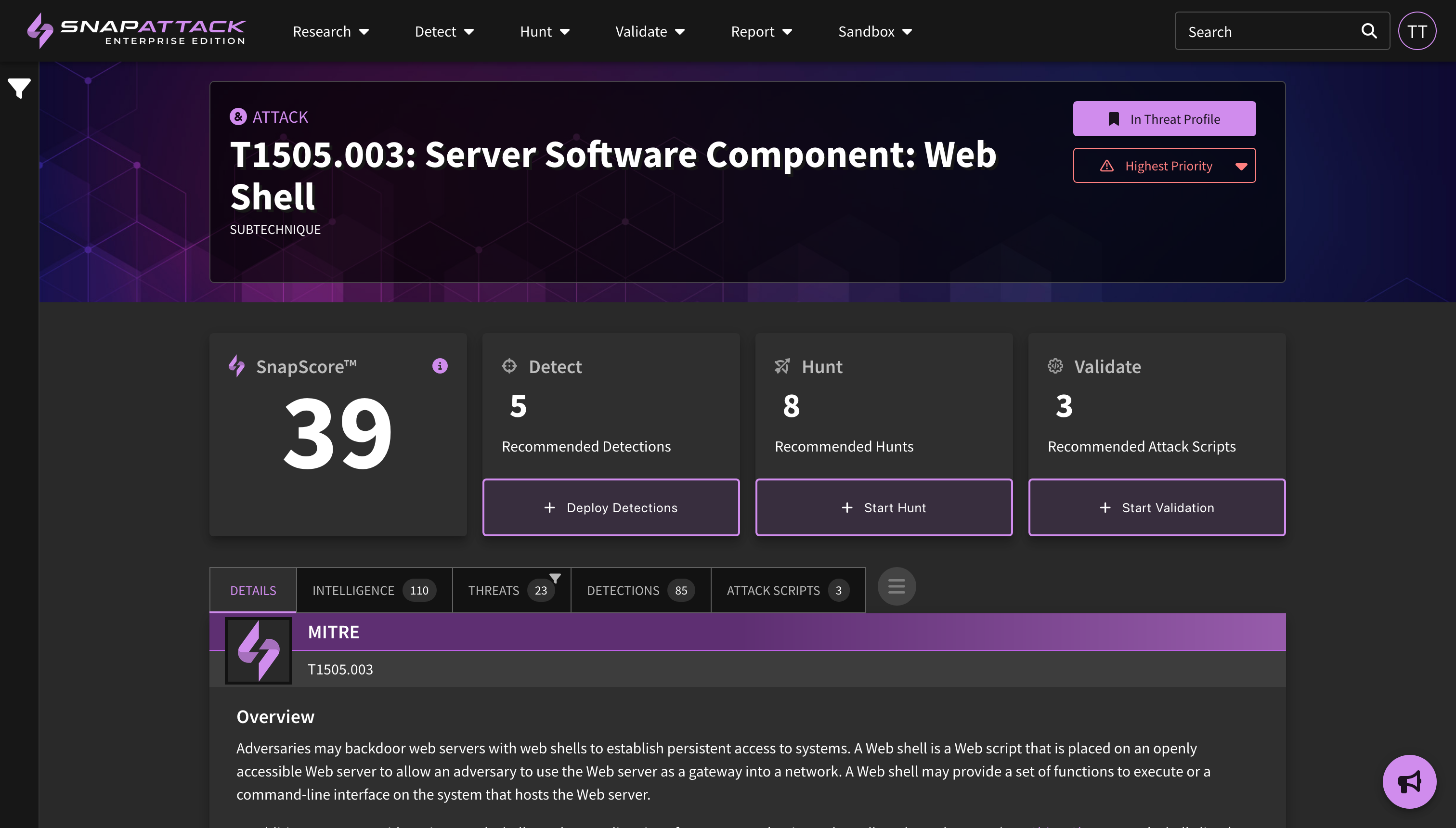
Viewing Threats in your Profile
The feed has been updated to display additional information about actors, software (malware/tools), ATT&CK techniques, and vulnerabilities. This information can be filtered (e.g., "show me CVEs that are actively exploited in the wild"). Users can also filter items that are included or excluded from their threat profile, and can see where they are prioritized in their profile from a scoring of Highest → Lowest. We suggest that users tackle the highest priority items and work their way down.
