Release Notes
2025.01.04
- SnapAttack, now part of Cisco: As of January 31, 2025, we're thrilled to announce that SnapAttack is now officially part of Cisco. This marks an exciting new chapter following Cisco's December announcement of its intent to acquire SnapAttack. Together with Cisco and Splunk, we look forward to advancing the development of cutting-edge threat detection content and engineering capabilities. Read More.
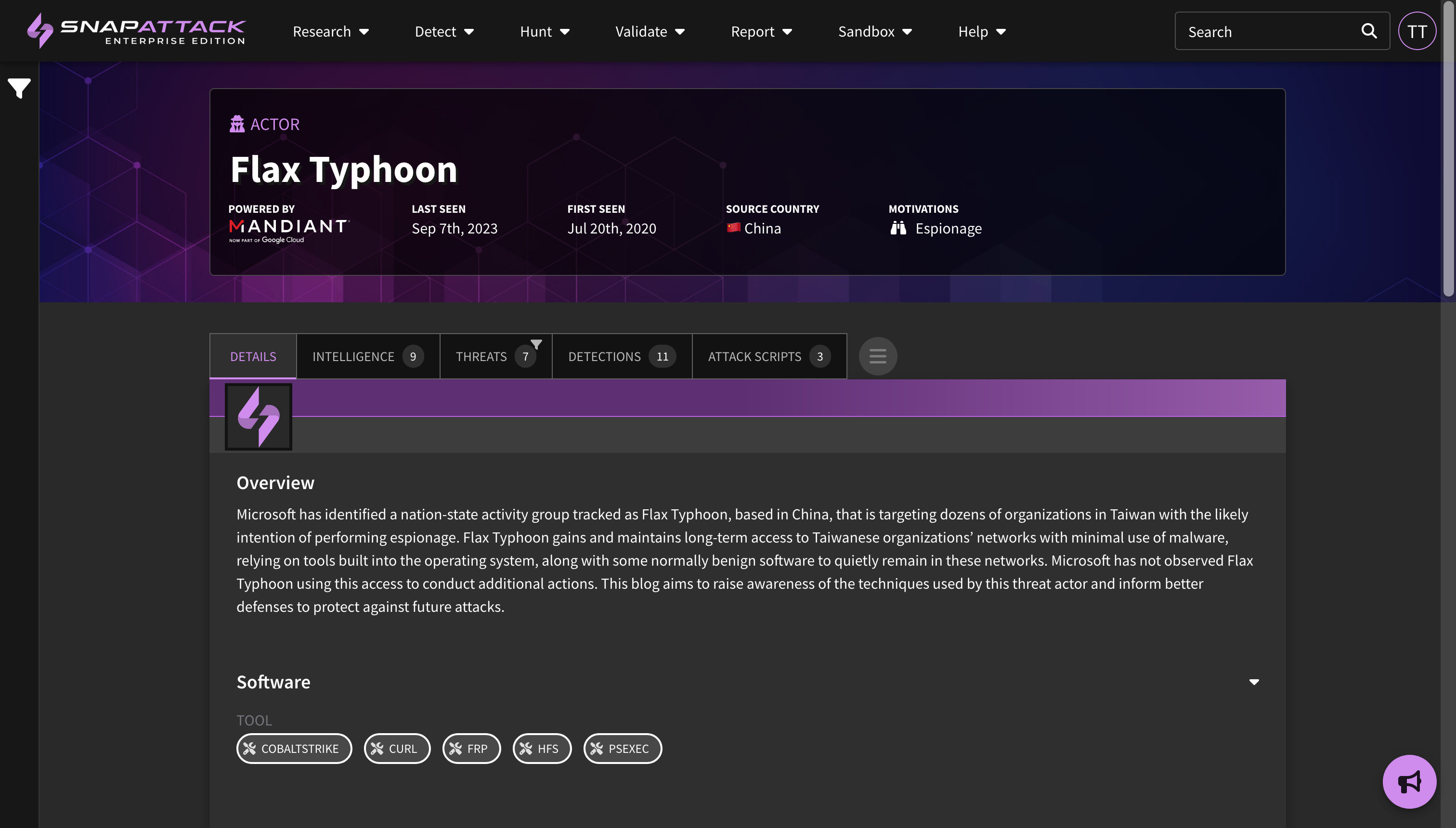
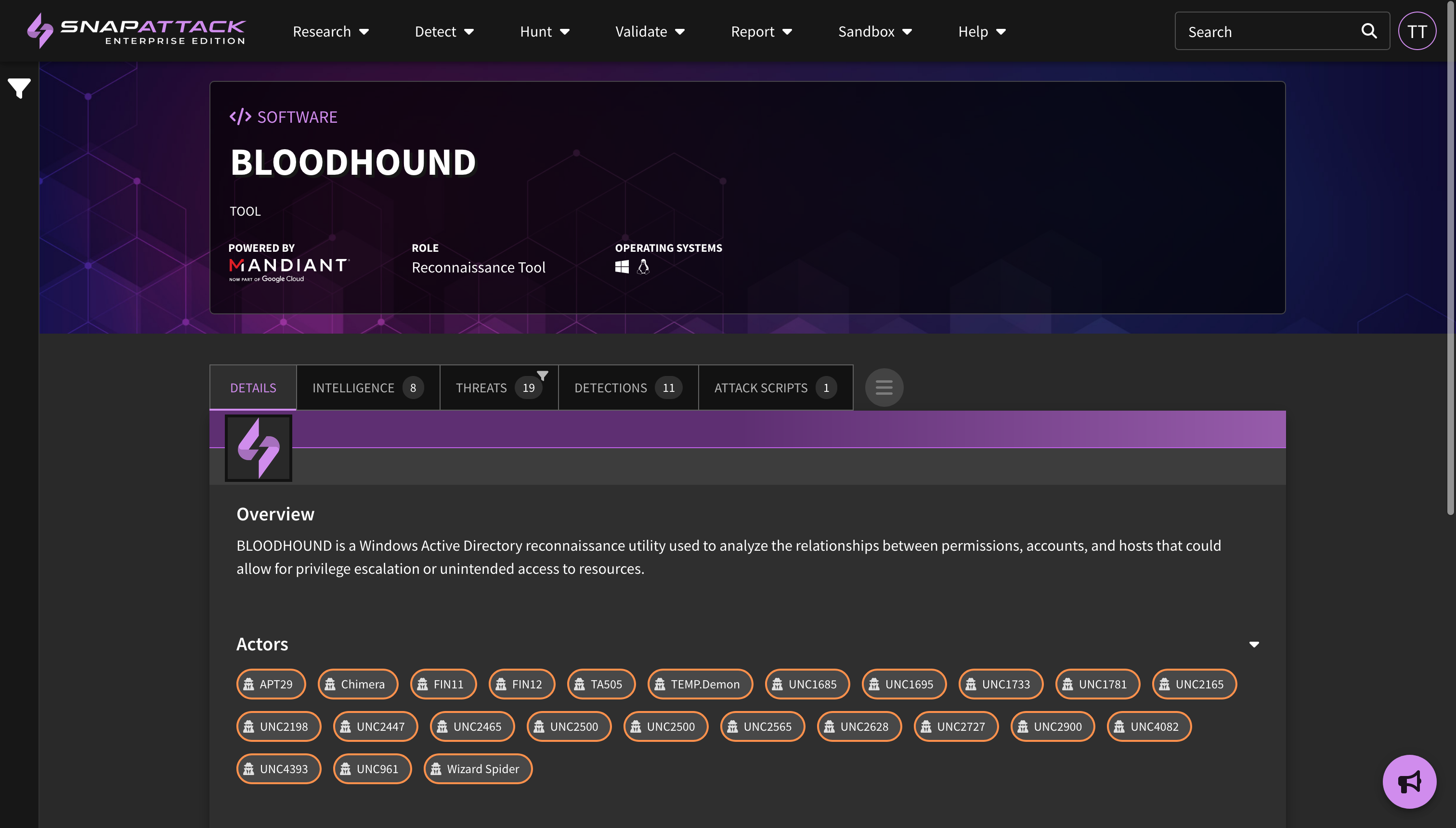
- Changes to Mandiant Intelligence Access: Starting immediately, SnapAttack subscribers will no longer have access to Mandiant threat intelligence or indicators of compromise (IOCs) within the platform. Collections for threat actors, malware/tools, and vulnerabilities will now be curated from open source intelligence and SnapAttack's threat research team. Mandiant-exclusive content has been removed from the platform. While certain features—such as threat profile prioritization and recommendations—may experience temporary limitations, we are committed to rapidly enhancing our platform to address these gaps and deliver even greater value to our users.
2025.01.01
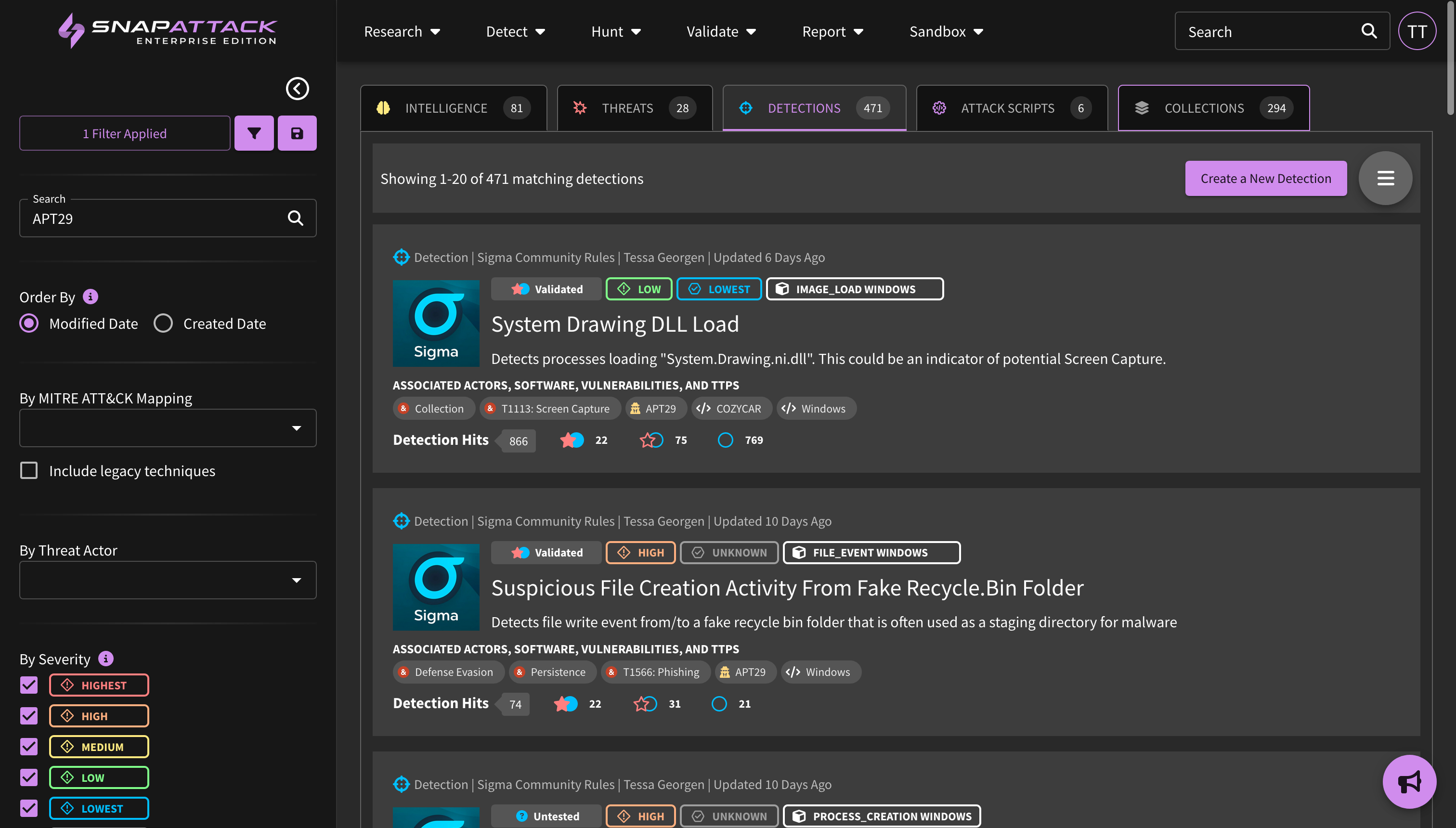
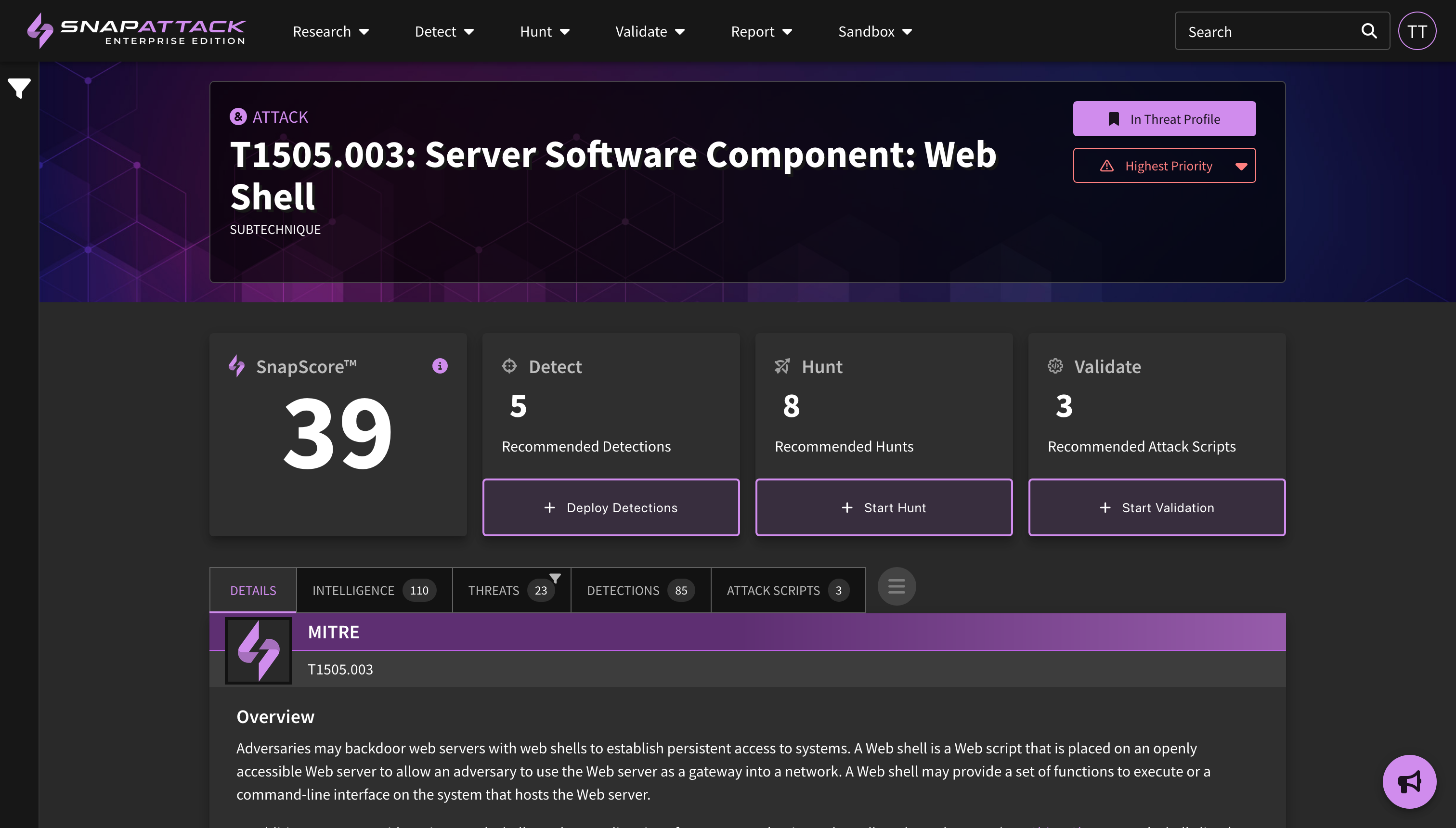
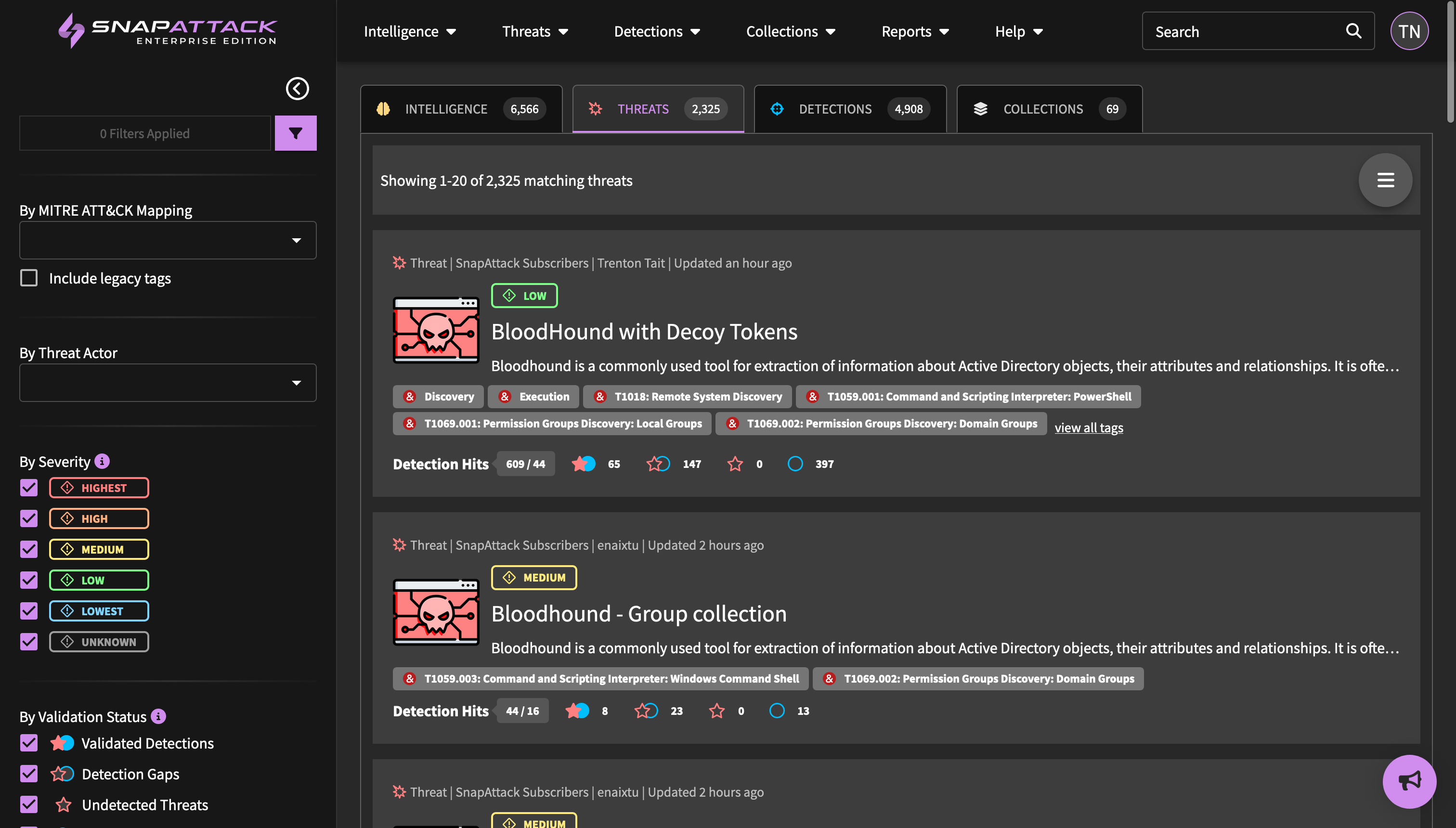
- MITRE ATT&CK v16: SnapAttack has been upgraded to using ATT&CK v16.1. Techniques that have been revoked or deprecated are automatically updated as part of this process. New techniques have had default severities mapped. To learn more about this update, review the ATT&CK release notes.
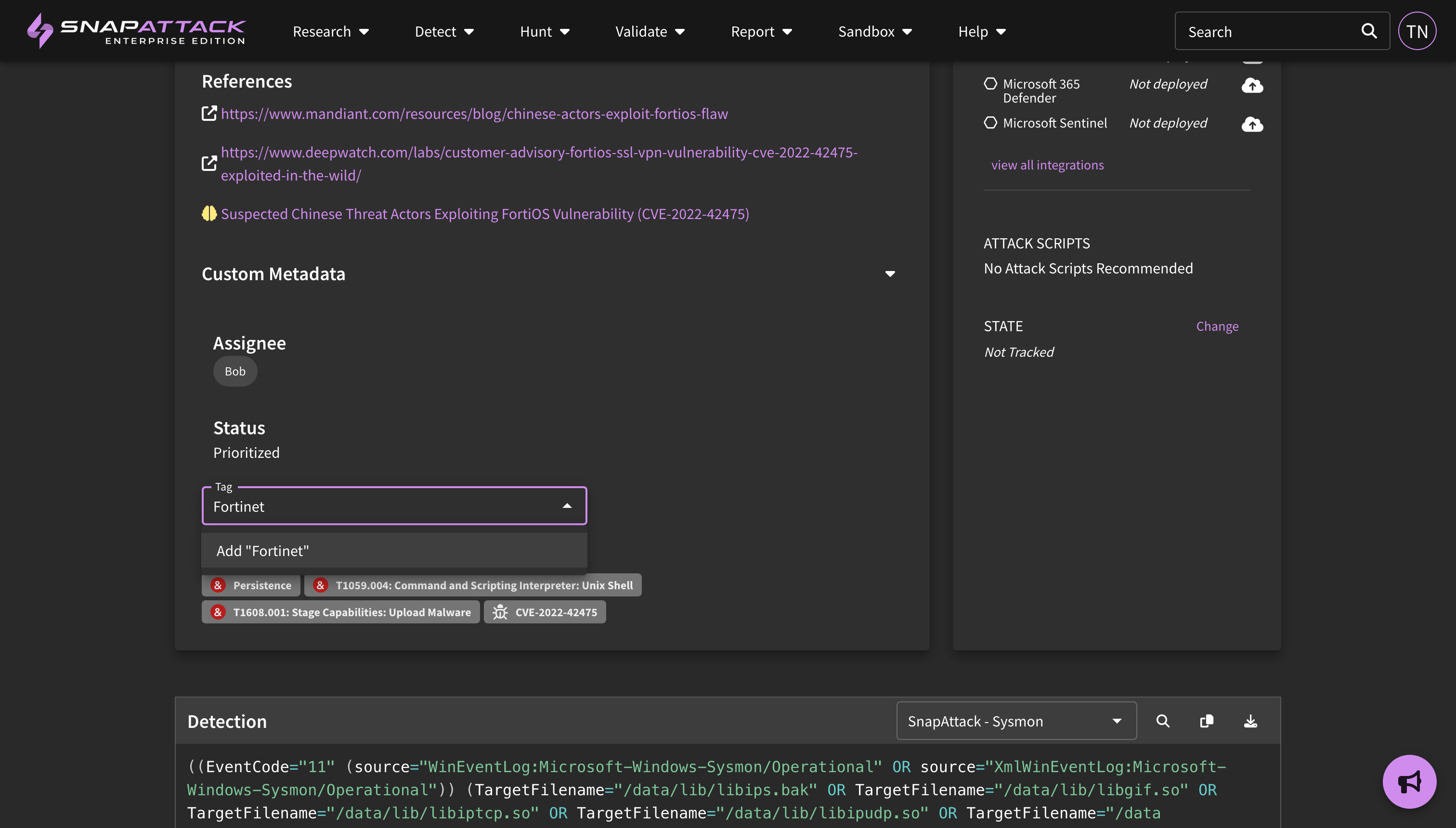
- Higher Fidelity Attack Labelling: Previously, attacks on threat captures were only labelled with MITRE ATT&CK techniques. Attacks can now also be tagged with threat actors, software, and vulnerabilities. These higher fidelity labels improve recommendation and validation algorithms, especially on threat captures that have multiple markers. Actor, software, and vulnerability tags can no longer be applied directly to threats; instead, these tags are inherited from the attack labels. Tags that were previously on threats have been automatically migrated to attack labels, where applicable.
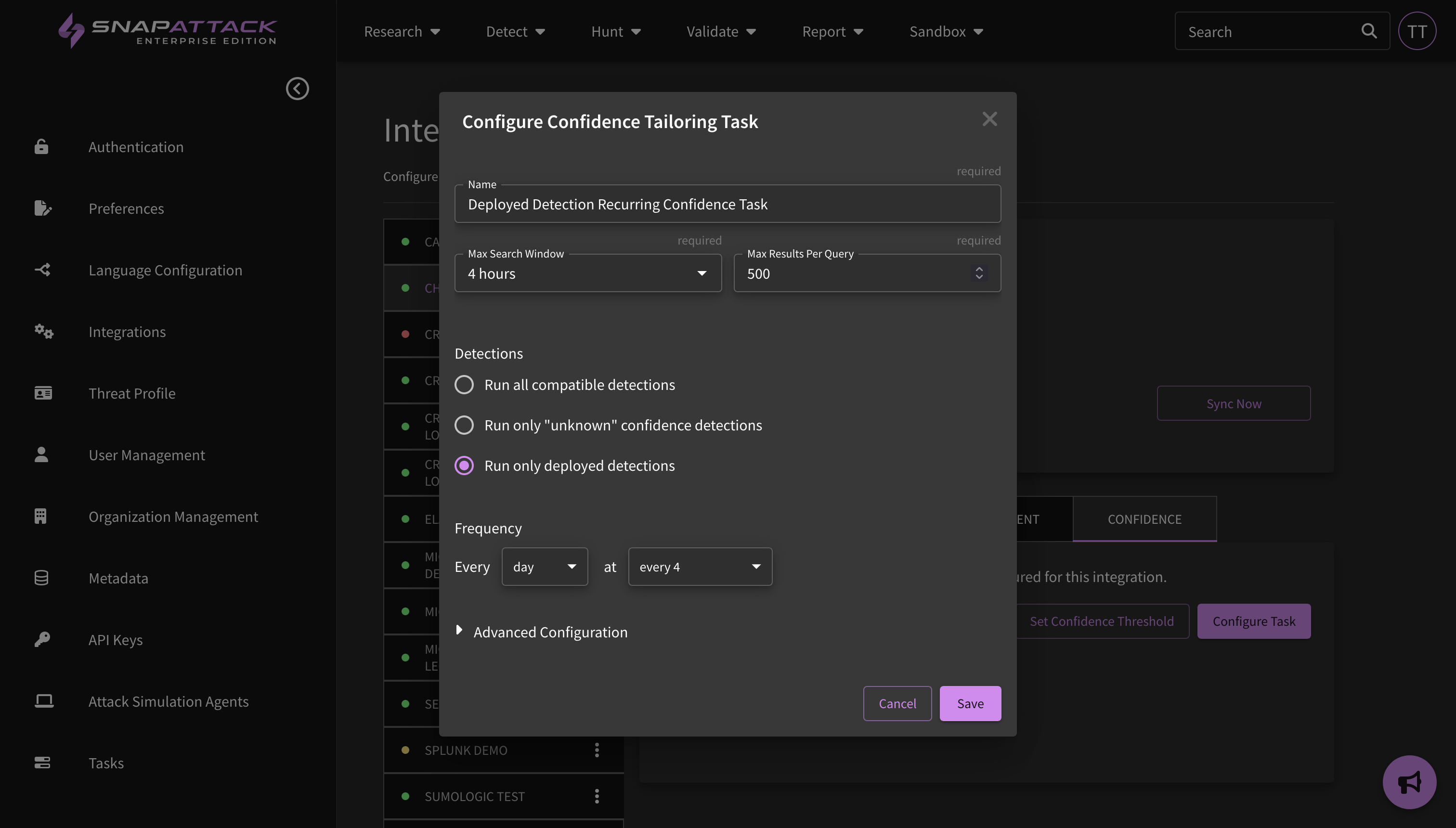
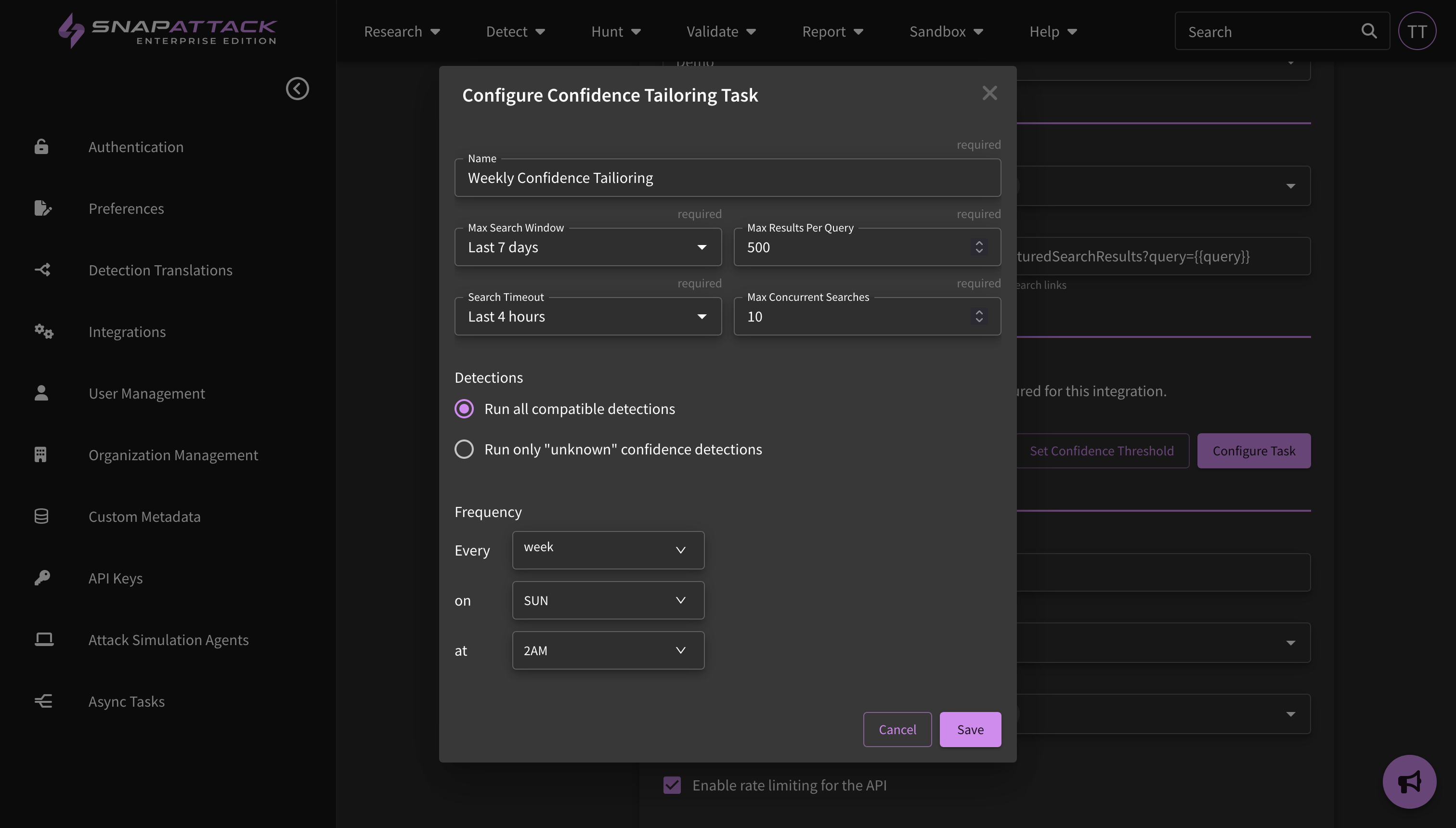
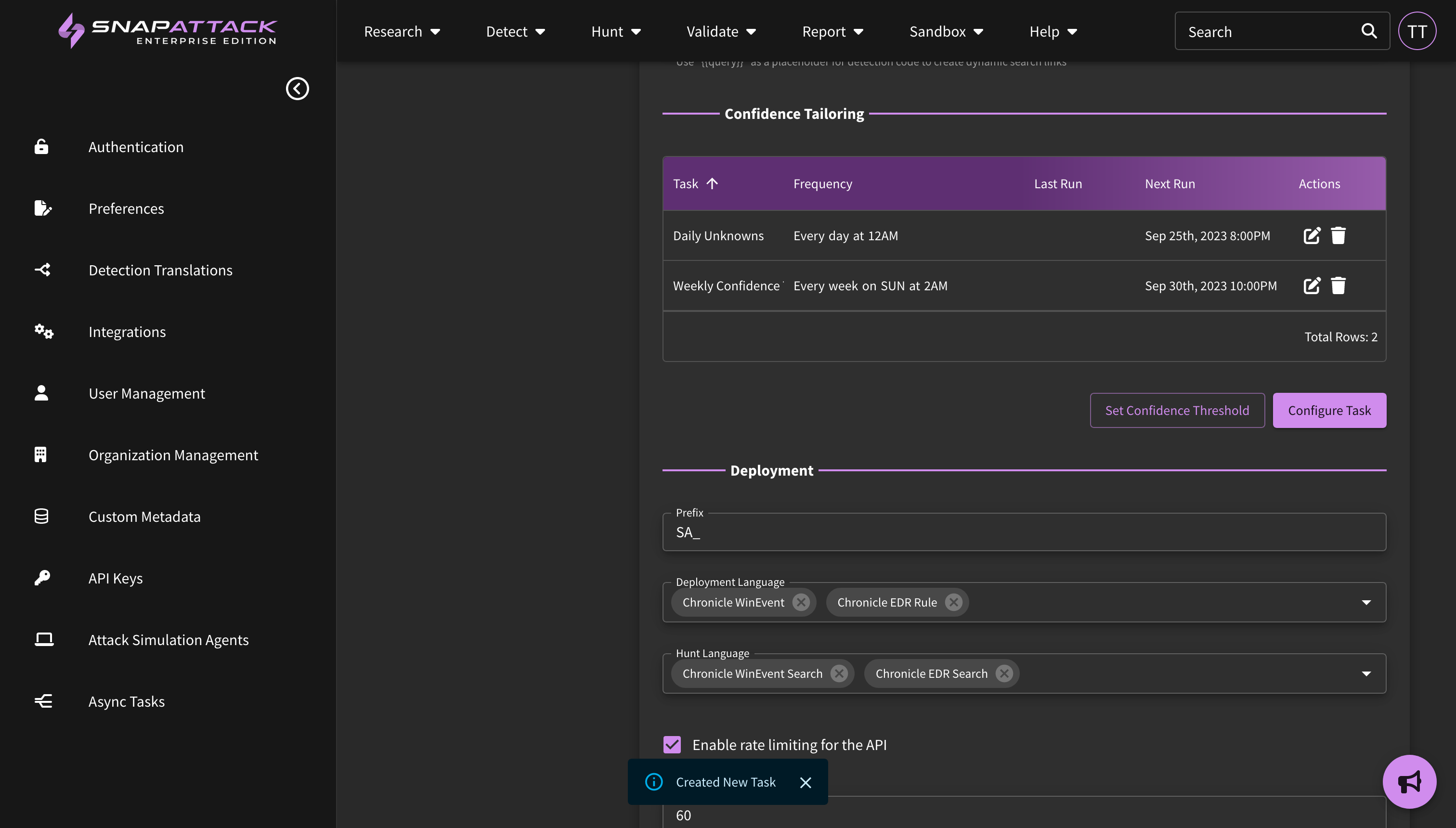
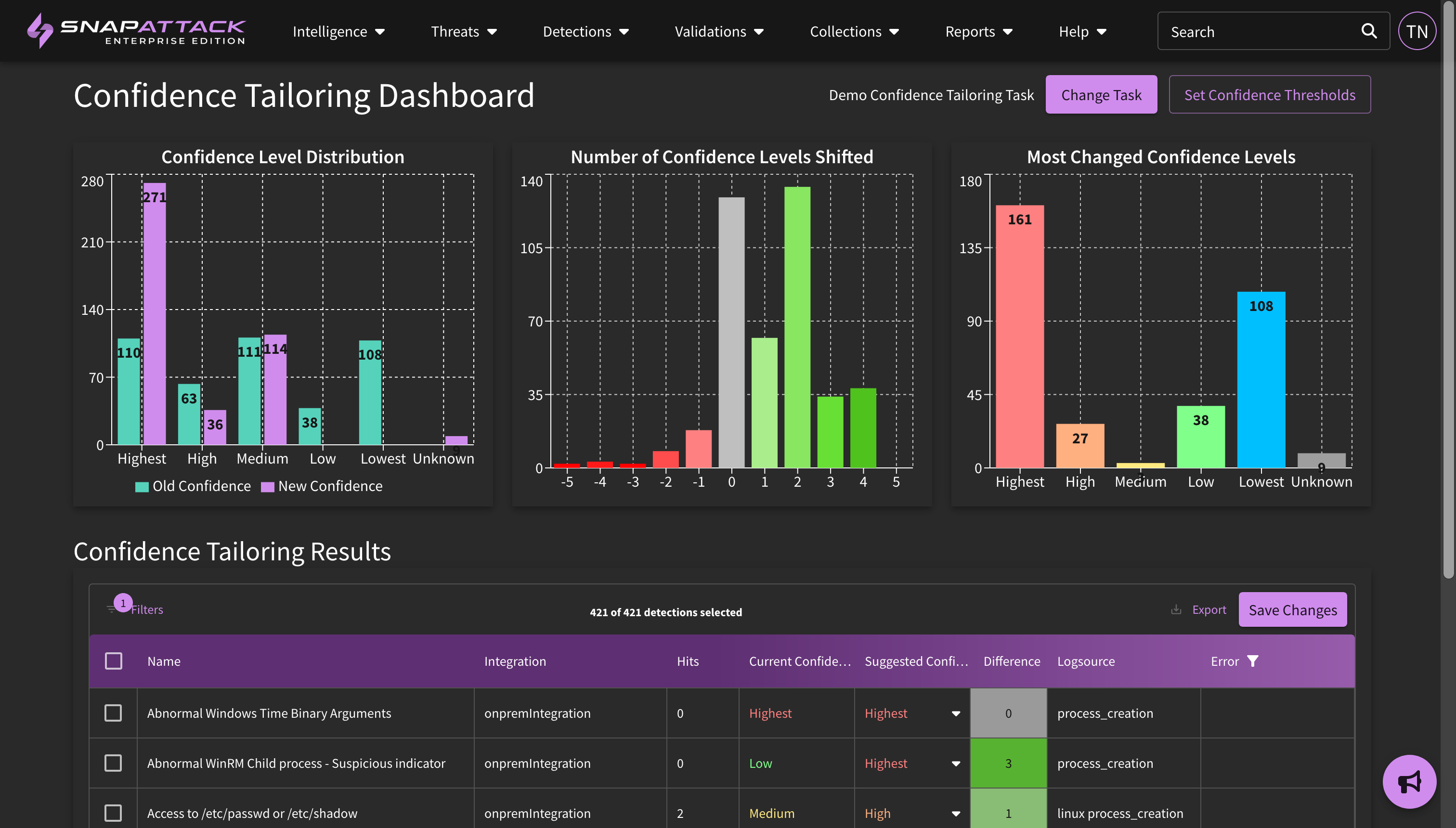
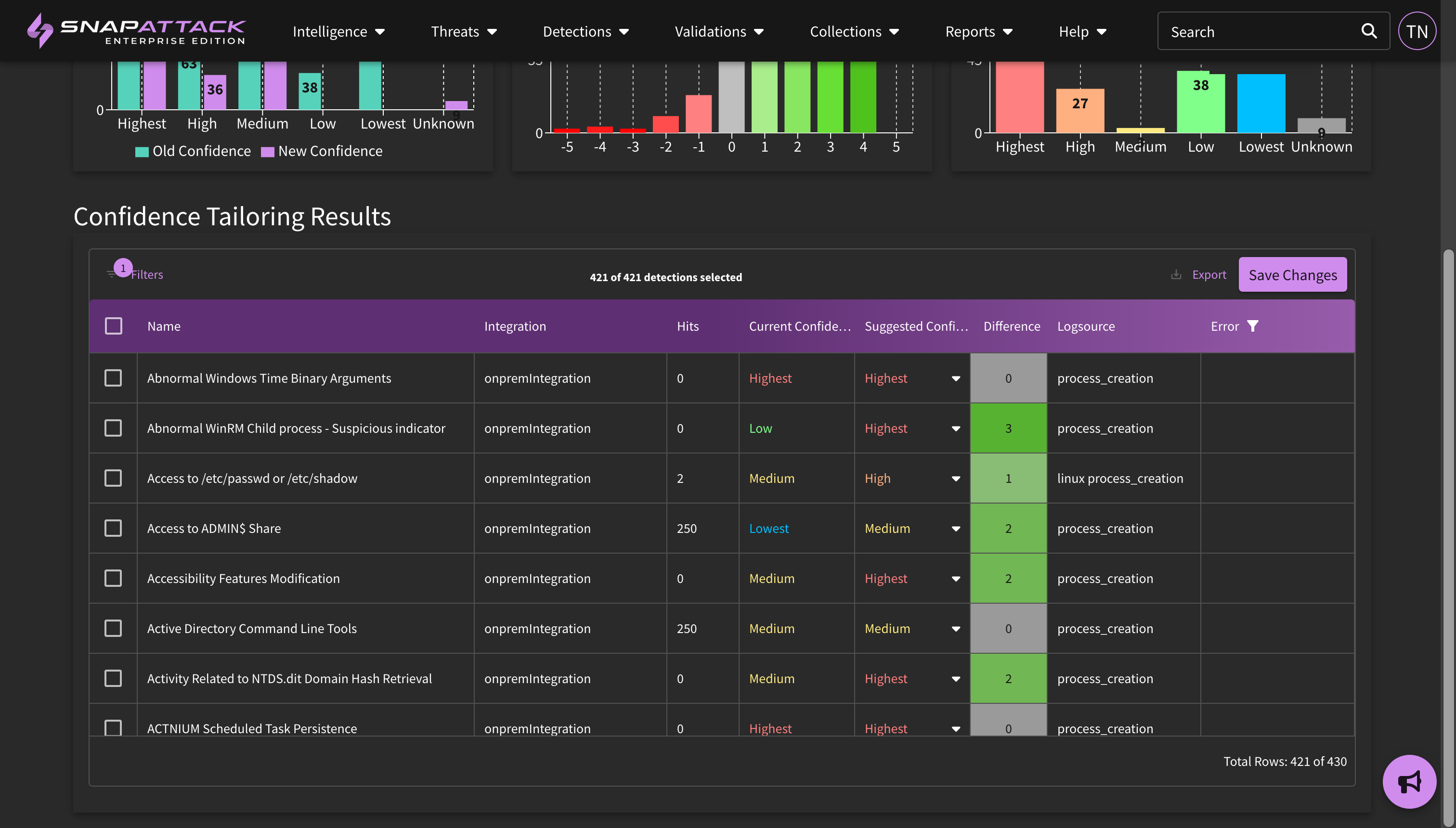
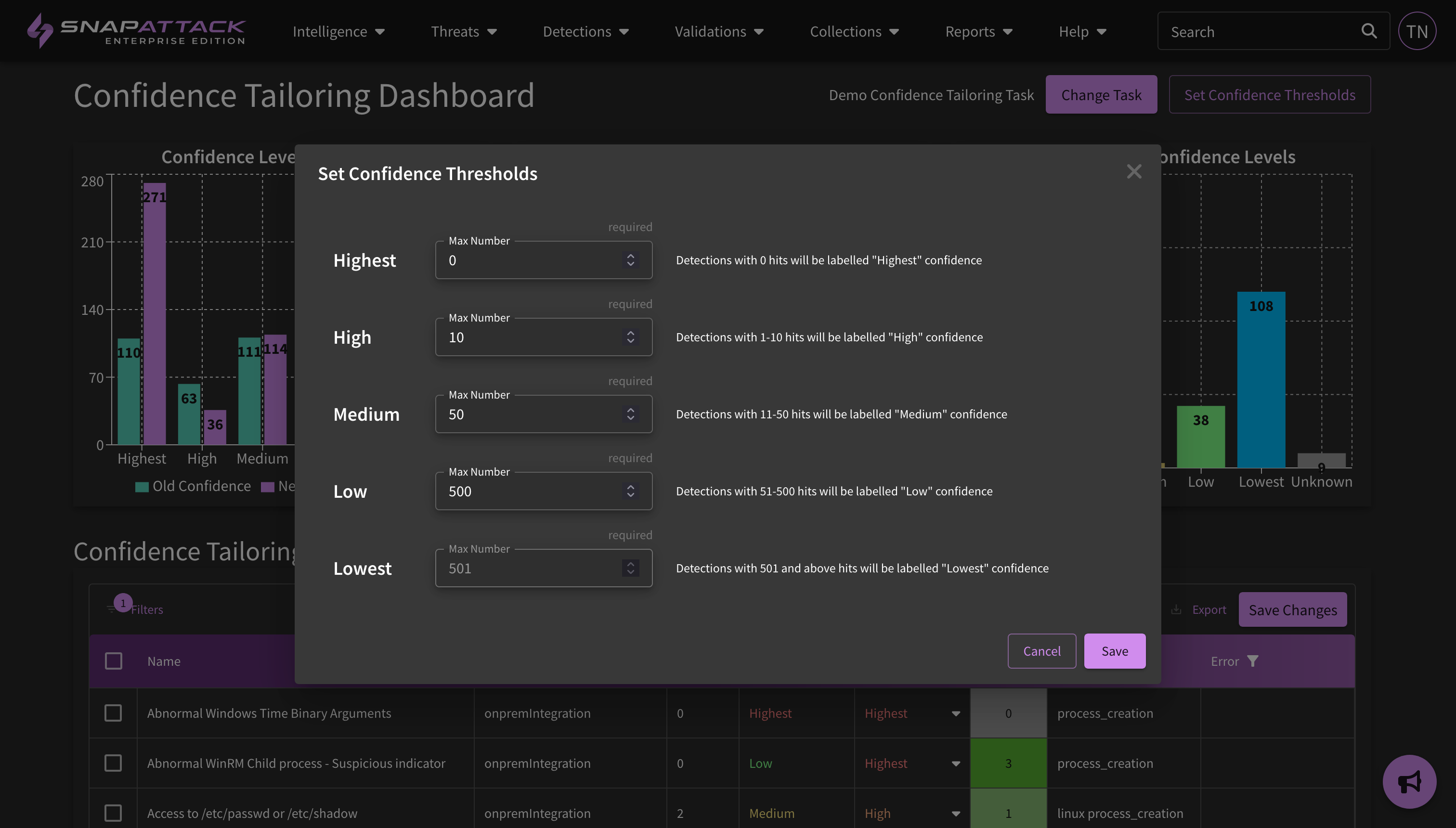
- Improved Confidence Tailoring Calculations: Confidence tailoring was originally job-centric; the organization defined levels for "highest", "high", "medium" and other confidence levels was applied after each job completed, regardless of the lookback window. This could lead to issues with different sized lookback windows (e.g., searching over 1 day vs. 30 days). Confidence thresholds are now defined as the expected number of weekly hits. SnapAttack will measure the average weekly hits over the last month in calculating the confidence value. This works across jobs and is applied automatically.
- Detection hit counts are now displayed on the SOC manager dashboard when confidence tailoring is used to measure deployed detection hits.
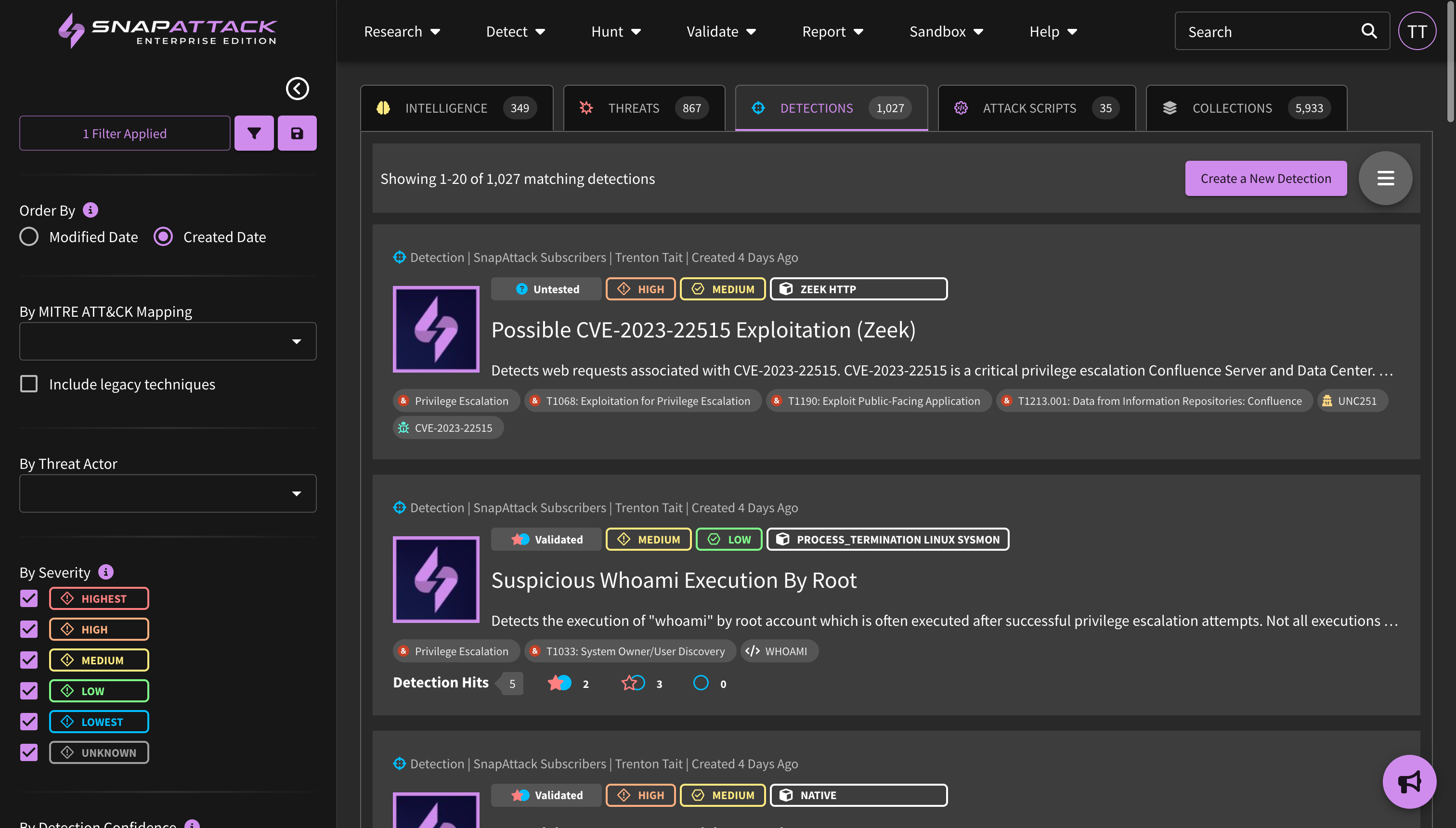
- Improved re-ordering of columns in grid view.