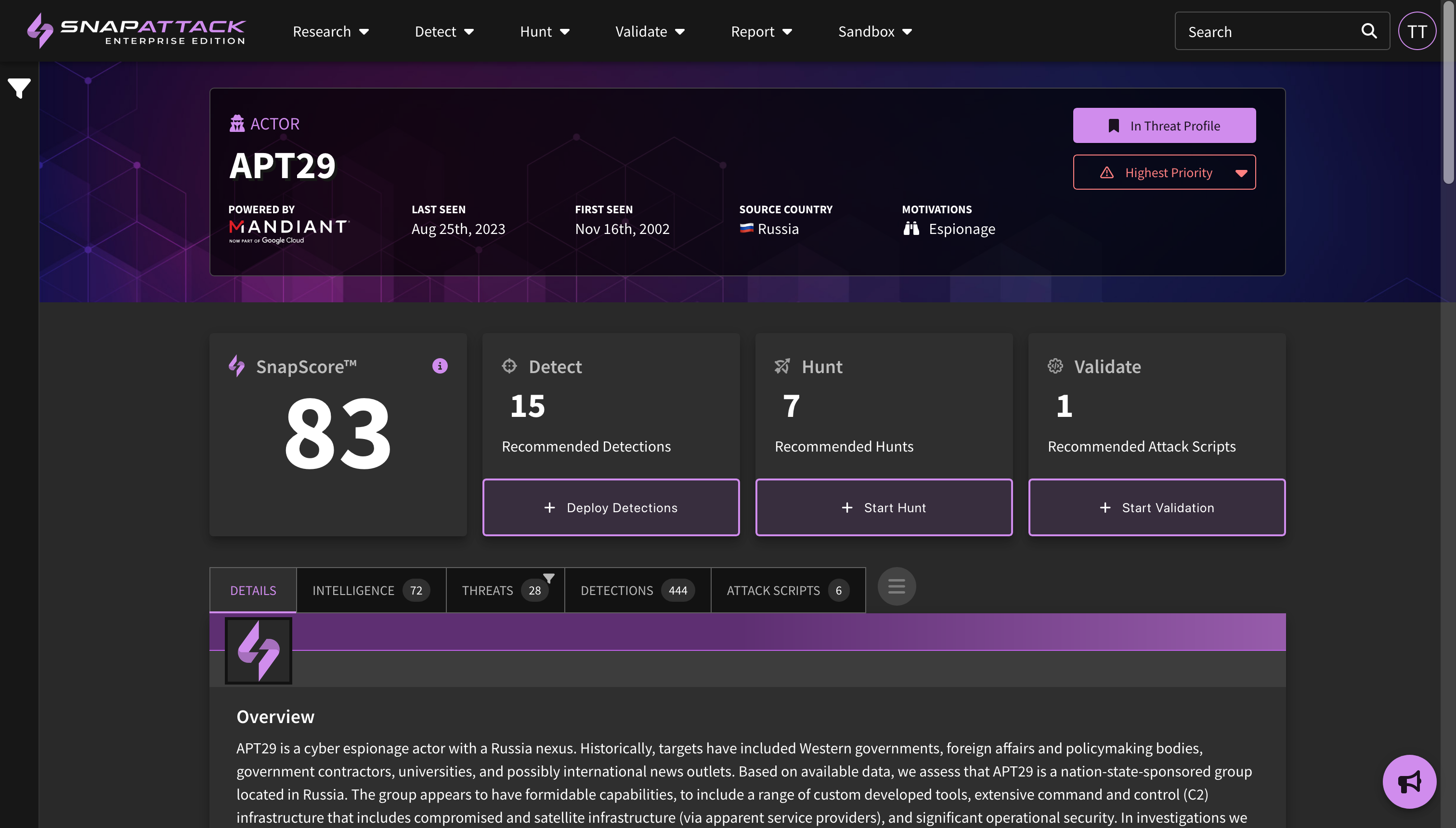
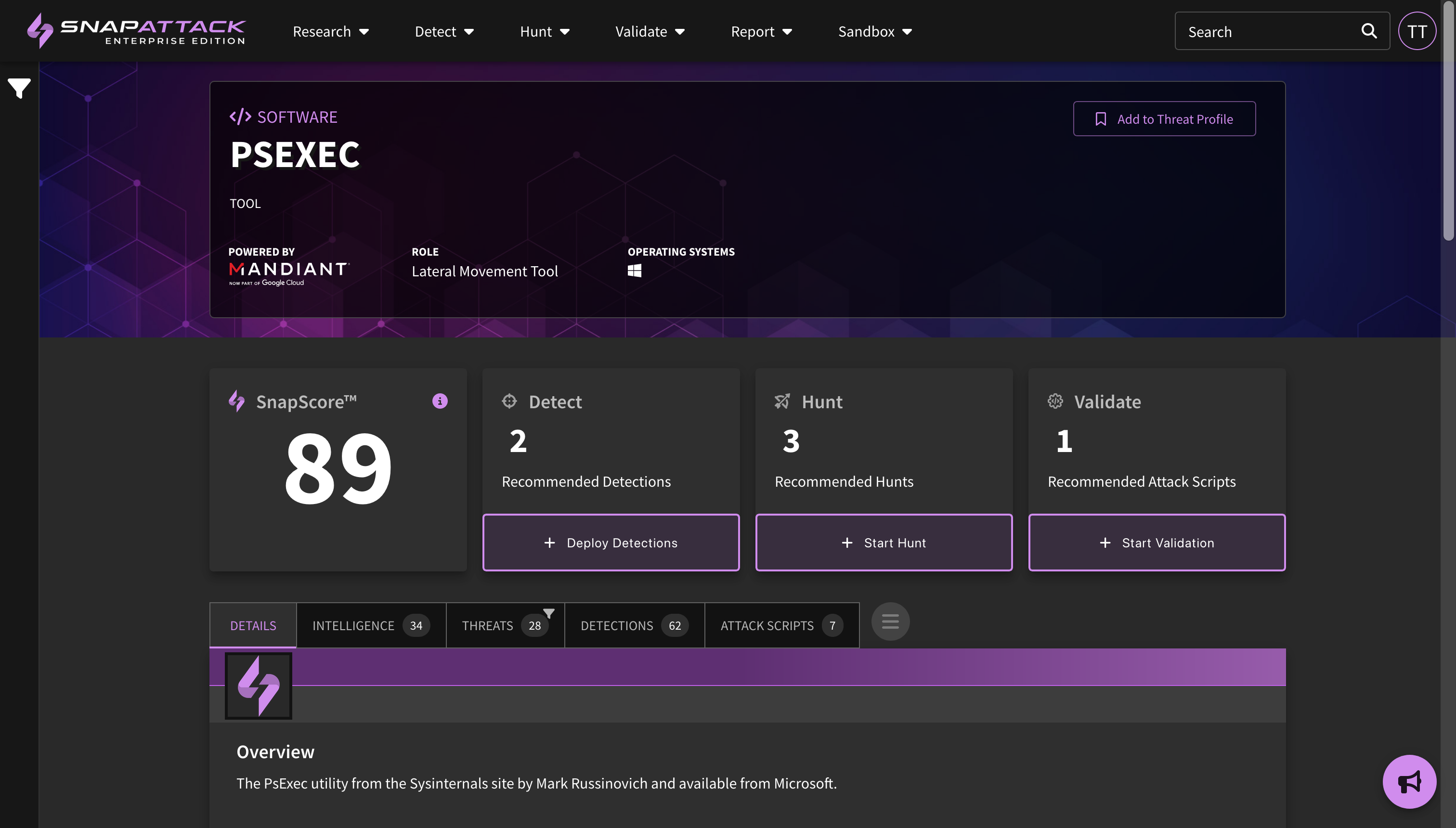
Actioning Threats in your Profile
On an individual actor, software, ATT&CK techniques, or vulnerability page, a user can see if an item is inside their threat profile and its priority. They can also change or override those values if desired. There are also recommendation panels that suggest detections to be deployed or hunted, or attack scripts to be run. Completing these actions will result in an improvement to your SnapScore, which is an assessment of how prepared your organization is against that specific threat based on the data available to SnapAttack.