- General bugfixes and stability improvements to enhance the user's experience.
2024.12.01
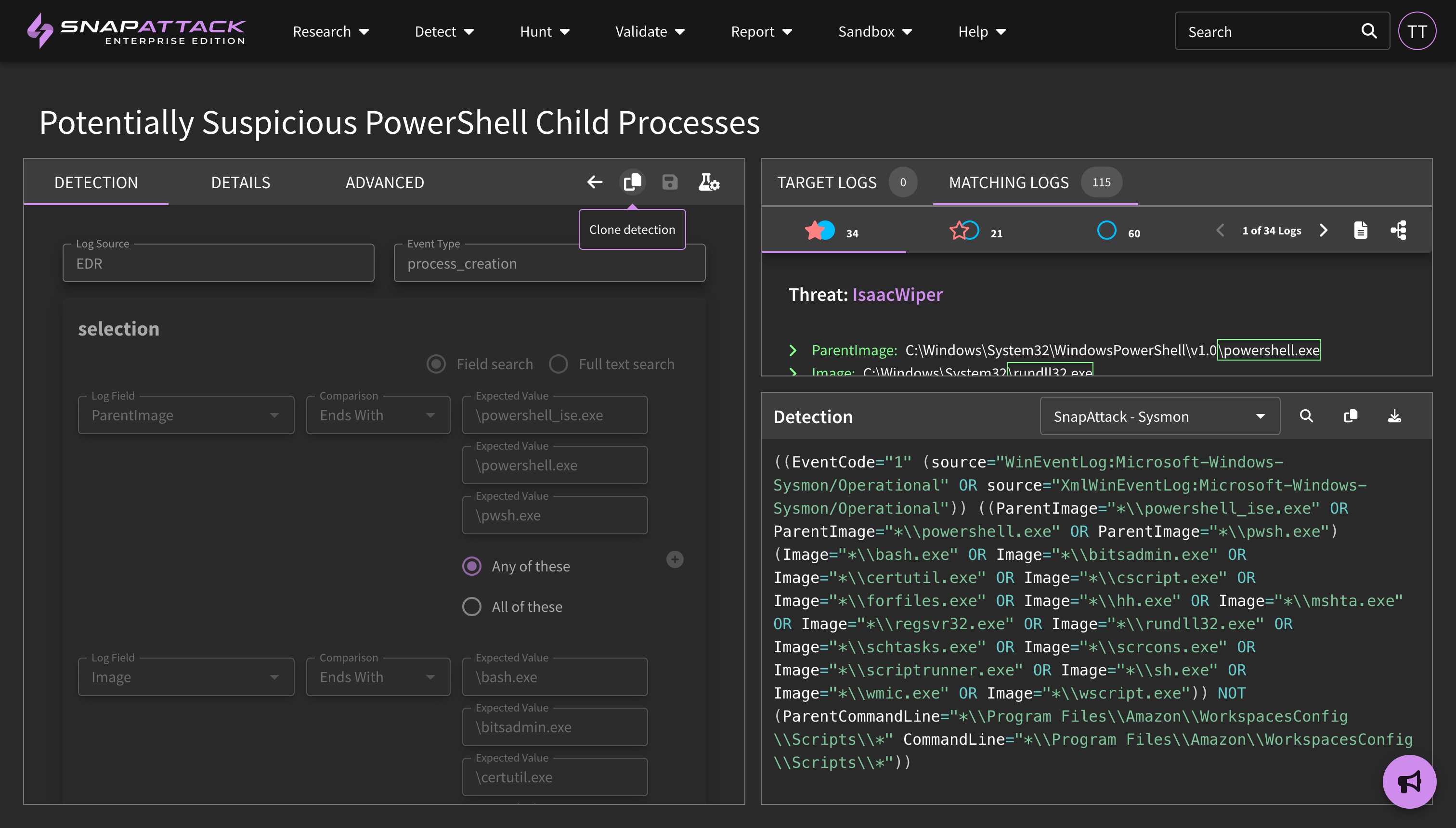
- Added detection logic syncing support for Splunk. Detection logic modifications made in the SIEM will now be synced back to SnapAttack. This requires updating the Splunk app to version 0.0.26.
- For SPL-native detections that are owned by the user's organization, the updated logic will be reflected in SnapAttack while also incrementing the version number to track the logic changes.
- For any detections not owned by the user's organization, or for Sigma detections, a new SPL-native detection will be created (while linking to the original detection as the parent) and be marked as deployed, while deleting the deployment record for the original detection. Any changes will now be tracked on this new child detection.
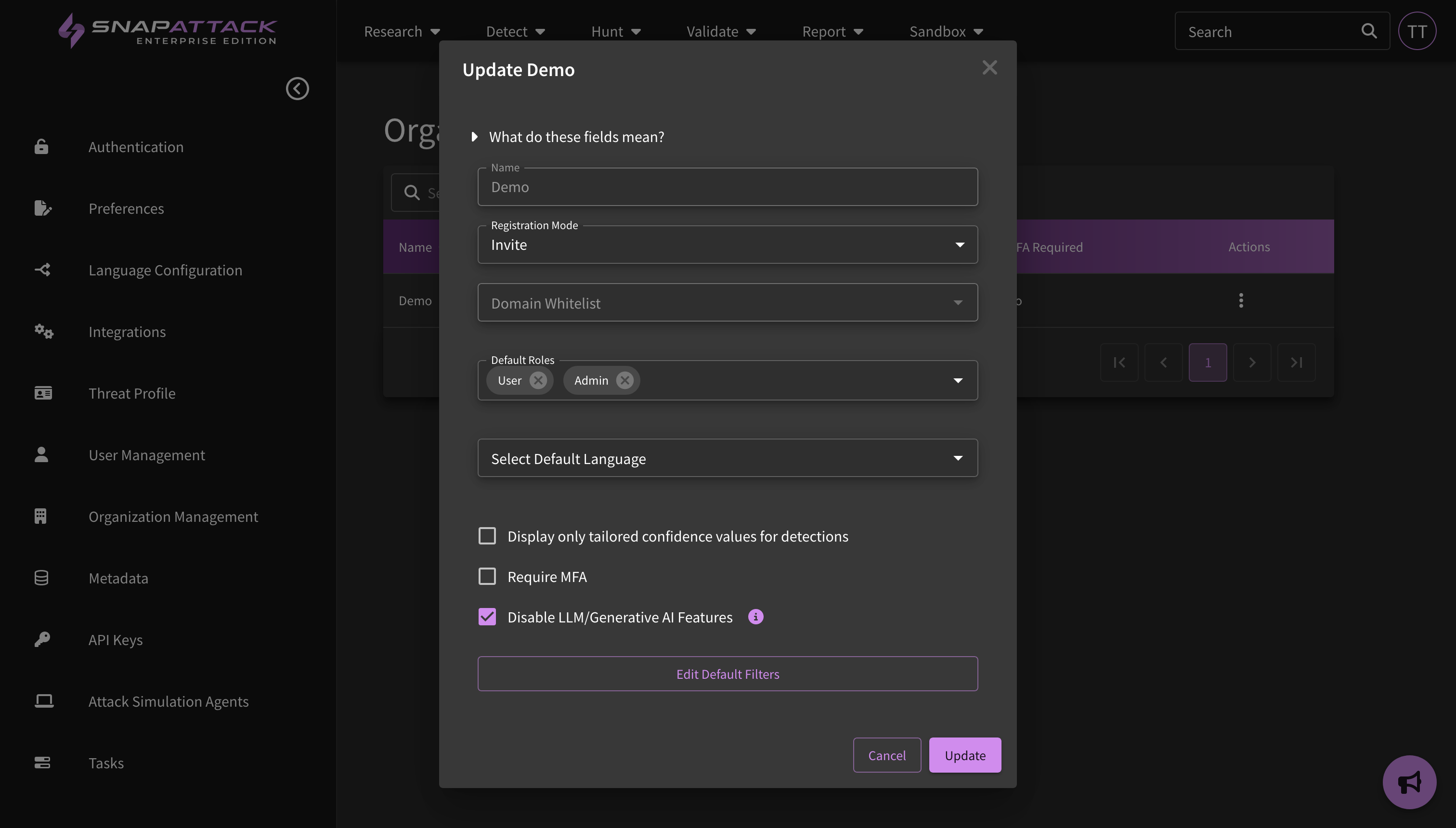
- Updated detection confidence badges to display both the SnapAttack and organization's confidence values for a detection. By default, if a detection's confidence is unknown, we will display the SnapAttack confidence value, which is an aggregated and anonymized value across our customer base. Organizations who prefer to see only their organization's confidence values, including if a detection's confidence is unknown, can change the organization-wide setting when managing their organization.
- Improved audit logging for user management, better tracking when permissions are added or removed to a user's account.
- Added additional actions to the hunt results page, enabling use cases such as deploying a detection after first testing it with a hunt.
- Added the ability to deploy multiple detections to a custom integration. Custom integrations allow users to mark detections as deployed in SnapAttack for platforms where API-level integrations do not yet exist, or in situations where integrations are not possible such as for air-gapped deployments.
- General bugfixes and stability improvements to enhance the user's experience.
2024.11.01
- Improved logsource badges for native detections using LLMs to determine the correct logsource when possible.
- Introduced compatibility badges for Sigma detections, indicating supported languages and integrations.
- Added filtering options for both native and Sigma (detection-as-code) detections.
- Expanded AI-enhanced descriptions for detections, now generated during updates as well as creation. This feature respects the organization's "opt-out" setting for generative AI/LLM features.
- Added controls for scheduled hunts, including the ability to enable/disable hunts individually and batch-update statuses via the hamburger menu.
- Enhanced the hunter's workbench sidebar to improve usability with multiple integrations, sorted detections by hit count, and clarified the currently selected detection.
- Updated the threat profile to not automatically rebuild when reaching the "Threat Review" step. The profile is updated periodically throughout the day in the background. This manual rebuild can be run at any time, and may take a few minutes to complete.
- Adjusted the threat profile priority threshold step to disable threshold modifications while a profile is rebuilding.
- Resolved multiple minor issues in threat profiles that affected priority filtering and display accuracy.
- Fixed a syncing issue with Mandiant Threat Intelligence data and introduced a background task to remove IOCs deleted from Mandiant Intelligence.
2024.10.07
- Threat Profile Priority Thresholds: added the ability for organizations to configure the number of items at each priority level in their threat profile. For example, organizations can designate the top 10% of actors as "highest priority". This allows organizations to better align resources based on capacity.
- Updated the threat profile filters, removing the previous "in profile" and "not in profile" filers and replaced with with an "unprioritized" priority that has the same meaning.
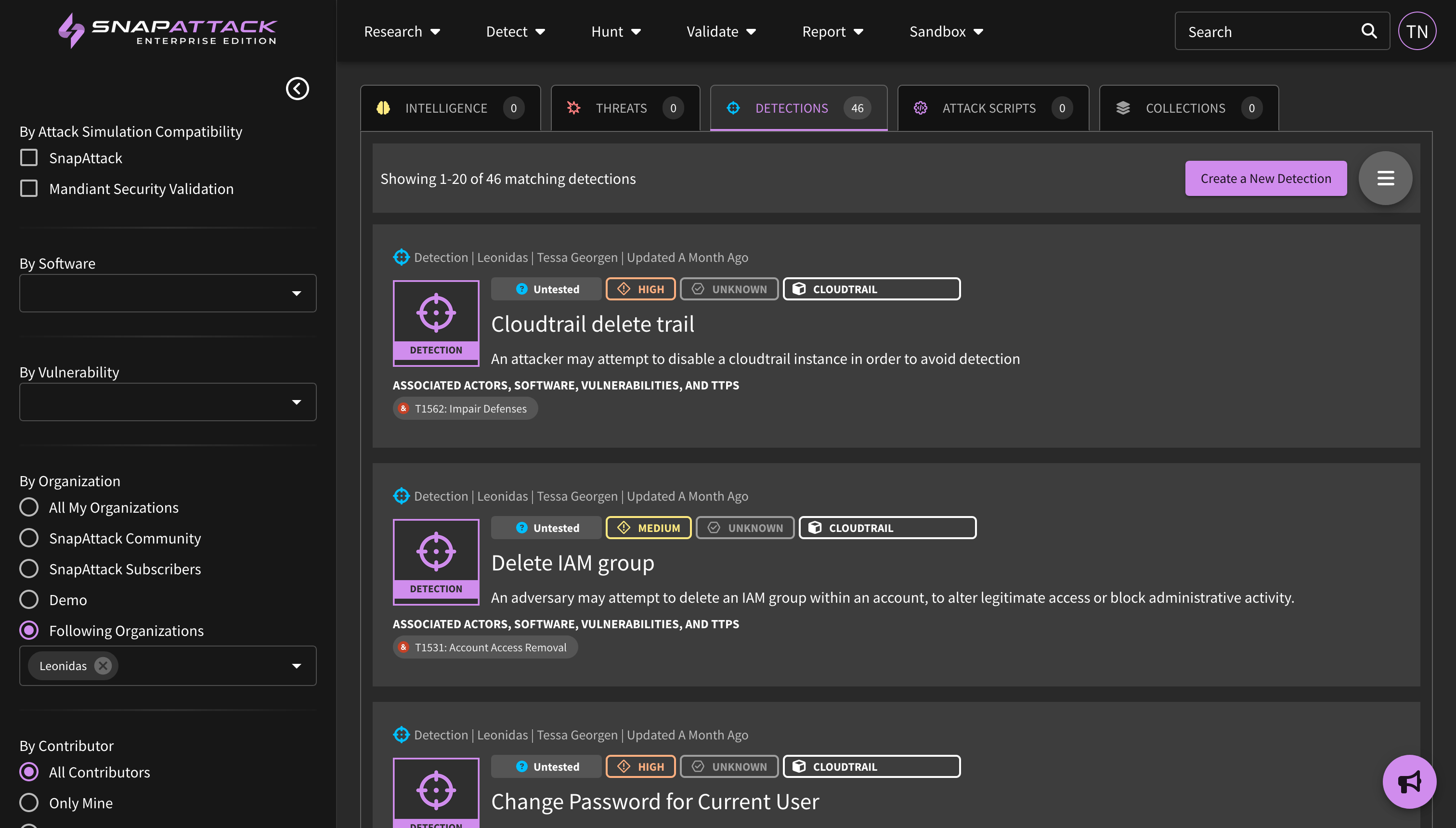
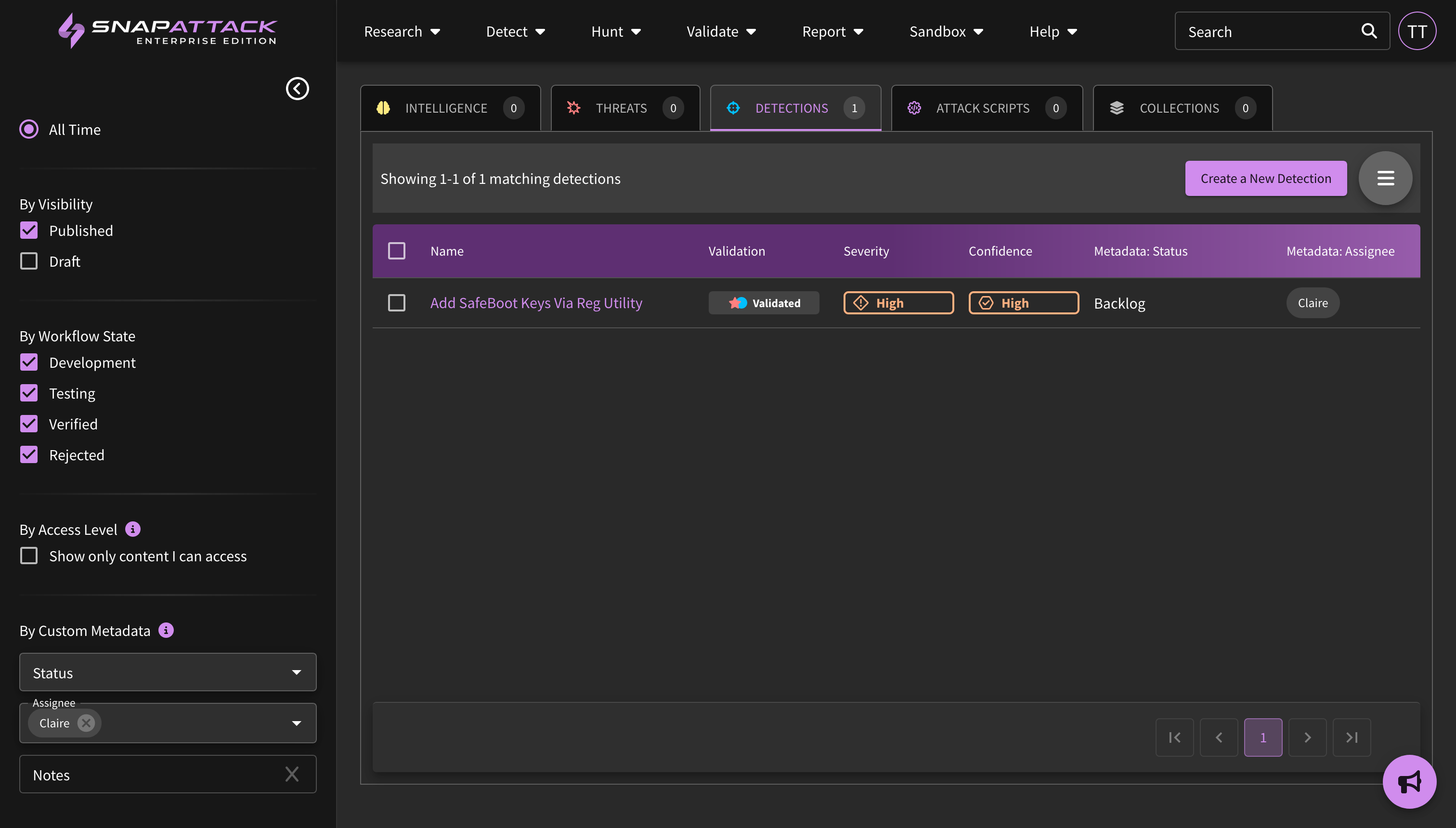
- Added the ability to manage metadata across multiple objects from the feed page and inside collections. Navigate to the grid view and select "manage metadata" to get started.
- Updated the logsource filter to allow a user to search for a custom logsources.
- AI-enhanced descriptions can now be generated on-demand per organization. Reach out to your customer success representative if you would like AI-enhanced descriptions generated for your existing detections.
- Added pagination to the hunt overview and tasks pages to improve load times.
- Fixed detection compilation issues with Falcon LogScale / NG-SIEM not correctly adding parentheses to OR statements, and fixed CrowdStrike IOAs that were incorrectly splitting "all of" conditions with ORs.
2024.10.04
- Automatic Detection Version Upgrades: Deployed detections that do not have any logic changes (for example, addition or removal of a tag, updates to the title or description, etc) will be automatically upgraded. This will reduce the number of detections a user sees that are "out of date" on the detection health dashboard. Any detections that a user sees that are "out of date" will have logic changes and should be manually reviewed before re-deploying.
- Updated the scheduled confidence tailoring configuration to clarify if raw logs or only hit counts would be returned, and also if the new confidence values should be automatically applied based on the organizations's confidence thresholds.
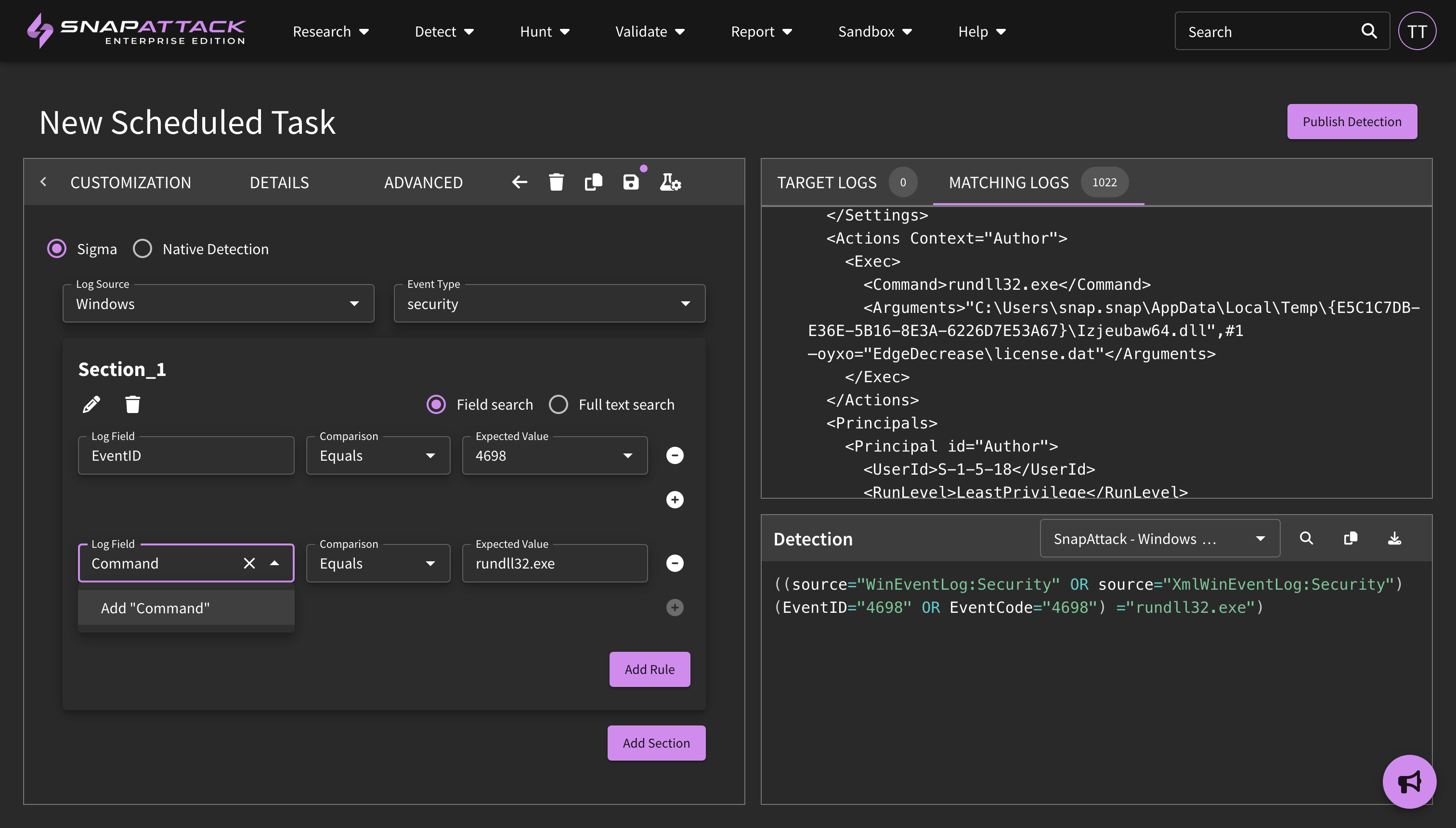
- Added a syntax validation to the detection builder and translation page. Users can validate a detections syntax against their integration's APIs during the development and testing process.
- Added the ability to create and save feed filters for collections.
- Upgraded OpenSearch to the latest version, which fixed a bug that caused a red block to appear over log details in our Hunter's Workbench for Chrome and Chromium-based browsers.
2024.10.01
- Added Azure AD as a logsource to the detection builder.
- Added the SnapAttack Splunk app to Splunkbase to facilitate easier installation and management.
- Updated the SnapAttack Splunk app to allow customers to configure the index name where detection hits are stored.
- General bugfixes and stability improvements to enhance the user's experience.
2024.09.03
- AI-Enhanced Descriptions for Native Detections: Native detections now come with automatically generated, AI-enhanced descriptions when they are created or imported into the platform. Users can also manually generate an AI description for any existing detection from the detection page. Organizations concerned about generative AI usage can opt-out by disabling AI features on the organization settings page.
- Hunt Jobs in Confidence Tailoring Dashboard: Hunt jobs can now be reused on the confidence tailoring dashboard, reducing the need to re-run similar jobs. Additionally, job types are now sortable, allowing for easier navigation and retrieval of specific jobs.
- Improved detection hit load times when viewing threats by approximately 50%, providing a noticeably faster experience particularly for longer duration threat captures.
- Resolved an issue where time windows and filters were not correctly applied in the hunter's workbench.
- Fixed crashes and regressions related to detection version diffs, stemming from recent integration and language selector updates.
- Corrected a bug where detections deployed to multiple integrations were being double-counted on the detection health dashboard.
2024.09.01
- Audit Logs: SnapAttack now provides visibility into user activity via the platform's Audit Logs, accessible under Settings → Audit Logs. By default, organization administrators have access, but permissions can be customized per user. Audit log events can also be exported via the SnapAttack API for integration into SIEMs or data lakes. To facilitate this, a service account with a REST API key can be set up for log access and export.
- Per-Deployment Configurations: Users can now specify configuration options for each detection at deployment. When deploying detections, an "Advanced Configuration" option will appear if additional settings are available. This allows users to configure parameters such as CRON scheduling and alert thresholds on a per-detection basis.
- The SnapAttack Splunk app now supports per-deployment saved search parameters. An update to the Splunk app is required to enable this feature. Additionally, minor bug fixes have been applied to resolve job processing errors.
2024.08.06
- Improved the user interface for detections that are managed by a SIEM, but synced to SnapAttack via API for reporting, versioning, and tracking purposes. Because these detections are managed in the integration directly, users cannot edit or undeploy them via SnapAttack.
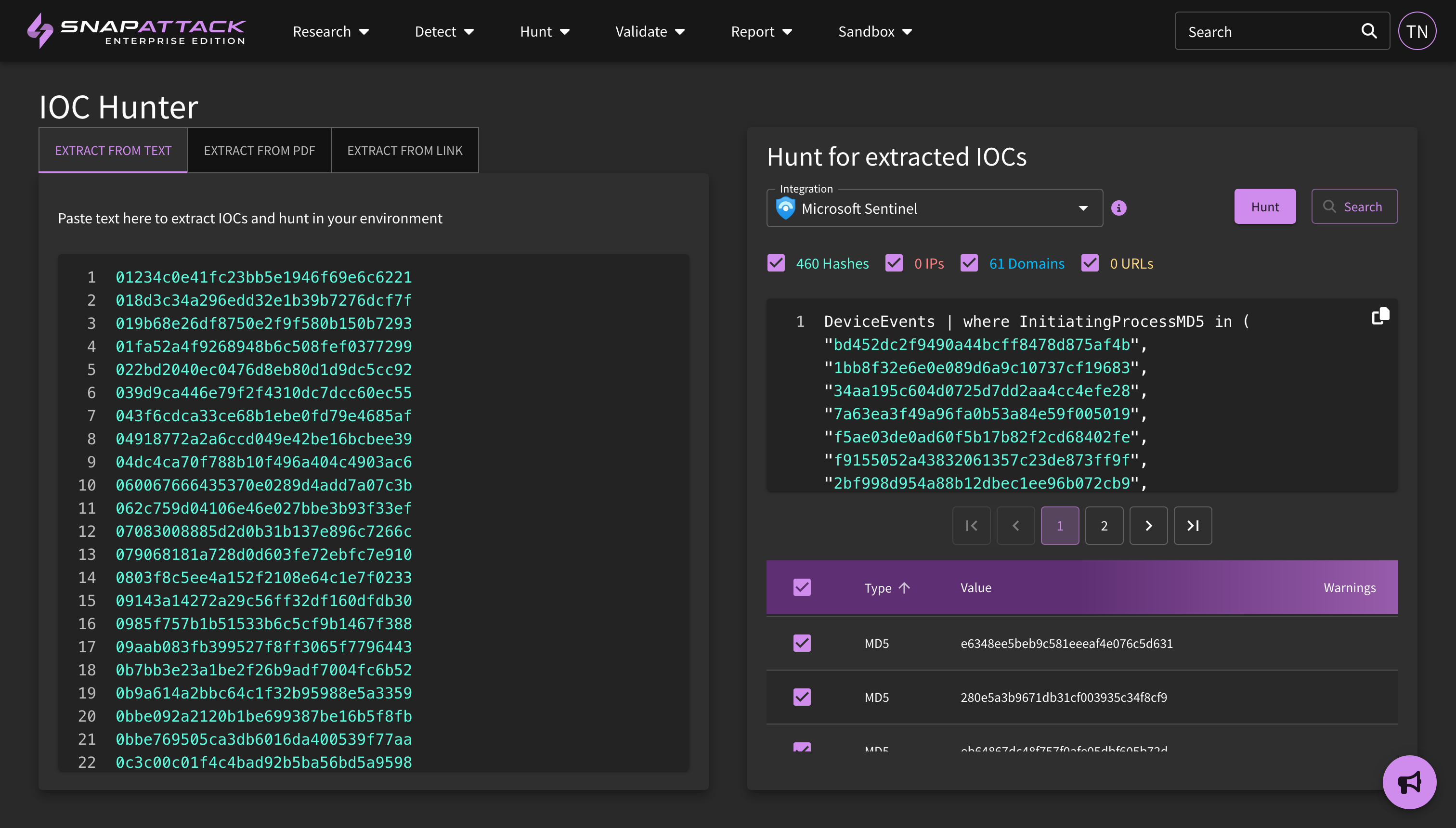
- Improved IOC Hunter's extraction capabilities, ensuring more comprehensive IOC extraction from web pages.
- Resolved an issue where metadata values were not displaying correctly in grid view, now ensuring consistent visibility across the main feed and collections.
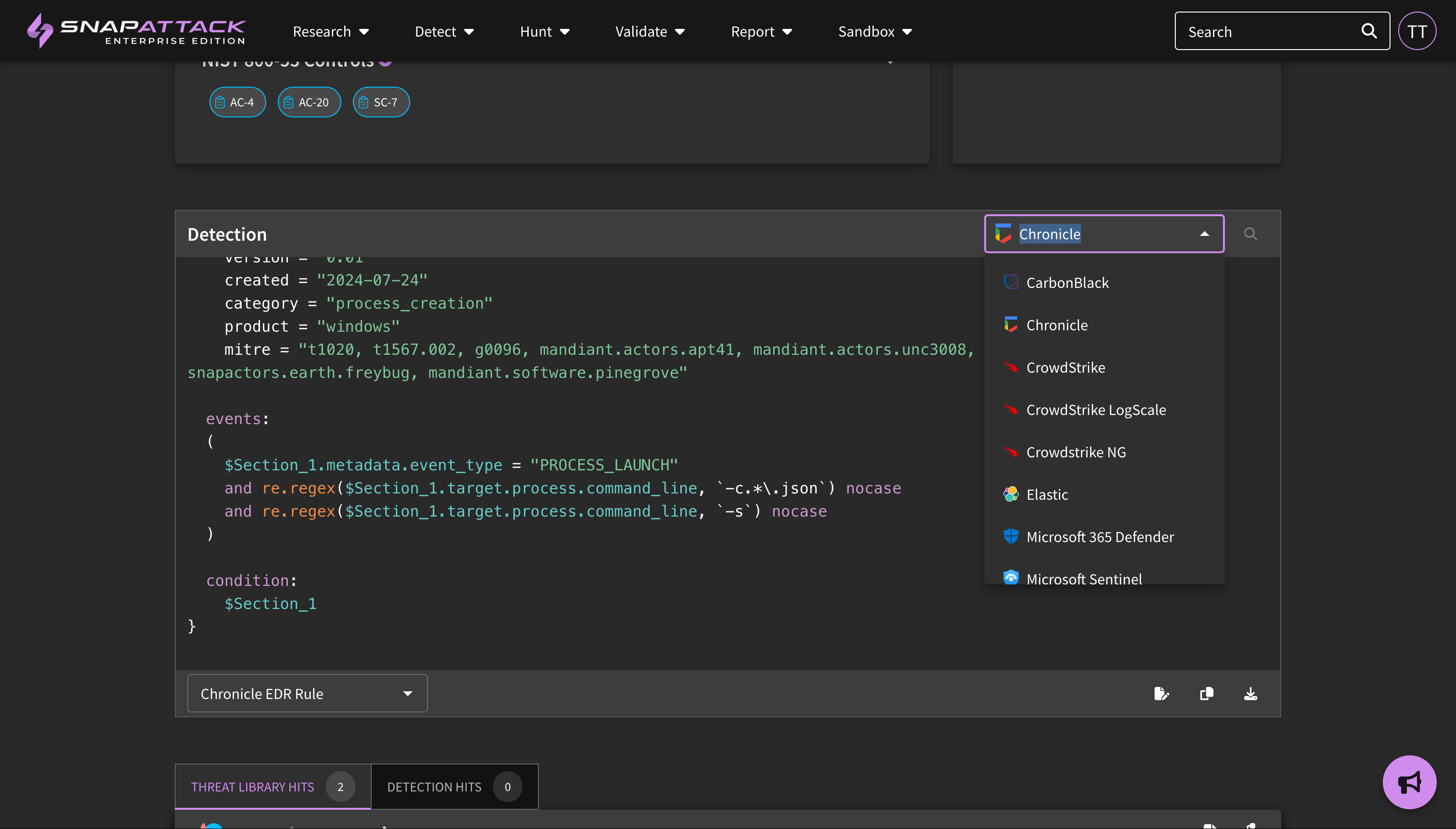
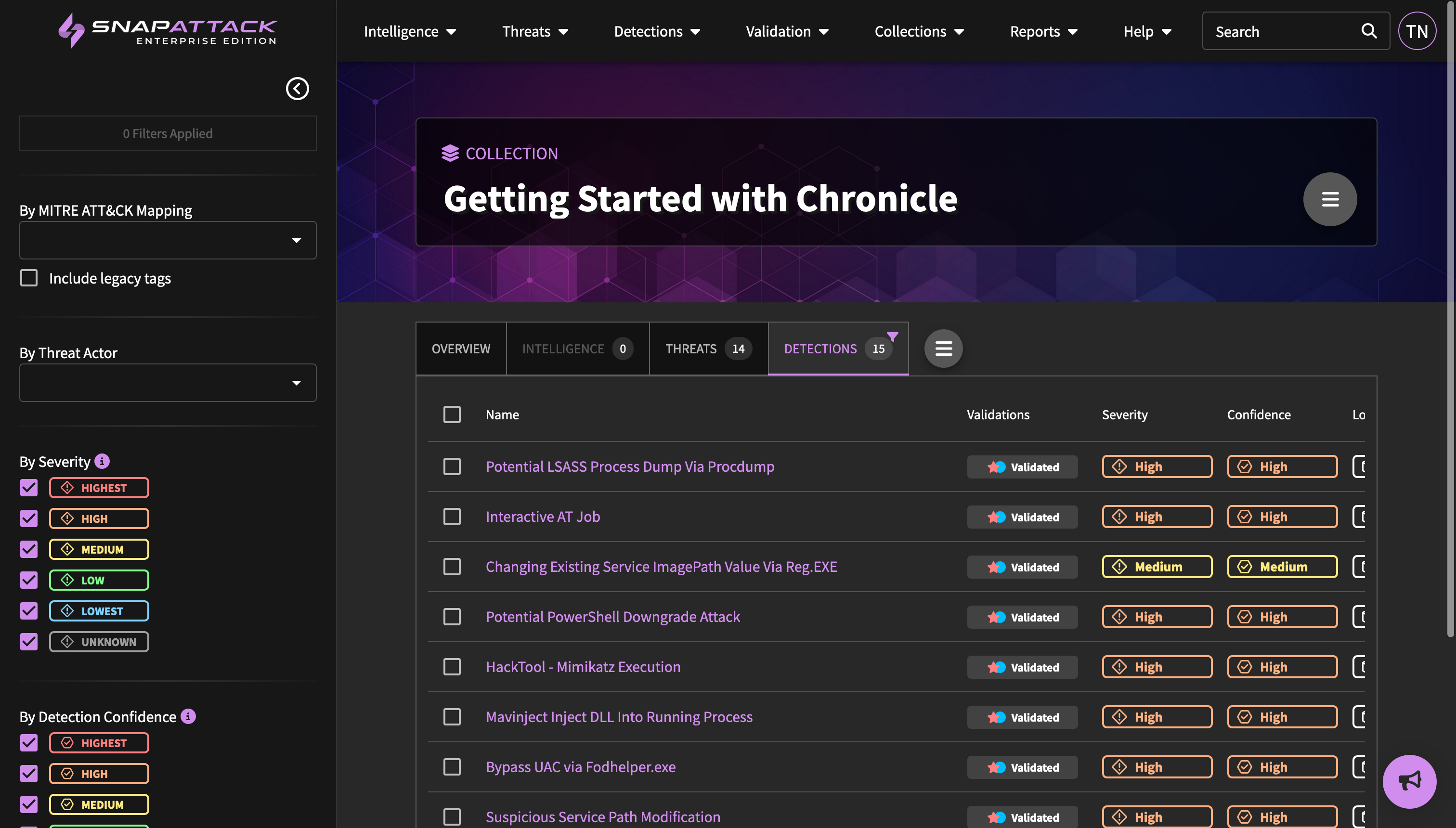
- Addressed a synchronization issue with Chronicle rules if the
metasection was edited in the Chronicle console and thesnapattack_fields were not first in that section. - Fixed an issue where scheduled hunts could fail to restart if an integration became unhealthy.
2024.08.04
- Refined the translation widget to enhance user experience: now, the first compatible language is automatically selected, the SnapAttack threat library languages have their own integration, and the widget is better organized by integrations and languages, with incompatible options clearly indicated.
- Streamlined the IOC Hunter widget by consolidating URL, PDF, and text input options onto a single panel, optimizing it for laptop resolutions. Also, corrected an issue where the hunt button might incorrectly appear disabled.
- Standardized detection logic operators (AND, NOT, OR) to lowercase in Sigma detections, ensuring compatibility with newer pySigma compilers without altering detection logic.
- Corrected the "time behind" calculation on the health dashboard, now accurately measuring the time elapsed since the first outdated version.
- General bugfixes and stability improvements to enhance the user's experience.
2024.08.02
- Updated the Splunk app to support IOC hunt job types; a Splunk app update is required to use this feature.
- Improved detection translation capabilities for Sumo Logic.
- General bugfixes and stability improvements to enhance the user's experience.
2024.07.04
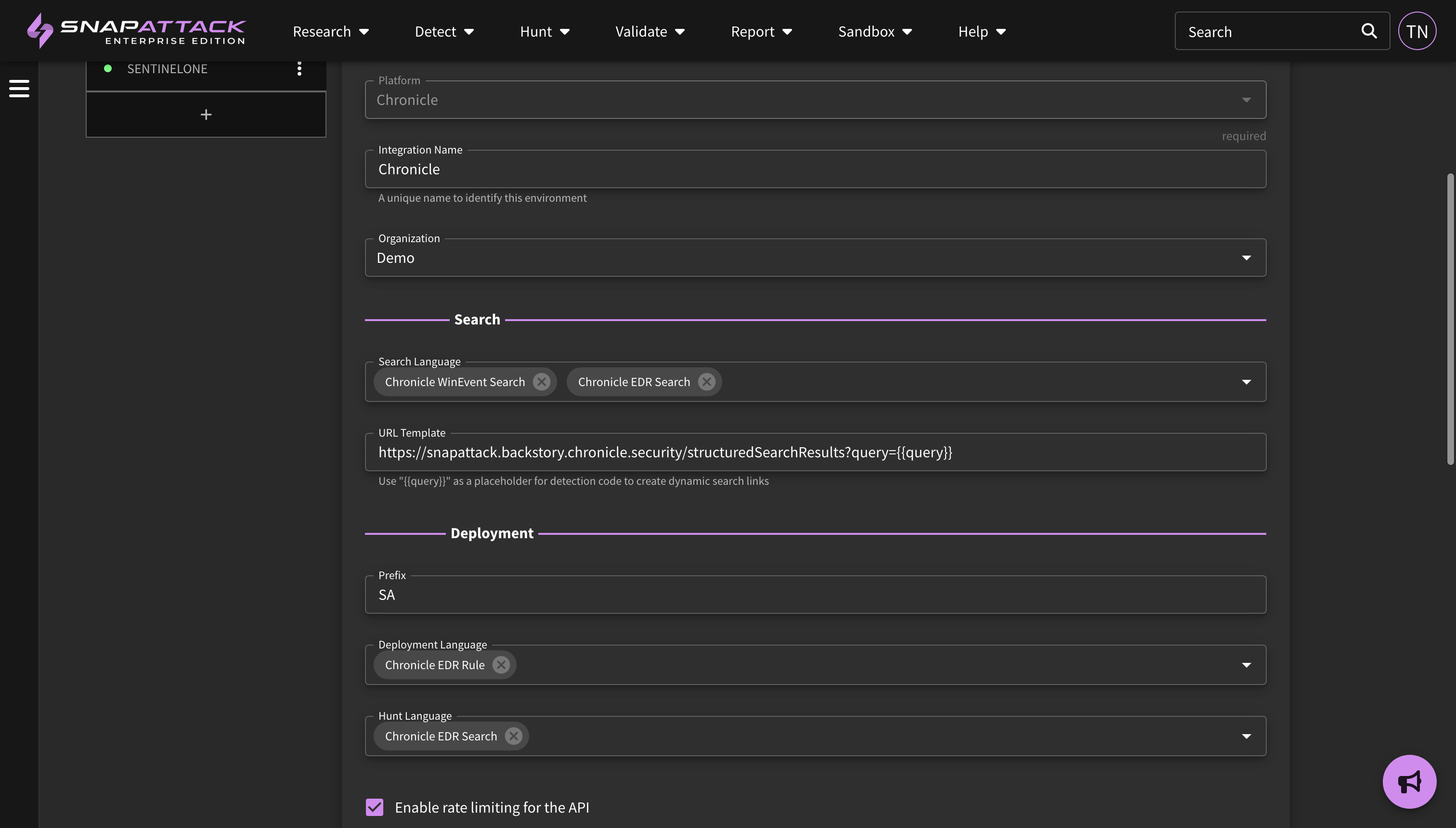
- Translation Widget: the translation widget on detection pages and in the IDE has been updated. Previously, users would select the language they wished to view. Users will now select an integration first, and may optionally choose a language second. This streamlines the process if an integration only supports a single language. For integrations that support multiple languages, this groups relevant languages for faster selection. The "preferred language" user setting is still applicable, and will target that integration and language in the selector if there is a valid translation.
- Integration Icons: integration icons have been added throughout the application. They can be seen on the logsource badges for native detections, in filters, the translation widgets, and on the integration settings page.
- Collection Contributor Role: a new permission was added to allow users to curate collection content. All users, including the read-only user accounts, can create their own collections. If an organization wishes to allow those users to add to or edit another organization user's collections, they can assign the collection contributor role. Content admins, by default, have contributor rights to all parts of the application, granting the ability to edit or delete other organization user's content.
- Microsoft Sentinel: MITRE ATT&CK reporting at the sub-technique level is not supported, so the parent technique is now used instead (e.g., if a detection was taggaed with T1562.001, it would show as T1562 when deployed in the Sentinel console).
- SentinelOne: improved detection translations for SentinelOne customers and hunt result reliability.
- Detection severity changes will now be updated across deployed integrations when the changes are made in the application. This will apply at the next scheduled sync interval.
- Reviewed the bulk action "hamburger menus" across the application to improve consistency. Inside collections, added the ability to undeploy detections, apply confidence tailoring, manage tags, add recommended detections to a collection, and export recommended detections. For detections, added the ability to deploy or undeploy to multiple integrations at once and apply confidence tailoring. Some menu options were also re-arrange for consistency.
- Resolved multiple bugs with metadata, including the ability to use metadata fields with saved filters, issues when editing in bulk or the IDE, or not seeing changes made when saving.
- Fixed a bug on the language configurations setting page that made it difficult to show/hide languages. Users who do not wish to see integrations/languages in the translation widget should hide those languages from this page.
- Added a link to the status page, which tracks platform uptime and scheduled maintenance windows.
2024.06.10
- PySigma language configurations are now generally available for all customers. There are two new tabs on the language configuration settings page for PySigma pipelines and validators. The languages tab will now ask if you are using the PySigma or legacy Sigma engine.
- Expanded support for SentinelOne customers - with PySigma, we now support the PowerQuery language (in addition to the previous Deep Visibility query language). PowerQuery can be used to deploy detections and hunt across the Singularity data lake.
- Expanded support for CrowdStrike customers - detections can now be hunted across the CrowdStrike LogScale "NG-SIEM" in the CrowdStrike console. This requires installation of a Falcon Foundry application. Due to API limitations, detections cannot be deployed the NG-SIEm, but users may copy the detection and manually import it into CrowdStrike.
- Updated the "By Time" filters to support time deltas (e.g., -30d), allowing saved filters to correctly display content including time filters. These filters need to be edited and re-saved for the new time values to be used.
- General bugfixes and stability improvements to enhance the user's experience.
2024.06.05 Major Release
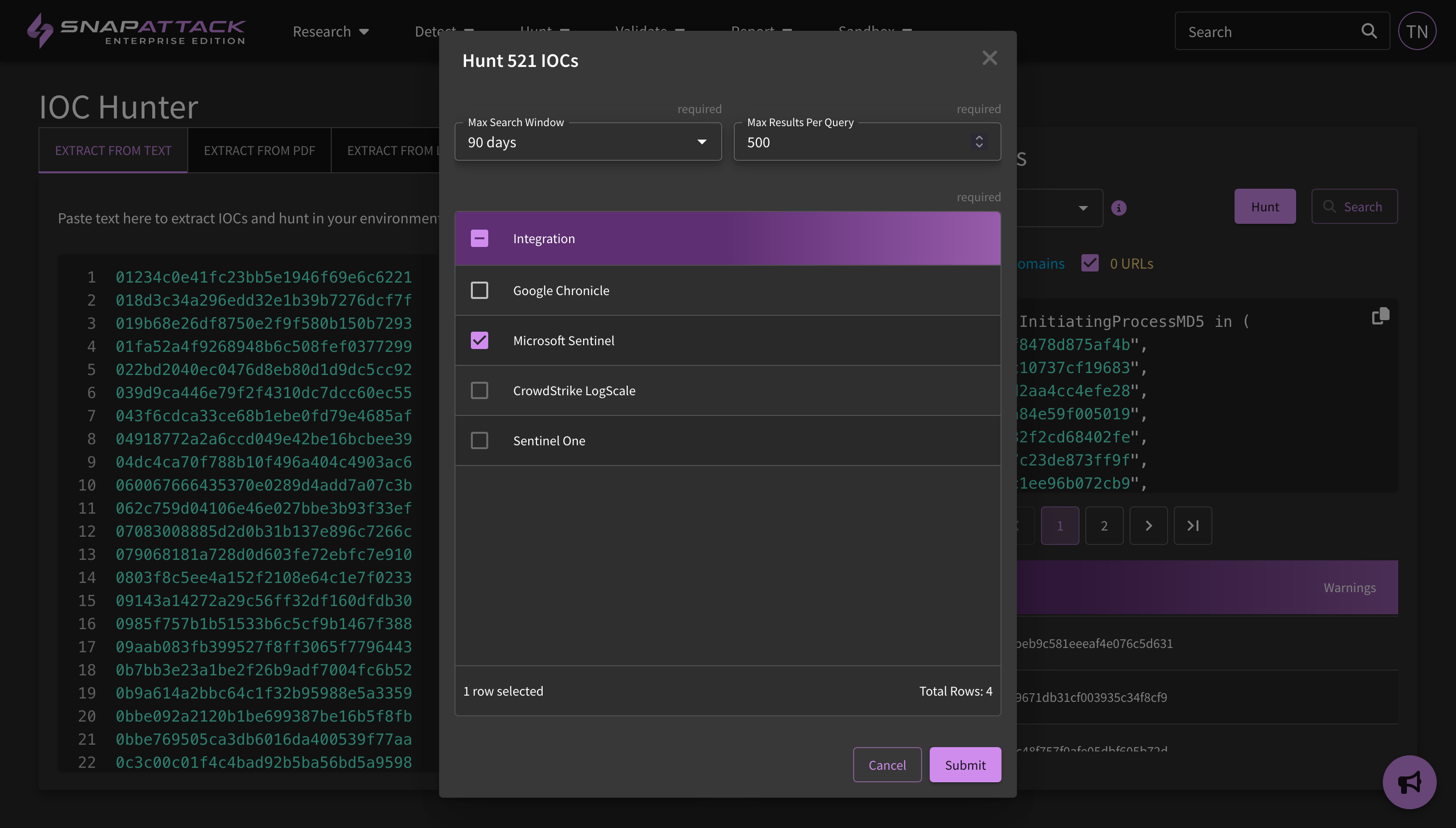
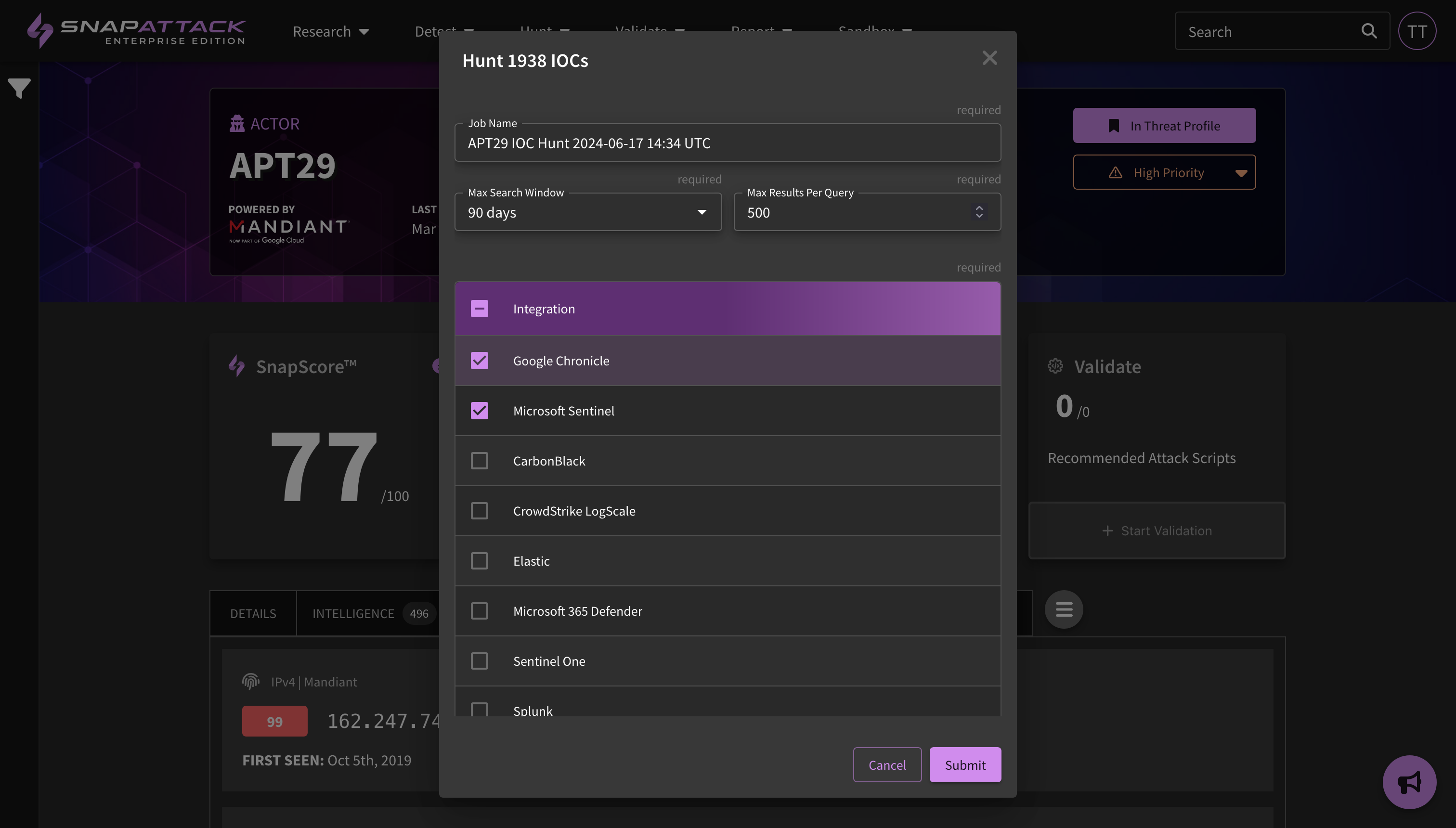
- IOC Hunter: The IOC hunter, which extracts indicators of compromise from text, URLs, and PDFs, has been updated. Search queries are now separated by indicator type, and have more efficient query payloads to search against configured integrations. The new query template can be configured in the integration settings page, and can be more easily customized to your specific environment. Large queries are now also broken up as needed. Finally, indicators can now be hunted just as detections are across one or multiple integrations, with the results being stored in SnapAttack.
- IOC Hunting from Collections: Indicators on threat actor, software, vulnerability, and MITRE ATT&CK collections can now be hunted across configured integrations. Results can be seen in the Hunter's Workbench.
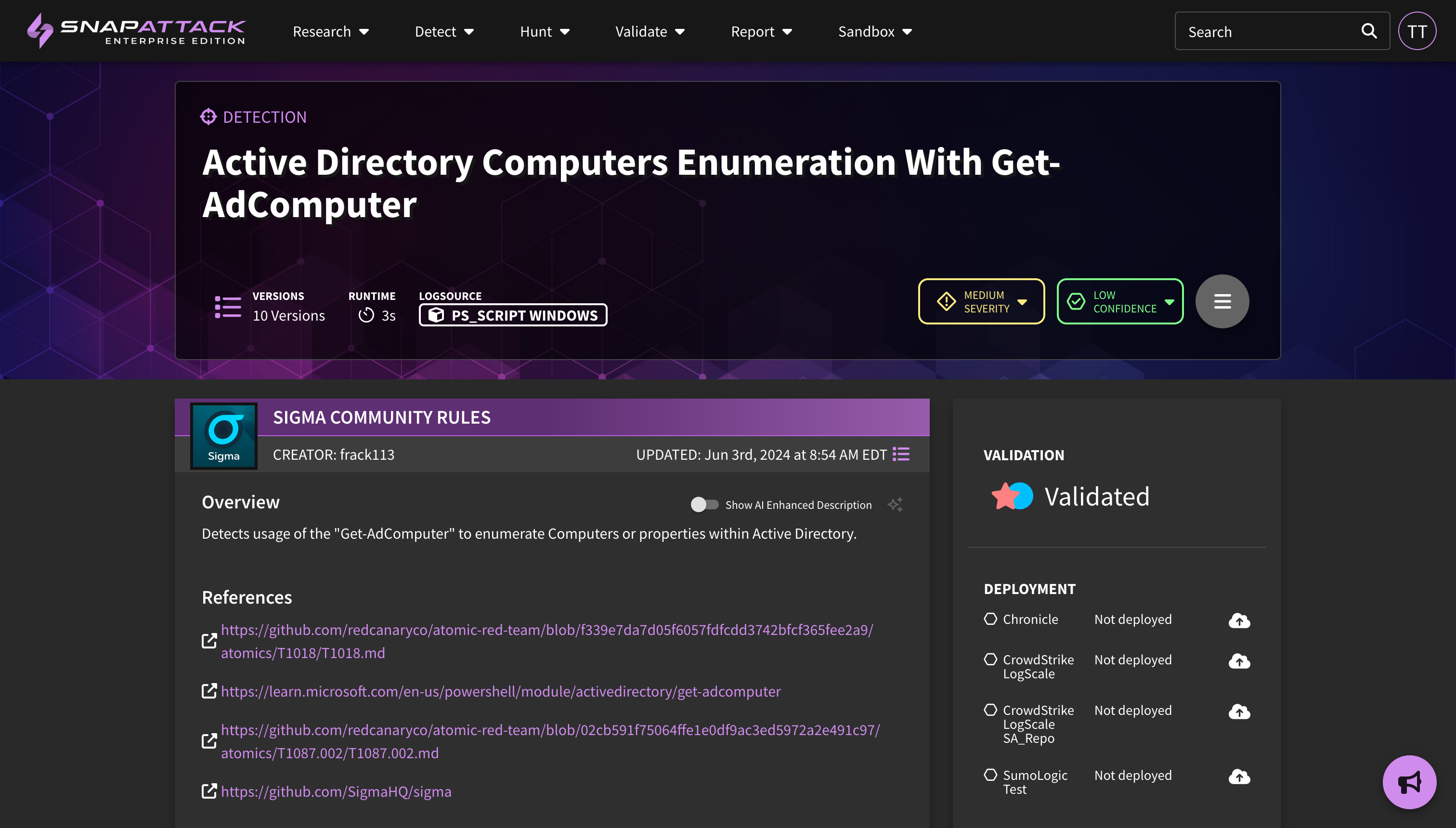
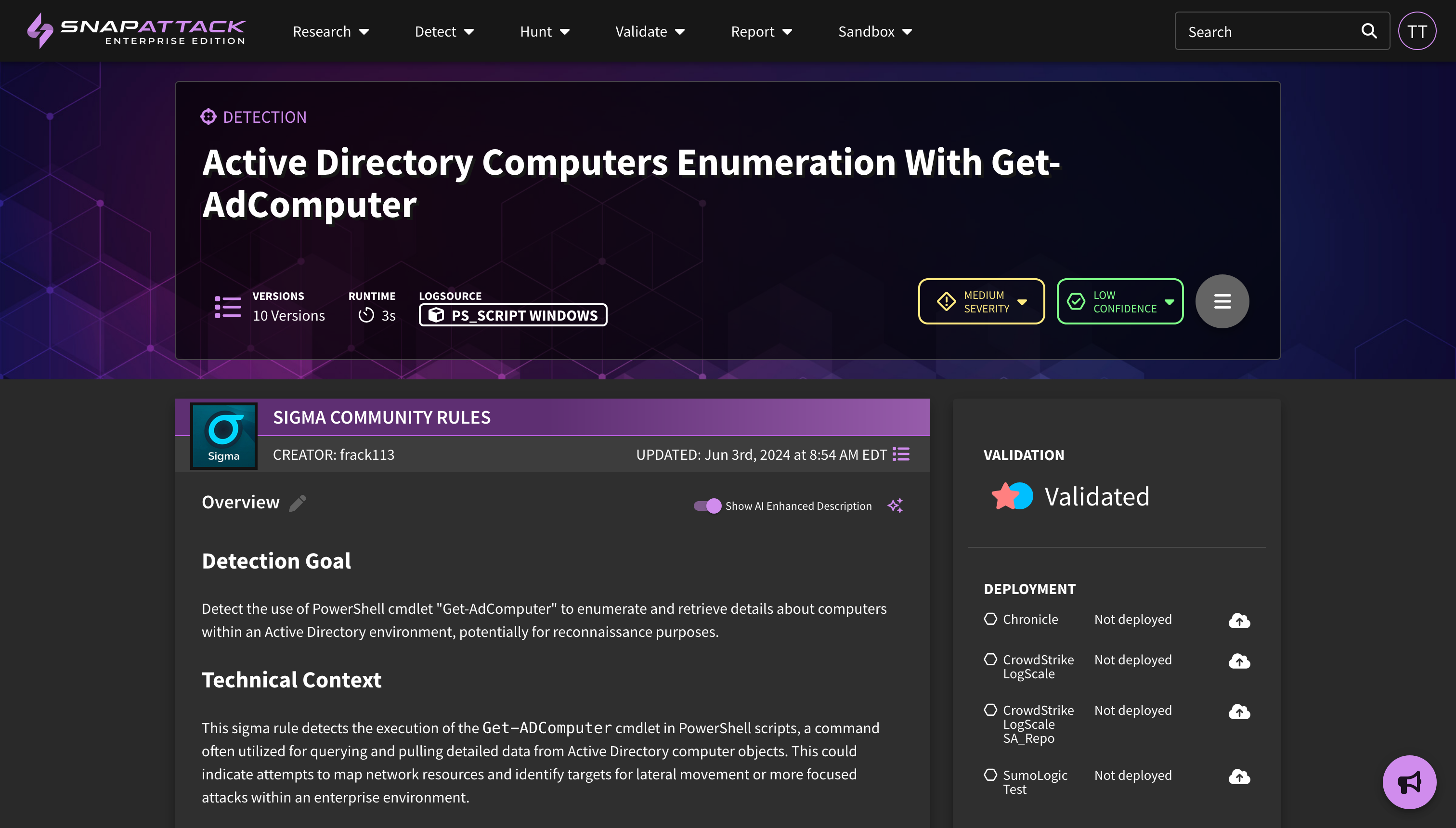
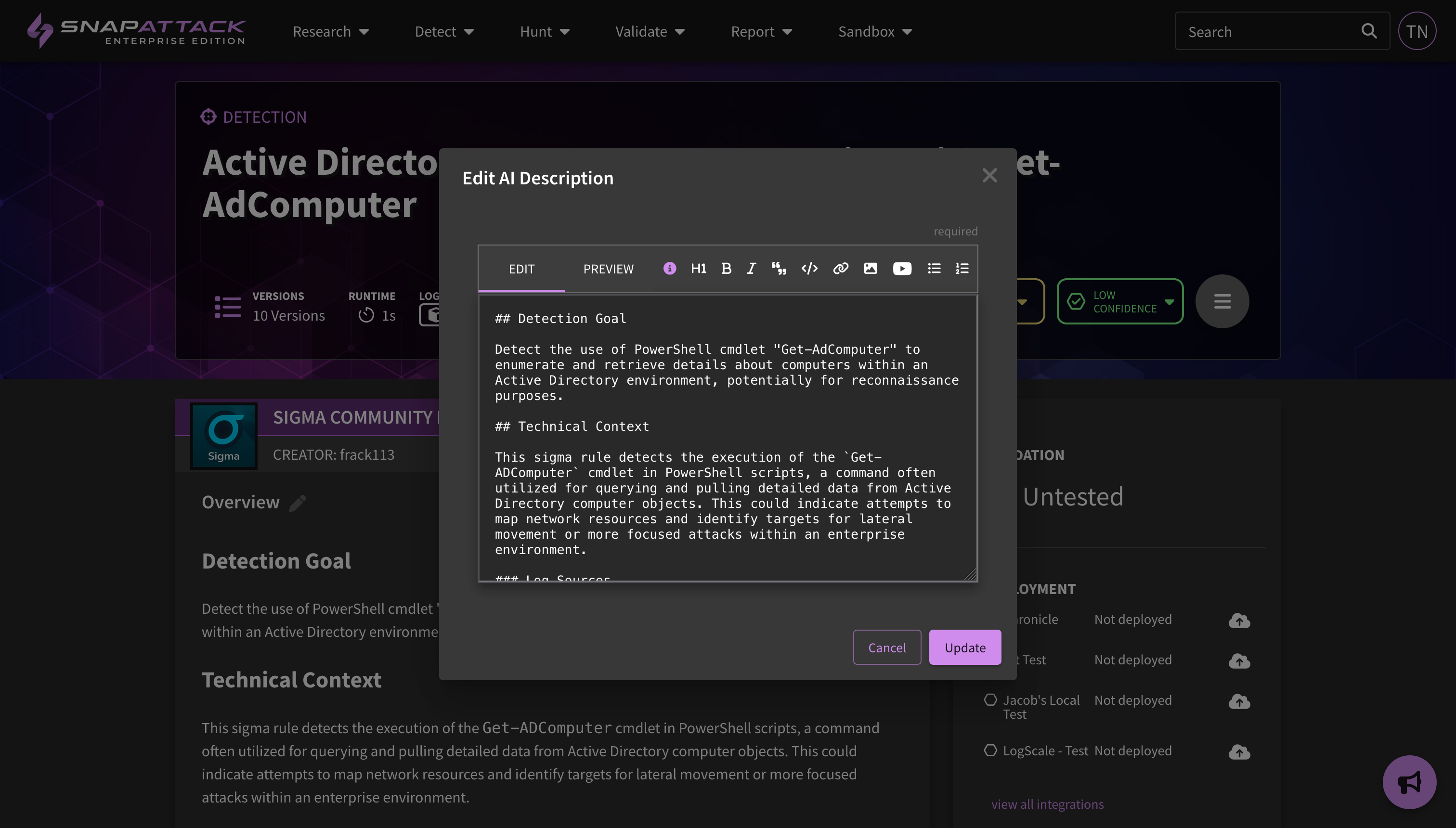
- AI Enhanced Descriptions: Some community detection repositories have poorly documented detections. At one point, we did the math and found the average description length to be about 10 words, most often a restatement of the title. Using large language models (LLMs), and providing context from the detection logic, references, and associated ATT&CK tags, we are piloting the ability to generate enhanced descriptions for Sigma detections. All new Sigma detections, whether brought in from the community repository or created in SnapAttack, will have an enhanced description generated. If your organization owns a detection (or you clone a Sigma detection from the community or subscription repositories), you can generate a description from the action menu on the detection page. The enhanced descriptions will be shown by default if they exist; if you prefer not to see them, you can use the toggle to show the original description. In the coming weeks, we will extend this functionality to all detections in the platform, including historical Sigma detections as well as all native detections.
- Usage of AI / LLM features can be disabled for your entire organization in the organization settings page. Disabling use of LLMs will result in some features not working, such as enhanced detection descriptions, threat intelligence summaries, and inserted tuning logic for certain detections with the new tuning workflow. We understand that some customers may have concerns about data shared with LLMs. We take data security and privacy very seriously; your data will not be used by third-party models for training. If you have further questions about how we interact with LLMs or the data that is shared, we encourage you to reach out to your Customer Success representative.
- Confidence tailoring can now be configured to run on deployed detections. We encourage this action for all configured integrations to ensure deployed detections have their confidence values continuously updated, and are suggested for tuning if there is a change in their confidence or false positive ratio.
- Column ordering on the grid view is now persistent. If you move or re-arrange columns, they will now persist just as the column visibility previously did.
- The user management page can now sort users by their roles. From highest to lowest privileges, this means it will show organization administrators → content administrators → content contributors → read-only users.
- Fixed a bug around metadata, where schema definition changes (e.g., adding an option value to a select dropdown) wouldn't be visible without a page refresh.
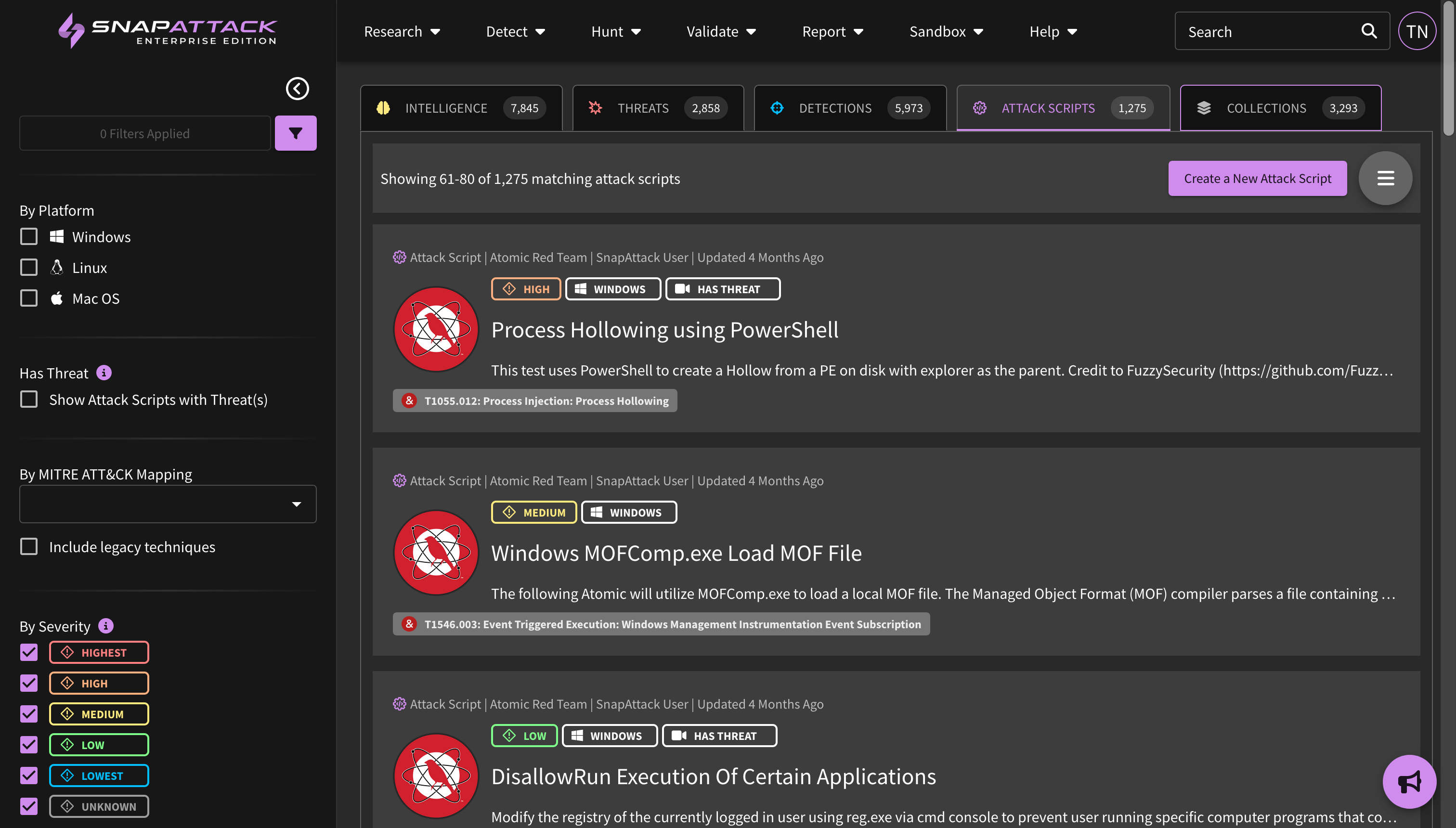
- Updated the attack script recommendation algorithm for threat actor, software, vulnerability, and MITRE ATT&CK collections to prioritize attacks based on configured agent operating systems and relevance to the organization.
- General bugfixes and stability improvements to enhance the user's experience.
2024.05.06
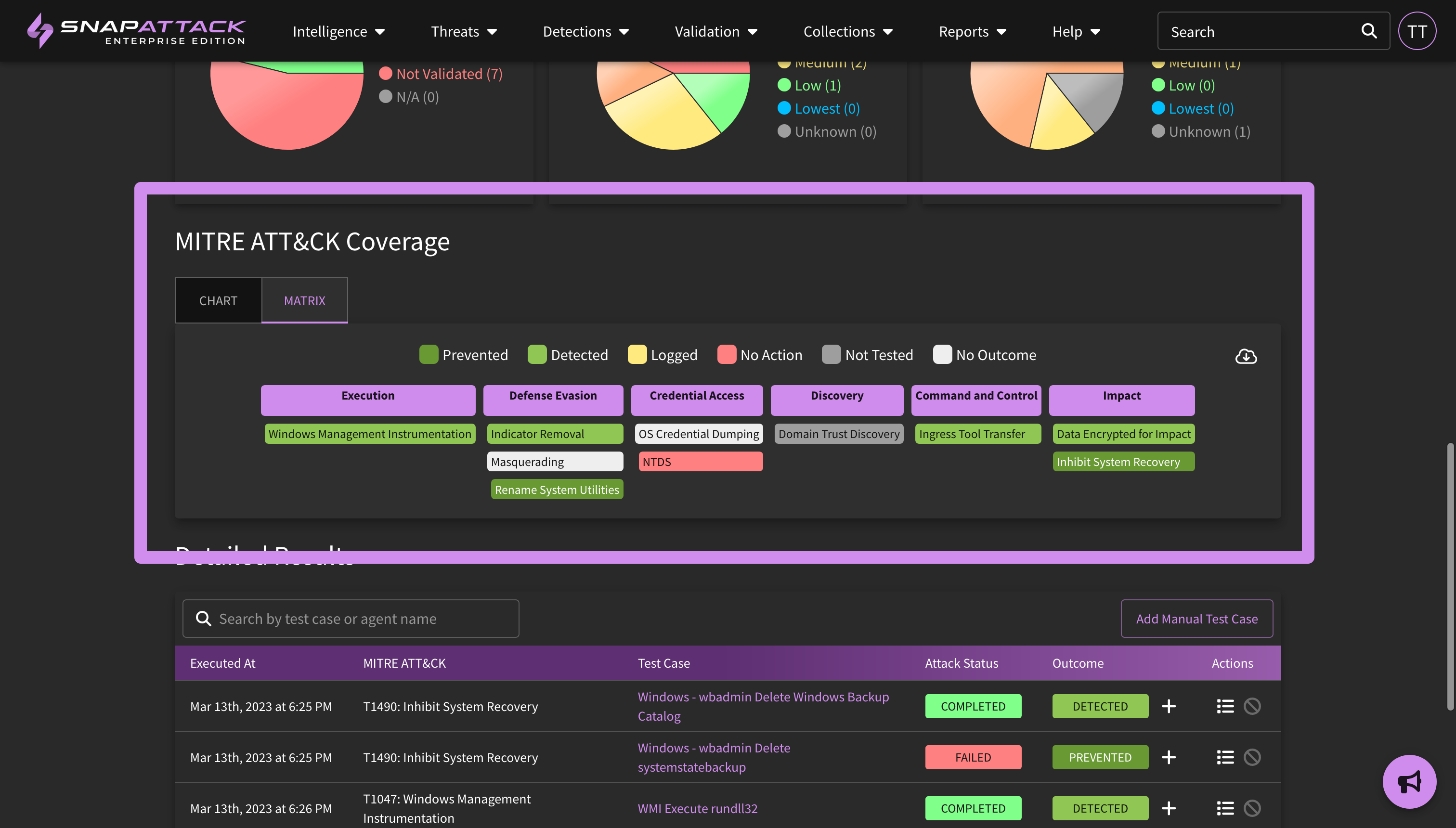
- Added threat profile filters to the ATT&CK matrix page, allowing technques to be sorted and colored by their priority in the threat profile. Displaying coverage by priority will be coming in a future release.
- General bugfixes and stability improvements to enhance the user's experience.
2024.05.03
- MITRE ATT&CK v15: SnapAttack has been upgraded to using ATT&CK v15.1. Techniques that have been revoked or deprecated are automatically updated as part of this process. New techniques have had default severities mapped. To learn more about this update, review the ATT&CK release notes.
- General bugfixes and stability improvements to enhance the user's experience.
2024.05.01
- Added integration support for Sumo Logic. Customers who have Sumo Logic as a SIEM can now deploy, hunt, and confidence tailor detections automatically via API integrations.
- Added support for pySigma, which will run side-by-side the legacy sigmac compiler in the platform. Integrations will be converted over to the new pySigma format over the coming weeks. This process does not require user interaction, and should ultimately be transparent to users. There should not be any breaking changes to detection compilations or drop in the number of available detections. This feature does not impact detections that are written in a native language (e.g., Chronicle YARA-L, Splunk SPL, Azure KQL, etc).
2024.04.05
- Updated the Microsoft Sentinel integration to support alert grouping.
- Added an organization filter to the threat timeline to see detections that belong to a specific organization.
- Added the ability to see the Splunk client application version in the integration settings page.
- Fixed the MITRE ATT&CK navigator export by upgrading the JSON schema to the latest version.
- Deprecated and removed the "customization" tab in the detection builder, which will be reintroduced as part of a more holistic tuning workflow.
- Multiple improvements to the threat profile and collection recommendation algorithms.
2024.04.01
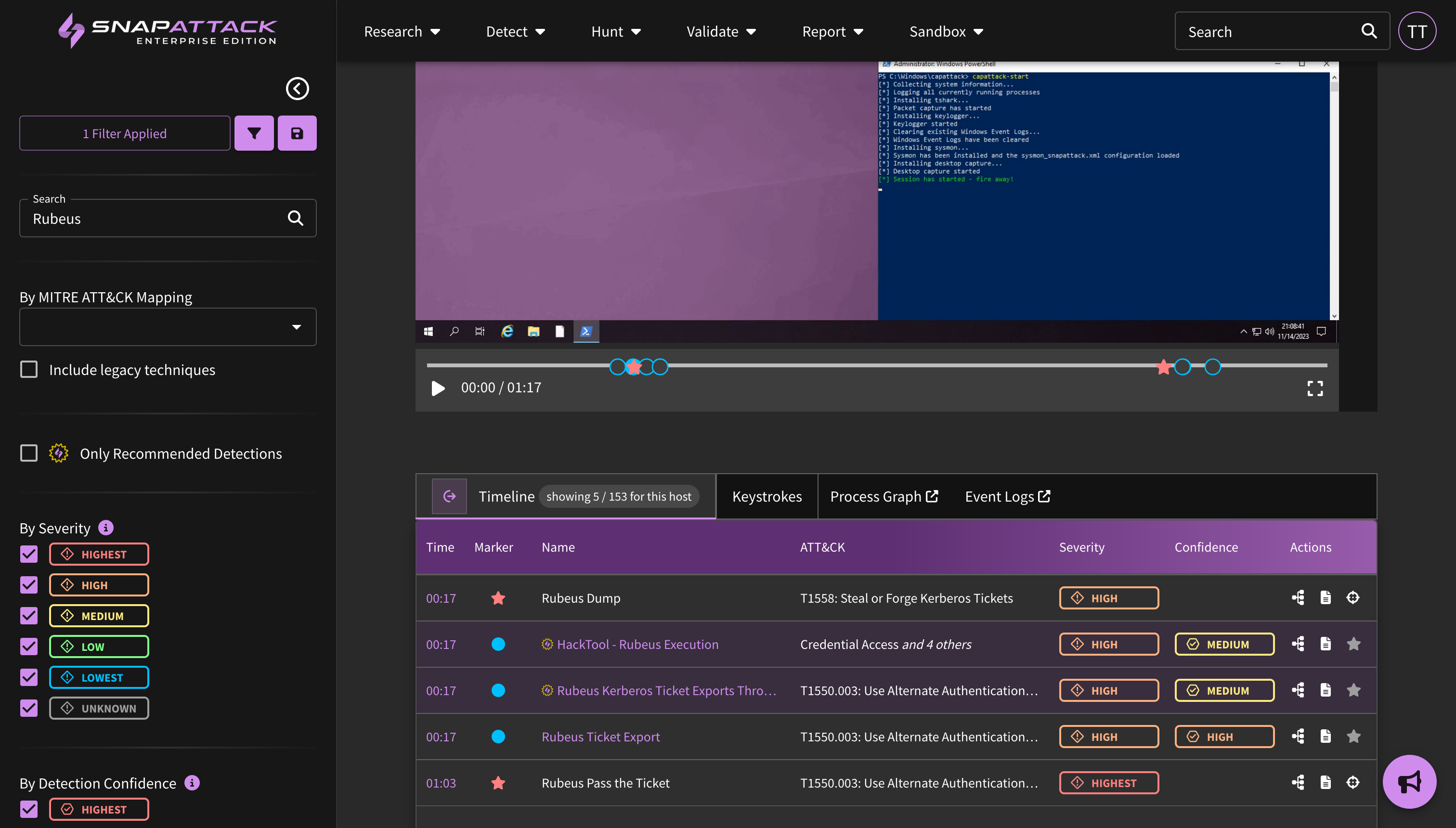
- Updated the attack range to allow better copy/paste for clipboard data, the ability to quickly send common keystroke combinations (e.g., CTRL + ALT + DEL), and dynamically resize the virtual desktop if the browser resolution changes.
- Added the ability to export raw threat capture file archives, which contain the event log, PCAPs, and other telemetry data. This can be accessed via the "Export" button in the table below the videos on the threat page. This feature is not enabled by default; if you would like to utilize this feature, please reach out to your sales or customer success representative.
- Added "Last Seen" date for software (malware/tools). Software can be sorted by when it was last seen to be used by any threat actors. The last seen date is also utilized when recommending relevant software in your threat profile.
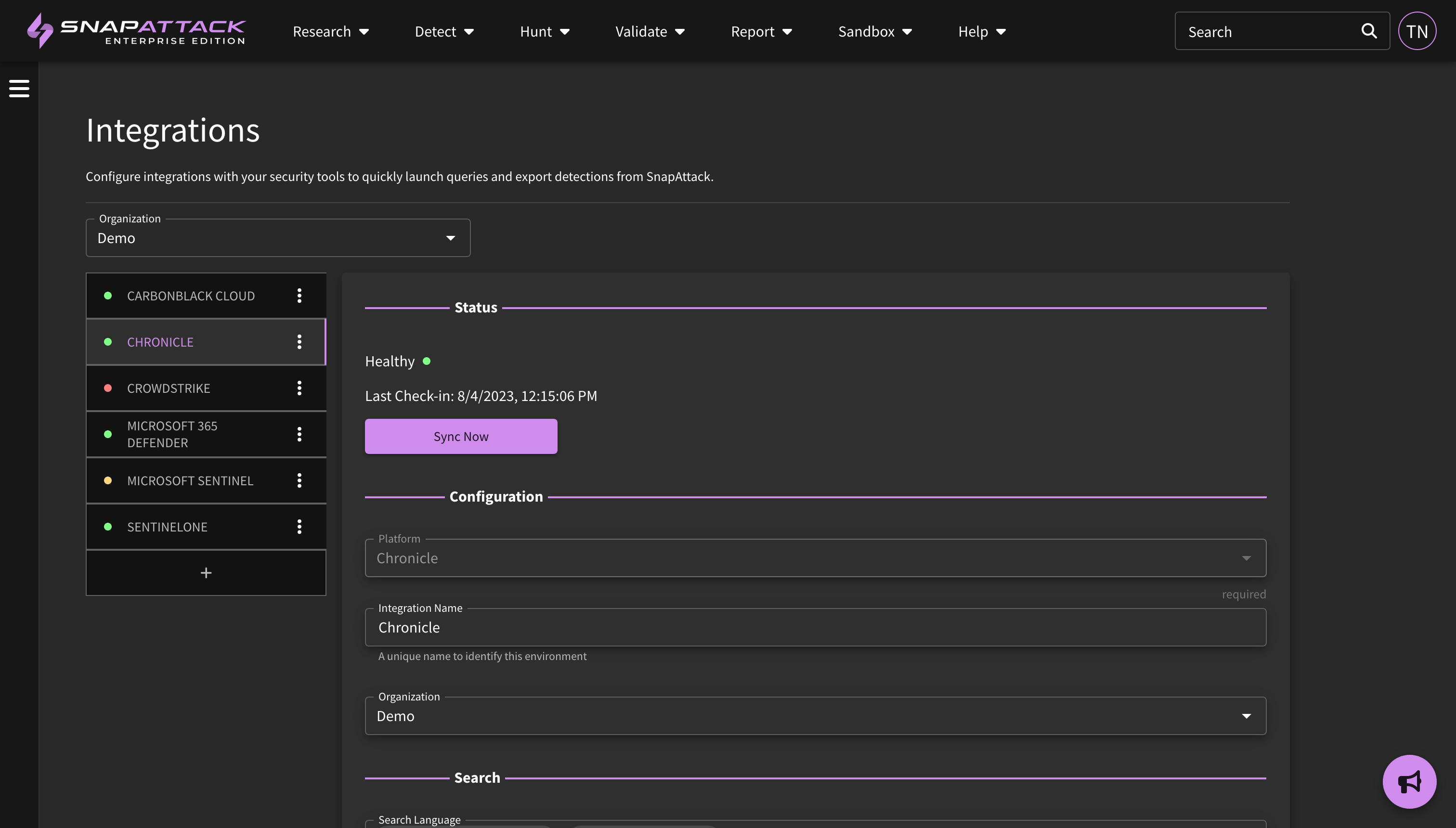
- Added support for regional endpoints for Google Chronicle to deploy detections to one or more specific regions.
- Added the ability to see an API key's creation date, last used date, and the user it's assigned to in the UI. Previously, a user could only see a list of their own API keys. This improves troubleshooting when an attack simulation agent or integration is configured using a specific user's API key. Users still will only be able to view and edit their own keys.
- Fixed a crash with the detection diff viewer where occasionally a version identifier was not specified.
- General bugfixes and stability improvements to enhance the user's experience.
2024.03.04
- Multiple updates to the hunt and task pages. Performance is improved with new API endpoints. Additional information is displayed about the tasks, such as the initiating user, progress percentage, and estimated time remaining. Results are also displayed for in-progress tasks. Standardized several status between hunt and attack simulation tasks.
- Greatly improved the scalability and reliability for large hunt and confidence tailoring tasks.
- Added the detection logsource to detection page, and updated the badges for native detections to represent which language the detection is written for.
- Updated the algorithm for recommending detections from an attack simulation to include more possible detections. This results in better and more accurate outcome determination, at the cost of speed for integrations that have query rate limits. Fixed a bug in which outcome determination could not be re-launched if the task had originally failed.
- Multiple integration improvements, including:
- Fixed compilation and translation errors for Carbon Black Cloud.
- Support the new Graph API for Microsoft 365 Defender. Customers with this integration will have to update permissions to use this feature. Please reach out to your customer success representative for further instructions.
- Updated the Splunk application to send incremental status information to report on in-progress tasks back to SnapAttack.
- Re-enabled bi-directional detection sync for Google Chronicle.
2024.03.01
- Improved the logsource selector in the Detection IDE, making it easier to search across all available logsources. Additional logsources will be added in an upcoming release.
- Increased performance for viewing Attack Simulations jobs and results.
- Added the ability to view recommended detections, hunts, and attack scripts inside regular collections, as well as the SnapScore towards completing the recommended actions.
- General bugfixes and stability improvements to enhance the user's experience.
2024.02.07 Major Release
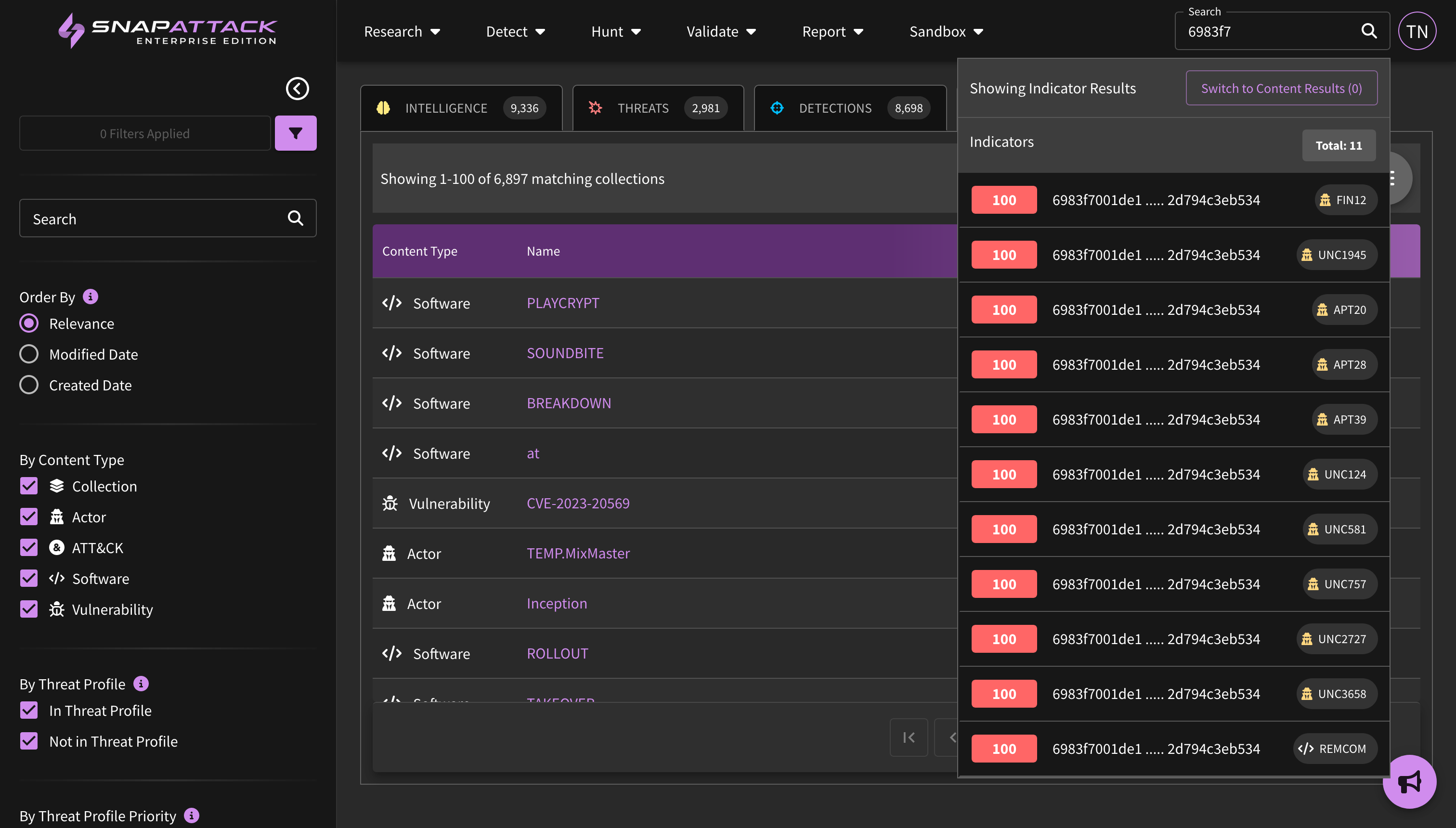
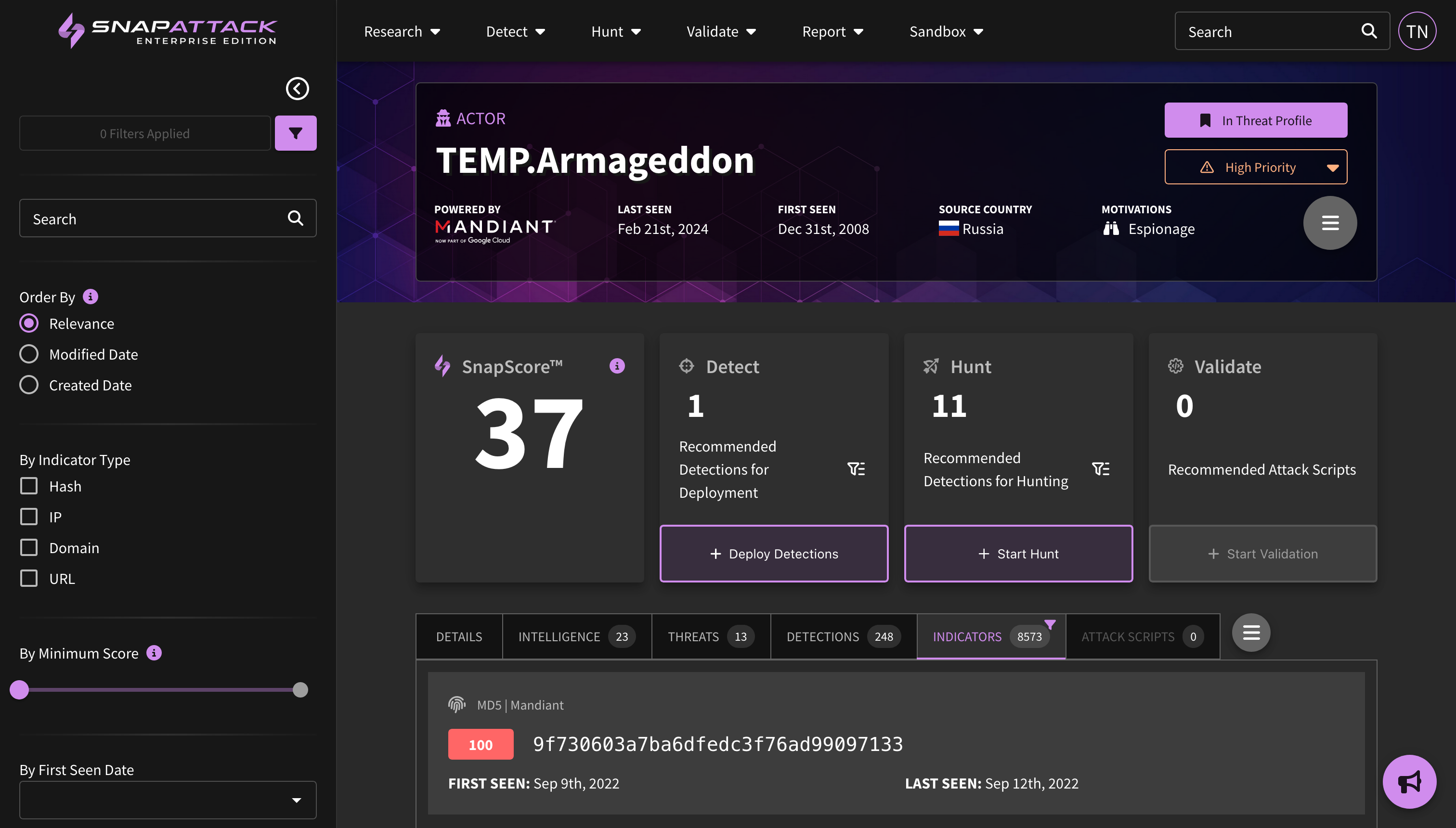
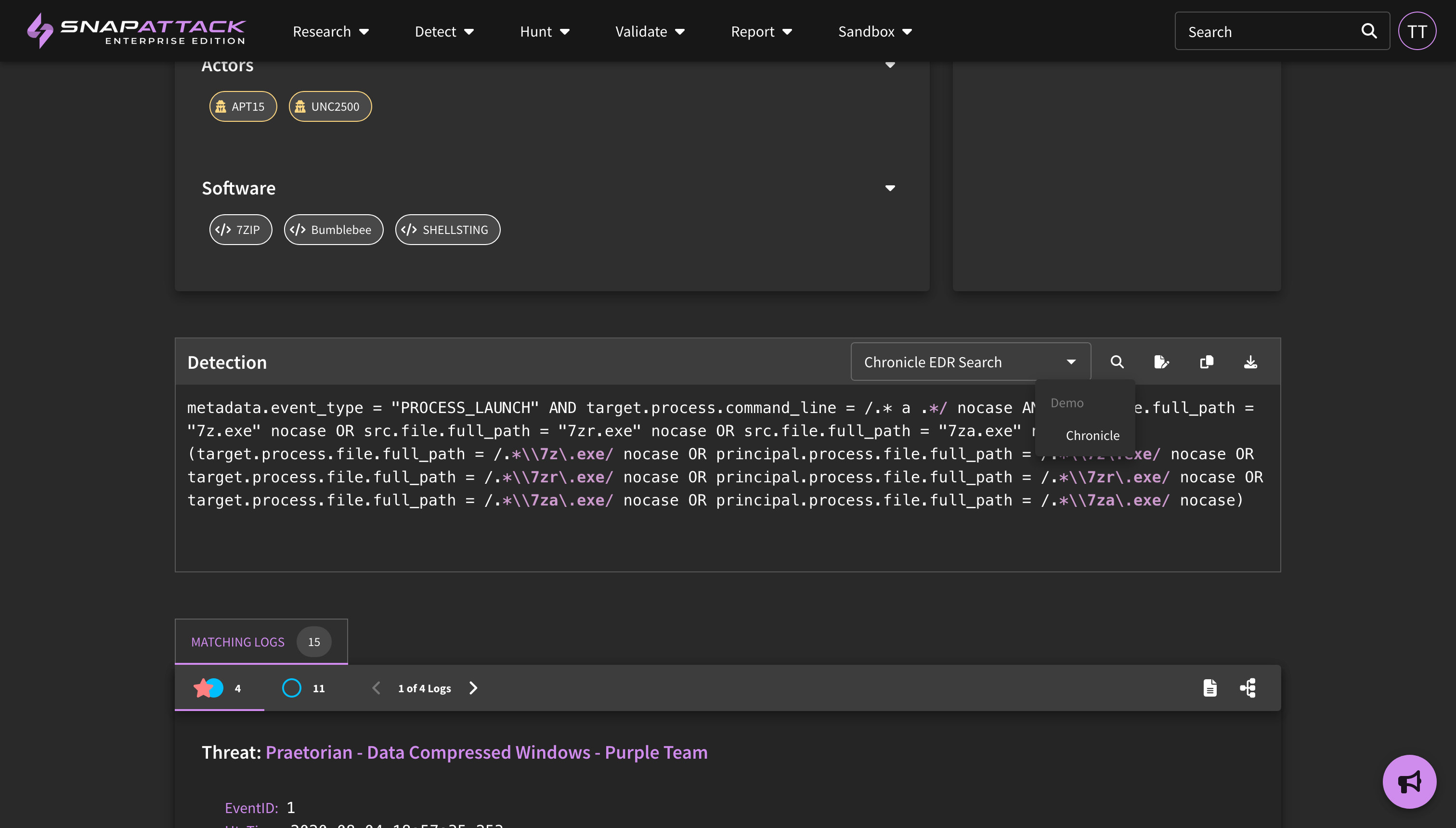
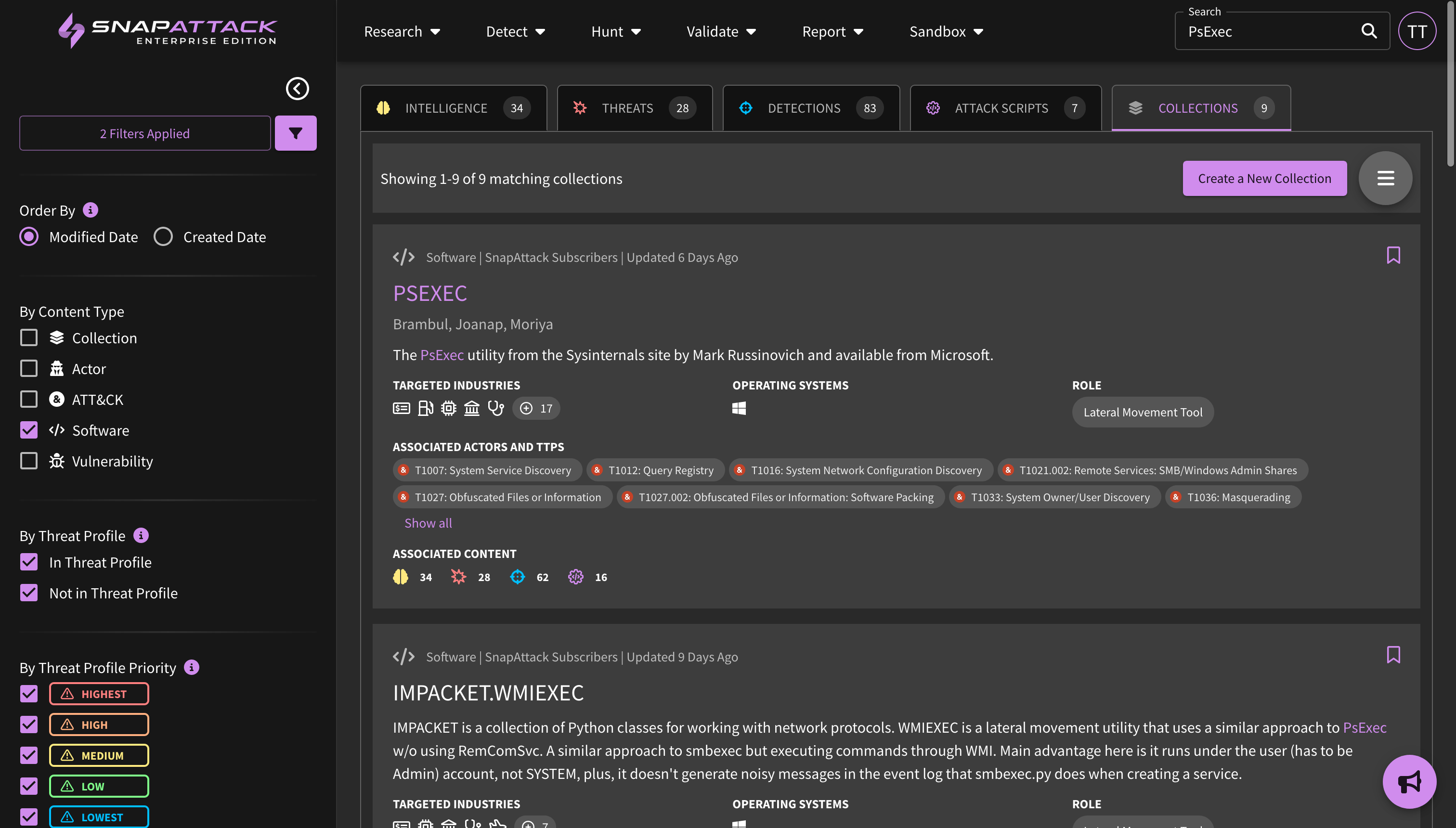
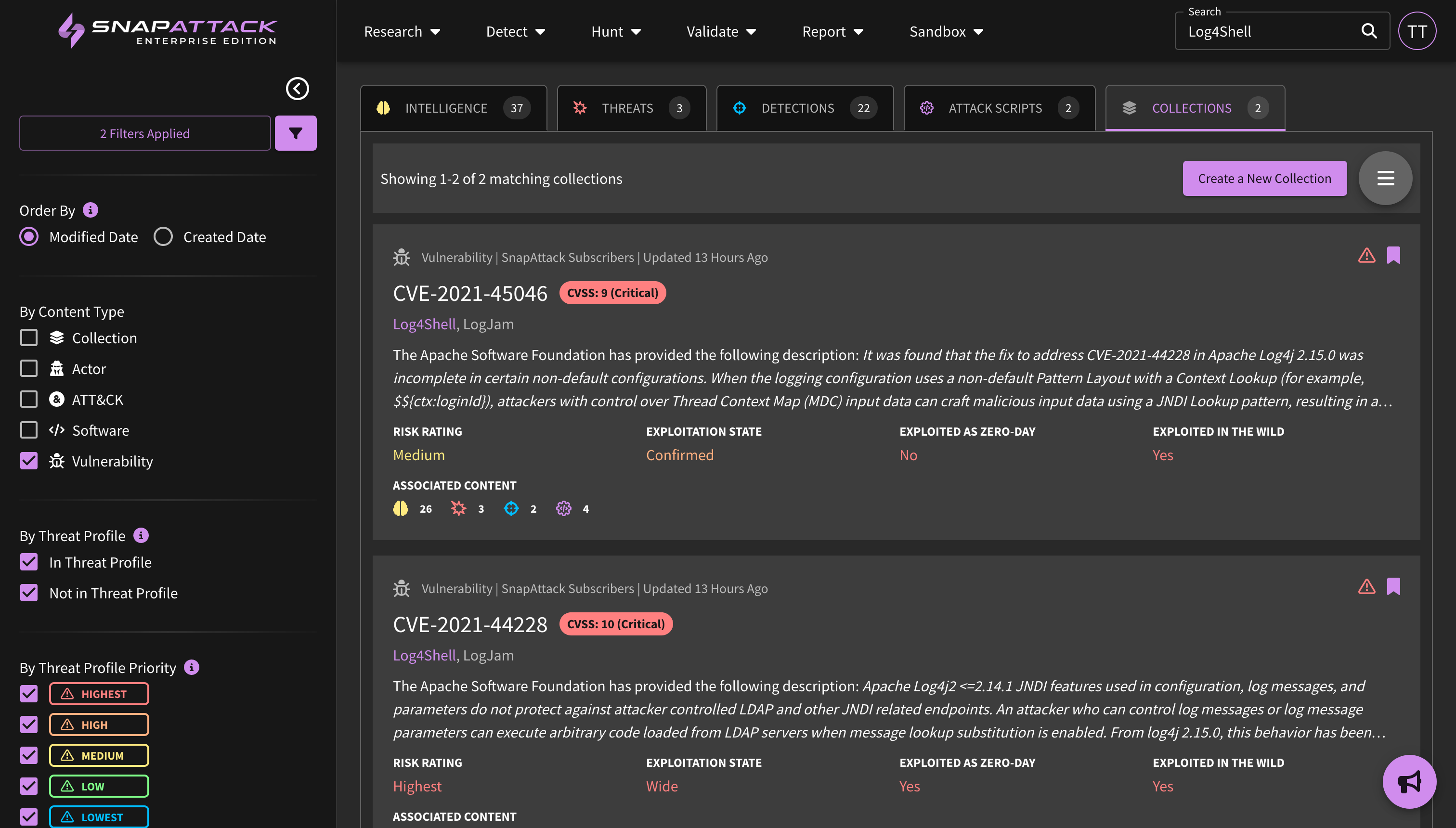
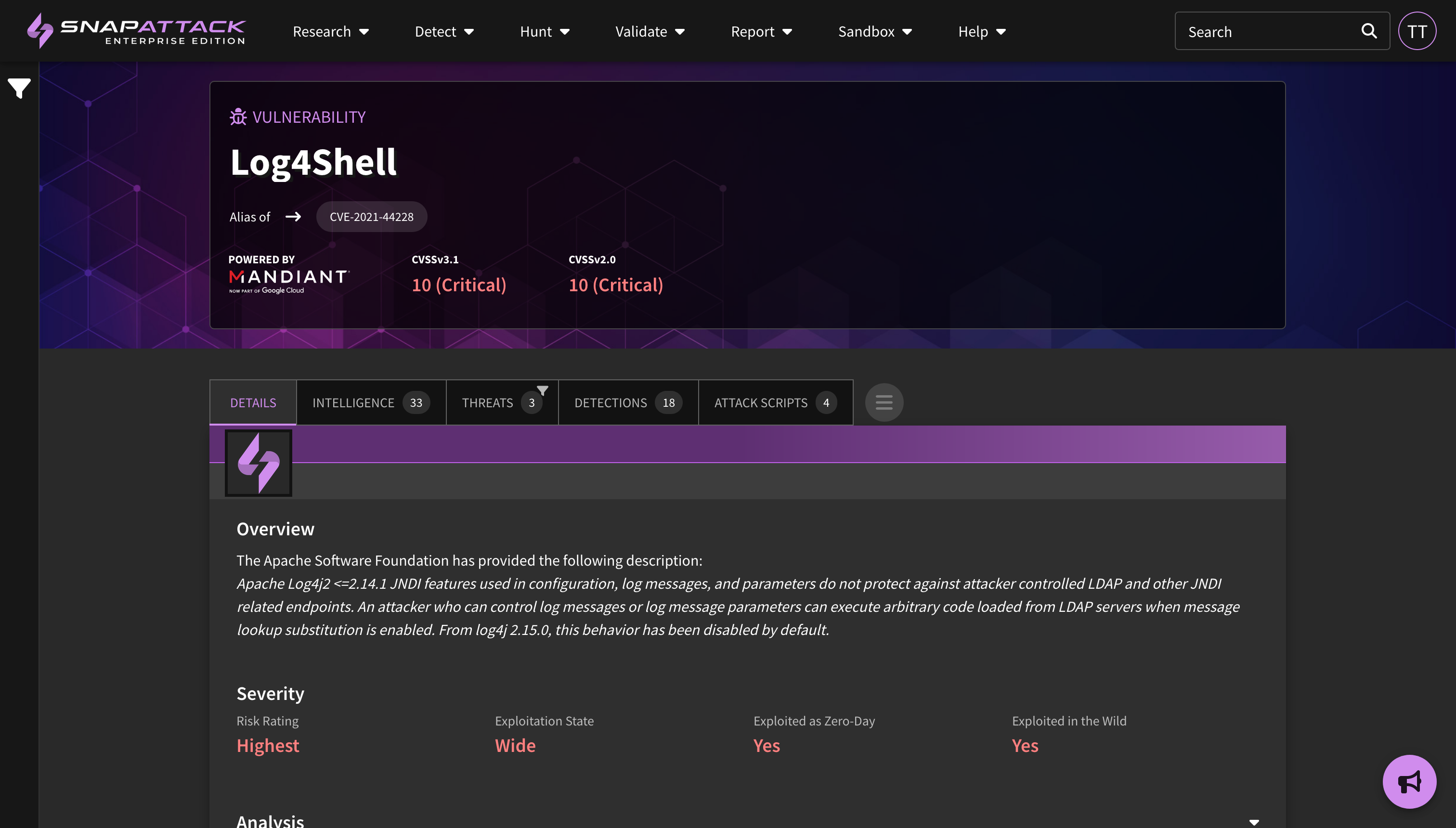
- Indicators of Compromise (IOCs): Indicators have been added to threat actor and software collections from our partnership with Mandiant (now part of Google Cloud). Users can search indicators across all collections from the navbar search. Indicators can be filtered by their first seen and last seen date, maliciousness score, and indicator type. Users can also export indicators to a CSV for ingestion into other platforms. Indicators are not included in all subscription plans; for questions, reach out to your sales or customer success representative.