FAQ
Q: Do I have to complete every item in the threat profile questionnaire?
A: No, but the more data that you provide, the more comprehensive and complete your recommendations will be.
Q: What happens if I add or remove items in my profile, or change the prioritization?
A: Items explicitly added or removed from your threat profile, and prioritization manually specified by your organization, will not be touched by our recommendation algorithm. A future update will expose a way to "reset" this override to let the algorithm alter the values.
Q: A threat was in my profile yesterday, but isn't there today, or the prioritization changed. What happened?
A: Our algorithm is continuously evaluating knowledge of threats in your profile. We recalculate your profile nightly, and each time you complete the questionnaire.
Q: How do you determine recommended detections, hunts, and attack scripts?
A: Recommended detections are ones that are compatible with one or more of your integrations, have a medium to highest severity, and have been validated. Detections are also deduplicated based on the observed similarity of the threats and individual logs that they hit on from our threat library. Since we use the detection confidence scores to bucket them into recommendations for deployment (as alerts) or to be hunted, we suggest organizations complete a confidence tailoring exercise at least once, and configure a recurring confidence tailoring task so that new detections will be evaluated and existing detections will have their confidence values updated as needed/ Compatible attack scripts that are known to trigger one of the recommended detections or hunts be recommended as a means to validate your detection capability. Recommendations for hunts and detections will go away after they have been performed, and reset every 90 days.
Q: What is SnapScore? How does that work?
A: SnapScore is a measure of how prepared you are against a specific threat. It uses knowledge of the threat from open-source intelligence and our own knowledge from our threat, detection, and attack script libraries. Completing the recommended actions for detections, hunts, and attack scripts will increase your SnapScore. Your score may decrease as recommendations change, or the impact of your hunts/attack simulations have aged off. This score is a measure of what SnapAttack knows about this threat and your environment. A score of zero does not mean you aren't protected by other security controls. A score of 100 for each threat should not be the goal. If you arrive on a page and see an existing score, that means you've already actioned some of the recommendations - either for this threat specifically, or through another threat in the system (e.g., powershell is commonly used by actors, so deploying powershell detections may improve your SnapScore across multiple pages).
Q: Can I see recommended detections, hunts, or attacks scripts across all of my threat profiles? Can I sort them by priority so I know which is the next best action to take?
A: Global recommendations are coming soon. We have built our recommendation algorithm from the ground up, starting inside an individual threat session capture, then moving to the threat page, and finally will expose global recommendations. This allows us to apply graph theory and weights to the most commonly connected threats, detections, and attack scripts.
Q: Can I sort my threat profile by priority?
A: You can currently use the feed filters to search actors, software, ATT&CK techniques, and vulnerabilities by their buckets (e.g., Highest, High, Medium, Low, Lowest). On the backend, there is a numeric score for each of these, which will be exposed as a sort order option with the global recommendations update.
Q: Can I get notified as threats are added, removed, or modified in my threat profile?
A: Notifications are a commonly requested feature and prioritized on our roadmap. We plan to offer both in-app and e-mail based notifications for common workflows and functionality, such as when a task completes, new content is added to the platform, or your threat profile changes.