- Beta Features: Design partners and customers can now more easily access beta features live in the application. Organizations who opt-in to the beta channel will receive early access to features that are nearly completed in development, the first two of which can be seen below. Please reach out to your customer success manager if you would like your organization to receive beta features.
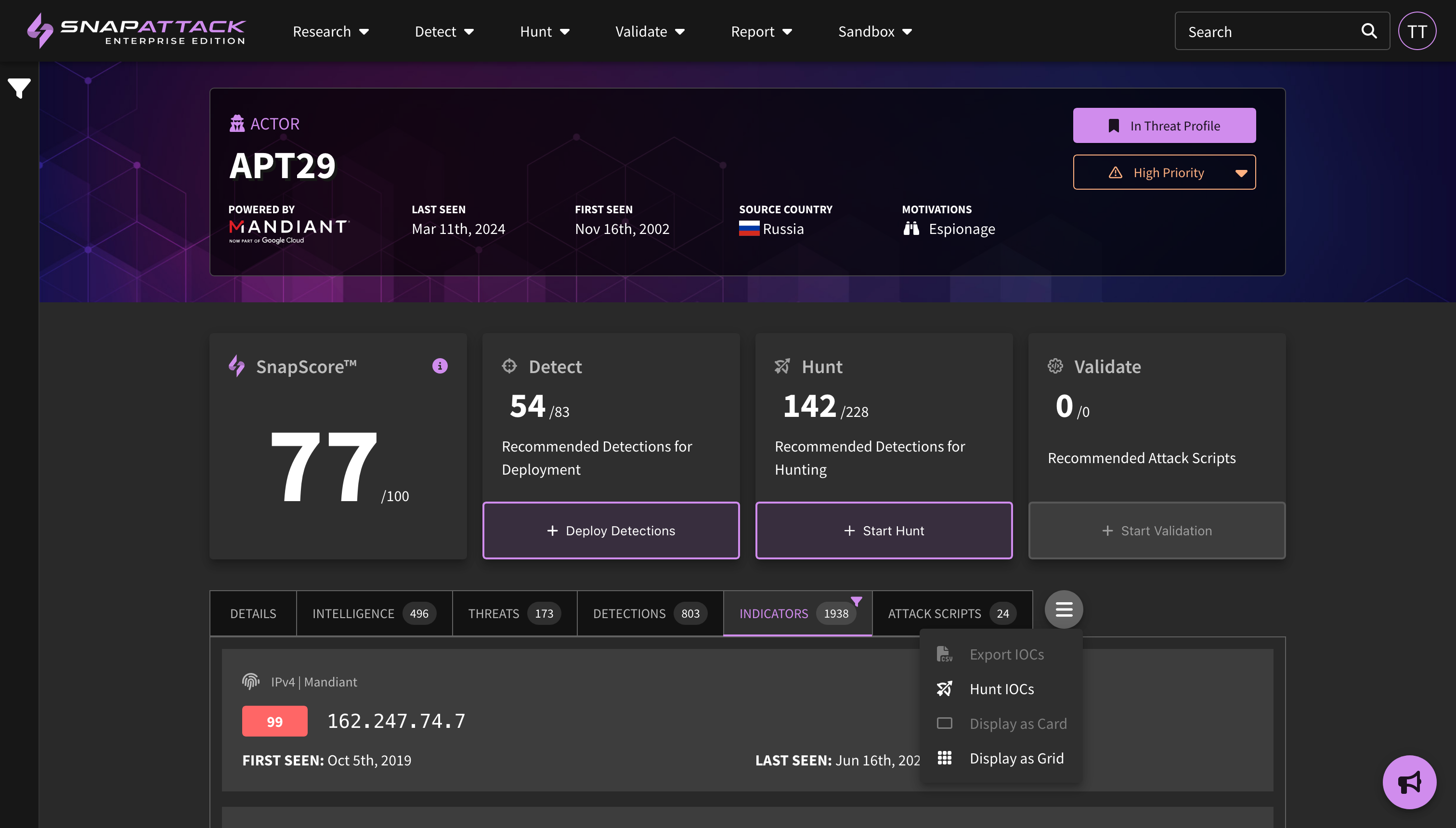
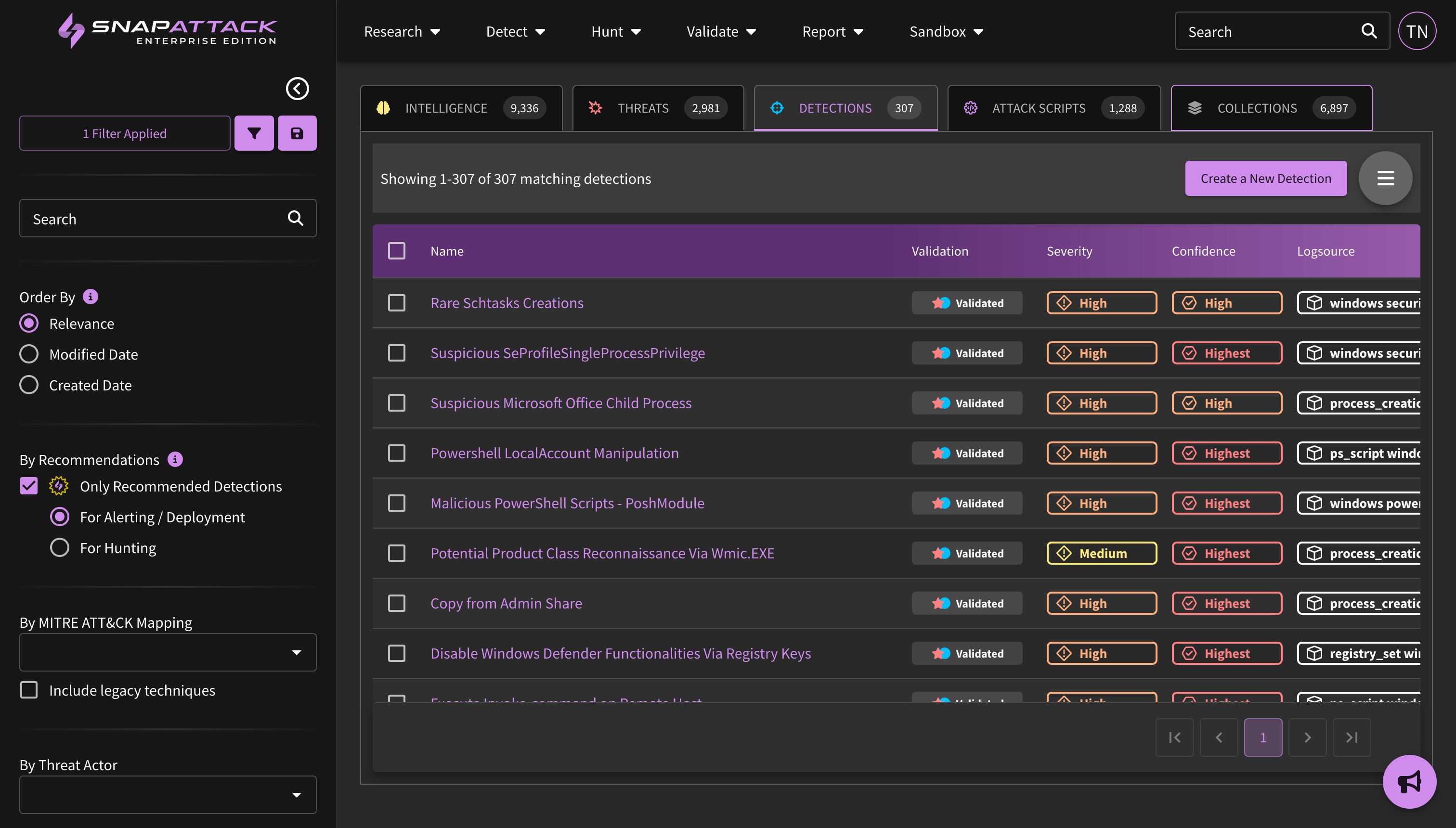
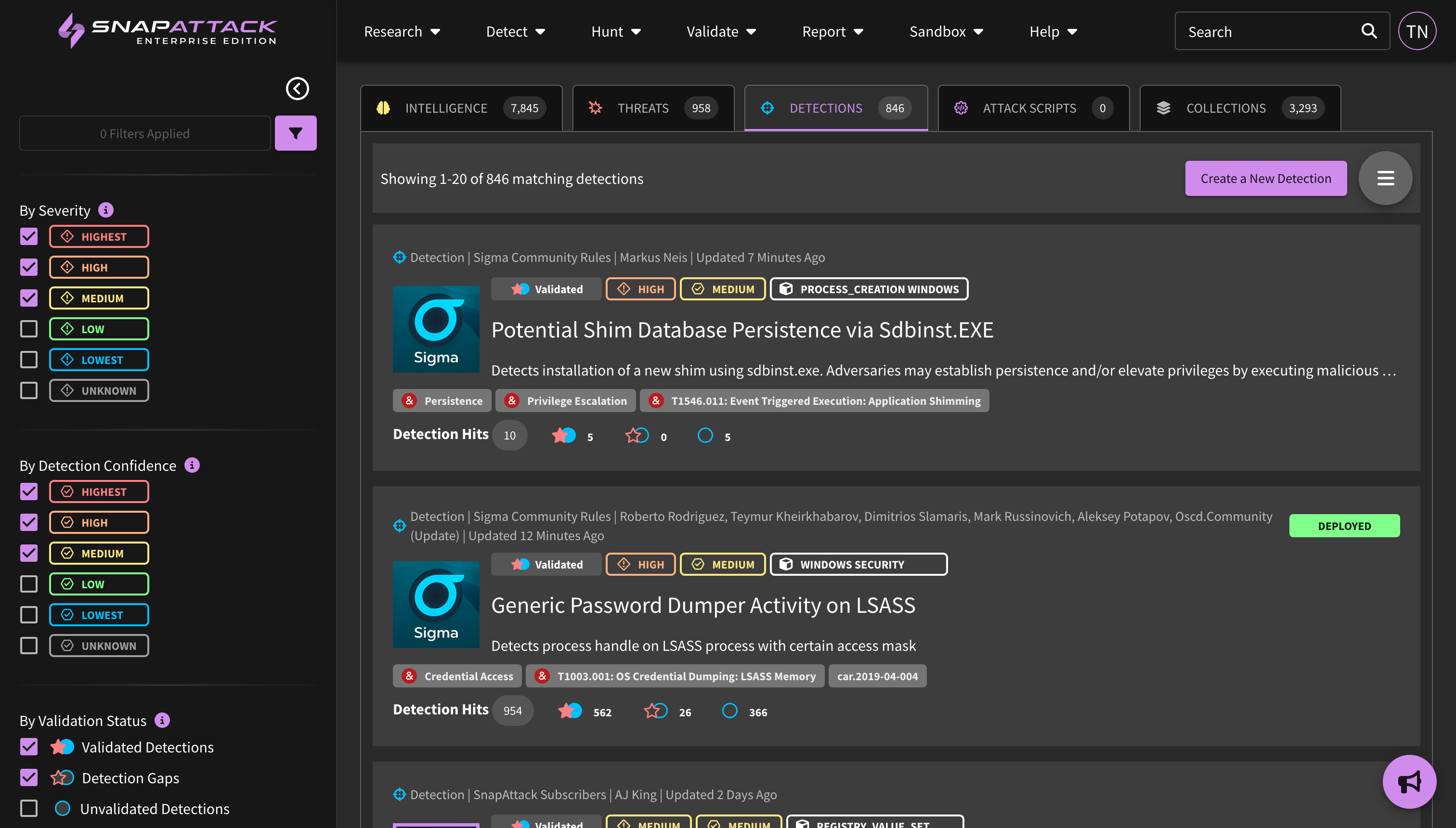
- Sitewide Detection Recommendations (Beta): Powered by threat profiles, users can now see and sort recommended detections by use case (for deployment/alerting or threat hunting) across the entire library. This allows users to see the best detections across collections. Behind the scenes, we calculate a recommendation score based on the priority of the collection in your threat profile, the number of threats that detection is recommended for, and all of the other weighted filters for recommending a detection in general (confidence, robustness, logsource availability, compatibility with existing integrations, etc).
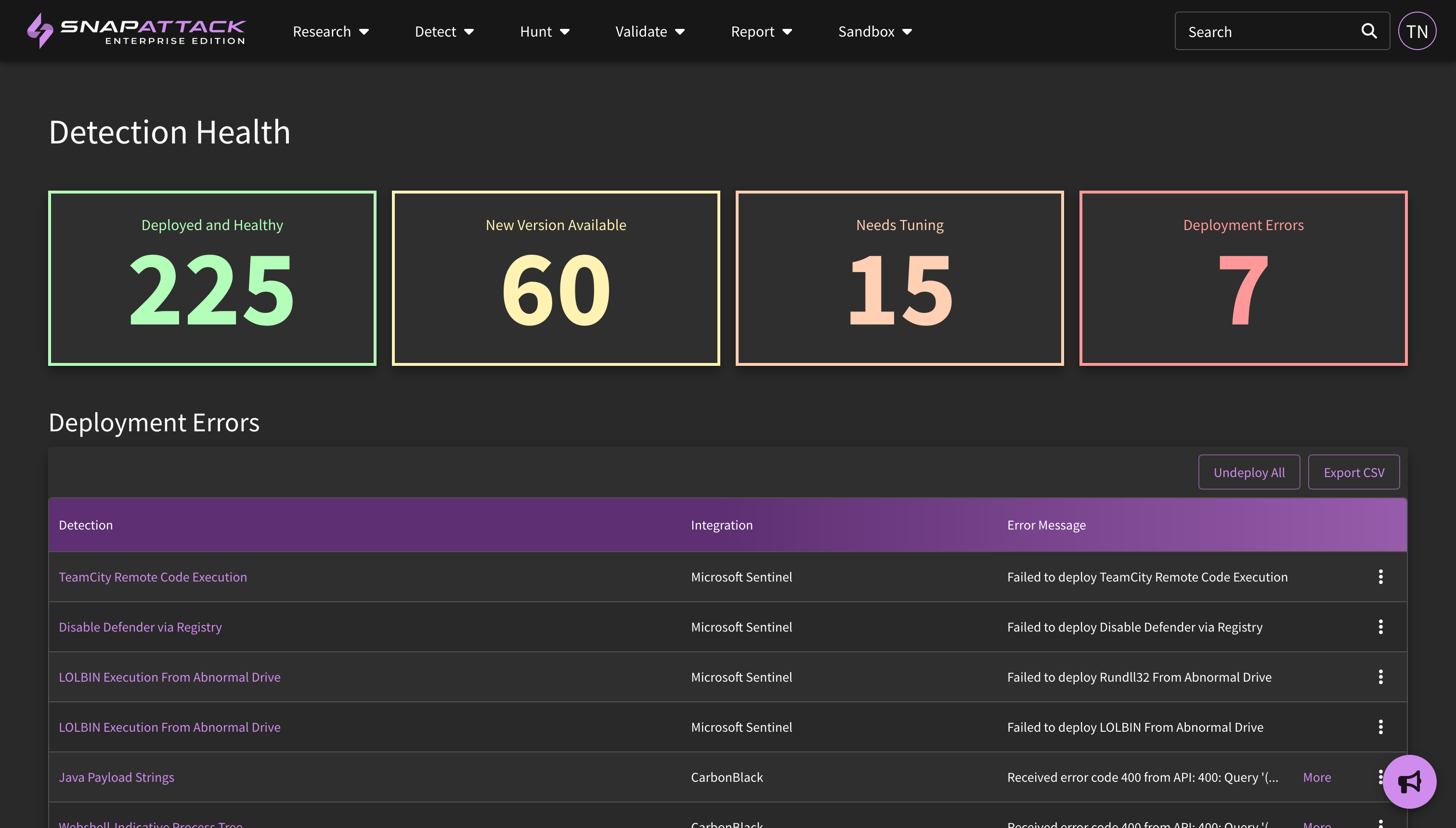
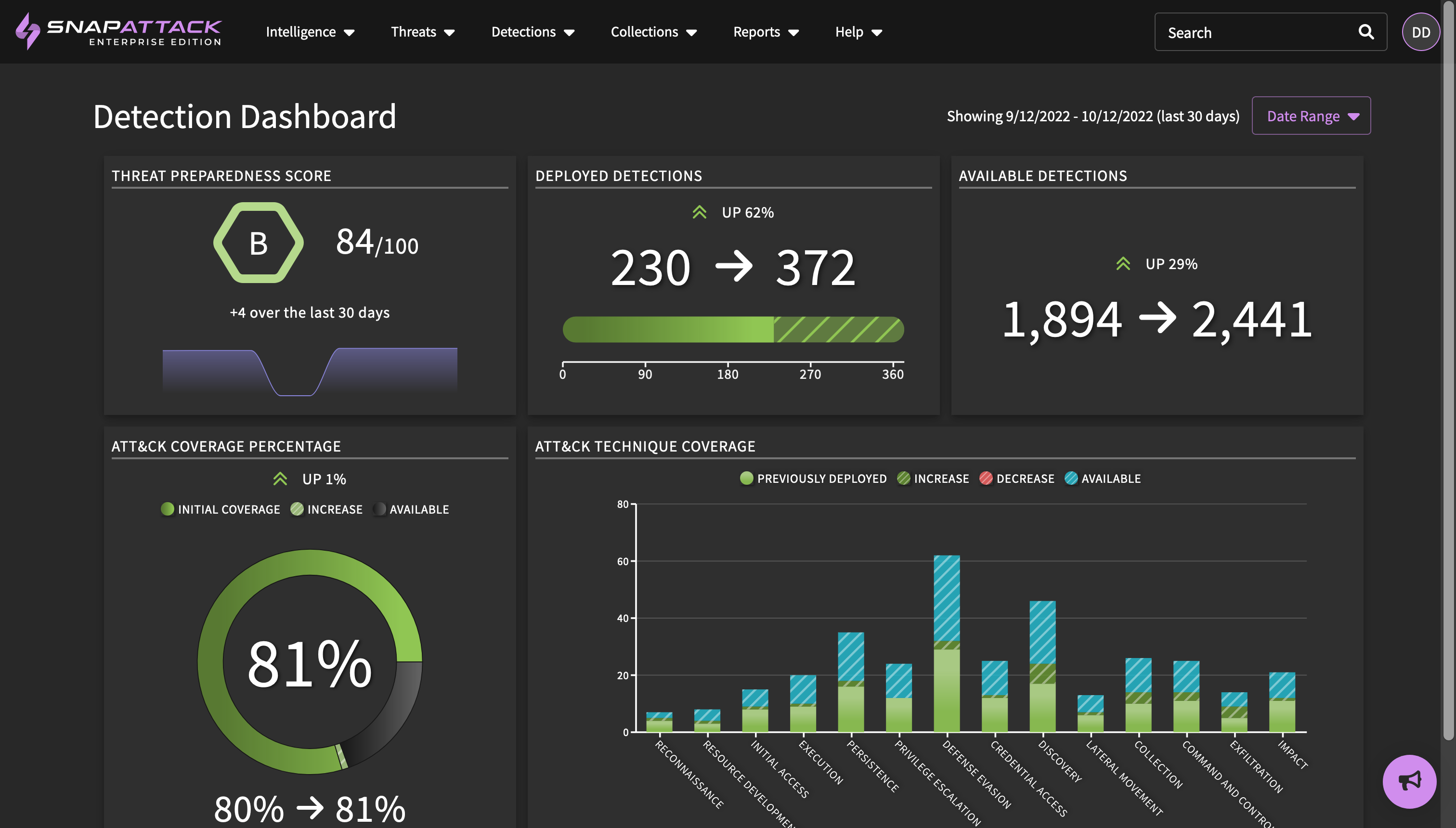
- Detection Health Dashboard (Beta): Customers can now more easily track deployed detection health across integrations. This dashboard reports on the number of detections deployed successfully, deployment errors, detections that need tuning, and detections with outdated logic, as well as tools and workflows to address detections in each state.
- Improved full-text search for aliases of actors, software, and vulnerabilities to return more relevant results. Aliases are also now shown in search results to provide context as to why that result was returned.
- Added missing filters for threat actors, software, and vulnerabilities on attack scripts.
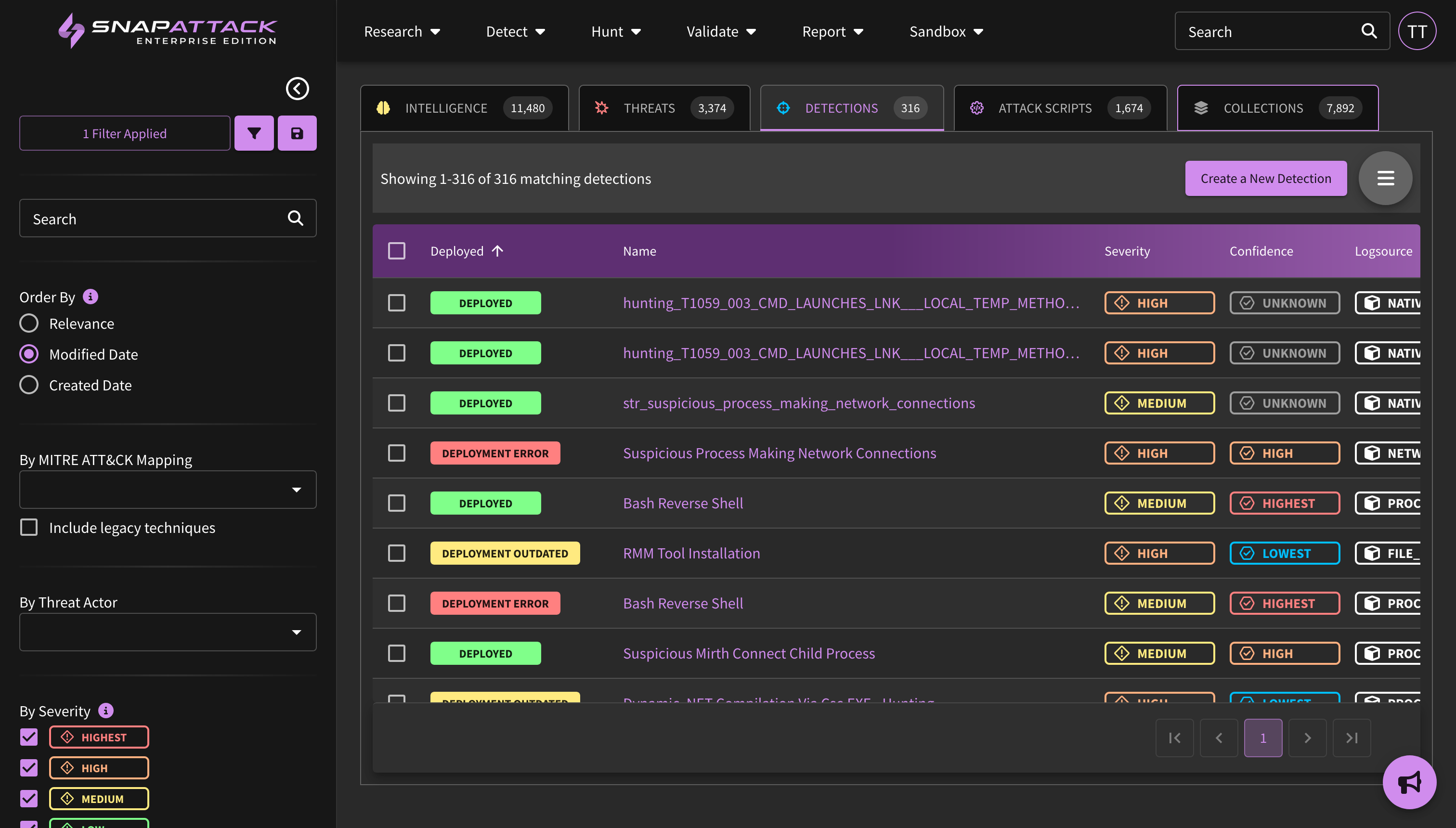
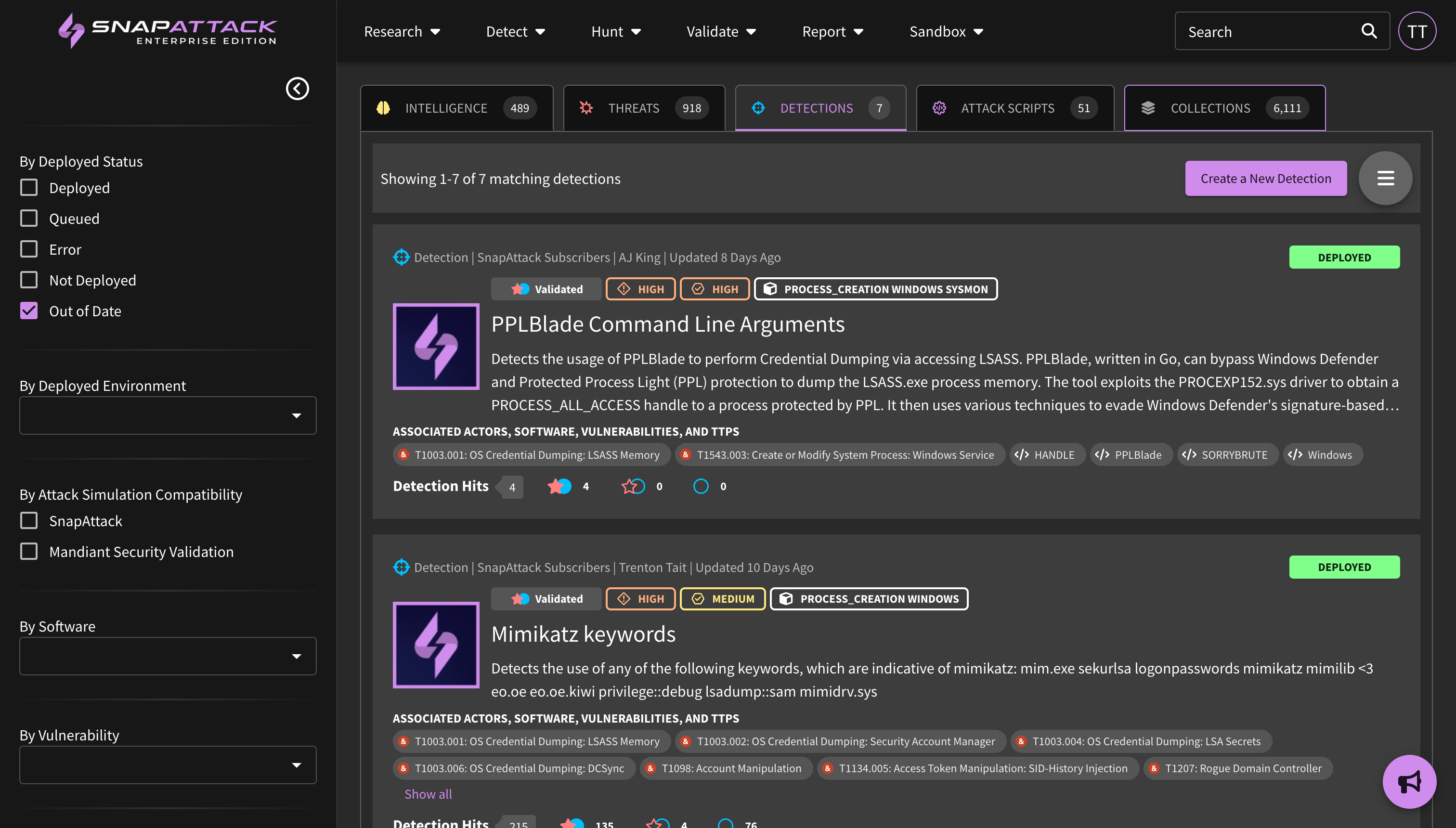
- Added a badge to the feed for outdated detections. Badges show the "worst" state to intentionally surface potential problems, and are shown in order from Deployment Error → Deployment Queued → Deployment Outdated → Deployment Success.
- Hunt results can now be exported to CSV from the workbench or the detailed hunt results page.
- Fixed a bug where global confidence values may have been incorrectly calculated, resulting in more "unknown" values than expected.
2024.02.04-06
- Fixed a bug that prevented hunts from being launched if there were no advanced configurations for the integration.
- Fixed a bug which caused certain languages to not show on the configuration page.
2024.02.03
- Scheduled Hunts: threat hunts can now be configured to run at a defined frequency, for example every two weeks over the last two week's worth of data. This allows organizations to continuously monitor specific threats that alone may not reach the severity threshold for alerting, or that cannot be tuned enough to be deployable as an alert. In this case, detection hits will be collected in the Hunter's Workbench for review by threat hunters. To create a new scheduled hunt, use one of the existing "Hunt Detection" buttons, set the frequency as "Recurring", and specify the interval.
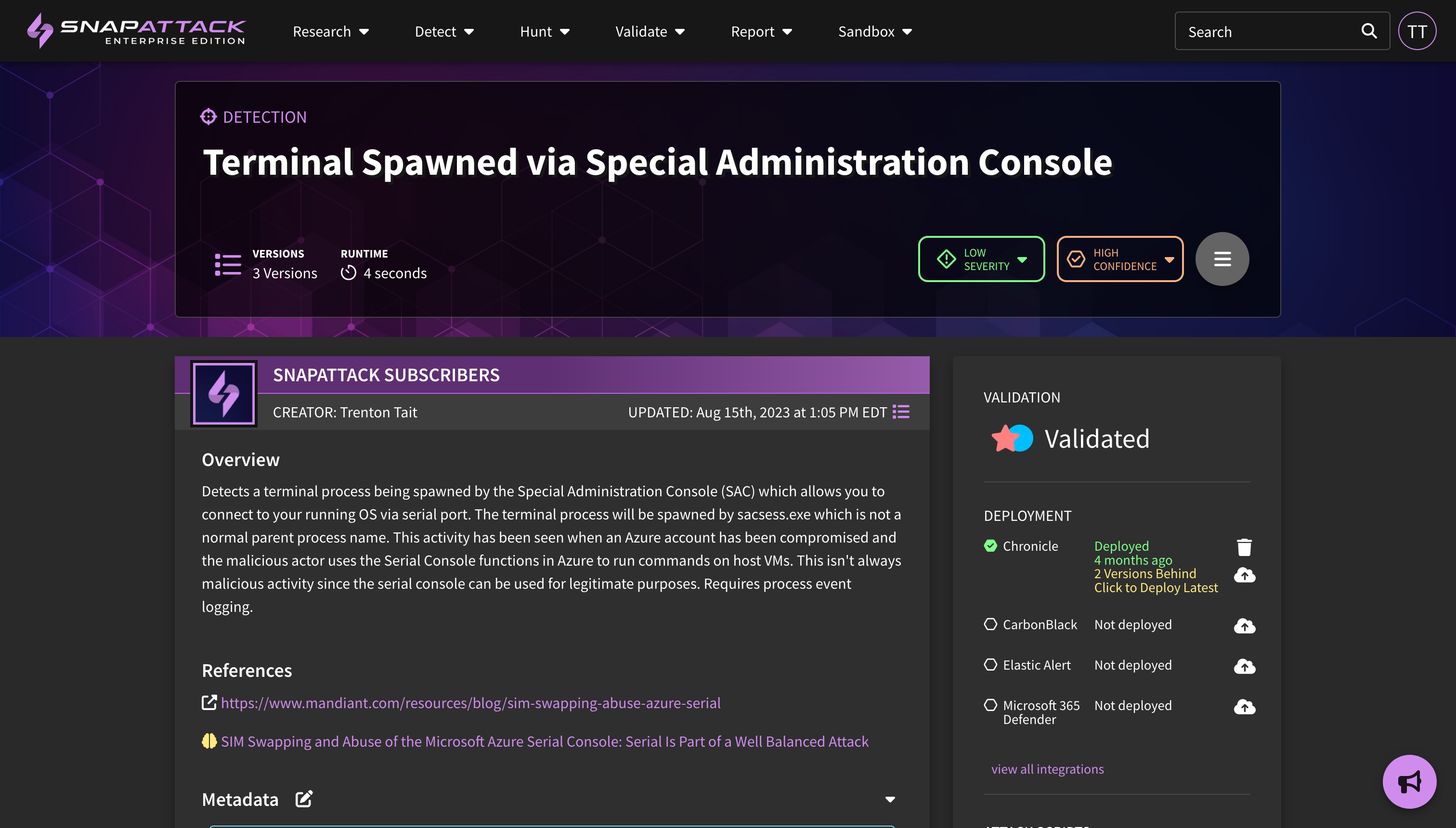
- Improved Deployed Detection Statuses: updated the grid view and detection pages to more accurately reflect a deployed detection's status. Detections can either be not deployed or deployed, and if deployed, it could be a sub-status of queued, deployed successfully, or errored. Detections which are out-of-date are also now reflected here. Users can use the diff viewer to see what changed between detection versions, as well as quickly upgrade to the latest detection.
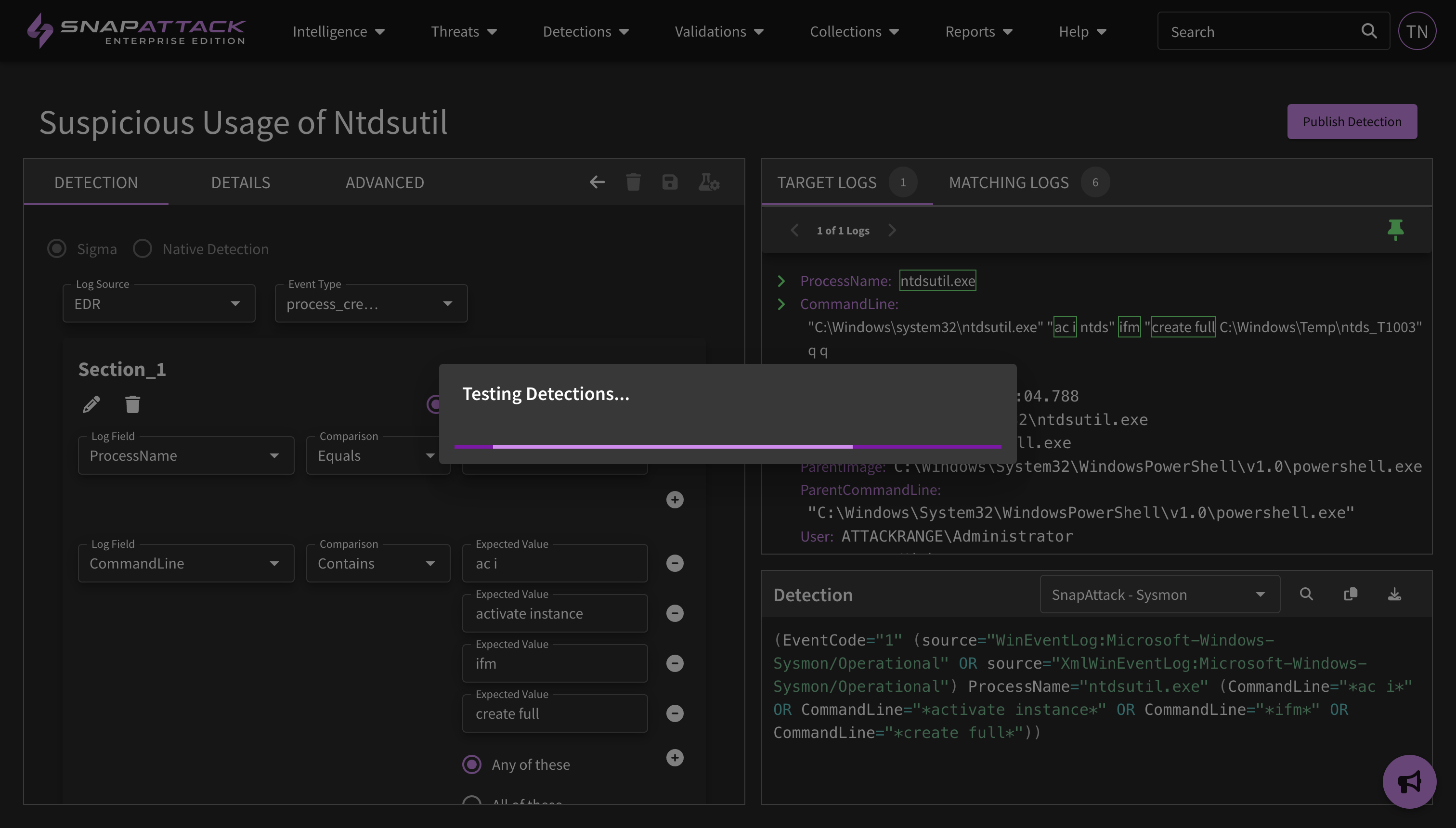
- Updated the display of detections that are currently being tested against the SnapAttack threat library. When a detection is created or a new version is published, we delete the old detection hits and re-run the detection across the threat library. Depending on the detection complexity and other tasks, it can take a minute or two to execute. We now display a message when detection hits are being calculated for a new version, and provide an update as to the job status. This helps alleviate situations where a user creates a new detection and there is some mystery as to why it remains "untested"; now, if the processing message is not being displayed, it means the detection has no hits and a user may want to review the detection logic or syntax for errors.
2024.01.04
- Bi-Directional Detection Sync: Deployed detections that are modified in a customer's integration will now have the changes synced back to SnapAttack. This is useful for customers who edit or tune a detection in their SIEM/EDR. These changes will now be synced back to SnapAttack and tracked as a new version. Some detection-as-code features, such as translating the modified detection to another language, will be unavailable for detections modified outside of SnapAttack. Reach out to your customer success representative to learn more.
- Improved reliability of long running hunt and confidence tailoring jobs.
- Added the ability to support boolean filters (OR, NOT) when searching contributors or organizations in the application.
- General bugfixes and stability improvements to enhance the user's experience.
2024.01.01
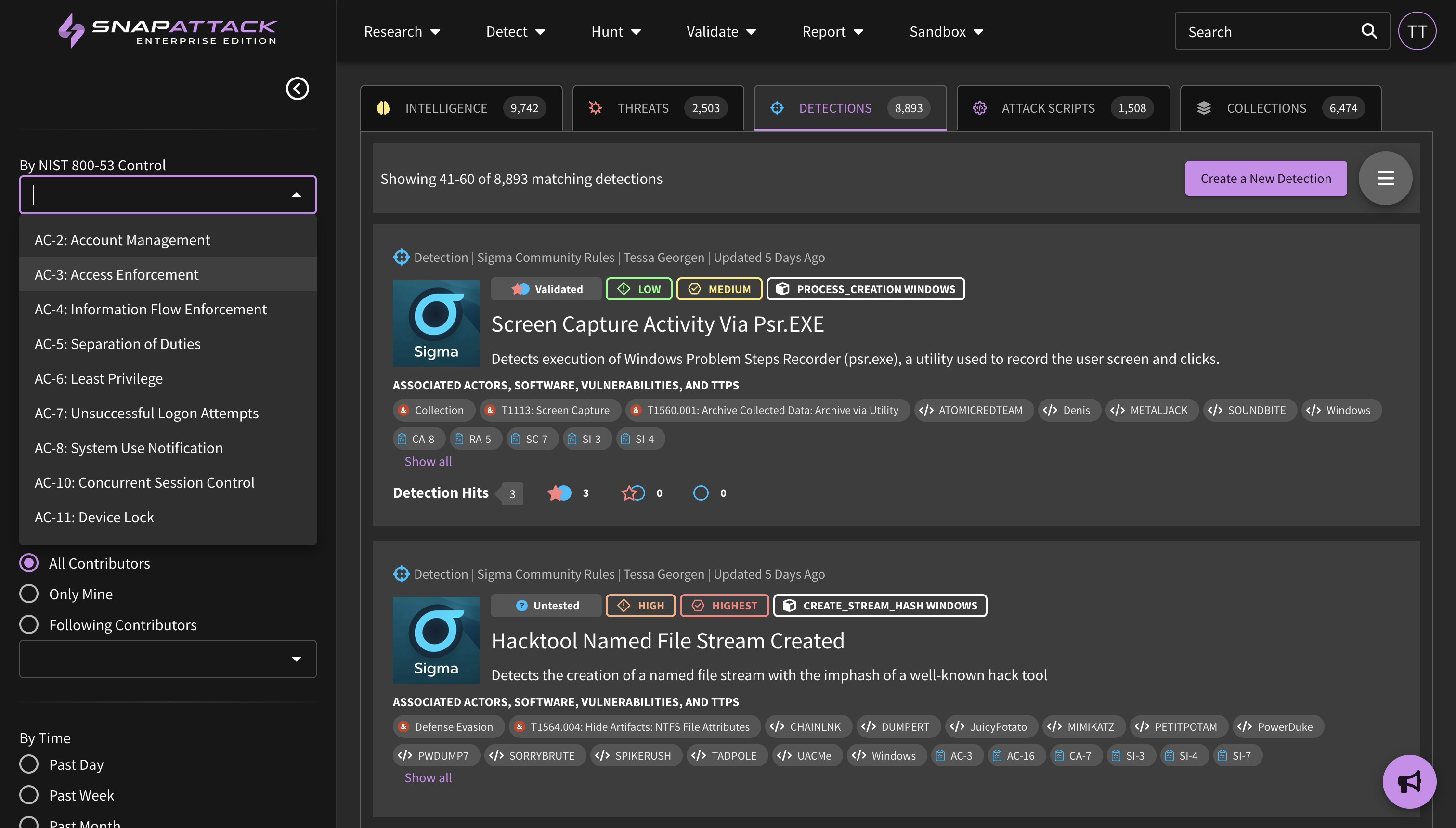
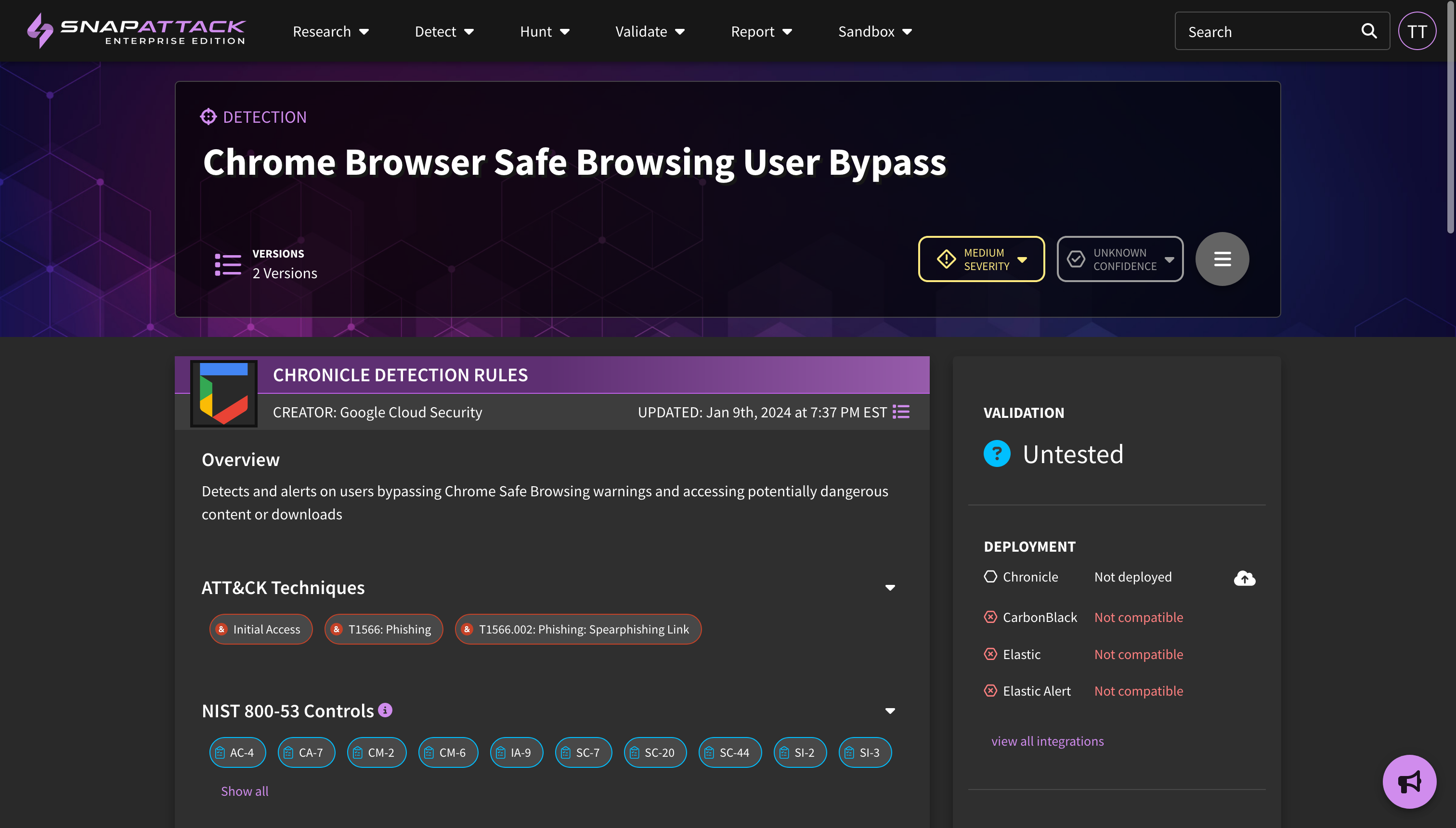
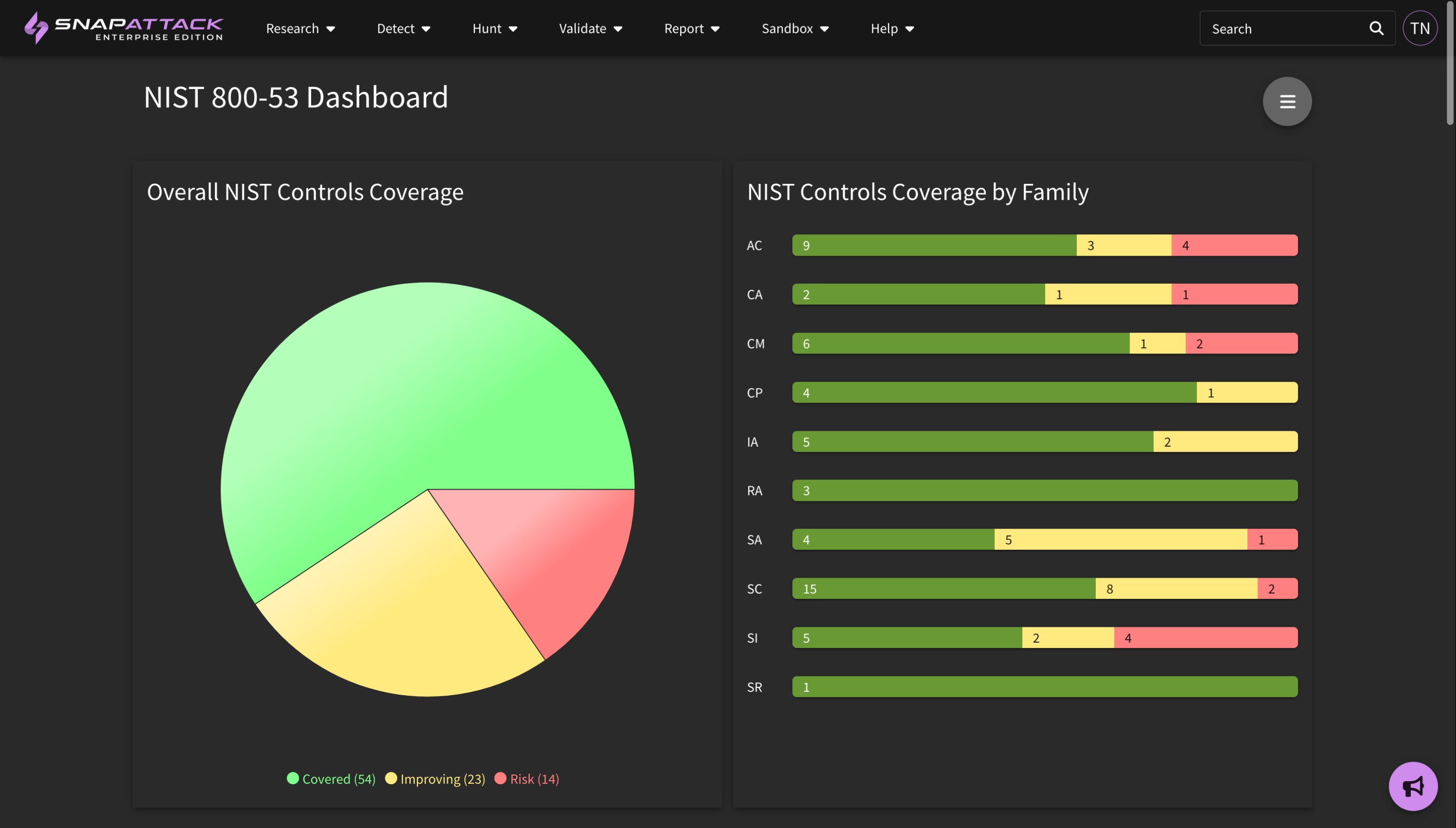
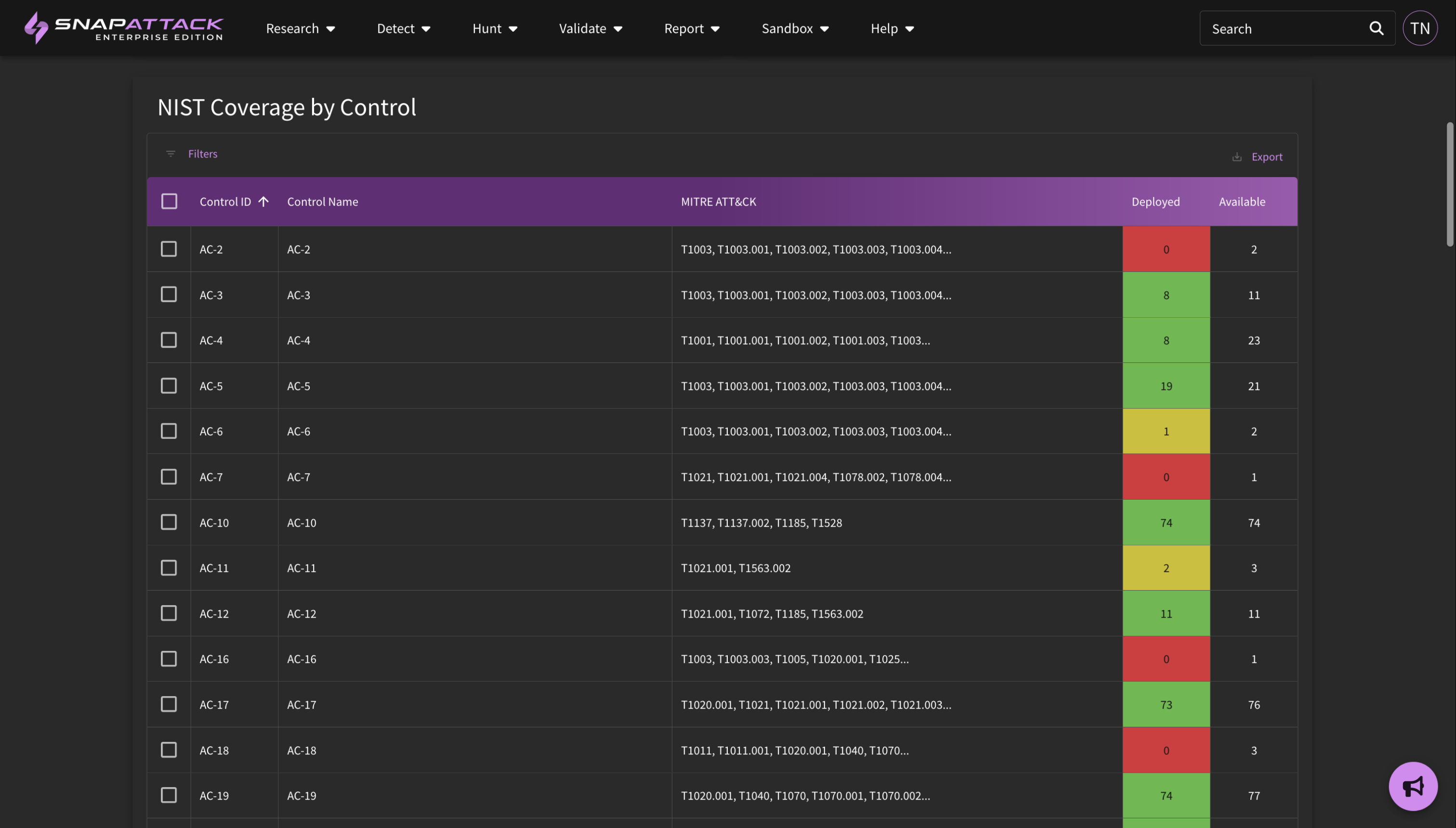
- NIST 800-53 Mappings: added the NIST 800-53 control mappings to detections using the ATT&CK Control Framework Mappings project. Applicable NIST controls will automatically be populated based on the MITRE ATT&CK tags for a detection. NIST controls are searchable and filterable from the detection feed, and are visible on the detection page itself. The NIST 800-53 dashboard is now drillable so you can identify the detections that are deployed or available for each control.
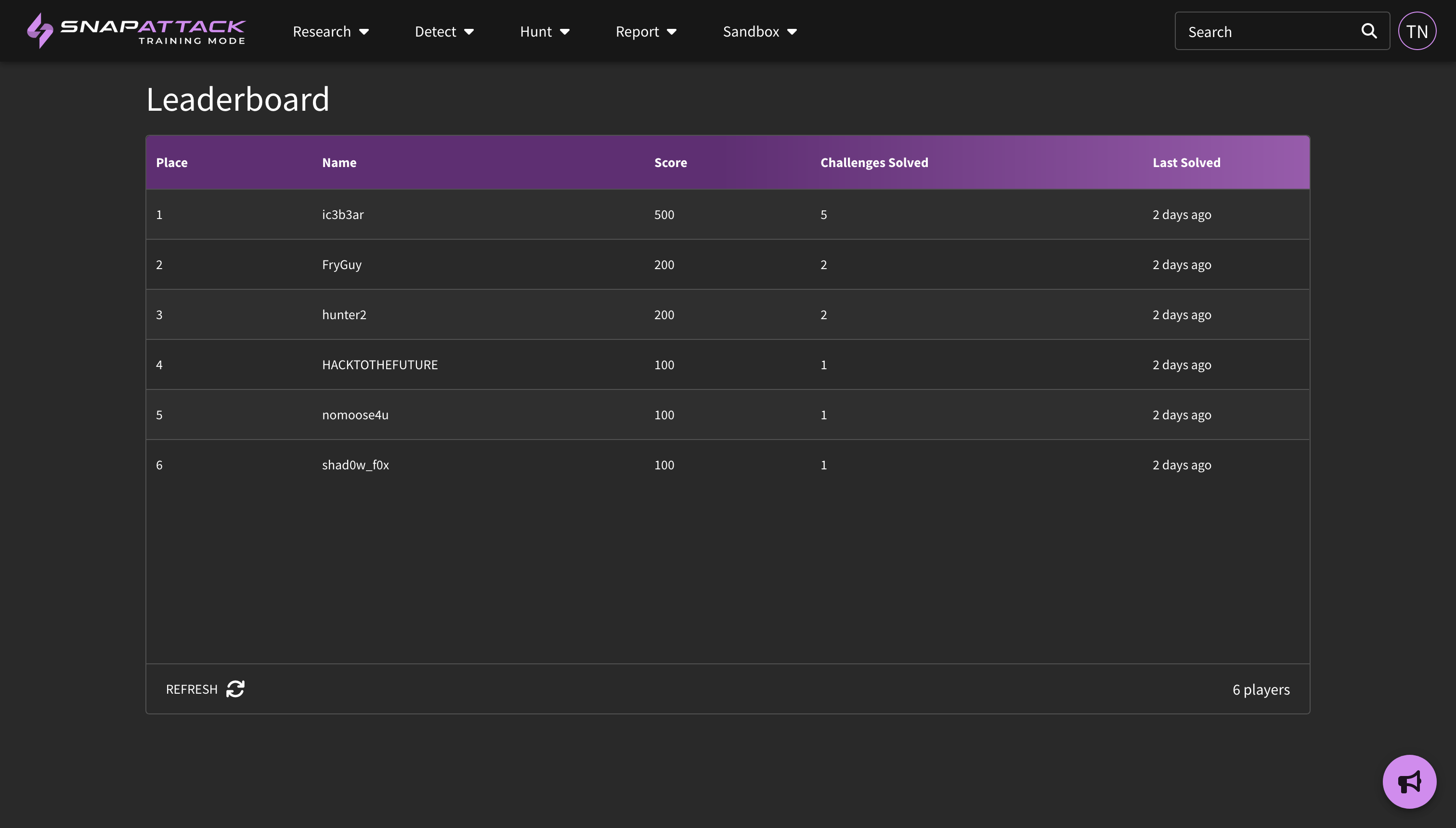
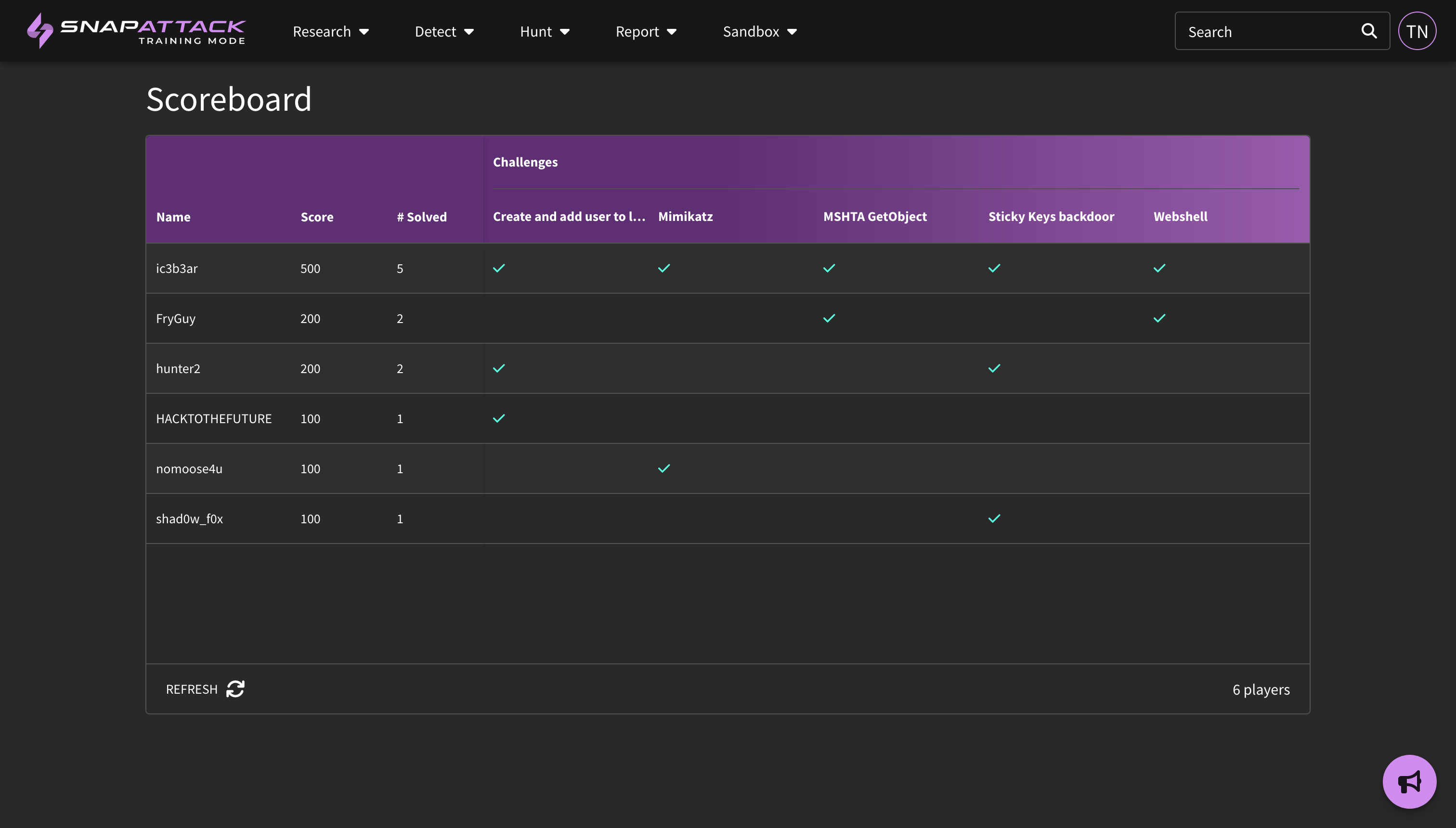
- Training Mode: training mode now has a leaderboard and scoreboard, so users and moderators can track student progress across challenges. Training mode content is easier to modify as well. Training administrators can create a collection of content they would like to use for a training session and share that content with the training organization. Only content explicitly shared with that training organization will be visible to students.
- Updated the "Add to Collection" modal to show which collections a content object is a part of, which will be shown at the top of the list.
- Logscale Integration: Created an integration for customers with CrowdStrike Logscale (formerly Humio). The integration supports all of the common use cases including deployment, hunting, and confidence tailoring.
- Improved the ability to perform longer duration hunt jobs in Google Chronicle by batching multiple smaller jobs to cover the full time window.
- Revised the algorithm for running detections against a new threat in the threat library to increase the speed of hits coming in. The algorithm now prioritizes a customer's detections first, then ones that have been previously validated and are likely to hit.
- Multiple small changes to threat intelligence objects to improve user experience. Removed the links to threats, detections, attack scripts, and other intelligence objects, which is the purpose collections. Added the ability modify or remove attachments and IOCs from an existing intelligence object.
2023.12.02
- MITRE ATT&CK v14.1: SnapAttack has been upgraded to using ATT&CK v14.1. Techniques that have been revoked or deprecated are automatically updated as part of this process. New techniques have had default severities mapped. To learn more about this update, review the ATT&CK release notes.
- User-Defined Tags: User defined/custom tags have been removed from the system, per the deprecation notice that was posted in the February 2023 release notes. We have migrated to using structured tags (around ATT&CK techniques, threat actors, vulnerabilities, and malware/tools) that are globally visible for all users. For use cases where there is a need for private tags, you can use the Metadata feature to tag content in the platform that will only be visible to your organization.
- CapAttack: Fixed an issue with Ubuntu not having the permissions to write the PCAP file. Fixed a framerate speedup issue which caused the attacker and victim videos to become out of sync. Fixed an issue with FFMPEG crashing when switching VMs or refreshing the page.
- Microsoft Sentinel: Completely re-wrote the Microsoft Sentinel integration, which now uses a direct API instead of the function application. There is a dramatic increase in speed for hunting and confidence tailoring, and improved reliability for long running jobs. Customers should reach out to their customer success representative with information about upgrading to the latest integration version.
- Fixed numerous small bugs with the Sentinel integration during the re-write, such as looking up the MITRE ATT&CK tactic if a detection doesn't have it mapped, and ensuring the correct severities are passed from SnapAttack.
- Created a "resume" endpoint for hunt jobs that are stuck in "pending". The job will pickup where it left off instead of needing to be restarted.
- Microsoft Sentinel "entity maps" can now be edited via the Settings → Integrations page. Other integrations that support advanced configuration options can also be updated this way.
- Our content syncing includes several new repositories, including the Leonidas framework for cloud attack and detection content, and the Azure Sentinel detections and hunt queries.
- General bugfixes and stability improvements to enhance the user's experience.
2023.11.06
- Metadata can now be applied actor, software, vulnerability, and ATT&CK collections. This allows organizations to better track and documentation knowledge around these threats inside the platform. There were also bugfixes around metadata features, including the "no renderer found" message when metadata has not been configured, and some data migration issues when changing values for fields like select and multi-select.
- Revised the search functionality for a more consistent experience across the application. The search in the navigation now functions the same on every page, performing a full-text search and previewing the results. On the feed, threat, or collection pages where the filter options are on the left, there is now a search input at the top to perform a full-text search of the items on the page. This means that you can now search for items inside a collection, or detection hits/attacks inside of a threat.
- Fixed an issue where weights were not being applied to search terms. This results in more accurate search results when using full-text search and there is a match in the name or description field.
- Revised the behavior of the search button on detection translations to make it easier to select an integration to search when multiple options are available.
- Deployed detections that are out of date, or have a new version available, can now be filtered from the feed, and is more easily seen on the detection pages. Users can click the deploy button on the detection page to upgrade the detection to the latest version if it is compatible. The ability to better track, manage, and resolve outdated detection versions will come in a future release.
- Updated Google Chronicle Yara-L translations to pretty print the detection logic, making it easier to read instead of the logic being on a single line.
- Fixed an issue that prevented scheduled confidence tailoring results from automatically applying. Users should go to the Settings → Integrations page and re-configure their confidence thresholds for the fix to take effect.
2023.11.01 Major Release
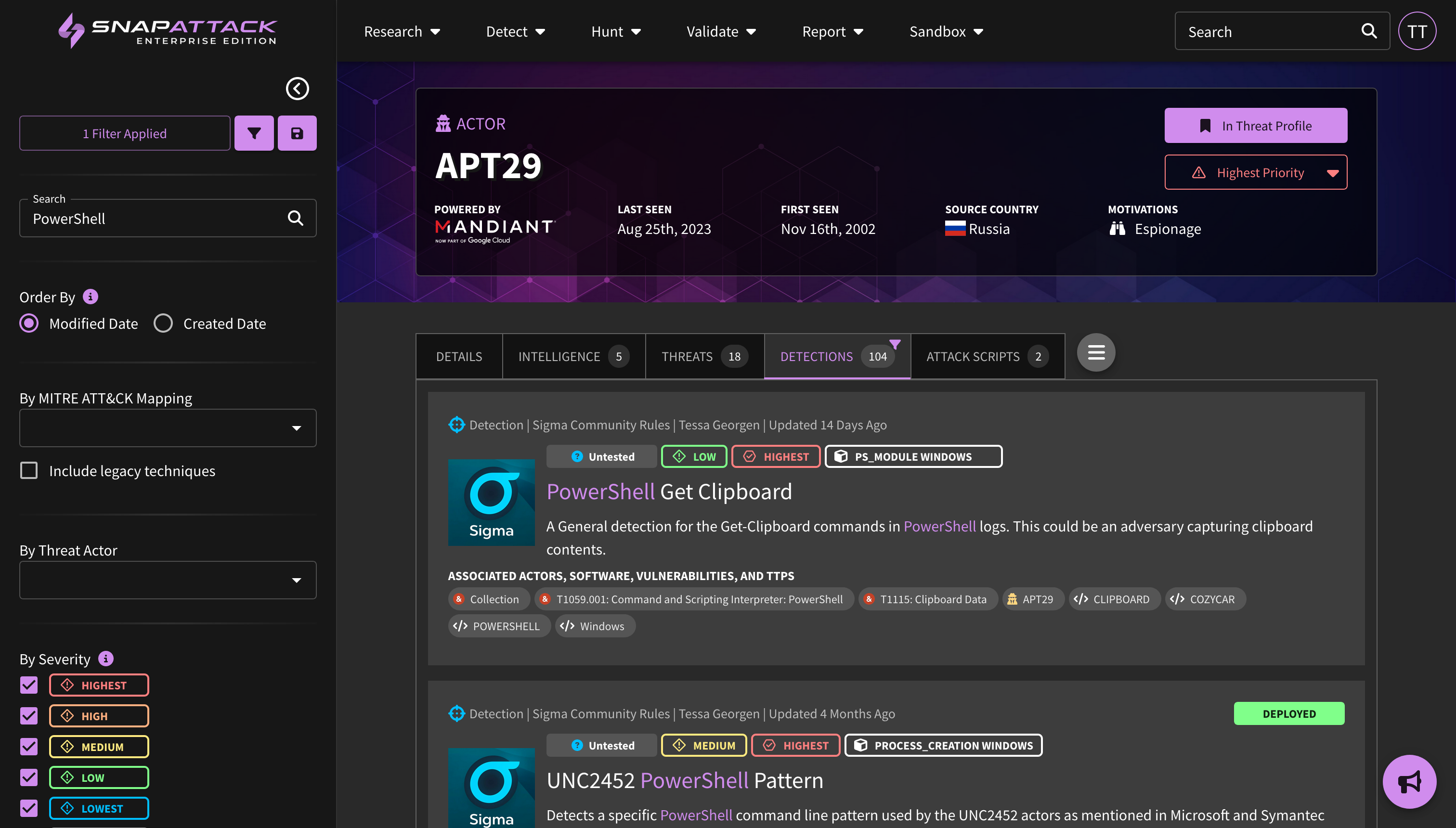
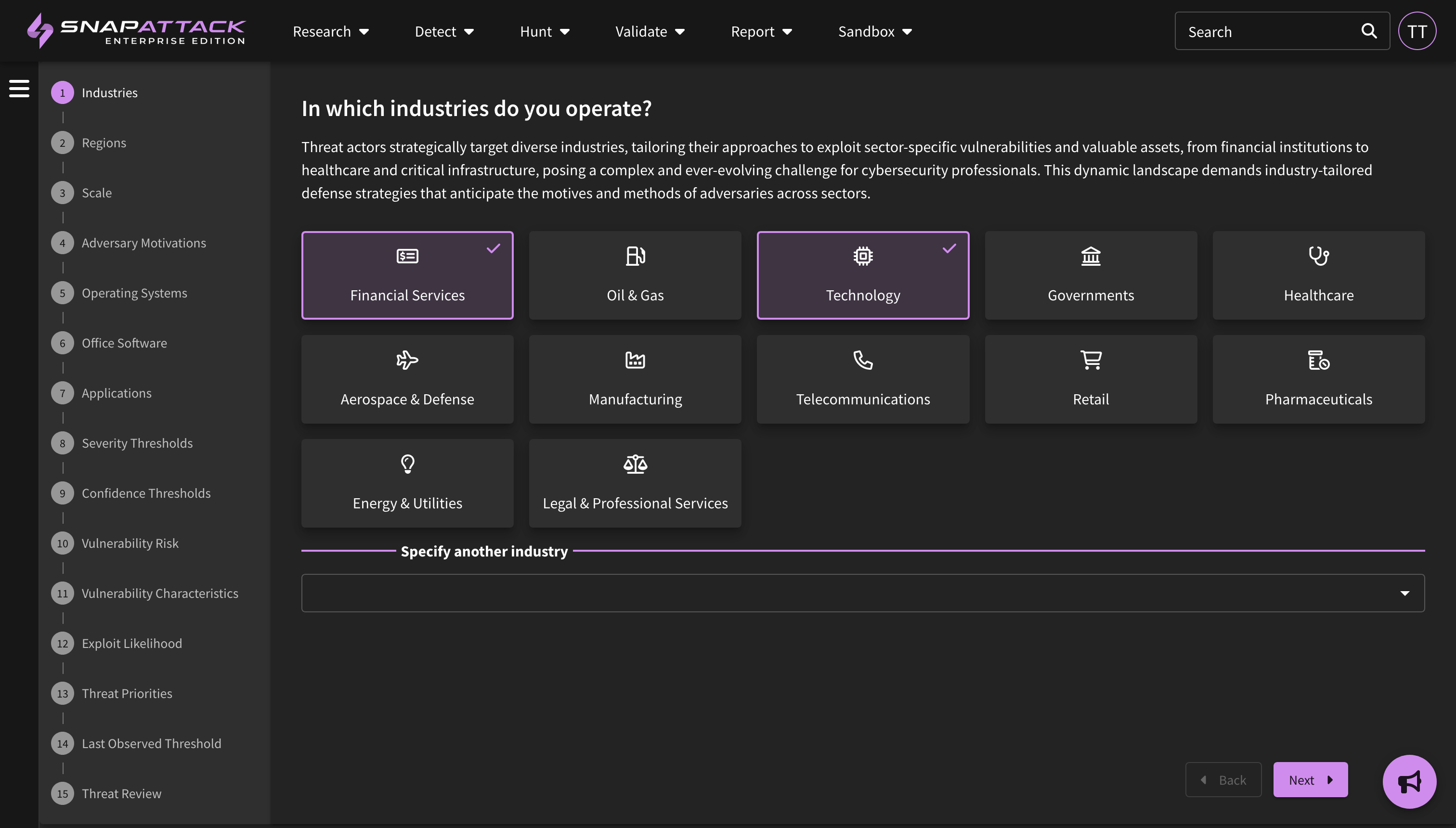
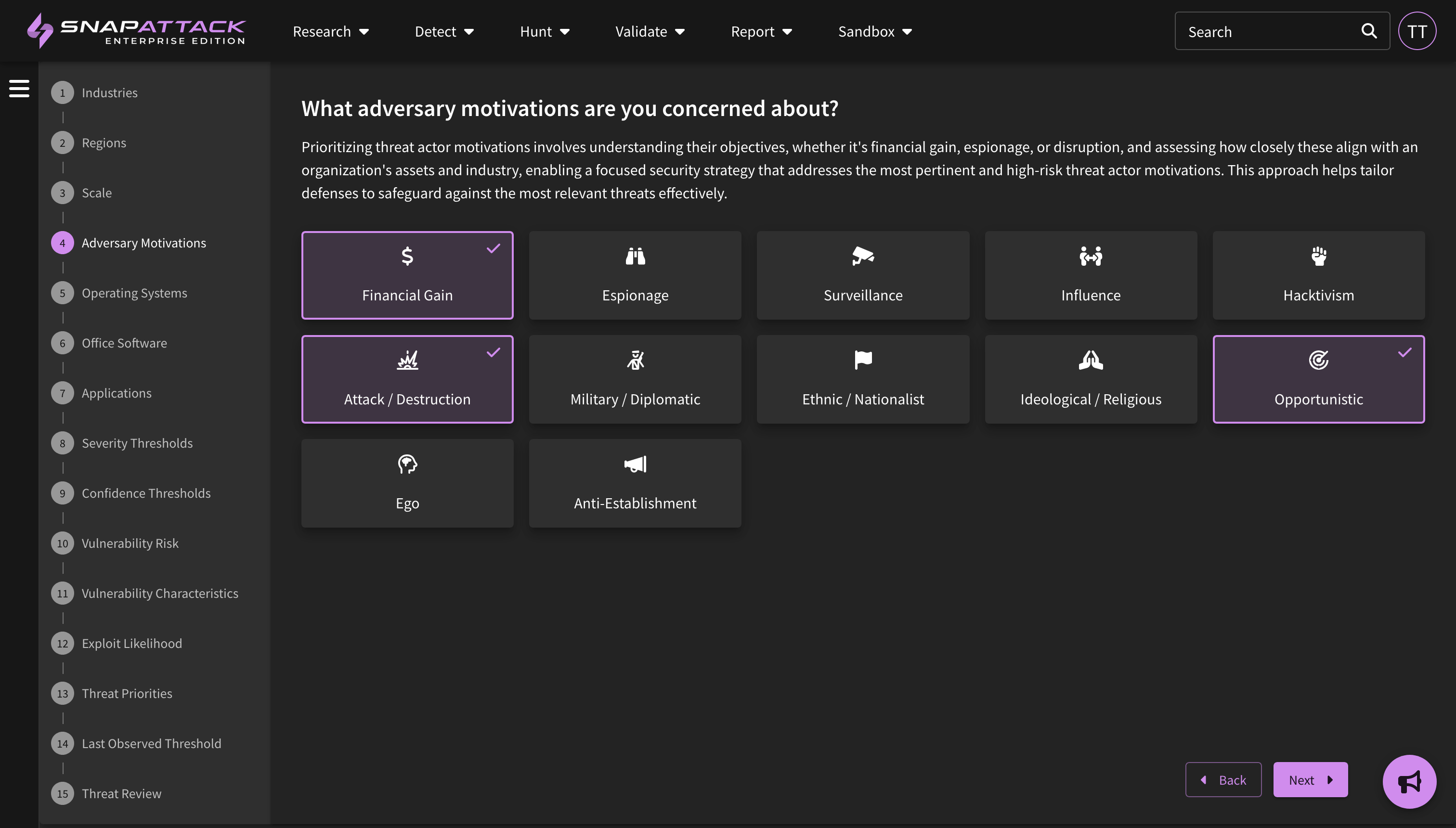
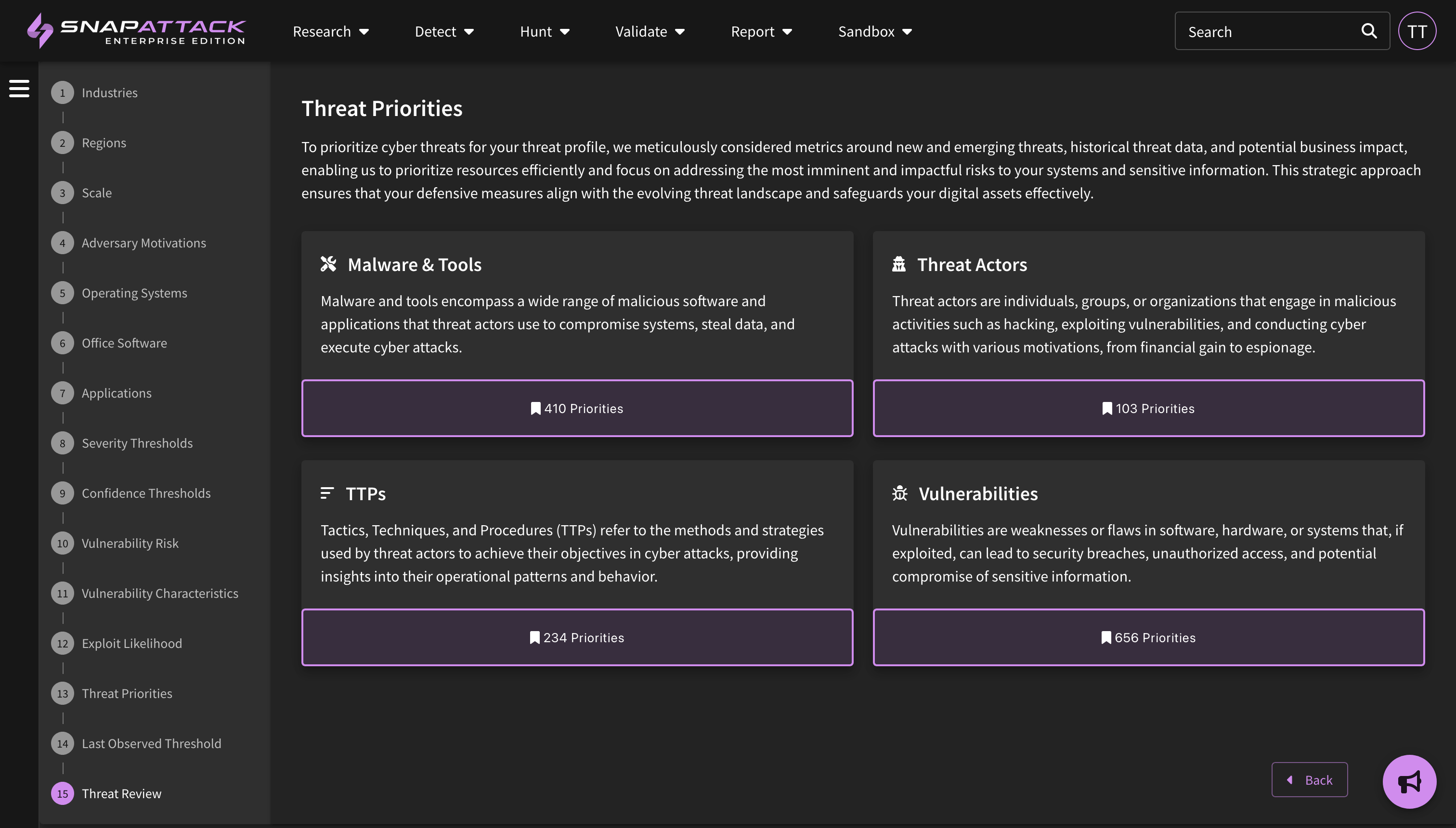
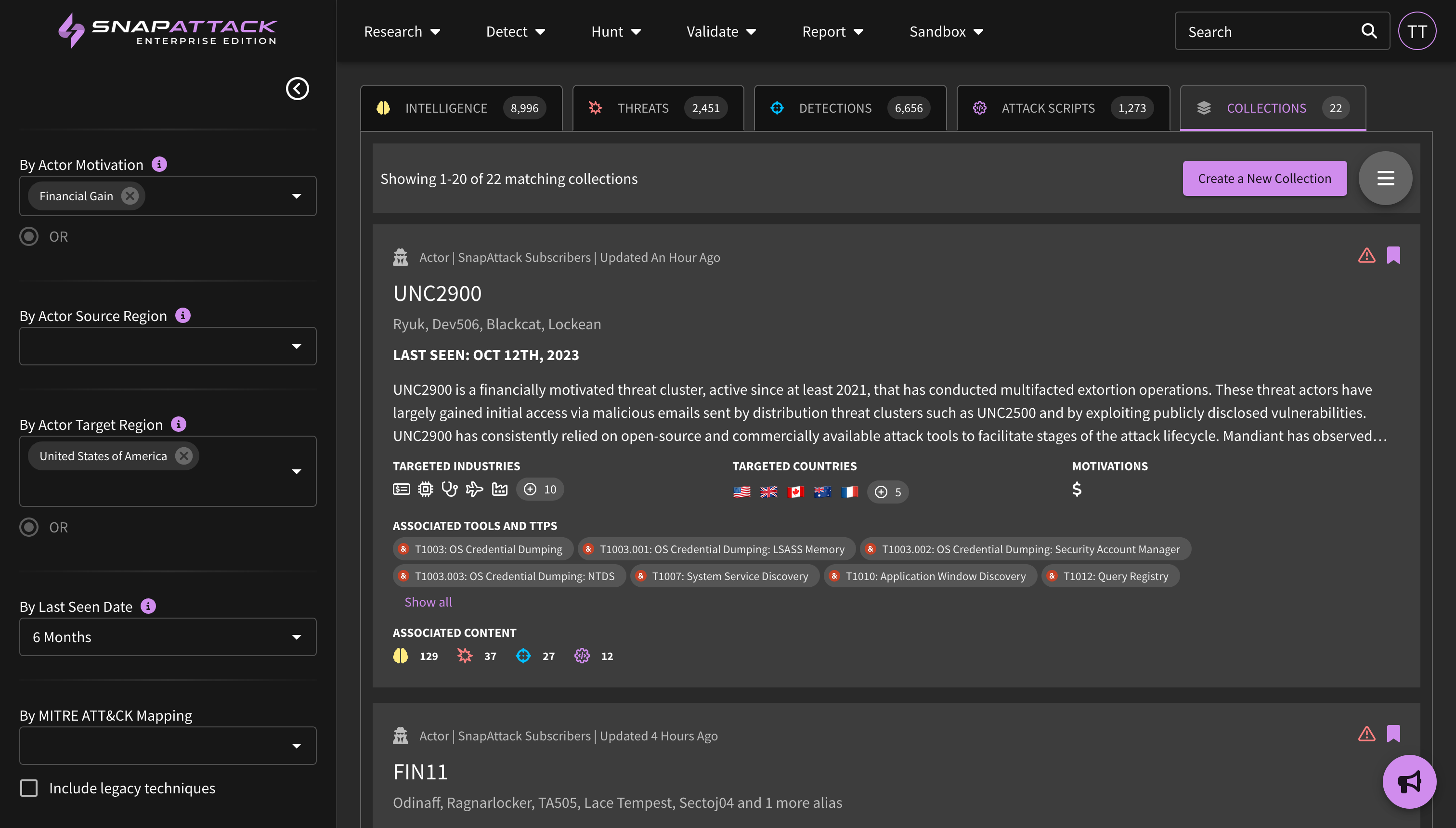
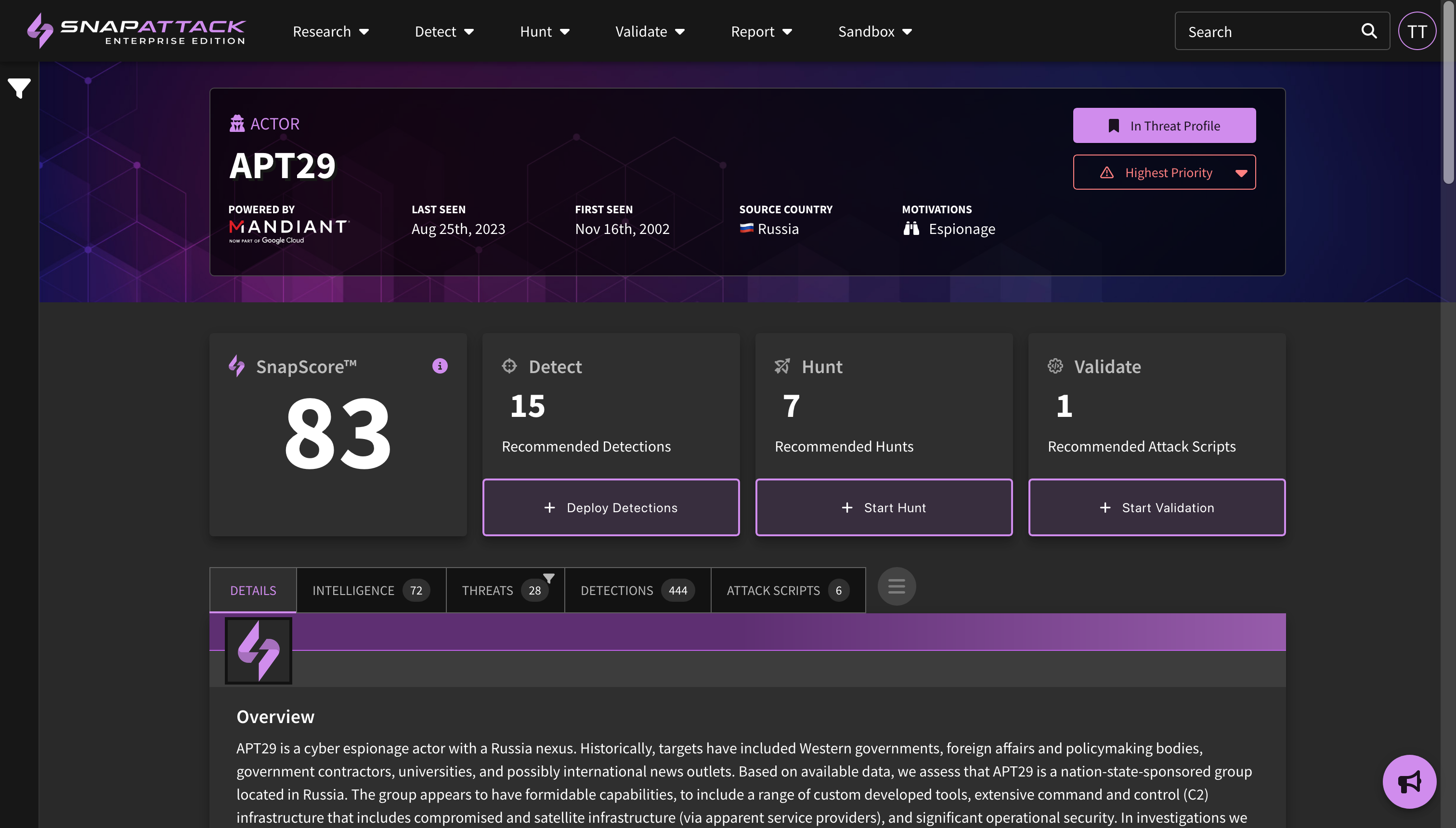
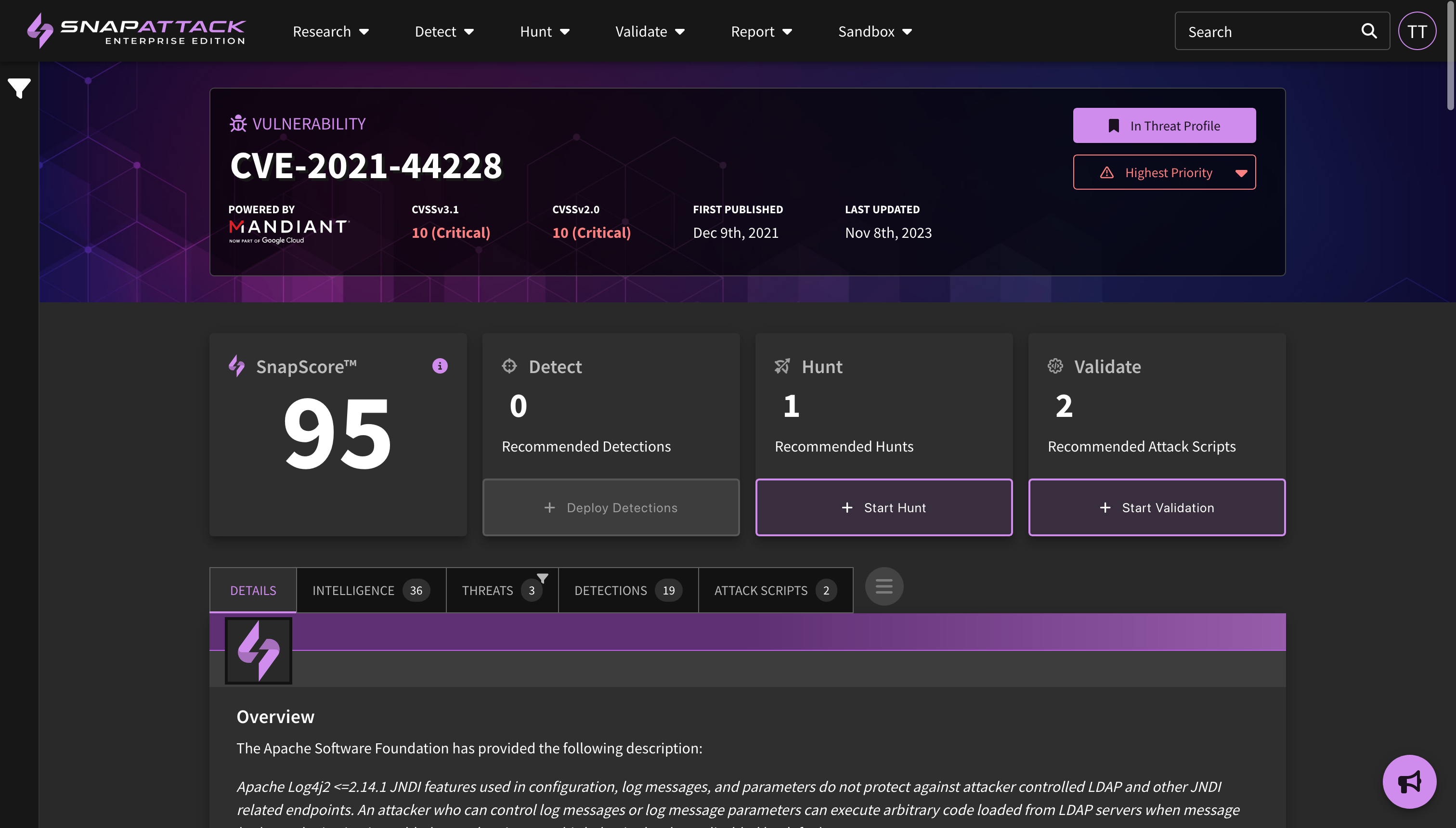
- Threat Profiles: Create threat profiles based on your organization's firmographics and the world-class threat intelligence from our partner Mandiant (now part of Google Cloud). SnapAttack combines information about your organization—such as the industry, company size, operating systems, cloud platforms, and applications used—with intelligence on threat actor motivations, the malware and techniques they commonly use, vulnerability characteristics and exploit likelihood—to create a threat profile custom tailored to your organization with the threats individually prioritized. This helps cut through the noise, as most "newsworthy" or trending intelligence isn't actionable or often relevant to most organizations. Learn more about threat profiles.
- Collection Recommendations and SnapScore: Our recommendation engine can now provide recommended detections, hunts, and attack scripts for threat actor, software, ATT&CK technique, and vulnerability collections. Taking actions against these recommendations will improve your organization's SnapScore, which is a measure of how prepared you are against a specific threat.
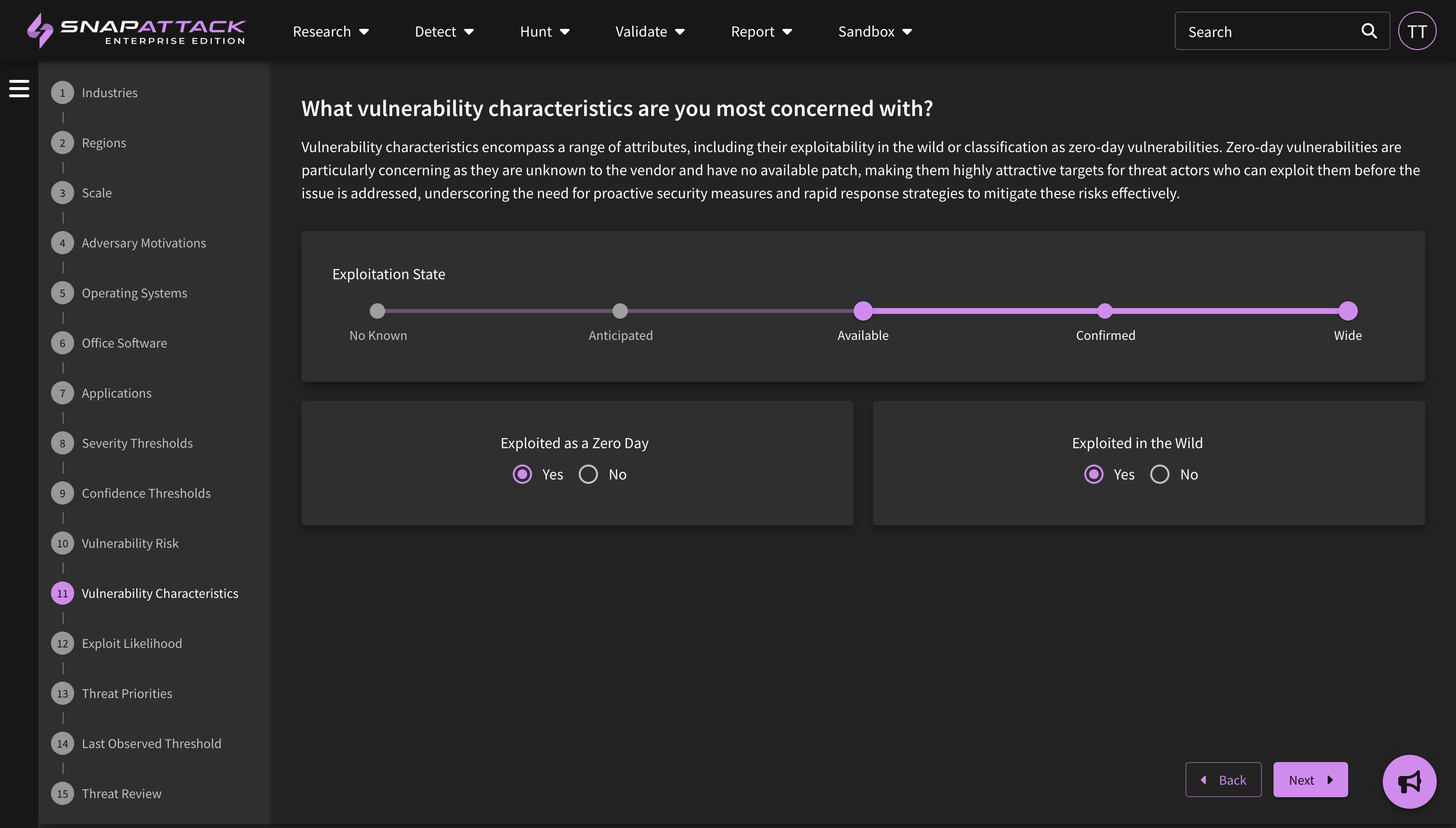
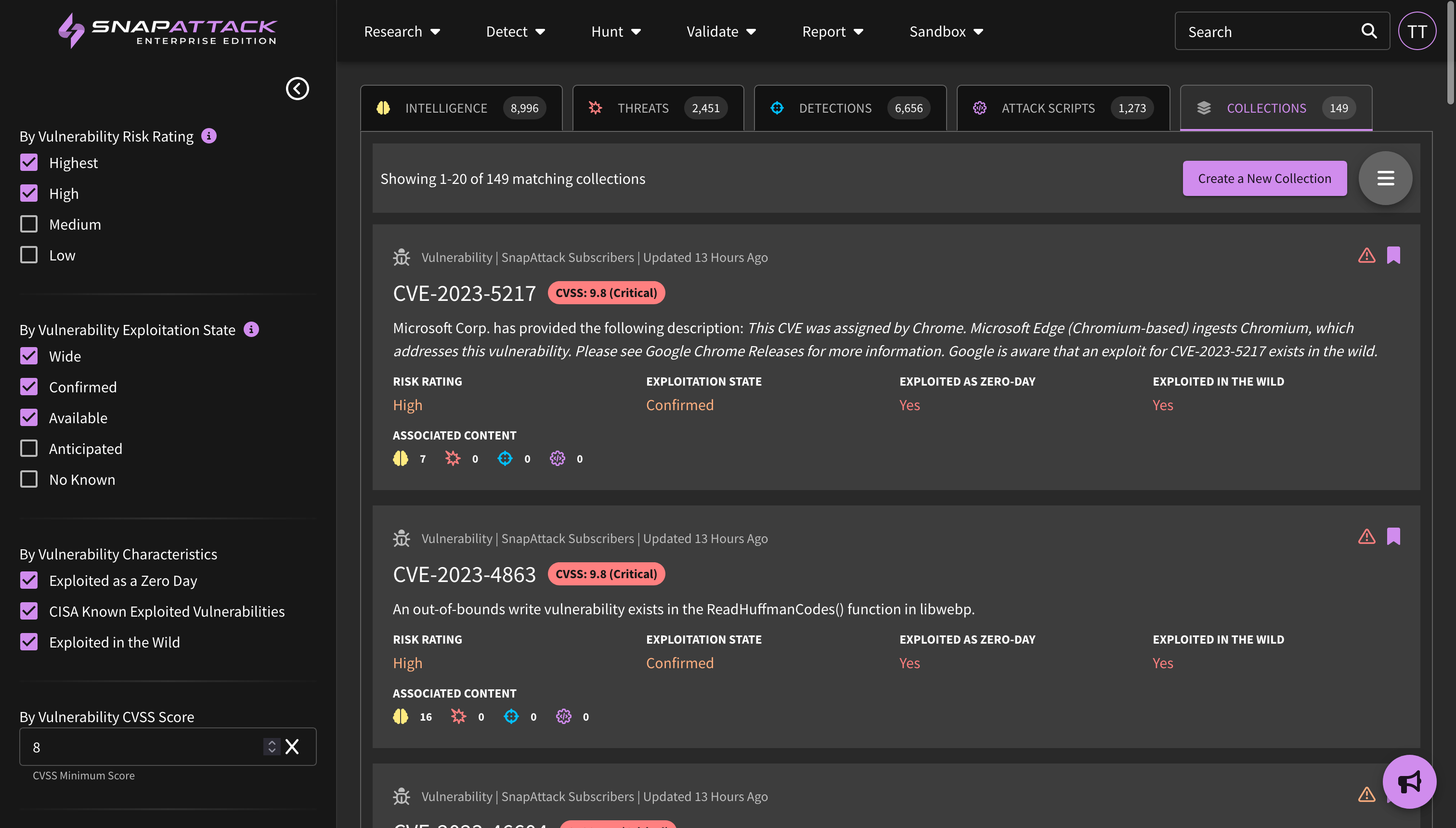
- Collection Feed Cards and Filters: Collection feed cards and grid view have been updated to provide additional information from the Mandiant dataset. This includes actor motivations and source/target regions, target industries, and vulnerability risk and characteristics (e.g., exploited in the wild, as a zero-day). All of these attributes are also filterable.
- Search Highlighting: Matching search terms are now highlighted in the results for the name, aliases, and description fields. This will often make it more clear why a search result was returned when using full-text search.
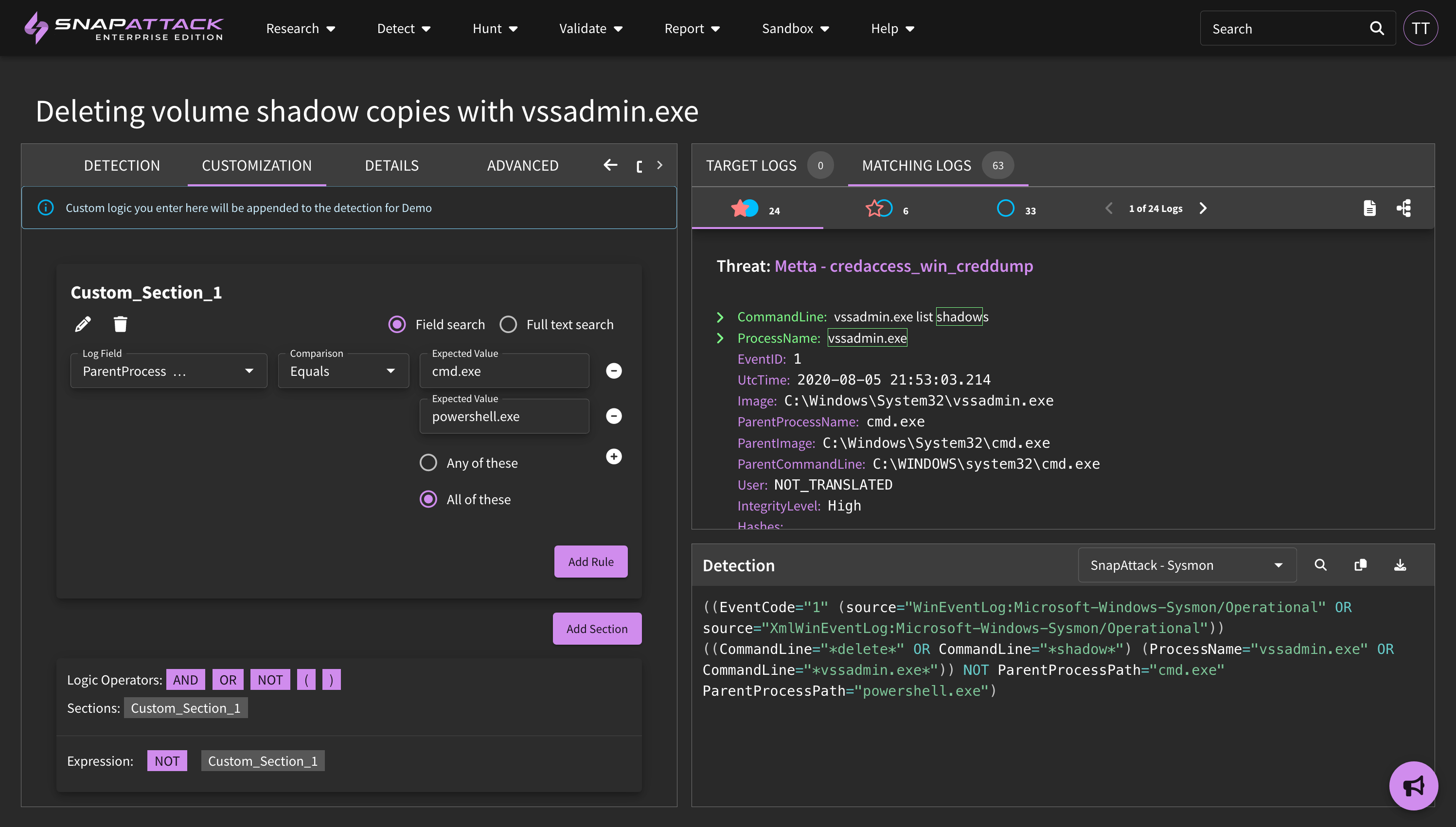
- The detection builder has been updated to allow false positive reduction or tuning logic for native detections. Tuning logic is always private to the organization and will be applied when a detection is deployed. If a detection logic has changed, including tuning logic, then a detection should be redeployed.
- Organizations can now configure the default language for all users in the organization. This sets the language anywhere a detection translation is seen across the application. Users may override this setting by specifying it in their user preferences.
- The feed grid view has been updated with additional columns for organizations, created and last updated users to better allow sorting and filtering.
- The latest attack simulation agent release is now generally available, and links have been updated in the application for new initial installer. Some of the features include the ability to configure the agent to start with the computer, an improved GUI interface for viewing the test execution details, system tray icon, and related attack files or binaries being downloaded "just-in-time".
2023.10.04
- Integrations: Improved support for Microsoft Sentinel entity types. Sentinel now also supports syncing existing customer detections into SnapAttack for improved management, tracking, and reporting. Improved API integrations for Elastic and Carbon Black Cloud for managing detection deployments and threat hunts.
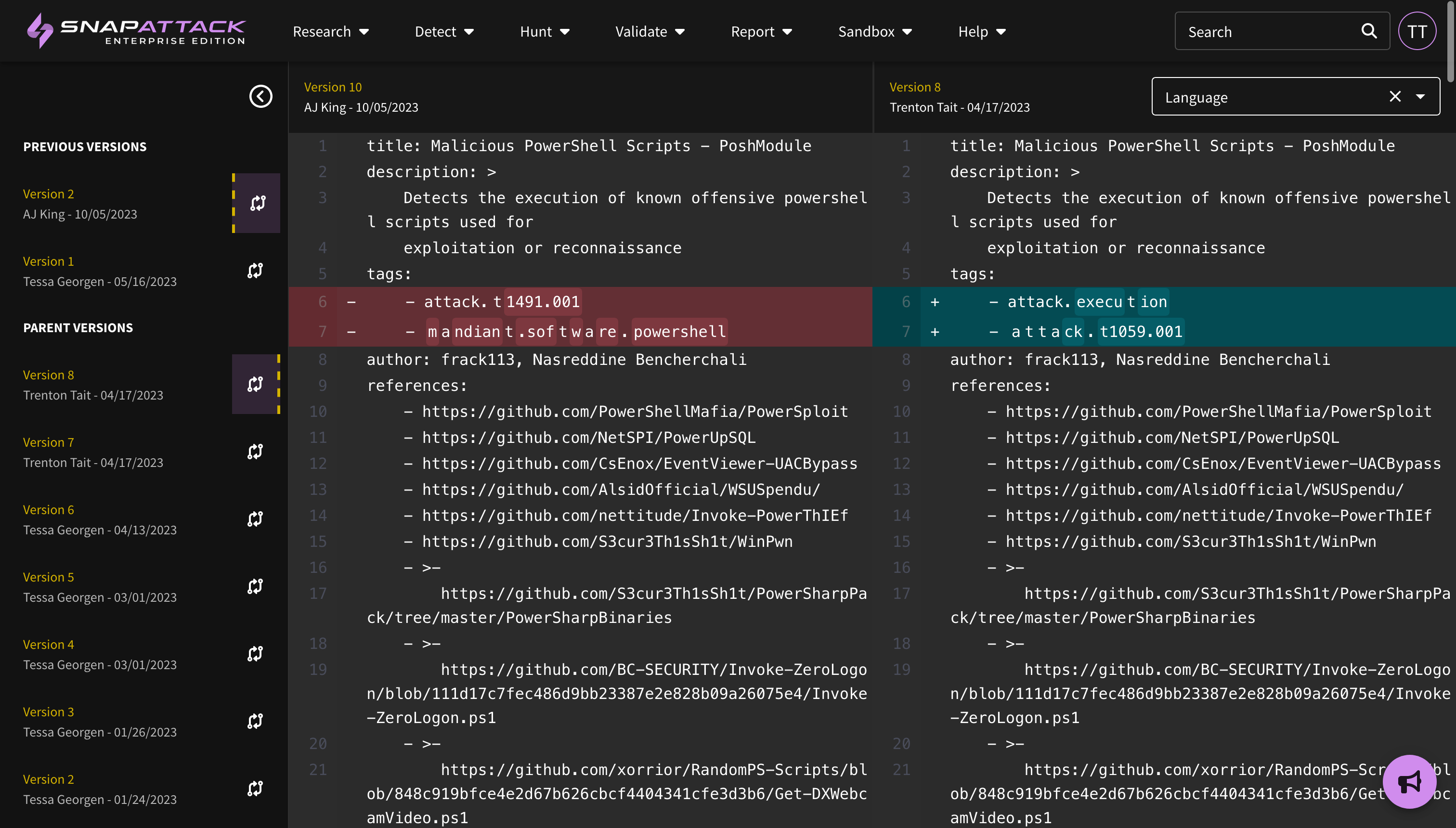
- Detection Version, Parents, Runtimes, and Visual Diffing: Detection version history and lineage has been more clearly exposed in the application, with the version number being displayed in the hero banner. If a detection was cloned from another detection in the library, that linkage is now displayed. This helps users determine if a parent detection's logic has been updated, and if they want to bring that over to their forked version. Users can use the built-in diff viewer to show changes in the detection logic across versions. Detection runtimes are also calculated and tracked during confidence tailoring, which can give users an estimate as to the performance of the detection.
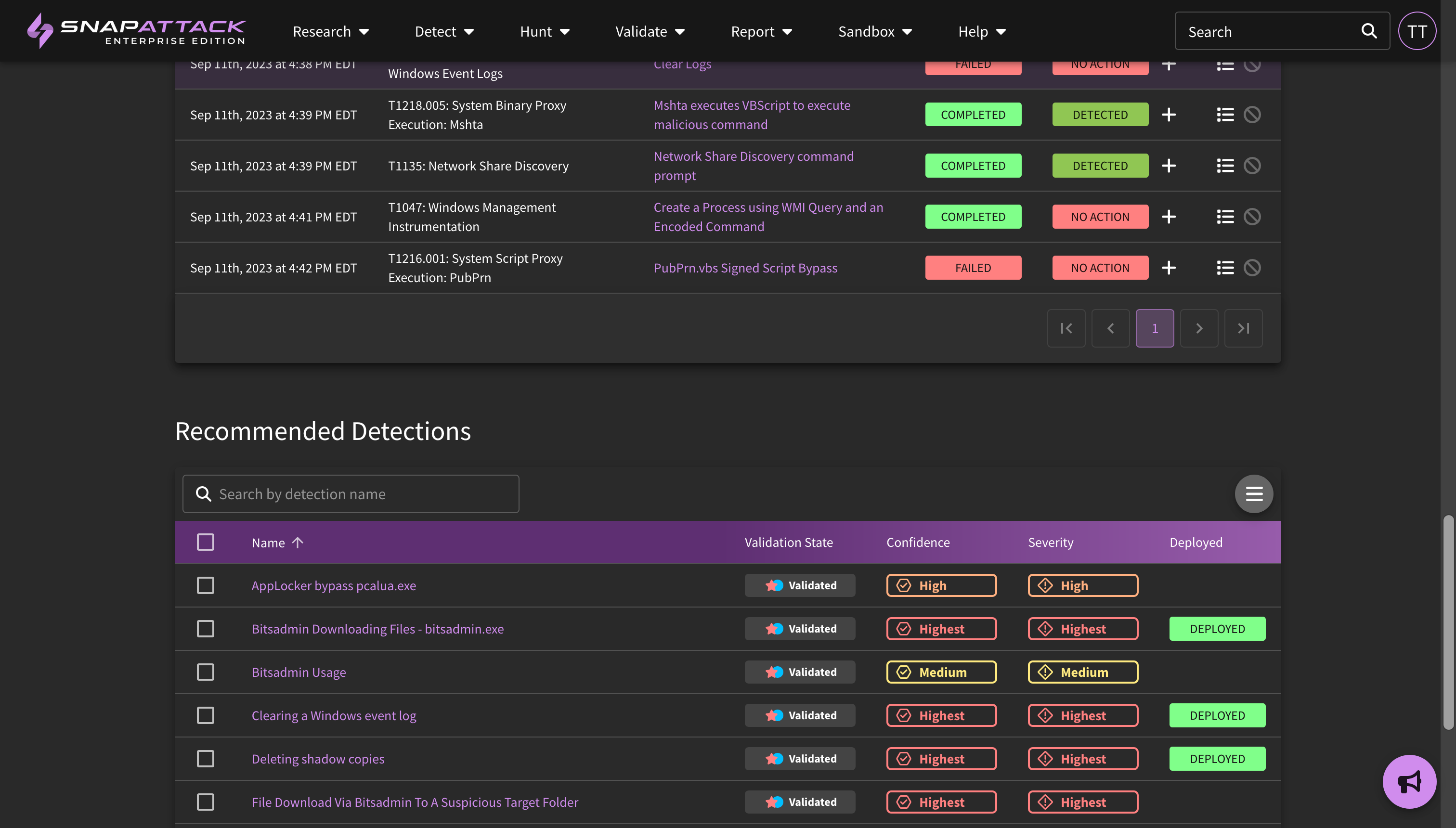
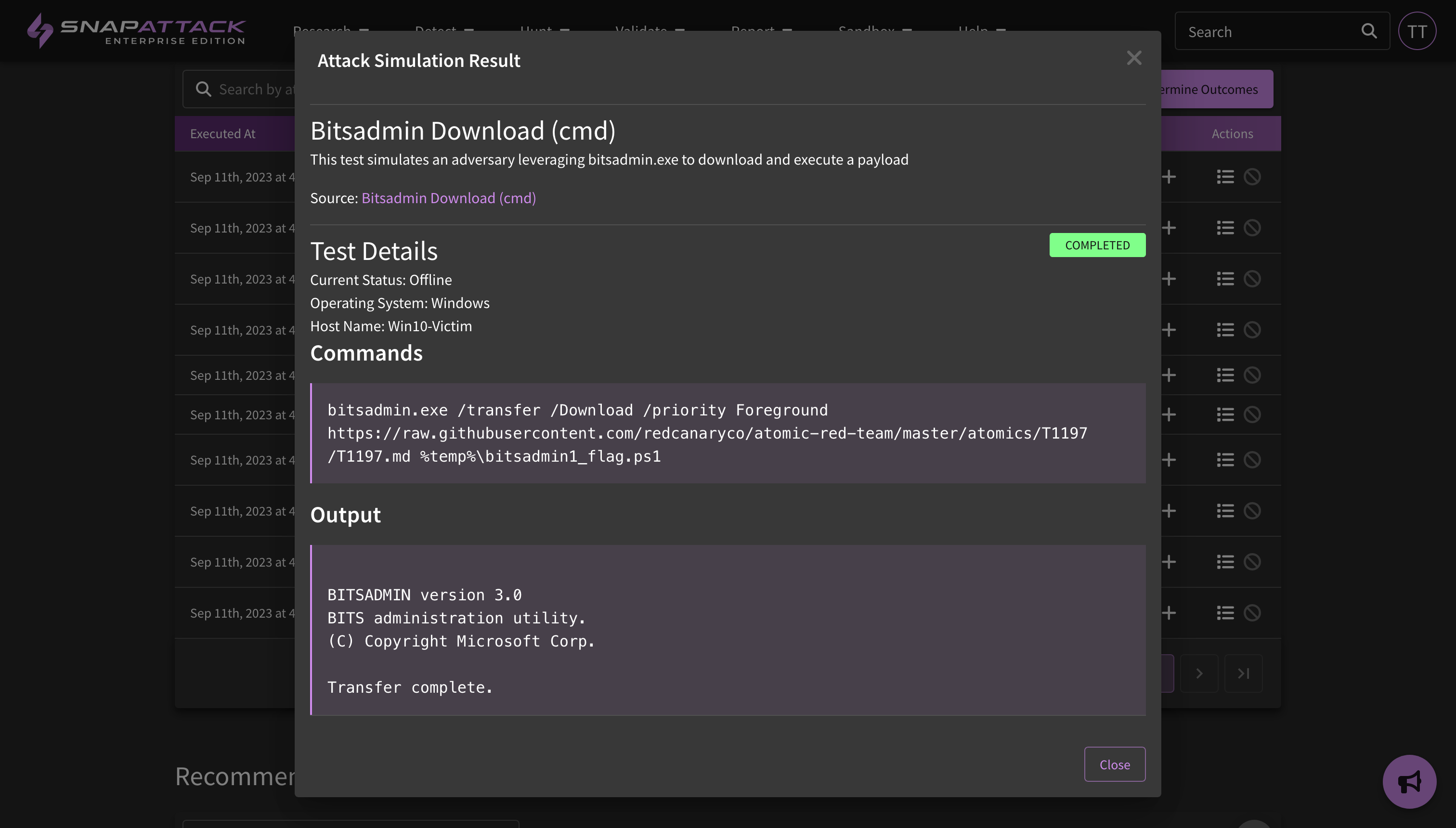
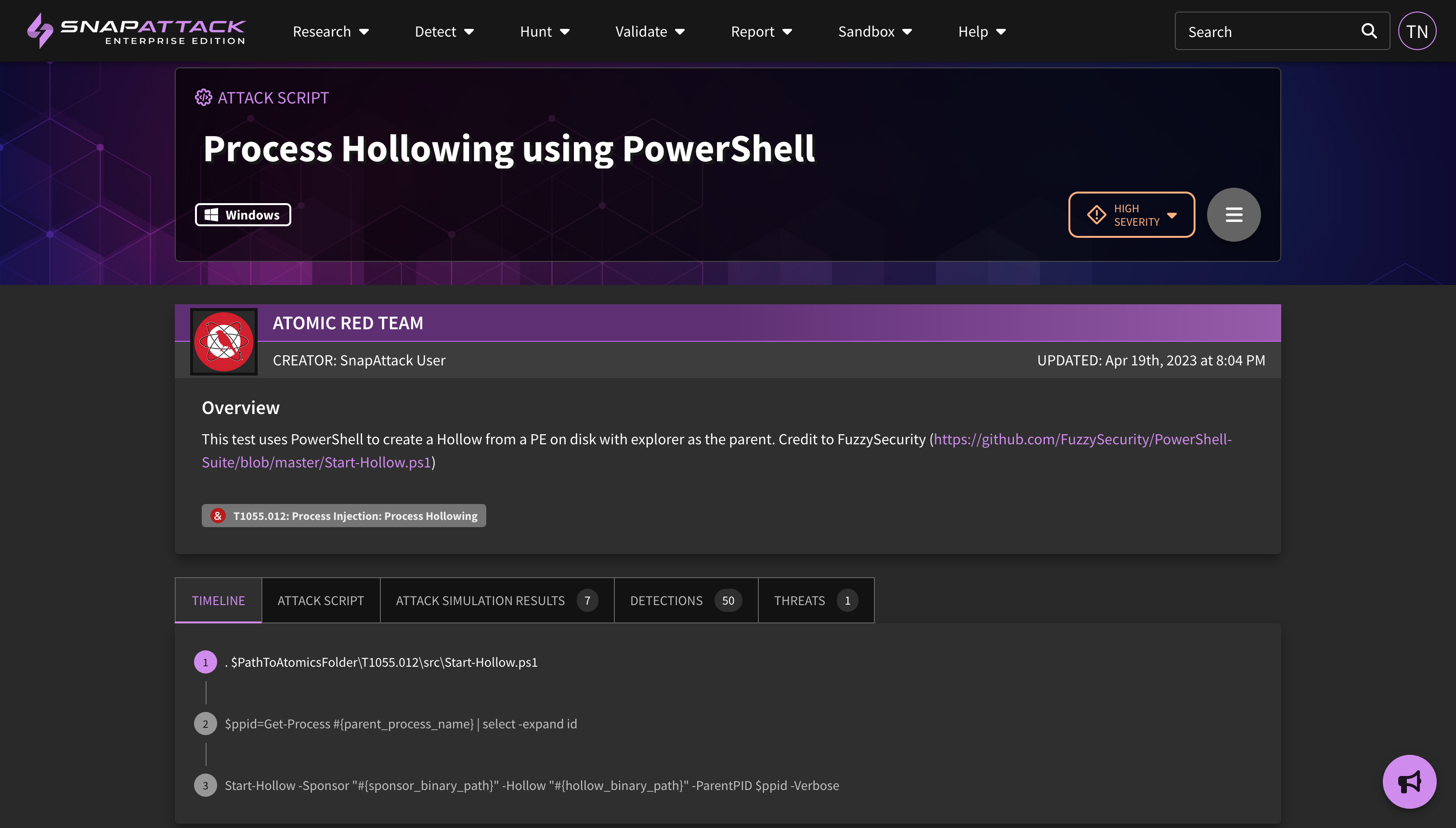
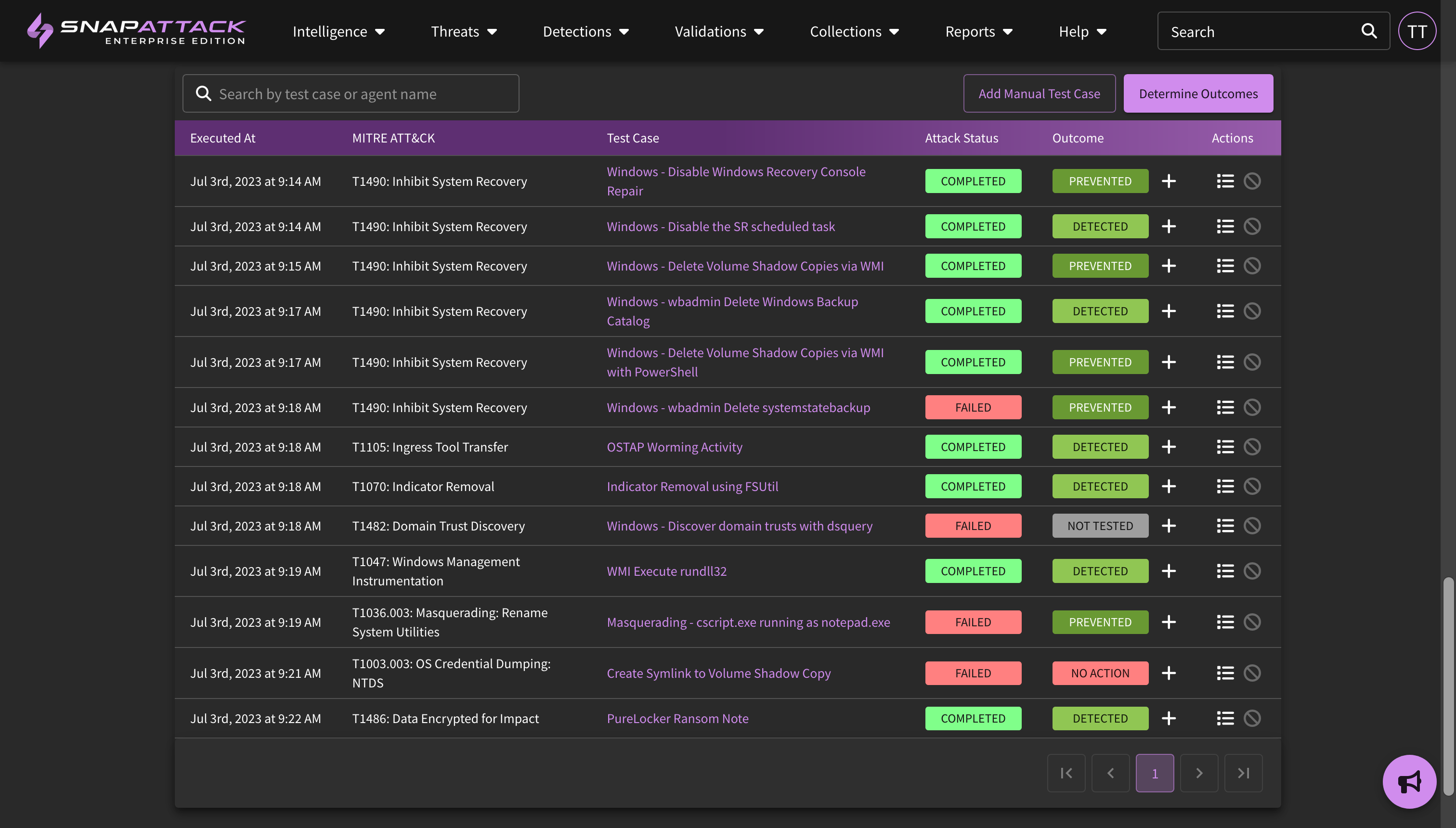
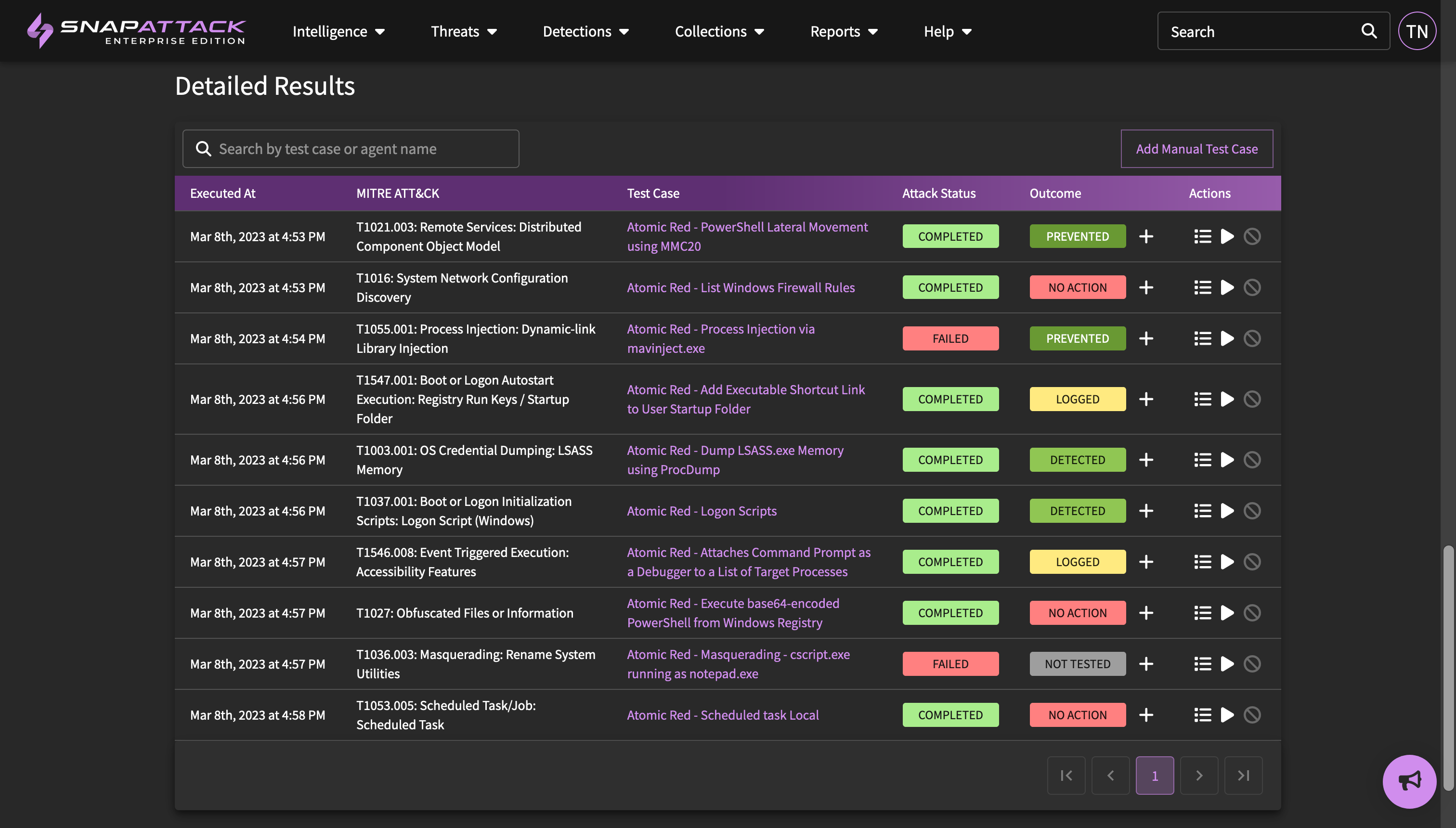
- Validation - Recommended Detections and Attack Statuses: Attack simulation results will now show the recommended detections for the attack test cases. These can be hunted to evaluate sensor coverage and telemetry, and quickly deployed to close gaps. These detections are used by by the "determine outcomes" feature released earlier this year. Attack status tracking has been revised to better track when a test case fails due to missing pre-requisite or not passing success criteria.
- Multiple improvements to the attack simulation agent, including an EXE/MSI installer, new Linux agent, support for downloading test dependencies "just-in-time", and the ability run the agent at startup or as a service.
- Metadata fields can now be edited at once rather than just individually.
- Customers now have access to Slack content notifications, which track when new content has been added by community projects as well as the SnapAttack threat research team.
2023.10.01 - 2023.10.03
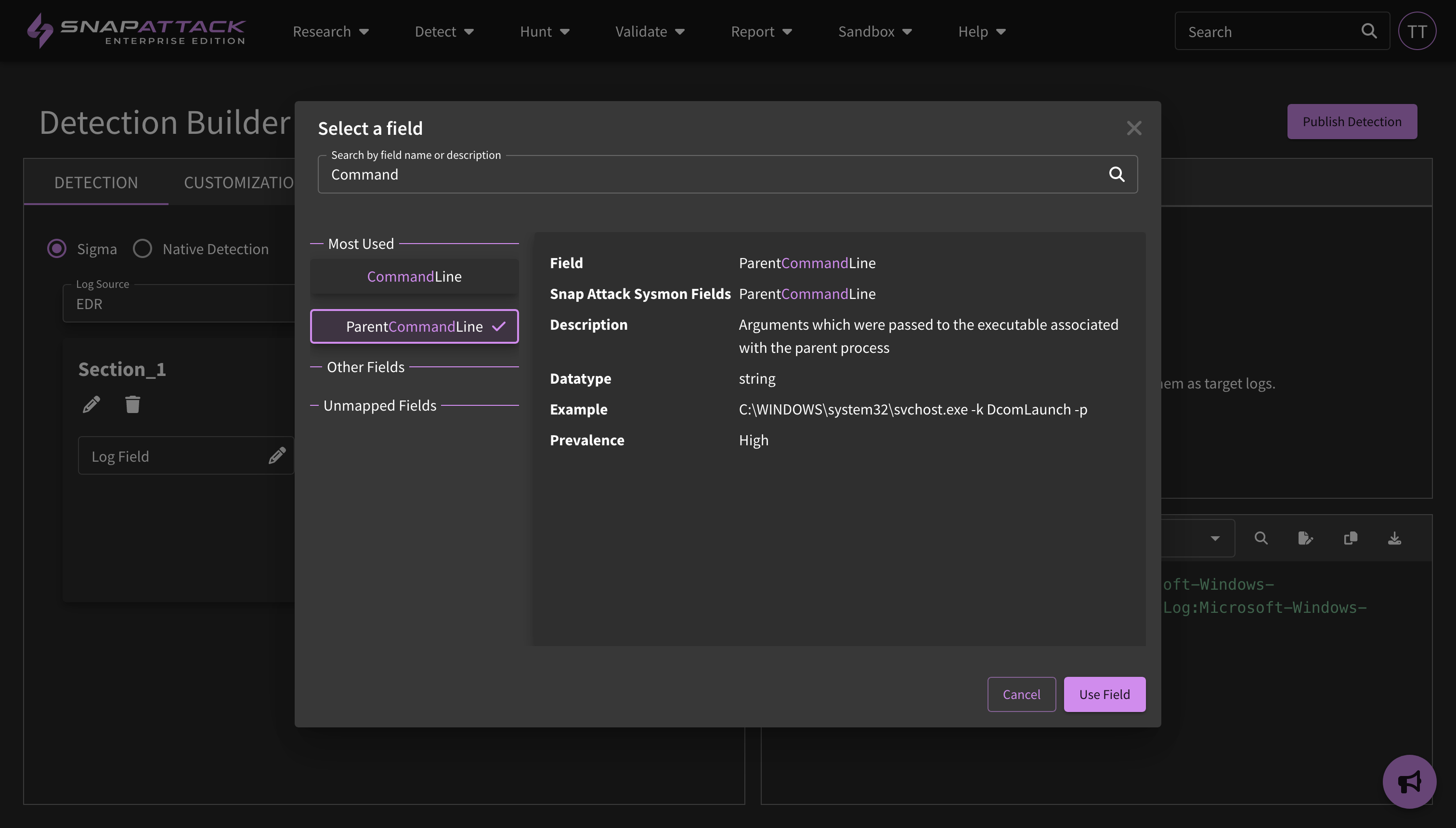
- Detection Builder Improvements: There is a substantial speedup for saving and publishing a detection. The detection builder also has a new field picker interface, which lets a user see additional information about a field such as its data type, example values, and prevalence across detections.
- Sort Order: The various content libraries and feeds can now be sorted by created or modified date; previously, the default sort order was only modified date to show the most recent content. Additional created and modified date fields have been added to the grid view, which complement the relative date fields that are seen by default.
- Persistent Layouts: A user's choices for grid or card view, as well as grid layout preference, such as which columns are displayed or hidden, or the ordering of columns, will now be persisted in the browser's local storage.
- The language configuration settings pages have been updated, making it easier to find and filter relevant configurations as well as make modifications.
- Updates to the USM Anywhere, Splunk, and Microsoft Sentinel compilers.
- General bugfixes and stability improvements to enhance the user's experience.
2023.09.01 - 2023.09.04
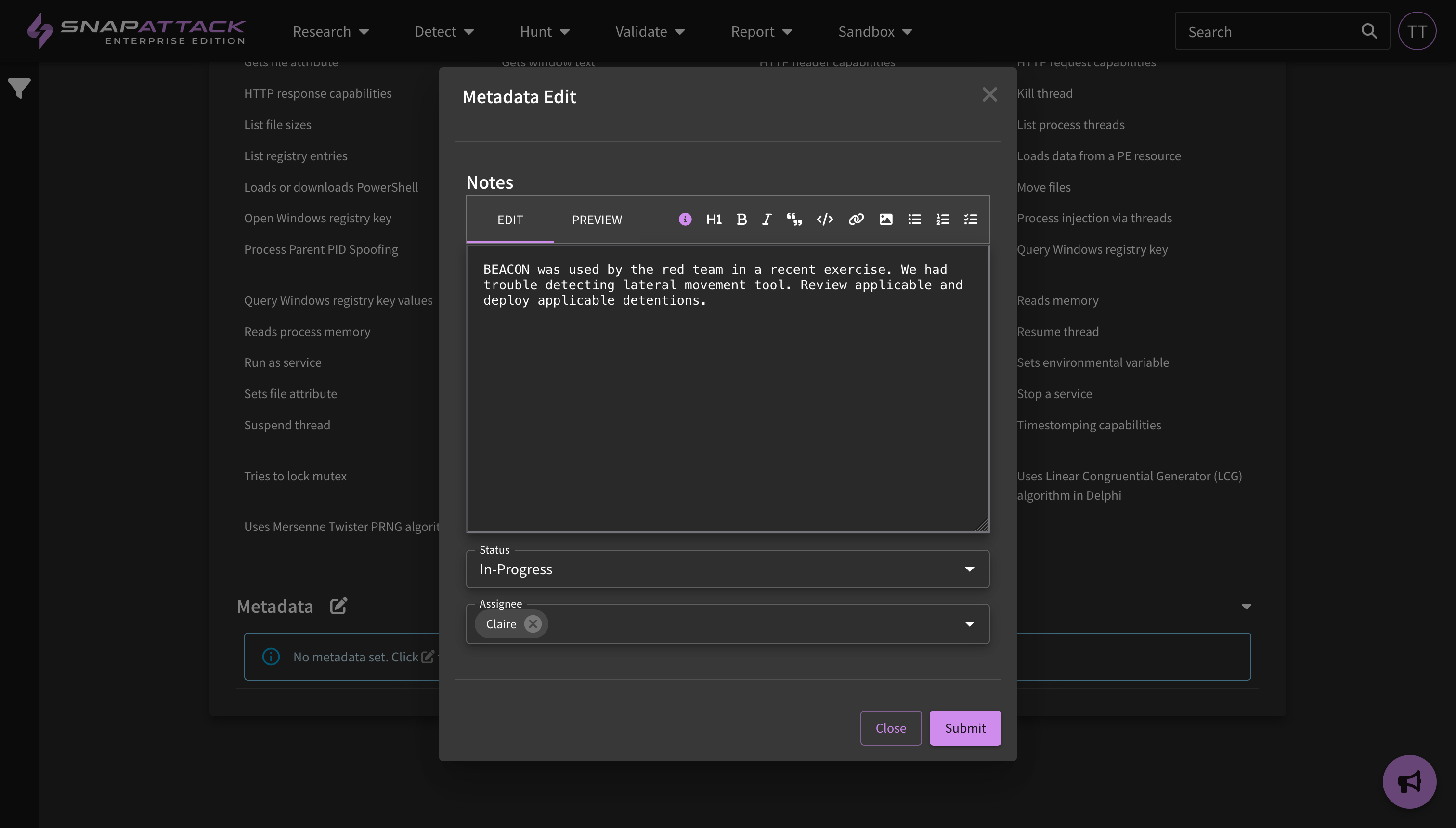
- Metadata Edit: Introduced the ability to edit metadata fields, including the name, applied content types, and options for select and multi-select fields. Metadata type migrations (e.g., short to long text field, or tag to select) are not supported at this time.
- Scheduled Confidence Tailoring: Confidence tailoring tasks can be scheduled for each integration. This will automatically run the tailoring task and apply the results at the specified intervals. Common use cases are a daily confidence tailoring task for new, "unknown" confidence detections (used in conjunction with the "Displaying Customer Confidence Only" feature described below) or a periodic re-calculation of all confidence scores.
- Detection Customization: The detection builder now has a customization tab that allows users to add false positive logic or other changes to detections that they do not own. This allows them to receive updates to the detection that would otherwise be lost if it were forked/cloned.
- Severity: Severities have been updated for ATT&CK v13.1 (and will be updated again for ATT&CK v14 when it releases next month). This sets the severity for a few new techniques that would previously show up as "unknown". Severities have also been applied and updated to attack scripts.
- The MITRE ATT&CK matrix is now filterable by platform. By default, only the enterprise matrix is shown.
- Tag inputs across the application have been updated to autocomplete fields for improved performance.
2023.08.07 Major Release
- Threat Intelligence, powered by Mandiant Advantage: SnapAttack has a strong integration and partnership with Mandiant (now part of Google Cloud) as a technology partner and a member of the Mandiant Cyber Alliance Program. In deepening this relationship, we are please to provide all SnapAttack enterprise customers access to threat intelligence from the Mandiant Advantage platform. This includes:
- Access to thousands of threat intelligence articles, seen in SnapAttack under the "Research" tab as Intelligence.
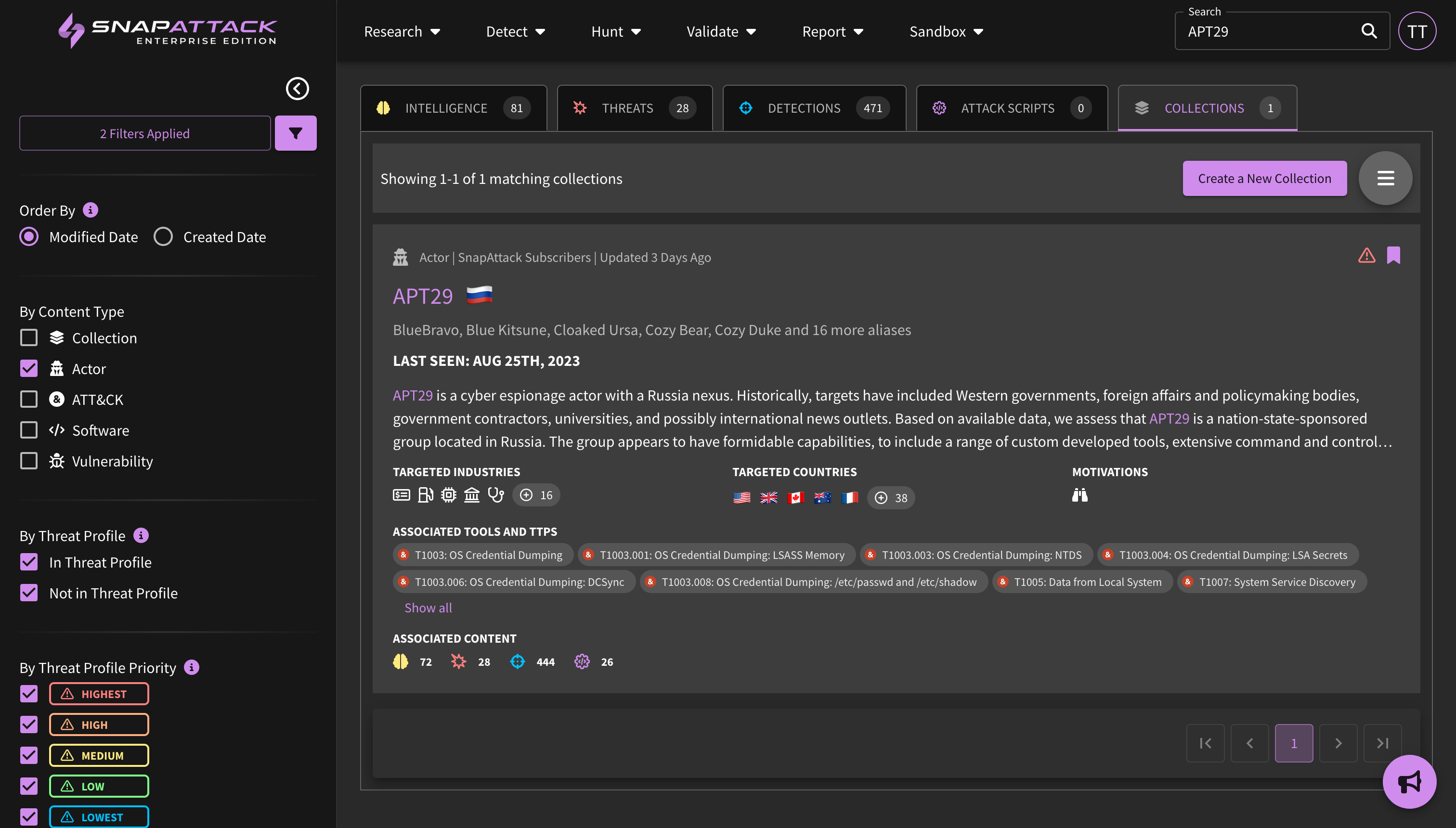
- Significant increases in the number of tracked threat actors (135%), malware and tools (592%), and high risk vulnerabilities (80%), seen in SnapAttack under the "Research" tab and as Collection types.
- Greatly improved depth and coverage for each of the above pages, including more precise MITRE ATT&CK coverage, target regions and industries for threat actors, tracking of malware/tool capabilities, insights into observed exploitation activity for vulnerabilities to improve prioritization, as well as remediation and mitigation guidance from vendors.
- Planned for Q4: New collection types centered around threat actor campaigns; Mandiant Indicators of Compromise (IOCs) deployable or huntable to configured integrations; and creation of an organization security profile to prioritize threats based on Mandiant Intelligence.
- Detection Builder Improvements: The first iteration of several improvements to the detection builder for workflows around creating, tuning, and maintaining detections. Detections that a user does not have edit permissions on, such as a community or subscription detection, can now be quick cloned in the builder and edited on the fly. Users can specify custom fields if they are not provided as autocomplete options. Addressed some minor bugs around tagging and testing detections.
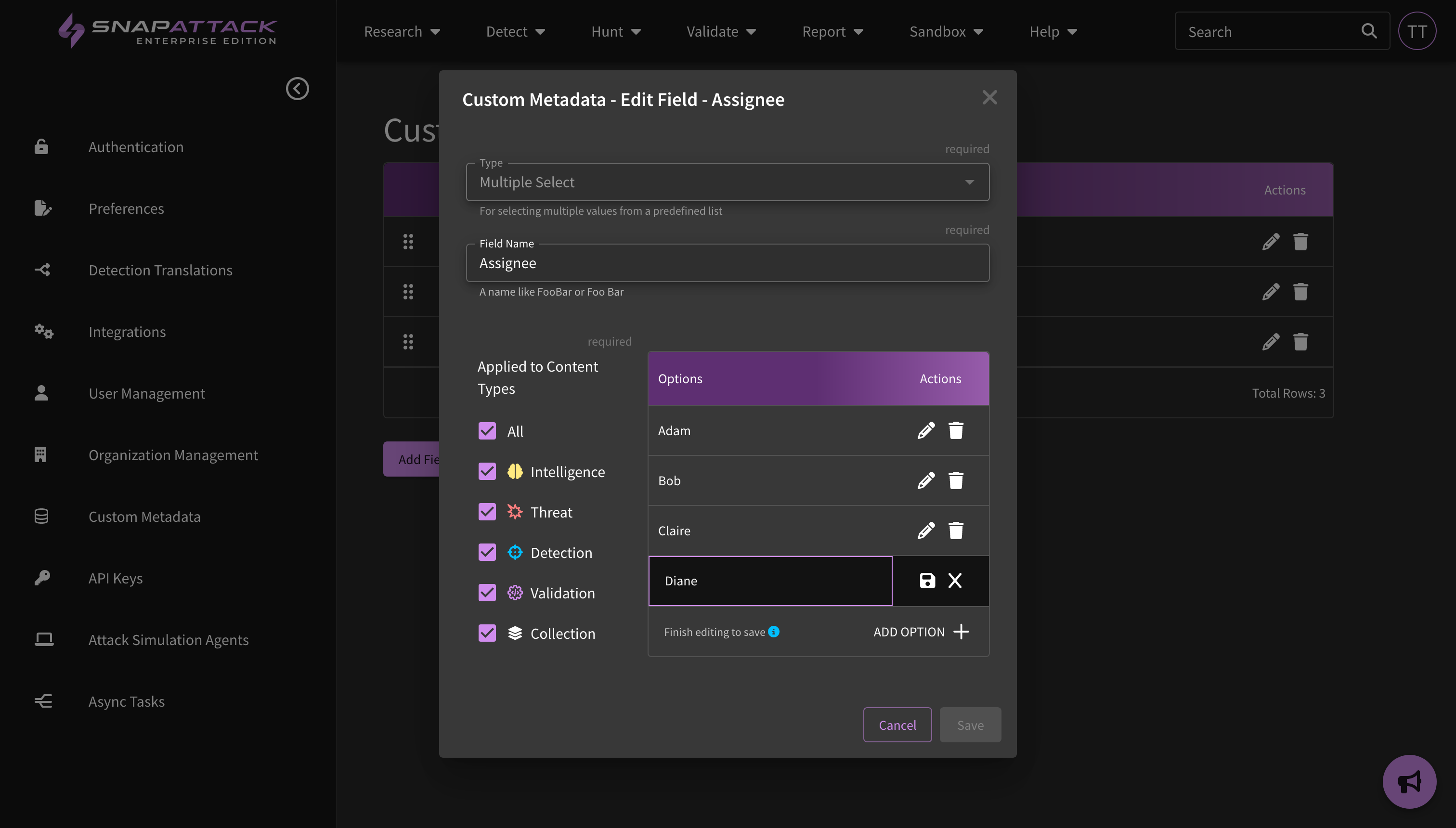
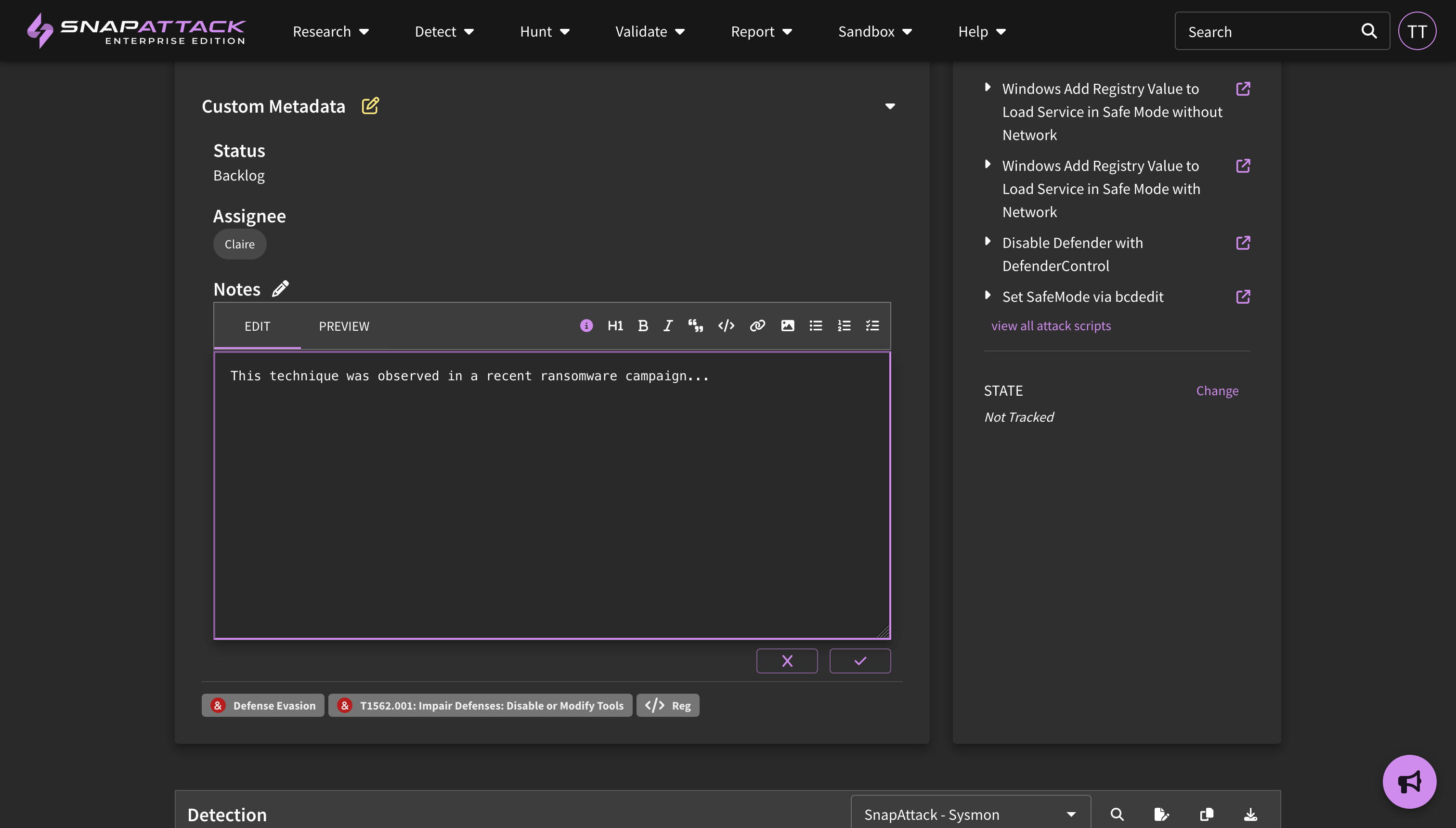
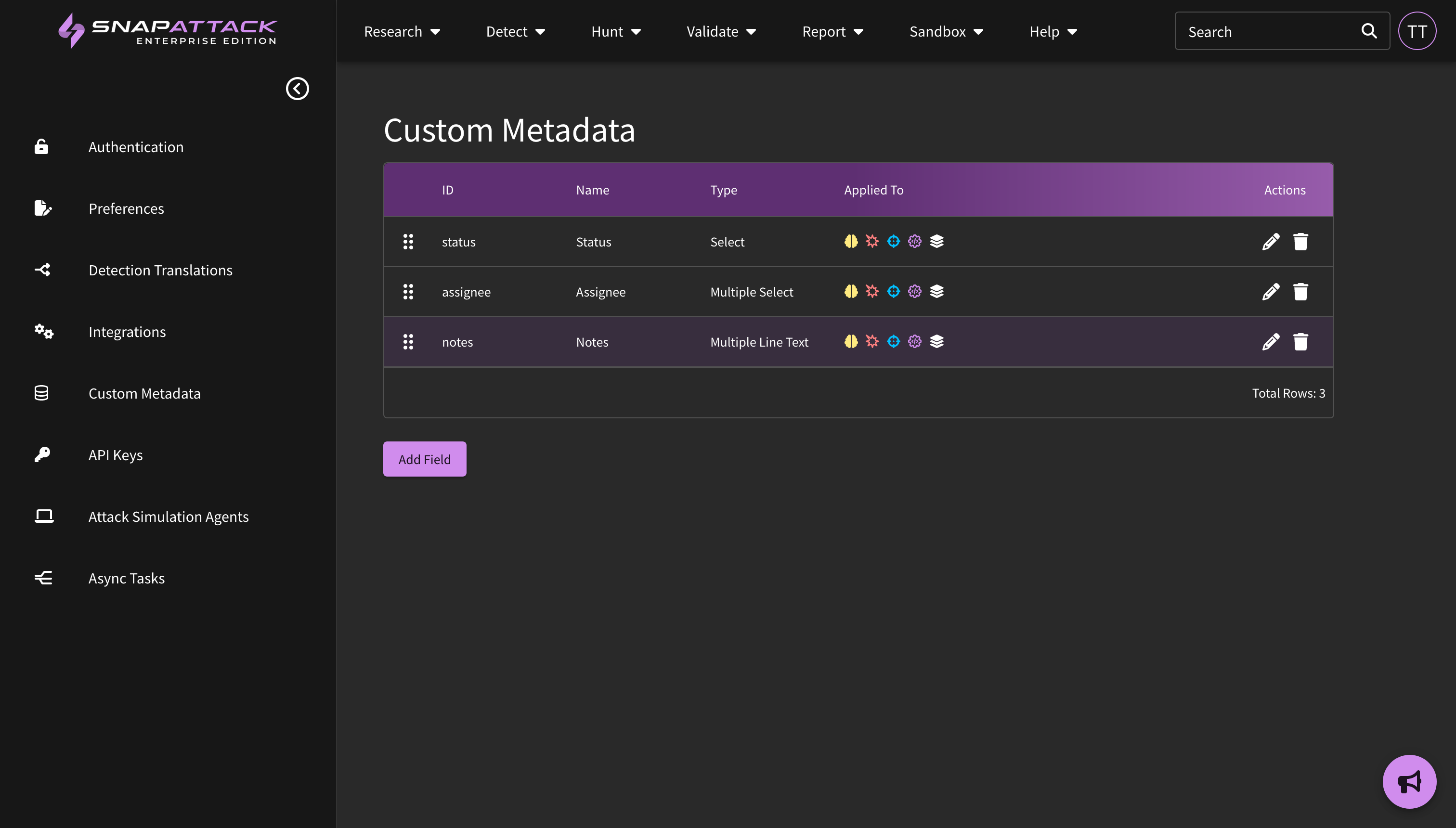
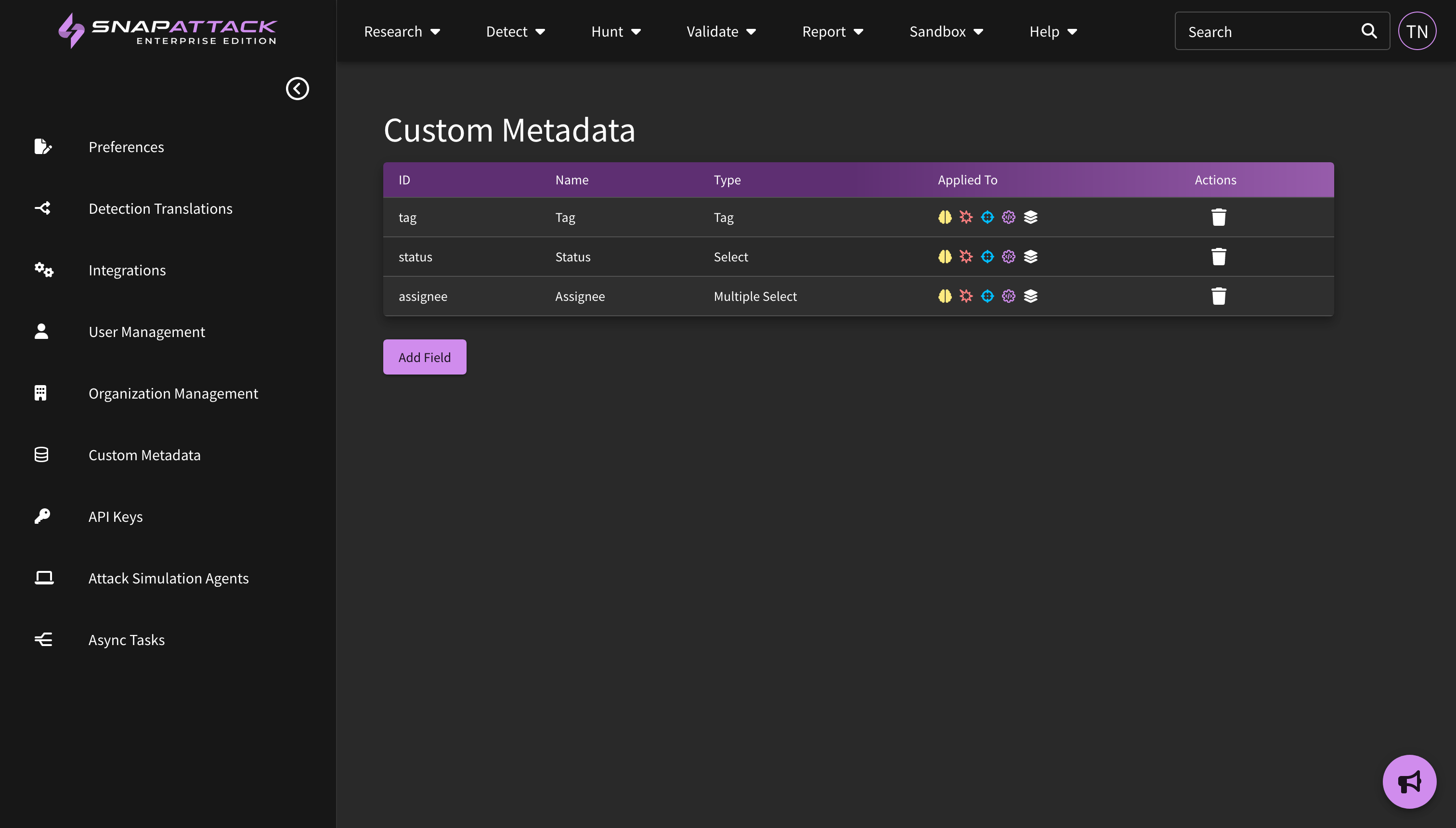
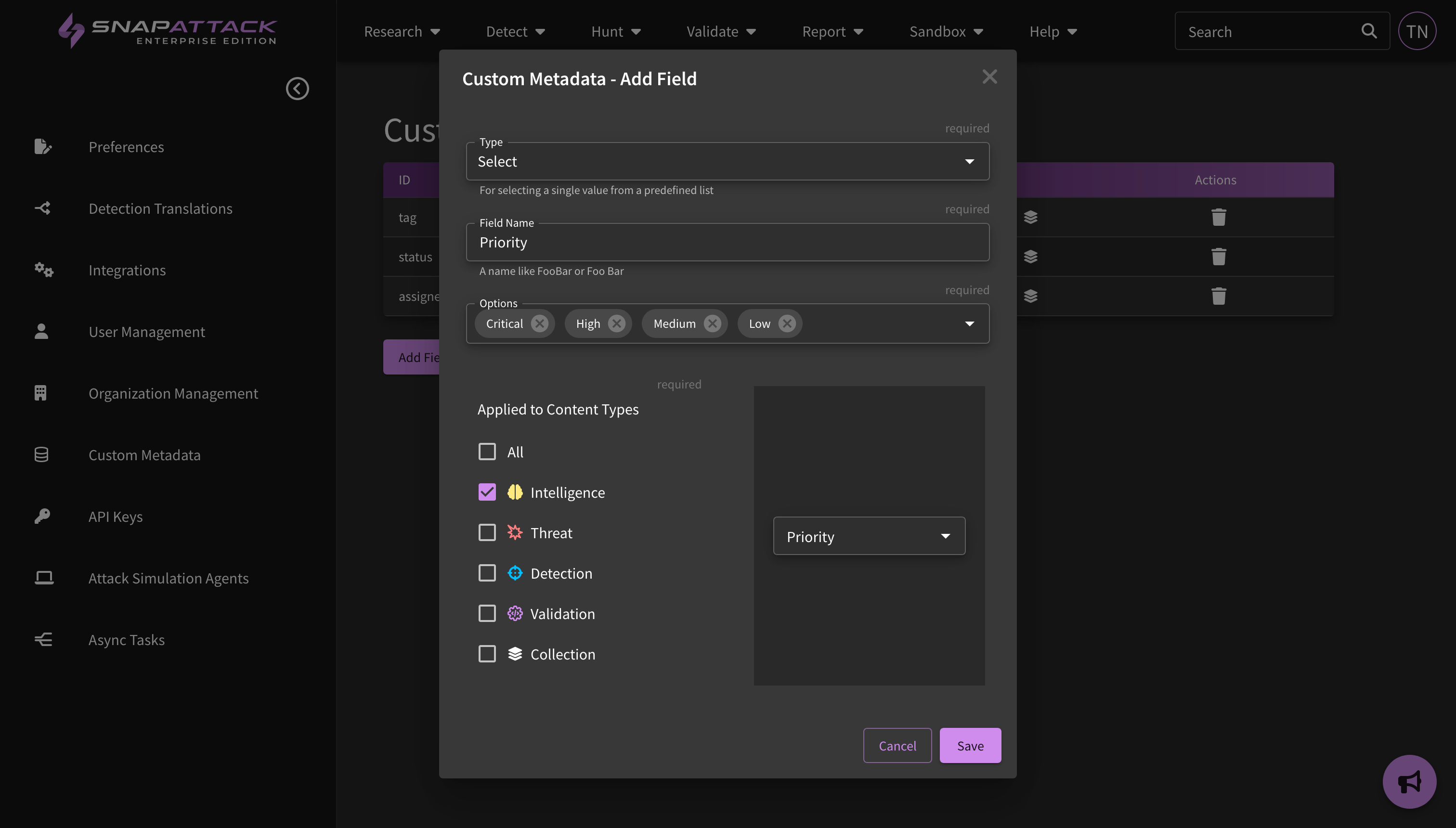
- Custom Metadata: Updated the way that custom metadata is viewed across the site. Users can click to edit custom fields, which will be hidden on pages where they are empty. The large text field now supports Markdown formatting. Searching for custom fields has been improved. Fields can be re-ordered by dragging and dropping them on the settings page.
- Integration Deployment Tracking: The deployment filter for detections has been updated to track additional states. Detections will be shown as 'queued' initially while SnapAttack syncs with the integration, and then will either be reflected as 'deployed' (successfully) or with 'error'. Errors typically will include things such as syntax issues or invalid fields, however multiple errors with newly deployed detections could be an indicator of poor integration health and should be reviewed. Deployment state can also be searched on a per-integration basis. Deployment states reflected on the detection feed will also reflect the worse case state if there are multiple deployments; for example, if a detection was successfully deployed to one integration but has an error in another integration, it will be shown as 'error' in the search results. Users can also now more easily view detections that have not been deployed correctly from the feed with these filters. Detections that are 'queued' can be manually synced via the "sync now" button on the integration settings page.
- Displaying Customer Confidence Only: SnapAttack anonymizes customer and other real-world data to calculate global confidence values for detections. However, sometimes these values will vary within a customer's environment. Customers who use our confidence tailoring feature can now configure the ability to see only their tailored values, meaning all new detections will appear as 'unknown' until the confidence has been calculated. This helps reduce the possibility that a noisy detection could be deployed to a production environment. In the next release, customers will be able to configure scheduled tasks for confidence tailoring, such as running all 'unknown' confidence detections every 6 hours or all detections once every month.
- Hunter's Workbench: An early beta release of the Hunter's Workbench is available to customers who opt-in. Hunter's Workbench offers an alternative to deploying detections as alerts to configured integration, such as a SIEM or EDR. Detections can be hunted across one or more integrations, with the results returned and aggregated in SnapAttack for further analysis, correlated across multiple rules or risk-based alerting when multiple events fire for a specific hostname, IP address, user, or other entity. Please reach out to your customer success manager for details.
- The "add to collection" interface has been updated so that new collections can always be created.
- Small improvements have been made to the "grid view", including the ability to sort by additional column headers (such as severity and confidence) and adding checkboxes to select individual items within all collections.
- Timestamps have been localized on several pages, and timezone information is displayed to add additional clarity, such as when a detection was deployed or when an integration last checked in with SnapAttack.
- Multiple small bugfixes and improvements to Google Chronicle and Microsoft Sentinel detection compilations.
2023.08.04 - 2023.08.06
- Updates to infrastructure and infrastructure as code scripts, resulting in increased application performance, scalability, and reliability.
2023.08.01 - 2023.08.03 Hotfix
- Additional improvements to Google Chronicle translations
- General bugfixes related to the last major release
2023.07.02 Major Release
- Navigation Changes: Updated the site navigation to better reflect user workflows and action-based outcomes.
- Research - formerly "Intelligence" and "Collections", we're refocusing our threat intelligence around threat actors, malware/tools, vulnerabilities, and MITRE ATT&CK techniques. Users can learn more about threats that align to these categories, deploy available detections, launch threat hunts, and use attack scripts to validate deployed detections. Users can also still create custom collections to prioritize and track topics that are relevant to their organization.
- Detect - formerly "Detections", this focuses on the elements of the detection-development lifecycle (DDLC). Users can quickly view recommended and deployed detections, or the entire detection library; they can tailor detection confidence to their organization, and they can create new detections in our no-code detection builder (IDE).
- Hunt - threat hunting, powered by SnapAttack, with a preview available at Blackhat '23 and an early-access version available to select customers (reach out to your customer success manager for more information). Threat hunting allows users to run any detection from the library as a hunt, bringing the results back into SnapAttack for further analysis. Roadmapped and in-progress features include normalization of key fields for XDR-like joining and pivoting across different logsources, automatic and scheduled hunts, correlated events and risk-based alerting (RBA), and customizable dashboards and reporting.
- Validate - previously, the "Threats" tab included our entire threat library, including both static threats that were captured for reference in our library as well as automatable threats that could be replayed in a customer's environment. We've separated out the automatbale threats as "Attack Scripts". Users can now view the attack-as-code that backs these scripts, as well as create their own. Attack Scripts are executed as an Attack Simulation in the customer's environment, and a customer can view the Attack Simulation Results as a means of measuring existing detection coverage or end-to-end validation of newly deployed detections.
- Report - all reports and dashboards are located here.
- Sandbox - formerly "Threats", the threat library has been relocated here. Use the attack capture agent or attack range to capture adversary TTPs in our sandbox for analysis by detection engineering and threat hunt teams.
- NIST 800-53 Dashboard: Using the ATT&CK Control Framework Mappings, risk-centric organizations can view their detection coverage across NIST 800-53 families and controls. Identify control coverage gaps and deploy detections to meet control requirements. This feature is available to all subscribers.
- Custom Metadata: Organization administrators can define new custom metadata fields for any platform content item (intelligence, threats, detections, attack scripts). This allows users the flexibility to track additional information in the platform and fit into existing organizational workflows and processes. Custom metadata fields can be anything — provide triage and remediation notes for a detection; create workflow statuses and assignees for project management; link to external URLs like your Jira or ServiceNow ticketing system; map content to your organization's own identifiers and naming conventions. All organization users can set or modify metadata values. This feature is available to all subscribers.
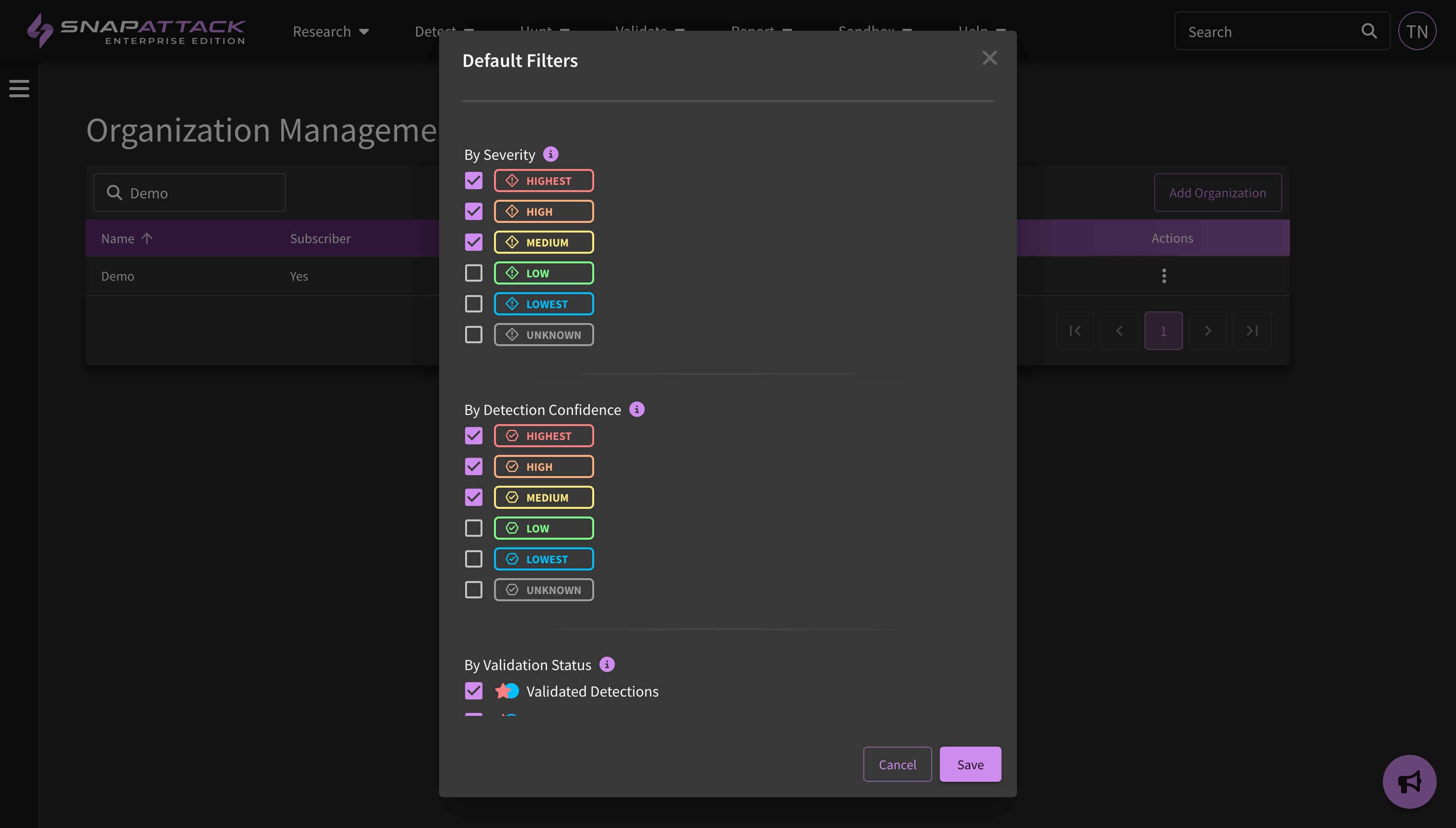
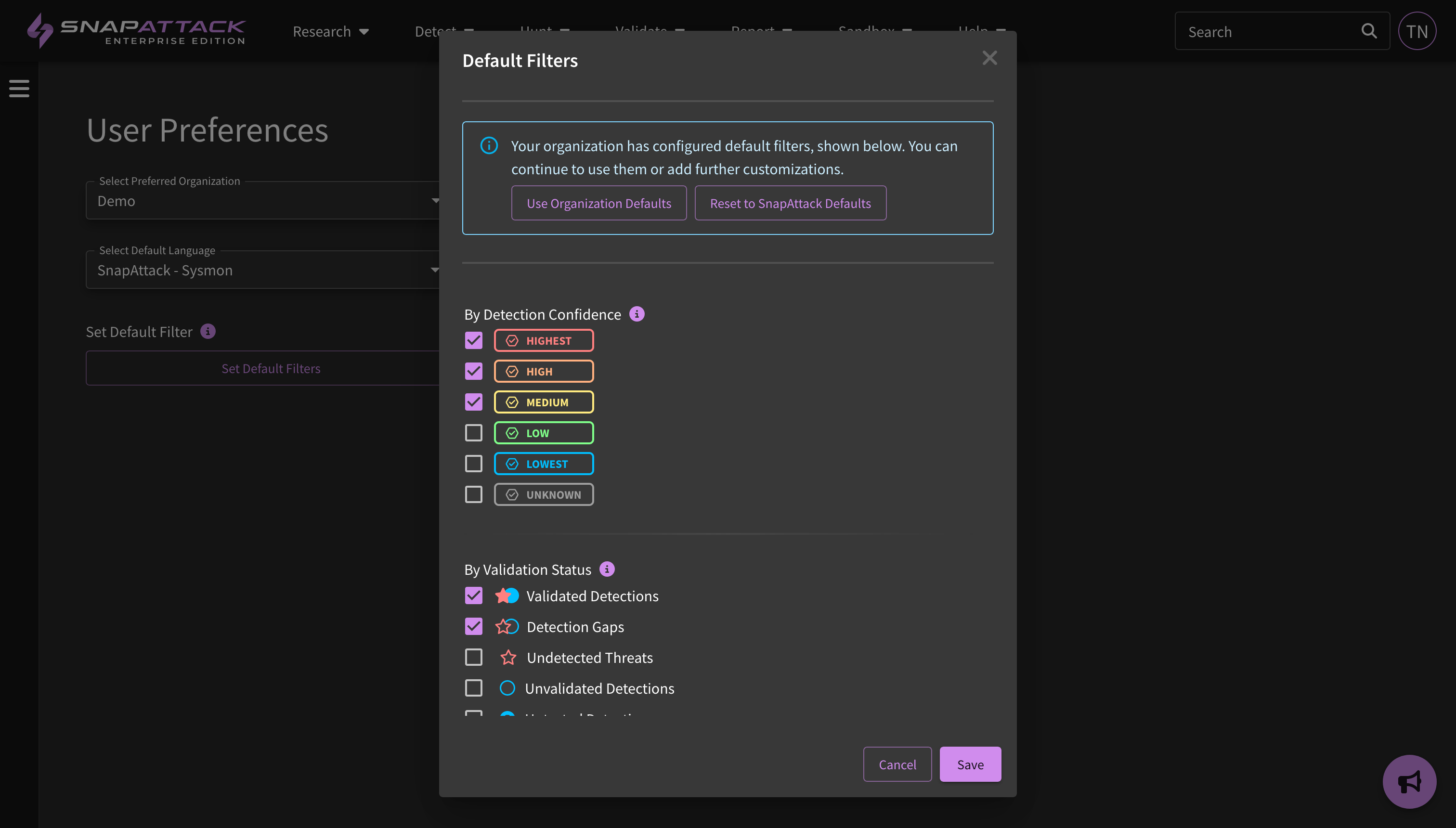
- Default Filters: Configure site-wide filters to make it easier to find relevant content across our libraries. Only want to see high confidence, high severity, validated detections that are compatible with your integrations? Done! Organization Administrators can define organization-wide default filters from the "Organization Management" settings page. Users will inherit these filters by default, but can override or configure their own default filters from the "Preferences" settings page. This feature is available to all subscribers.
- Integration Settings and Health: Integrations have been updated to allow more than one search, hunt, and deployment language to be specified. This allows a single integration to support multiple languages, or specify different languages for use case (e.g., Chronicle UDM for search, and Chronicle Yara-L for hunt and deployment). Integrations also have an icon next to them to report on their health status, that includes any recent messages or errors and the time of last sync. These features are available to all subscribers.
- Attack Scripts / Validate: Our threat library has always contained both manually created and scripted attacks. Scripted attacks have the benefit of being exportable, meaning that you can run them in your network as a diagnostic to measure your current coverage for that threat, or you can deploy detections and use them as a validation module for true end-to-end testing. To make it easier to create, modify, and use attack scripts, we have separated them out into their own content type. This feature is available to all platform users, though creating and executing attack scripts are limited to subscribers.
2023.07.01 Hotfix
- Updated behavior of the Google Chronicle integration due to breaking changes on their end. The Archive Rule and Delete Rule API endpoints were disabled for customers. If those endpoints are not available, undeploying a detection from SnapAttack will no longer be able to remove the rules page, but they will be disabled and the title will be change to note that they have been undeployed. Customers who wish to delete undeployed rules should reach out to Chronicle support to have these API endpoints enabled for their organization.
2023.06.03 - v2023.06.05
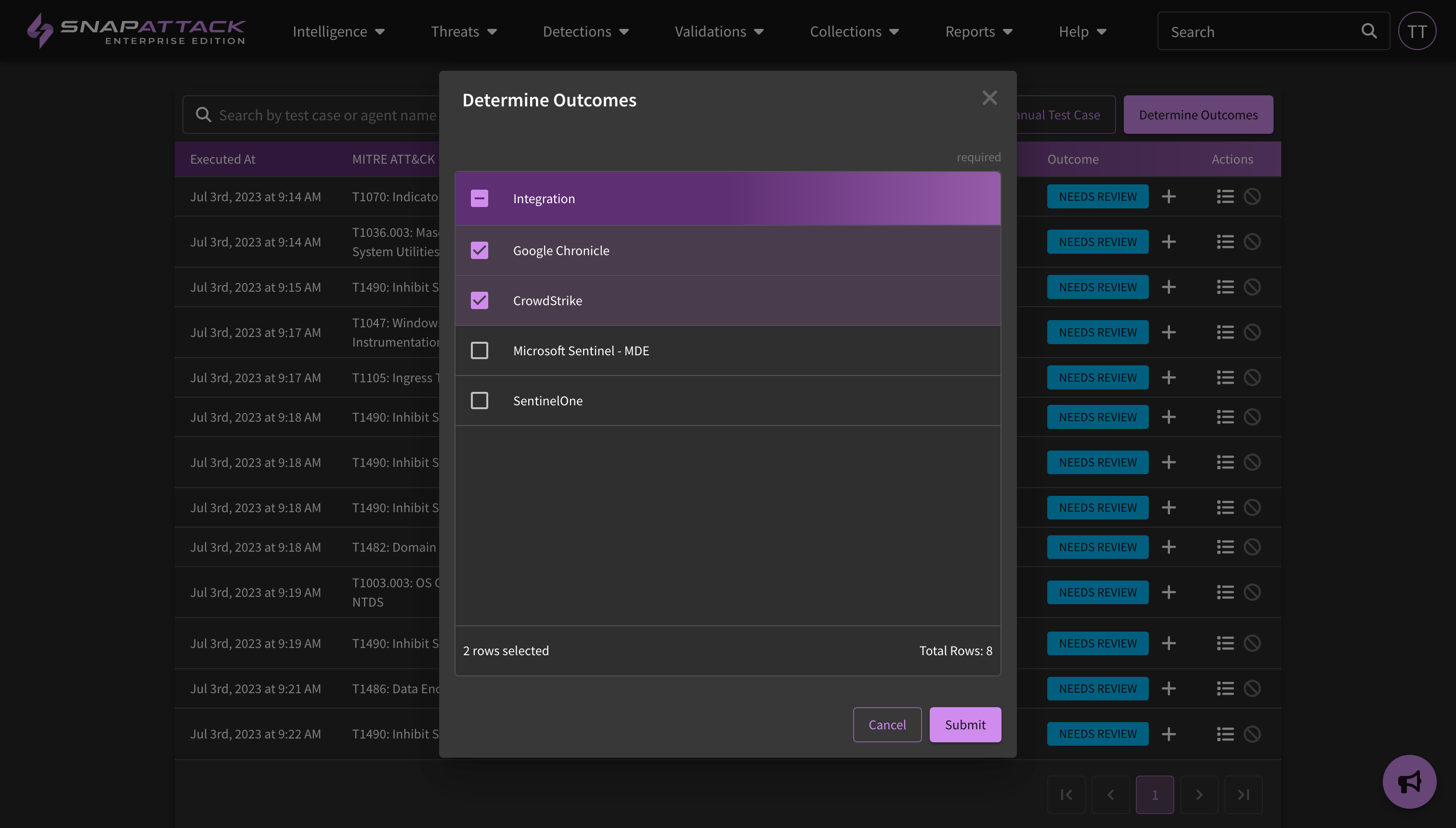
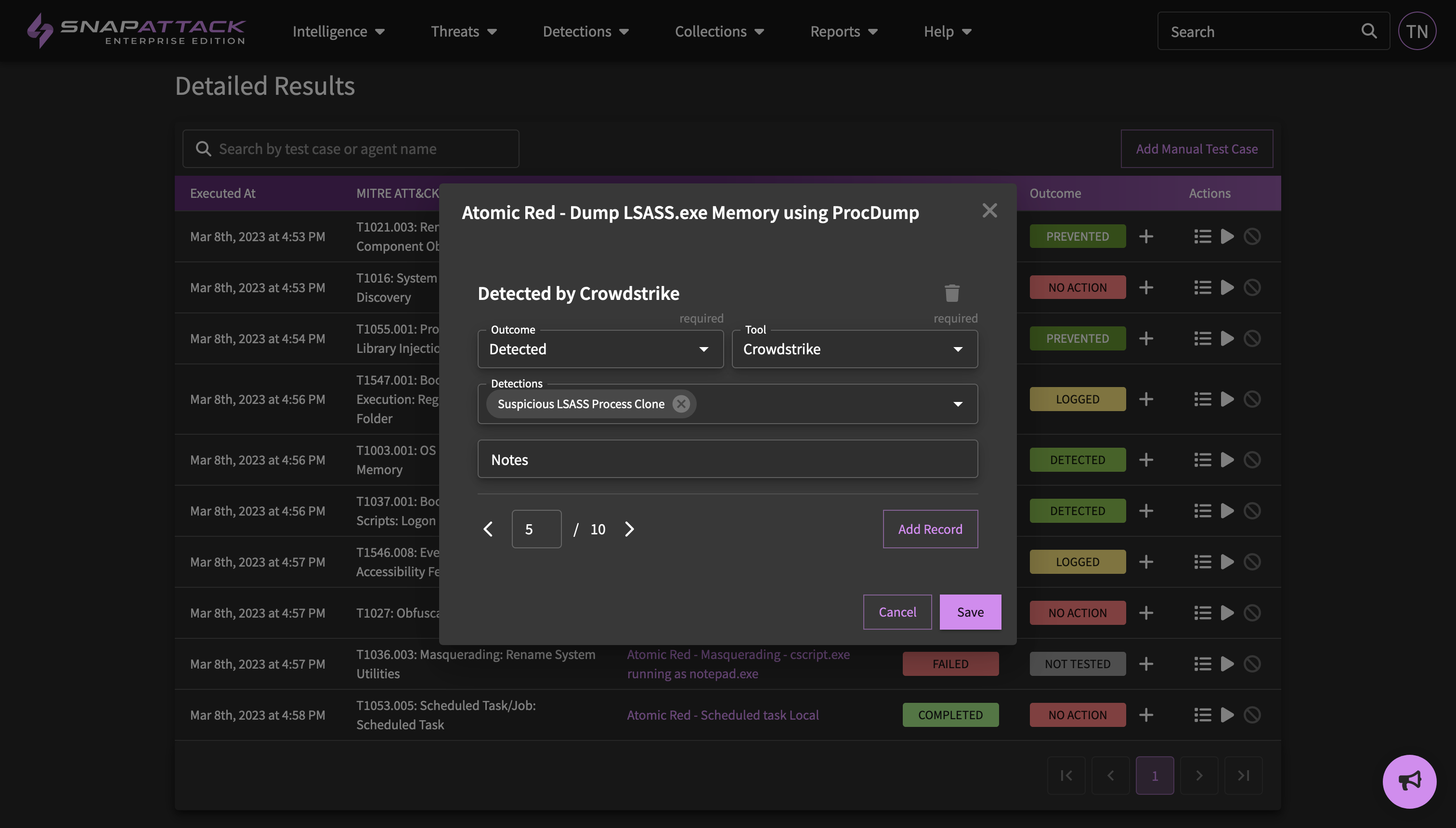
- Determine Outcomes: Previously, completed attack simulations would only report on the attack status - did the attack succeed or fail? While this is important, ultimately the goal is to determine the defensive outcome - was the attack prevented or detected? Do we have log visibility and coverage for it? Now, you can automatically determine detection outcomes for a configured integration by simply clicking the "Determine Outcomes" button and selecting your integrations.
- Updated the ATT&CK collections to have links to the related tactic, techniques, and subtechniques.
- Improved the confidence tailoring workflow to better track tasks that are in-progress or have completed with errors.
- Fixed a bug where filters were not working inside of collections.
- General bugfixes and stability improvements to enhance the user's experience.
2023.06.01, 2023.06.02
- Tailored Confidence: introduced the ability to test all compatible detections in the platform against an organization's integrations and update the confidence values. This allows an organization to measure how a detection performs in their environment. Confidence tailoring can be launched from the detection feed, and results can be seen and applied on the confidence tailoring dashboard.
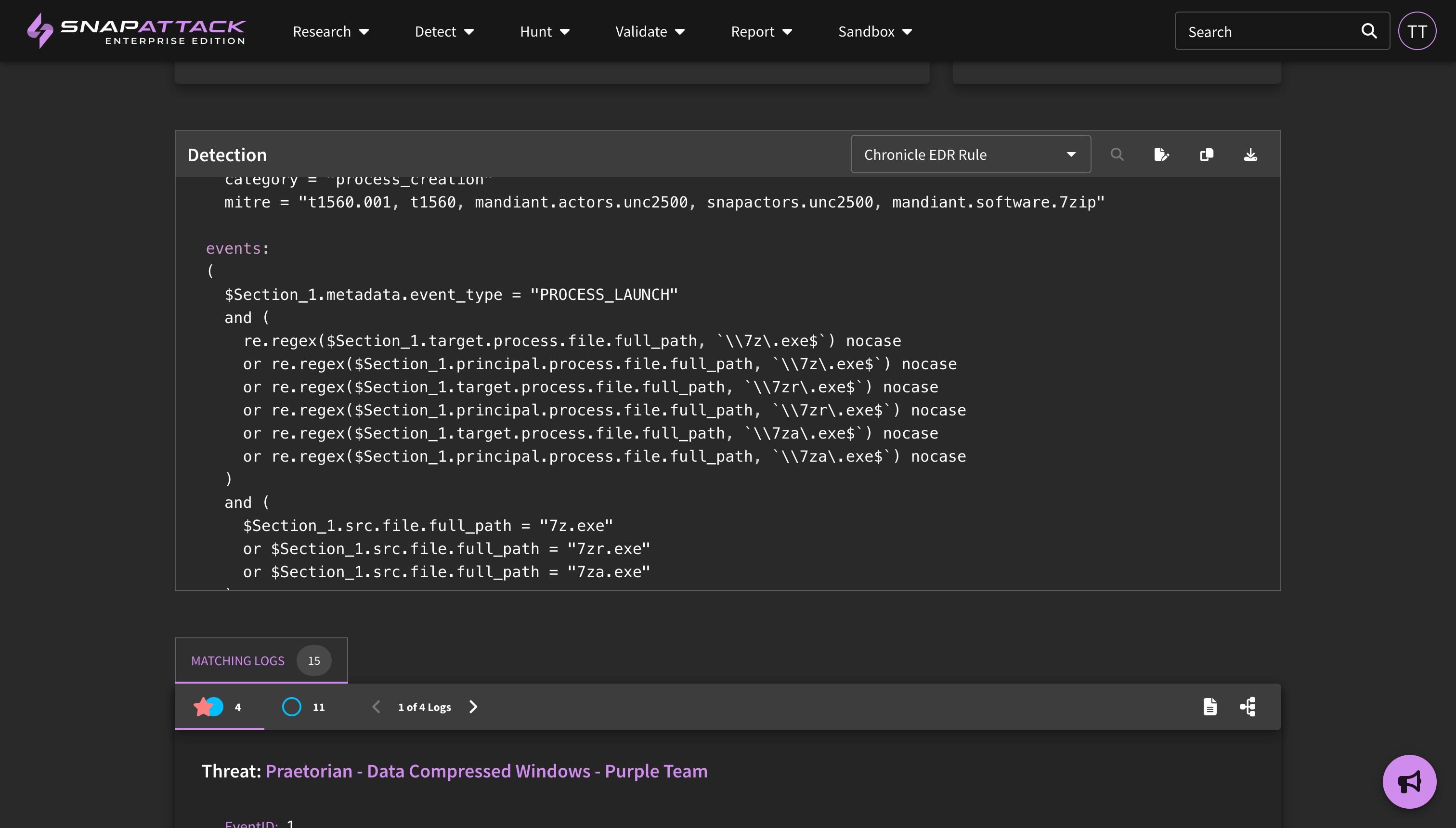
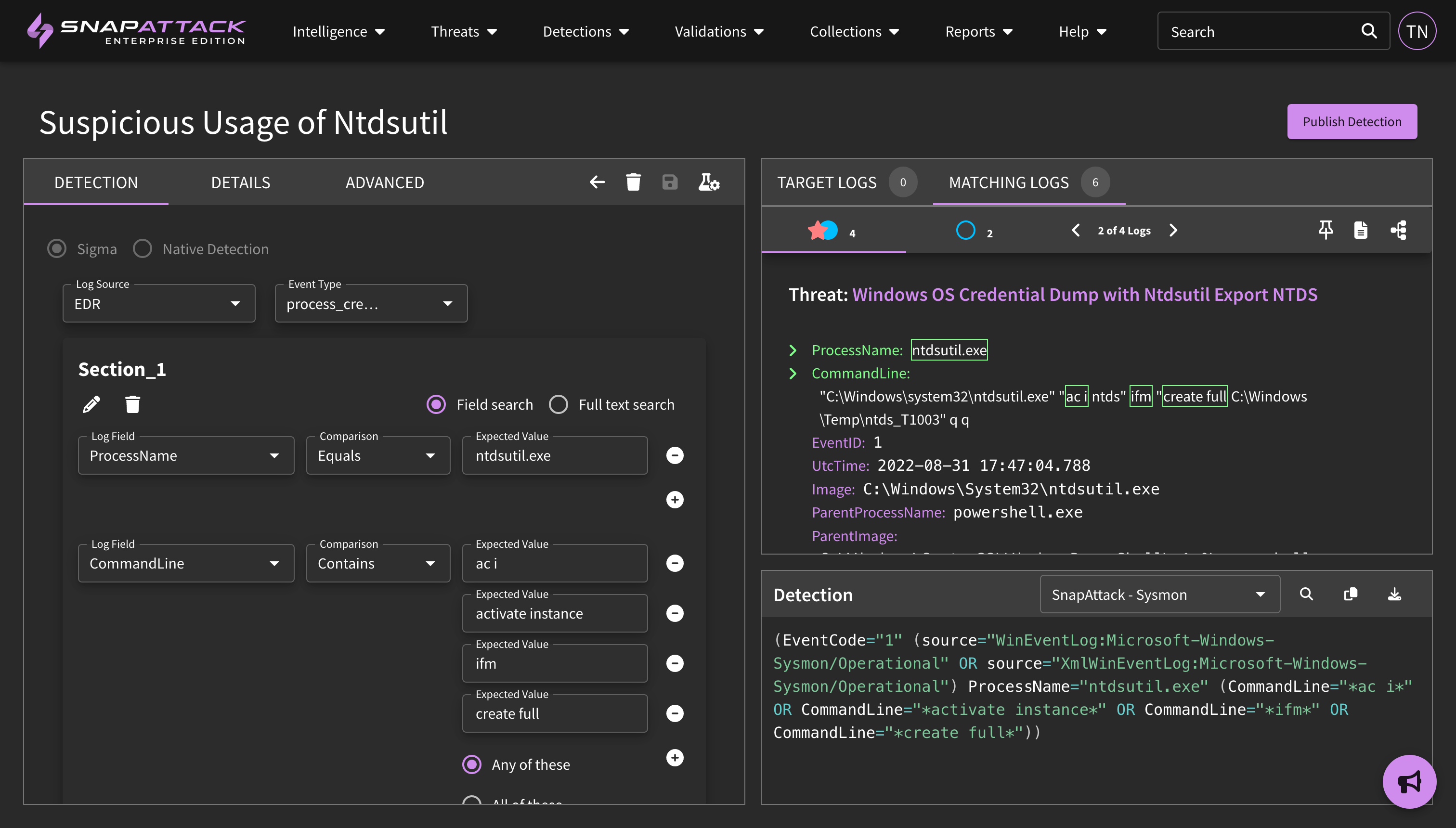
- Added the ability for a user to test their detection against SnapAttack's threat library from the Detection IDE and view matching logs. Updated the Detection IDE to display matching logs for published detections.
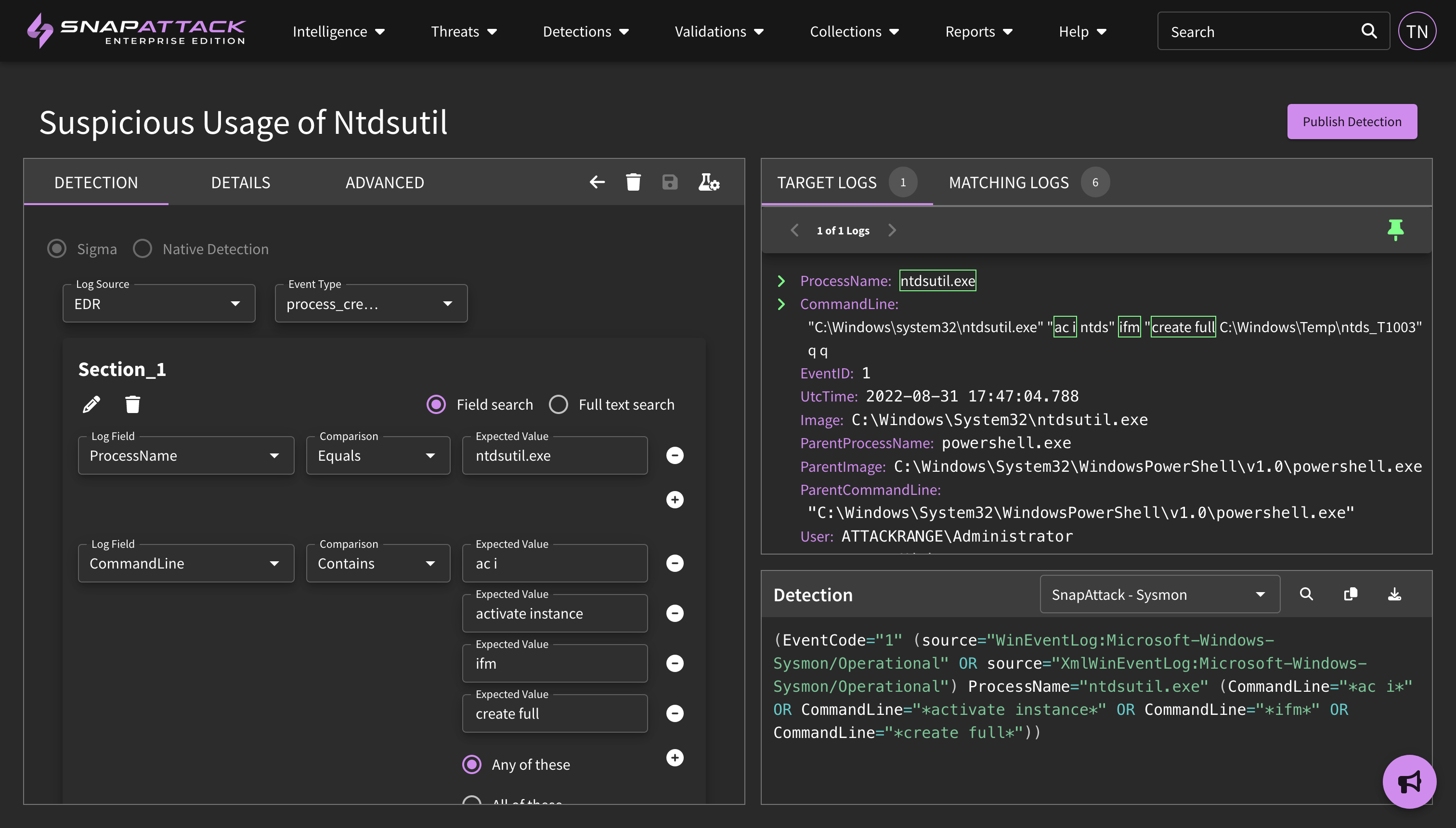
- Introduced the concept "pinning" a target log in the Detection IDE. When creating a detection from a specific event log, that log will automatically be brought into the IDE and pinned as a target log. A user may also test their detection against the threat library and pin specific logs as target logs. Pinned logs will remain in the IDE when you go back to the page, and will also stay even if they no longer match the detection logic, which can be helpful if you are tuning a detection and want to make sure your false positive reduction logic does not accidentally filter out your true positive test cases.
- Fixed bugs related to recent updates to the filter system, including navigation issues when hitting the back button after applying filters and issues filtering inside of collections.
- Fixed a bug where users may not see menu items for certain functions, like export detections.
2023.05.05, 2023.05.06 Hotfix
- Update async tasks for breach and attack simulation cached views
- Fixed an async task that was causing database locking issues
2023.05.04
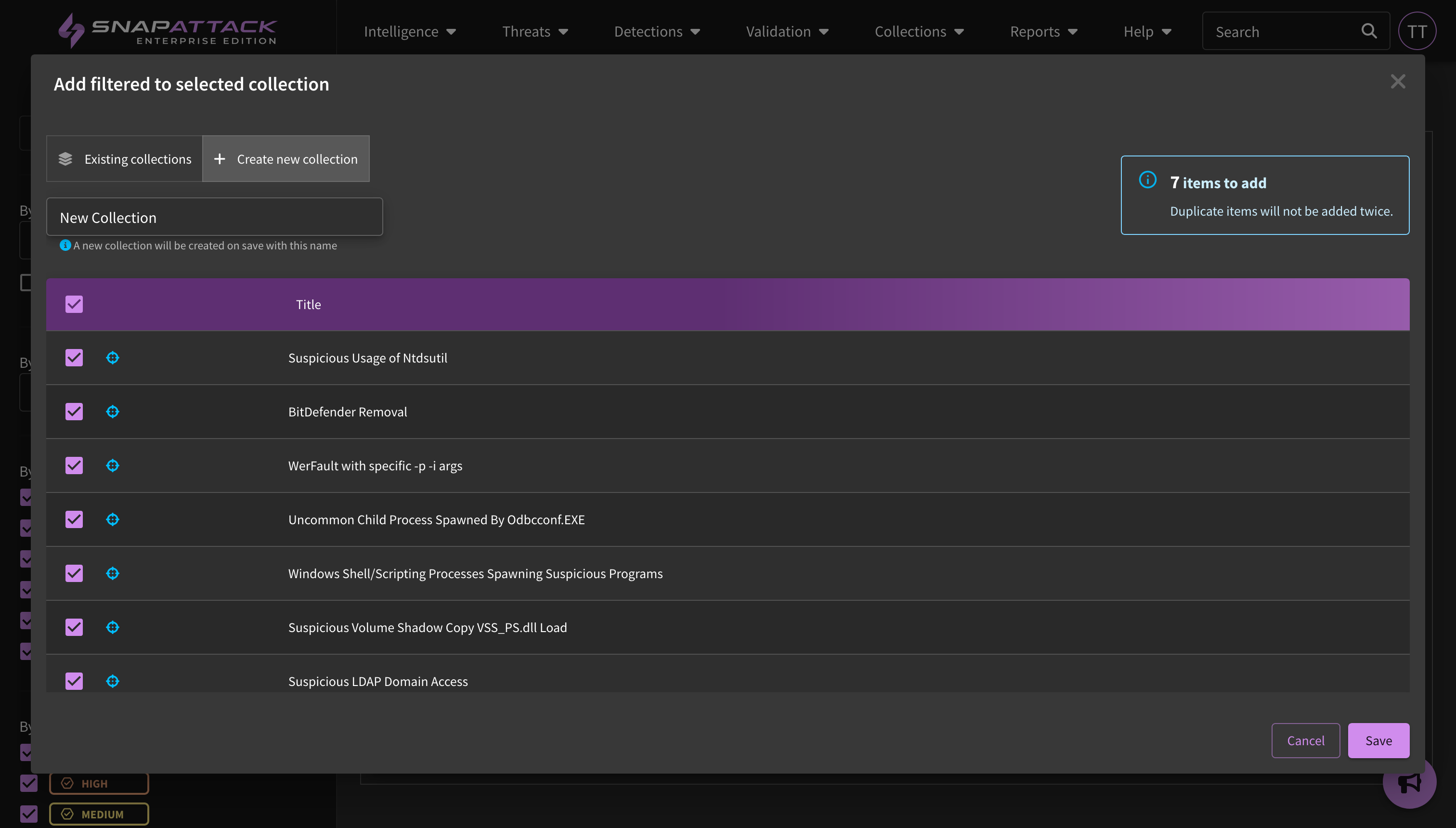
- Added the ability for a user to create a new collection when managing content; previously, a user could only add content to an existing collection.
- Updated the API endpoint for deployed detections to allow a user to filter by the last updated date, returning only the detections that have changes after that date.
- Upgraded MITRE ATT&CK to v13 (view changelog). This version of ATT&CK for Enterprise contains 14 Tactics, 196 Techniques, 411 Sub-techniques, 138 Groups, 22 Campaigns, and 740 Pieces of Software. SnapAttack content with deprecated/revoked ATT&Ck tags are automatically updated in the platform.
- Added a miniature ATT&CK matrix view for attack simulation results page to show the tactics and techniques used during that simulation.
- Added the ability to collapse the integrations section when viewing a detection. This improvement largely affects MSSP customers and those with several configured integrations.
- Updated the backend and packer build scripts to better handle when an attack range image fails to build, and continue to use the older version in the event of a failure. This should prevent missing or unavailable VM images from appearing in the application.
- Added the ability to delete attack plan results and uploaded attack captures.
- Improved the Sentinel One integration to reflect the severity value from SnapAttack; "highest" severity detections from SnapAttack map to "critical" in Sentinel One, and "lowest" and "low" from SnapAttack map to "low" in Sentinel One.
- The SnapAttack Splunk application has passed the cloud vetting process and may be used by customers within the Splunk Cloud Platform.
- Fixed a bug around orphaned detections that were deployed to a deleted integration.
- Fixed a focus trap behavior where a user may not be able to interact with a modal inputs if a hamburger menu is still opened.
- Fixed a bug where a user would encounter an error message when editing a threat.
2023.05.02, 2023.05.03 Hotfix
- Update permissions for stats collection, which powers several dashboards
- Update some infrastructure-as-code scripts for the production deployment
2023.05.01
- This release focused on reducing tech debt and fixing bugs within the application.
- Upgraded numerous libraries and dependencies to the latest version. This was outside of our established process for addressing dependencies with known vulnerabilites.
- Replaced legacy UI components with Material UI. Users may notice some small, subtle styling changes throughout the application where legacy components or styling existed.
- Implemented a global error parsing module on the frontend, which improves handling and processing for error messages displayed across the application.
- Refactored the filter system. While there are no visual changes, the filter system is more testable and maintainable, and will allow for future features around saved base filters and further customization.
- Improved backend processing for asynchronous tasks.
2023.04.04 Hotfix
- Updated and enabled the Commando VM image in the attack range, providing a Windows-based attack machine.
- Updated the Windows domain controller background image to make it easier to tell the difference from the desktop machine.
- Fixed a bug when checking out multiple VMs from the attack range.
- Fixed a bug where long descriptions would not properly wrap to new lines on the threat page.
- Fixed a bug where deploying or hunting detections from a collection would not properly observe the selected filters.
2023.04.03 Major Release
- Curated Collections: launched special curated collections around threat actors, software, vulnerabilities, and MITRE ATT&CK. Intelligence, threats, and detections that have one or more of these tags will be shown as linked content in the collection. Organizations will be able to see their private content if appropriately tagged, but that content will not be able to be seen by other organizations. This initial release allows the grouping of content around these items, and the ability to execute attack simulations or deploy detections within the collection. Future versions will include reporting around an organization's protection against that threat. Tags and collections will be expanded over time by our content team.
- Added the ability to search the entire threat timeline for specific words, such as a detection name.
- Added the ability for a user to clone a collection. This allows them to make changes to collections they do not own, such as modifying the collection title, description, or linked content.
- Upgraded the Ubuntu VM in the attack range to 22.04 LTS and fixed multiple small issues, such as the color managed device prompt and home directory permissions.
- Updated CapAttack with improved error logging and an optional a headless mode.
- Improved the stats collection backend which stores and processes data for dashboards and reports, resulting in faster load speeds.
2023.04.02 Hotfix
- Fixed a frontend crash when a user would click on a detection from the feed.
- Fixed two user reported bugs around API keys.
- Fixed two bugs with Google Chronicle detection translations with a missing space for AND NOT clauses, and certain translations failing for CNF.
- Fixed bugs around the user and organization management interfaces.
2023.04.01
- Added a Windows domain controller (DC) victim machine to the attack range. Attack techniques requiring a domain-joined machine can be done on this host, or the other Windows desktop can be manually joined to this domain for multi-host attacks (e.g., lateral movement).
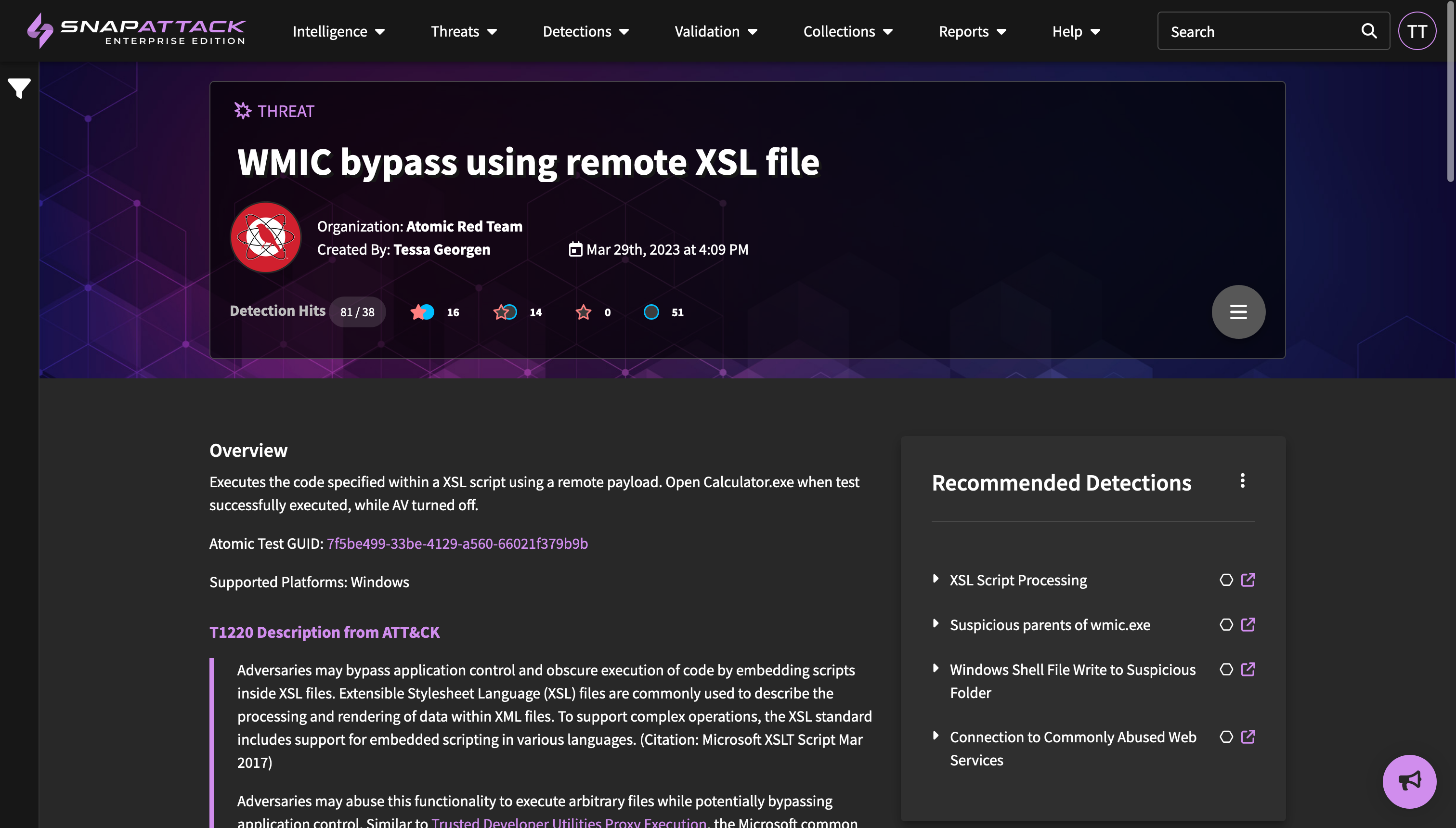
- Updated threat content for Atomic Red Team and Mandiant Security Validation. Updated Sigma Community content, ensuring original author and license URL are properly displayed, and providing a link back to the detection repository. Relocated these content items to their own content provider organizations, which makes filtering and finding this content easier.
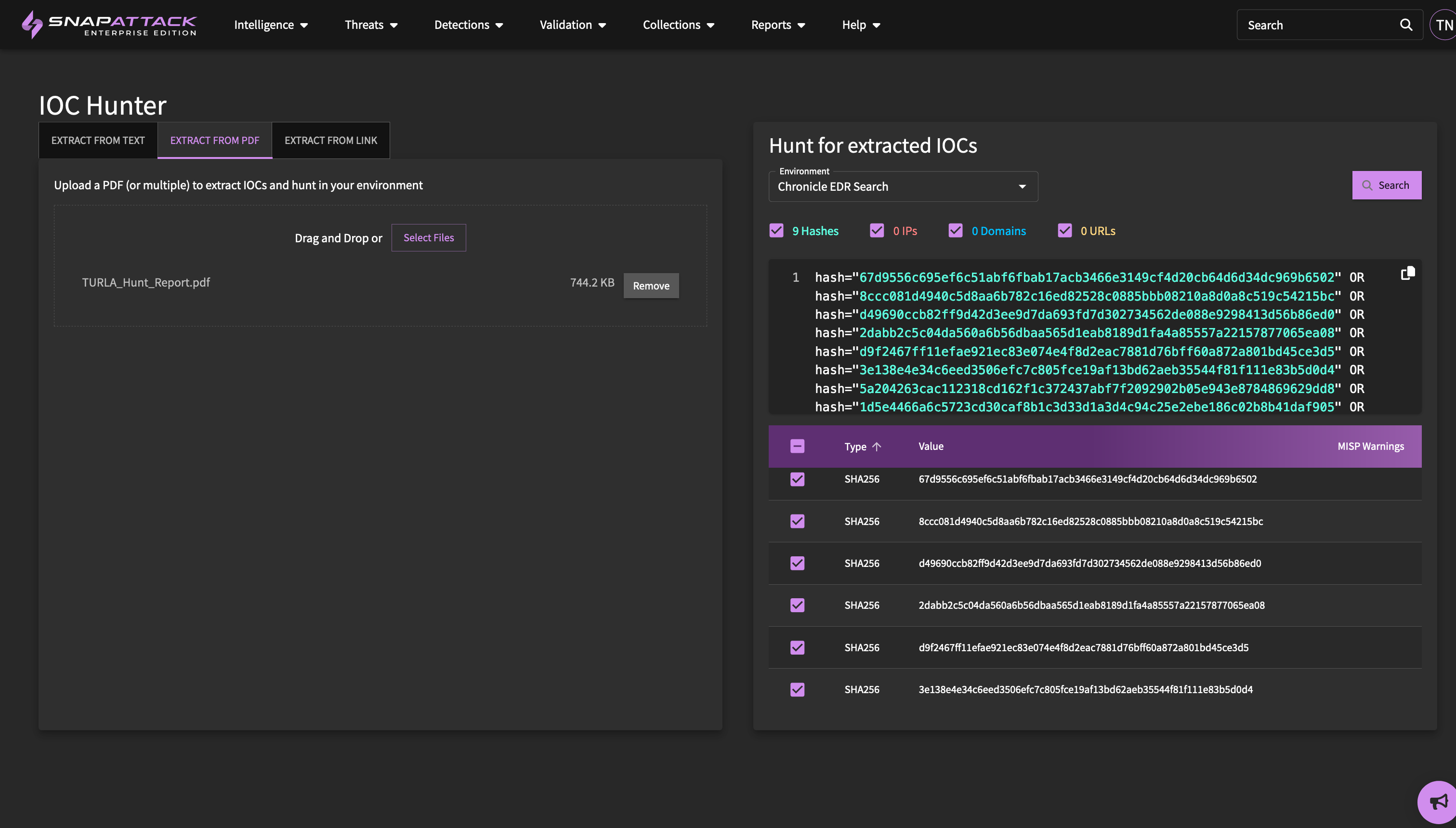
- Updated the IOC hunter to allow parsing PDFs and webpages, in addition to text. Also added the ability to extract details from PDFs for the quick add intelligence feature.
- Introduced the grid view for collections. Added some quality of life features to remember a user's preference for grid vs. card view, which should carry through across pages.
- Added the ability for users to un-deploy detections in bulk.
- Updated the upload threat capture interface to make it easier to find threats uploaded via the CapAttack API.
- Fixed a bug where labelling an attack by time would cause it to appear at 0 seconds on the timeline.
2023.03.06
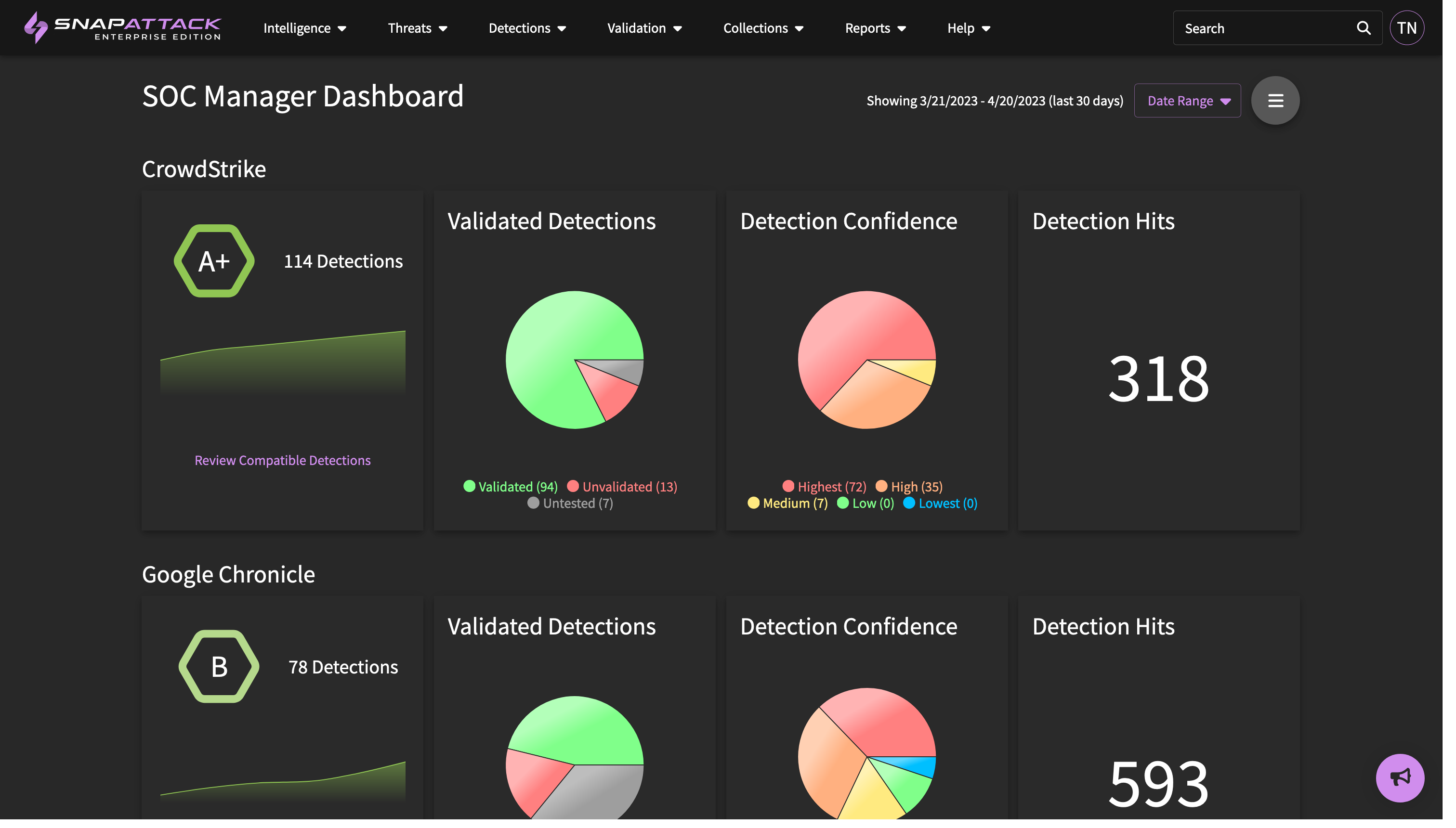
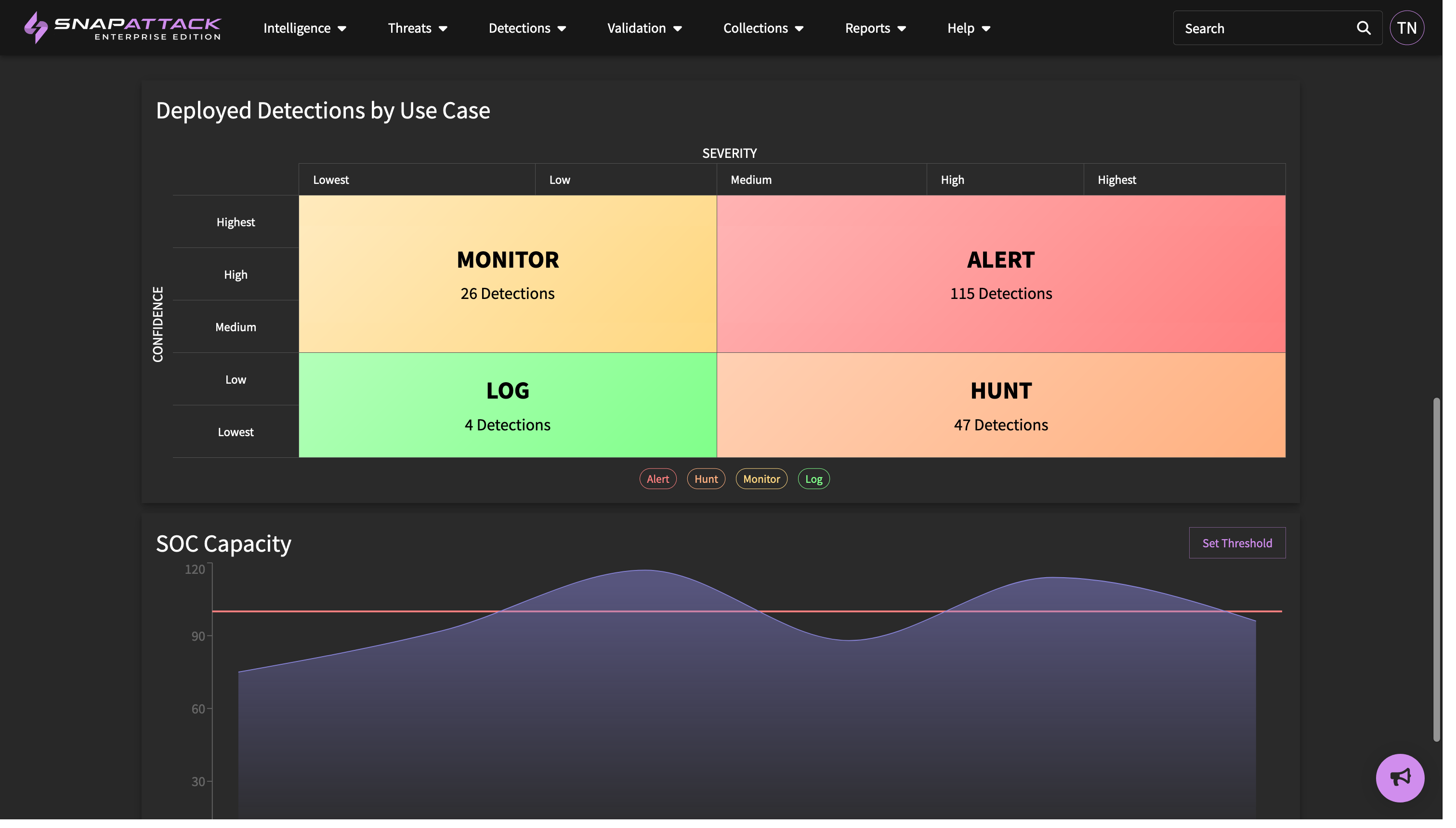
- SOC Manager Dashboard: introduced the SOC manager dashboard, which can be found under the reports tab in the header. This dashboard displays the health of configured integrations - including number of deployed detections, their validation status, confidence, and number of detection hits over the time period. It shows the deployed detections by use case - such as being used for alerts or hunt queries - as well as a SOC capacity chart. The SOC manager defines a threshold of the number of alerts the team can triage or respond to, and SnapAttack tracks this in relation to the number of alerts generated. Too many alerts and incidents can slip through the cracks; too few alerts means more detections could be deployed to increase coverage without impacting team performance. The date range for this report can be adjusted, and it can also be exported to PDF.
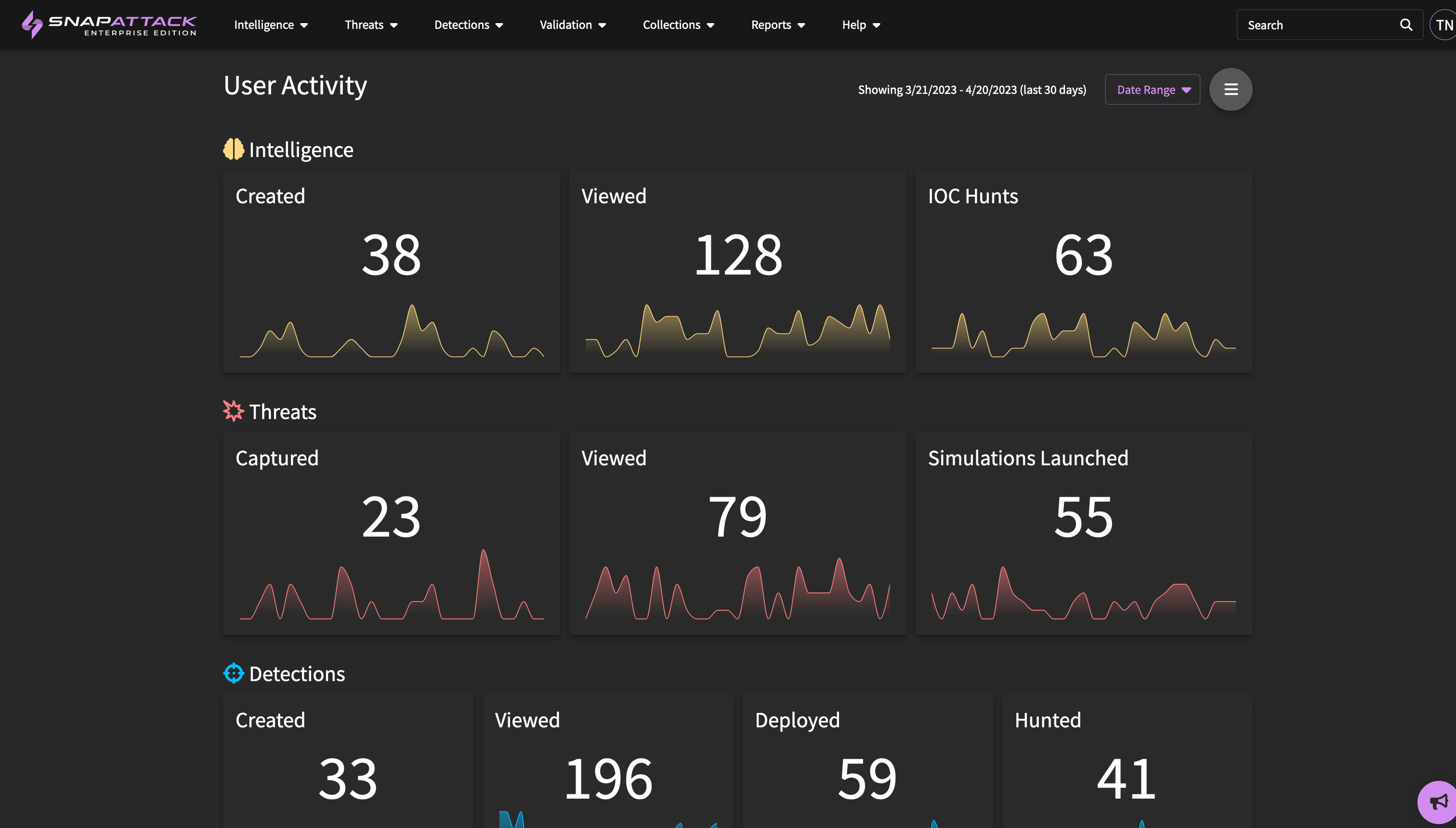
- User Activity Dashboard: introduced the user activity dashboard, which also can be found under the reports tab in the header. This dashboard displays your organization's activity in the platform, such as reviewing or creating intelligence, threats, or detections, executing attack simulations, deploying detections, and performing IOC or regular threat hunts.
- Added the ability for a user to cancel attack plans that are in-progress, or re-run attack plans that have been completed.
- Introduced the ability for users to add recommended detections to a collection or export recommended detections from the threat page.
- Added a new filter to the threat feed to allow filtering threats by their highest confidence recommended detection.
2023.03.04, 2023.03.05 Hotfix
- Fixed a bug where old or duplicate threats were linked to attack simulation modules.
- Fixed a bug where the delete button for collections was not always visible.
2023.03.03 Major Release
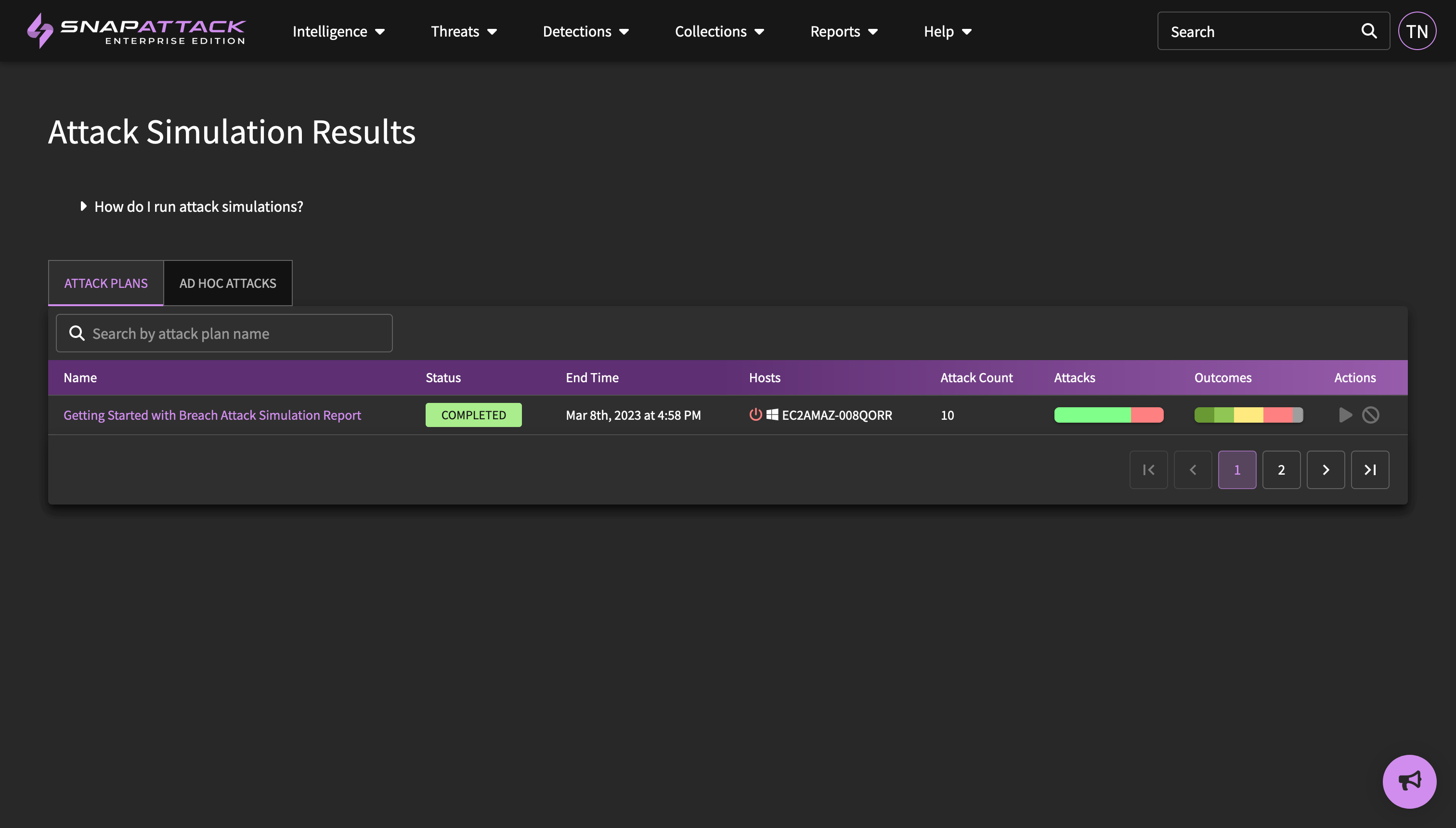
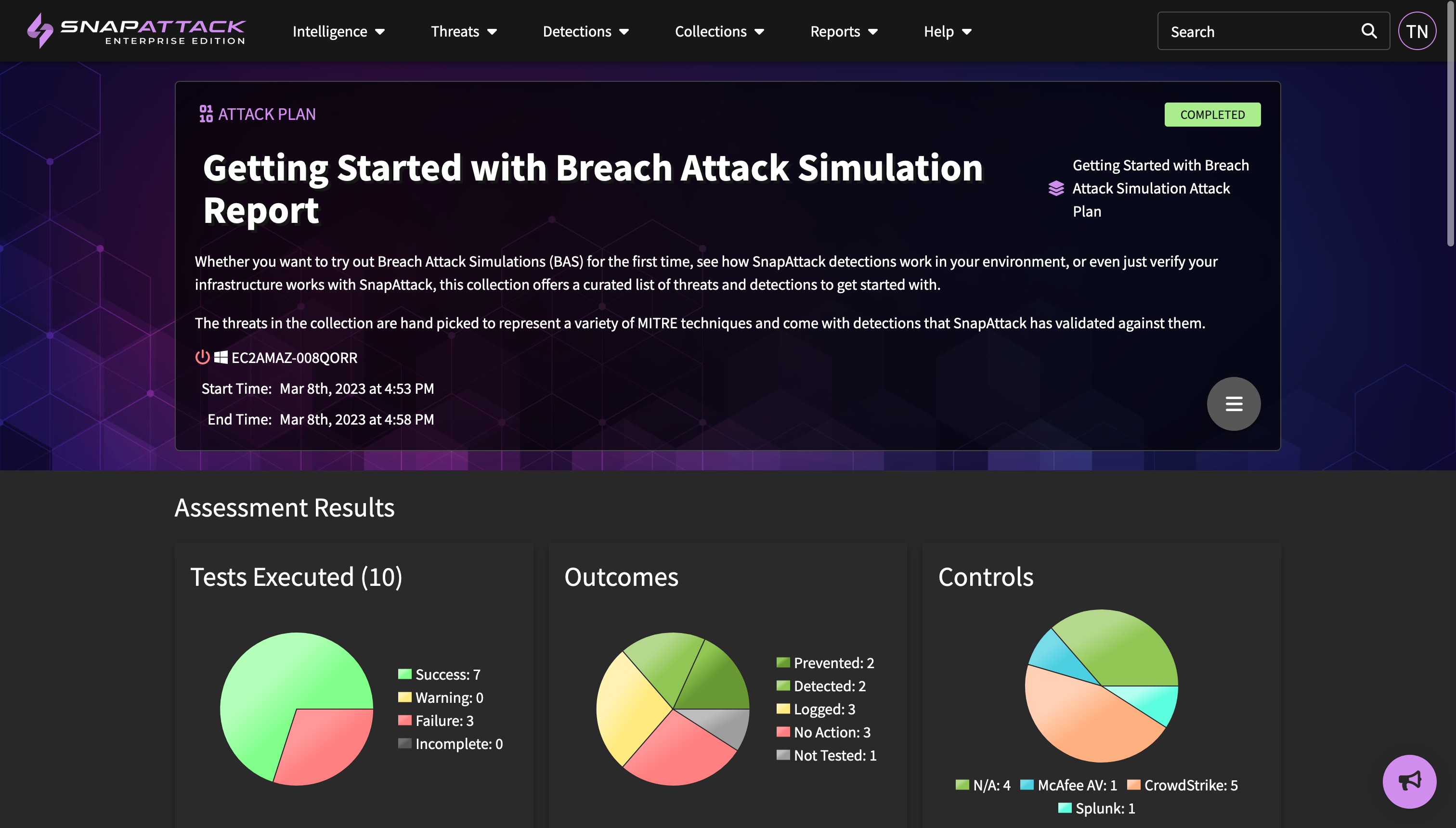
- Attack Simulations: a preview of our upcoming attack simulations has been released to enterprise customers in our beta program. This includes the ability to create and execute groupings of automated attack techniques as part of an attack plan, manual tracking of defensive outcomes (with automation coming soon for specific integrations), manual test case creation (to document red team activity or difficult to automate tests), and a report page with exportable PDF to document the test outcomes. Contact your customer success representative if you would like early access to this feature.
- Grid View: implemented a data dense way to view intelligence, detections, threats, and collections on the search page. This can be changed by going to the menu button and selecting "Display as Grid". Columns can be sorted, re-ordered, or toggled on/off. Bulk actions are available by selecting the checkbox next to specific items in the grid view. For performance reasons, up to 1,000 items may be displayed on the grid at one time. The grid view will be enabled for other areas of the site, including within collections, in a future release.
- Multiple small changes to the translation configuration page to improve overall user experience.
- Fixed a bug where certain filters would not apply on the MITRE ATT&CK matrix page.
2023.03.02, 2023.03.01 Hotfix
- General bugfixes and stability improvements to enhance the user's experience.
2023.02.03
- Released a new attack simulation agent. This is a complete re-write and has feature parity with the prior agent, but is better able to support our roadmapped items for attack simulations. The primary new benefit for this agent is ability to perform attack validations and better understand if the attack succeeded or failed on the endpoint.
- Improved the IOC hunter to display the query for the integration. Made the IOC hunter preferred integration aware.
- Improvements to SentinelOne and Microsoft Sentinel integrations. Expanded support for additional Windows event logs for Google Chronicle.
- Fixed a bug where captured threats against cloud targets (e.g., AWS, Azure) would not correctly extract logs upon upload.
2023.02.02 Hotfix
- Fixed a bug when checking out certain VMs from the attack range.
- Fixed a bug where reference URLs were not visible on intelligence and other objects.
- Fixed a bug where labelled attack descriptions were not properly being set.
2023.02.01
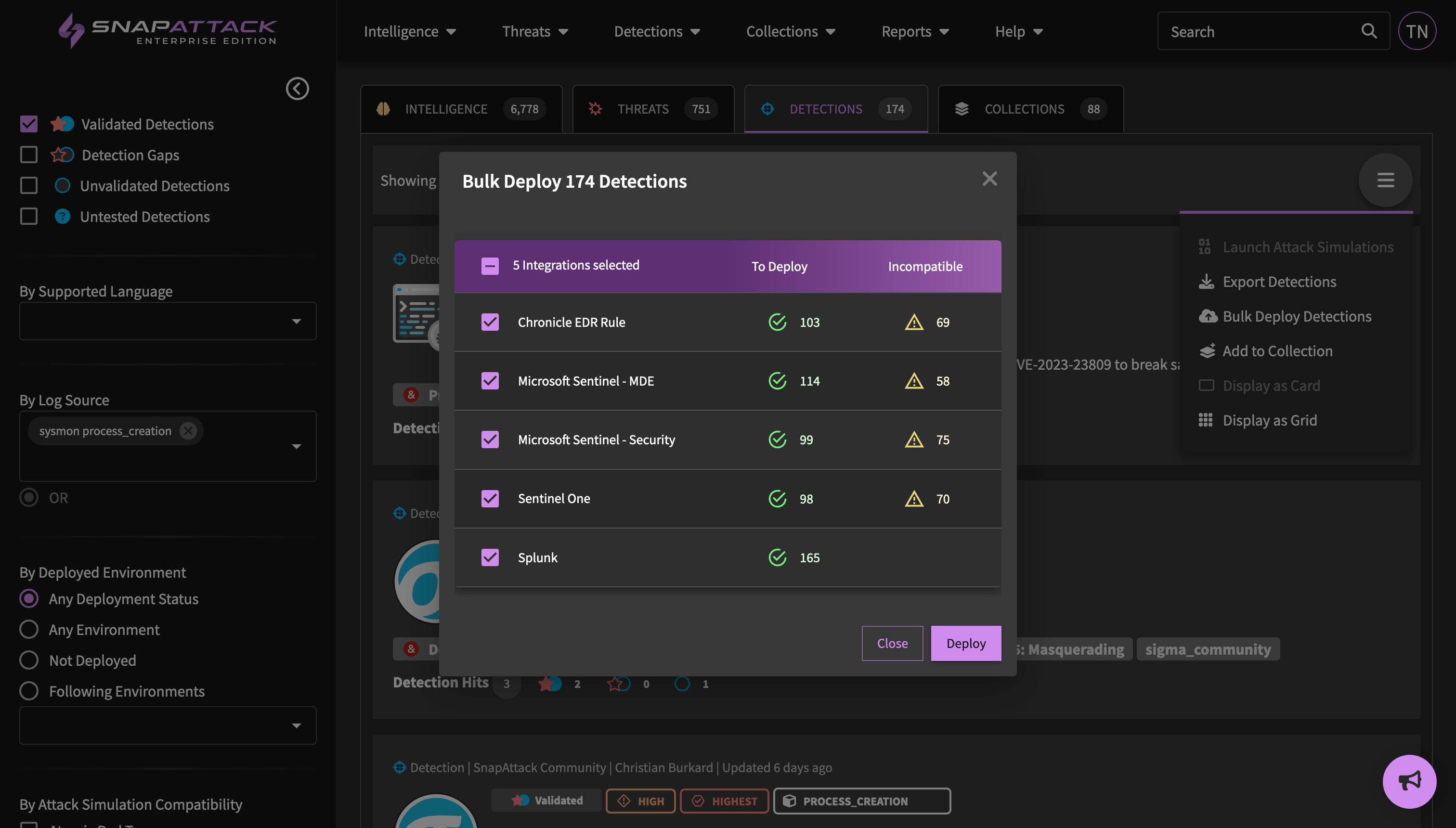
- Improved the interface for bulk deploying detections, allowing a user to target one or more specific configured integrations. Users will also see warnings if there are incompatible detections that will not be deployed.
- Added the ability to view and manage detection revision history from the detection page, as well as the ability to revert to a previous version of the detection.
- Improved IOC extraction for sources with hundreds of indicators by deferring MISP warning lookups. Warnings will be displayed after the intelligence object has been created.
- Reduced loading times for specific user and organization API endpoints. This will be most noticeable when opening additional pages/tabs after the initial login.
- Added highlighting to the IOC hunter to show matches for indicators in the source text.
- Added rate limiting to certain API endpoints. Users will see an HTTP 429 error code with description of the rate limit. Rate limits may be adjusted in the future.
- Updated Kali Linux image for the on-demand threat library. Installed pip3 which was previously missing from the base image.
- Sorted the intelligence feed by creation date for the reference, rather than last updated date. This means that recently added content for older intelligence will be displayed further back in the feed results. Additional sorting filters will be added to the feed in the next release.
- Multiple improvements to detection compilations for SentinelOne and Google Chronicle. For Chronicle, the UDM syntax requires the use of Conjunctive Normal Form (CNF), which limits the detections that can be translated to it. This does not impact deploying Chronicle rules which uses a different syntax. UDM search best practices can be found https://cloud.google.com/chronicle/docs/investigation/udm-search-best-practices.
- Removed user-defined, custom tags in favor of structured tags around MITRE ATT&CK techniques, threat actors, software (malware/tools), and vulnerabilities. Content will be centered around these tags in an upcoming release.
Deprecation Notice: Custom Tags
User-defined or custom tags are being deprecated as of this release. Existing tags will still be visible in the system, but will be removed in a future release. Organizations should begin using collections to group similar content where custom tags were previously used. Alternatively, the description fields for content are all full-text searchable and those attributes can be included in the content's description.
2023.01.02, 2023.01.03 Hotfix
- Fixed a bug where certain detections could not be loaded in the detection builder.
- Improved slow performance for bulk detection export.
- Fixed a bug where detections could not be loaded on mobile browsers.
2023.01.01 Major Release
- Indicators of Compromise: Added support for IOCs across the application. IOCs and CVE tags are now automatically extracted from threat intelligence objects, and intelligence can be filtered to find objects that contain IOCs. Users can perform a one-click hunt to search for IOCs in their configured integrations. IOCs are enriched to remove false positives and checked against MISP warning lists.
- IOC Hunter: Created a new page where intelligence analysts can quickly paste text blocks to have IOCs extracted, enriched, and have queries generated for one-click hunts in their configured integrations.
- Default Language Preference: Updated the user's preference under the settings menu to allow users to configure a default language preference. This will show translated detections in this language across the detection pages and the detection builder. Additional components will use this preference in the future.
- Improved query translations for SentinelOne and Google Chronicle.
- Allow multiple integrations for the same language within an organization, as well as the ability to give a custom name to integrations.
2022.12.02
- General bugfixes and stability improvements to enhance the user's experience.
2022.12.01
- Updated the deployment widgets on the threat and detection page to allow deployments to be managed at a more granular (per integration) level.
- Reintroduced the ability to copy a detection when a user does not have edit permissions. This can be found in the actions menu on the detection page.
- Improved the recommended detections widget, including being able to preview if a detection is deployed, not deployed, or not compatible with configured integrations at a glance, and being able to deploy from the widget itself rather than the detection page.
- Added the ability to highlight recommended detections on the threat page, including a filter option to see only recommended detections.
- Improved compilations for USM Anywhere and CrowdStrike IOA detections.
- Added the ability to export detection within a collection.
- CapAttack: added the ability to update libraries and reinstall when needed.
- Upgraded MITRE ATT&CK to v12. This adds 2 new techniques, 15 new sub-techniques, 1 group (actor), and 38 pieces of software, and makes updates to several others. You can read the full ATT&CK release notes here. Campaigns will be introduced into the platform in the coming weeks.
2022.11.02, 2022.11.03 Hotfix
- Fixed a bug where adding items to a collection would overwrite the collection contents.
- Fixed minor issues related to multi-factor authentication.
- Removed navigation links for upcoming features that were feature flagged from regular users.
2022.11.01 Major Release
- Search: Most users come to SnapAttack to learn about a specific threat. We've replaced the homepage with a search bar, encouraging users to find
- Filtering: Made several improvements to the filtering, including styling changes to bring it into the left side drawer on the page. This unifies the filter across the feed, threat, and ATT&CK matrix pages, and sets the early stage for the site-wide filtering that will also apply to pages such as collections and reports. Re-ordered filters to bring the most commonly used filters to the top.
- Multi-Factor Authentication: All SnapAttack accounts can now be secured by MFA. Enterprise customers have the option of requiring MFA for all users in their organization. Single Sign-On is also configurable with OpenID Connect. SAML support will be enabled in the next major release.
- Improved bulk actions on collections and feed pages.
- Improved user and organization management interfaces.
- Made improvements to SentinelOne, CrowdStrike, AlienVault USM Anywhere, and Google Chronicle integrations.
- Fixed a bug where training/isolation mode showed community content.
2022.10.04 - 2022.10.07 Hotfix
- Minor improvements related to the recommended detections panel and feedback widget.
- Fixed a bug that prevented configuring integrations with custom fields.
2022.10.03
- Improved our Google Chronicle integration to be able to deploy and sync detection rules from SnapAttack to a customer's configured Chronicle environment.
- Added the ability to manually sync detections to configured integrations. Detections may be delayed up to 15 minutes after being deployed if the integration architecture polls SnapAttack for updates instead of allowing SnapAttack to push directly to the integration. This feature forces a sync, which can improve the experience for integrations such as Chronicle, Microsoft Sentinel, and SentinelOne.
- Added a recommended detection panel to the threats page when there are prioritized detections for the threat. This panel will be coming soon to collections and other pages across the application.
- Significantly improved performance loading the detections and threats pages of the application.
- Updated the feedback widget to allow community edition users to be able to request a demo from the application, and allow enterprise edition users the ability to report an active incident in order to gain immediate assistance.
- Added SSO support for enterprise customers.
2022.10.02 Hotfix
- Fixed a bug that prevented users from exporting detections when certain filters were applied.
- Fixed a bug that prevented Attack Range On-Demand captures from being fetched from the host.
2022.10.01
- Improved search speed and flexibility. Users can now use a DSL to query specific fields. Advanced search examples can be found in the searching and filtering documentation.
- Opened the Attack Range On-Demand virtual machines to Internet. Care should be taken when executing malware if you do not want it connecting to C2 servers.
- Added the ability to use the 'Local Threat Capture' API scope in CapAttack to upload captured threats to SnapAttack, and a new interface to be able to attach those previously uploaded threat captures.
- Content Highlights: Created collections around Cobalt Strike and MITRE CTID Micro Emulation Plans, and the Microsoft NotProxyLogon CVEs, among other content updates.
2022.09.04 Hotfix
- Fixed issues with bulk exporting detections and bulk launching attack simulations with the updated feed.
- Improved performance of the detection recompilation task when field mappings are updated or changed.
2022.09.03
- Improved prioritization for background task queues to ensure workers are available for higher priority, short running asynchronous tasks.
- Improved the display of global confidence and severity ratings for detections. By default, these metrics are calculated across our customer base. Subscribers can override these values and manage their own confidence and severity levels.
- Improved search speed for finding content within the application.
2022.09.02 Hotfix
- Fixed a bug where the edit threat page was not accessible.
2022.09.01 Major Release
- Detection Dashboard: Enterprise customers can track their threat preparedness, deployed detections, and MITRE ATT&CK coverage from a single pane of glass.
- Collections UI Improvements: Several improvements have been made to collections, including a new user interface to bulk manage content items in a collection, and the ability to bulk deploy detections or bulk simulate attacks. Collections is a featureset that will continue to see improvements and refinement.
- REST API: A new API key scope has been added for the REST endpoint, and REST API documentation has been made available to customers. This can be used to automate tasks such as downloading or deploying detections.
- Improved the auto-calculated confidence scores by testing against known benign data sets, and improved the ability to calculate detection confidence based on customer provided data.
- Fixed a bug where tagged ATT&CK sub-techniques did not validate up the chain.
- General bugfixes and stability improvements to enhance the user's experience.
2022.08.06, 2022.08.05 Hotfix
- Fixed a bug where unauthenticated users may not be able to access the forgot/reset password pages.
- Fixed a bug where newly created detection hits were missing metadata that prevented the markers endpoint from returning.
- Fixed a bug with severity displaying as "Unknown" instead of falling back to the global severity.
2022.08.04
- Added severity data for labeled attacks and detection hits to process graph.
- Added multiple security enhancements to follow industry best practices around Content Security Policy (CSP), HTTP Strict Transport Security (HSTS), and other HTTP headers. Lowered thresholds for user inactivity timeout and account lockouts. Disabled support for weak SSL/TLS ciphers and protocols at the expense of reduced compatibility for legacy browsers.
2022.08.03
- Added additional encoding support for UTF-16LE query parameters for 1-click hunting with Microsoft Defender.
- Fixed a bug where search results returned the incorrect counts.
2022.08.02 Hotfix
- Fixed an issue with entitlements and how content organizations were displayed to users.
- Fixed a crash on the dashboard that prevented the application from loading for users who had not specified a preferred organization.
2022.08.01 Major Release
- Attack Range On-Demand: Enterprise customers now have the ability to spin up attacker and victim machines directly in the platform. This can be found in the navigation under "Threats" → "Capture a New Threat".
- Severity: Detections and labeled attacks can now have a severity assigned to them. Default severities will be assigned based on their MITRE ATT&CK mappings. Like confidence scores, severity can be overridden a the organization level. You can sort and filter content by severity.
- Collections: Collections are a flexible way to group one or more related intelligence, threats, or detections. Initial collections have been created around threat actors from Mandiant Threat Intelligence. Going forward, content in SnapAttack will be aligned to collections where applicable. Collections will be have different types, such as threat actor, ATT&CK technique, malware/software, and vulnerability. For example, if a user wanted to see how protected they are against APT41, T1055: Process Injection, mimikatz, or CVE-2021-44228 (log4j), they could navigate to the collection and find intelligence, captured threats, simulatable attacks, and detections. Users can also create private collections to track hunt plans, purple team exercises, or any other use case they see fit.
- Mandiant Threat Intelligence: With our recently announced partnership with Mandiant, we have added access to Mandiant Threat Intelligence to mutual subscribers. This allows subscribers to see captured threats (including simulated attacks with Mandiant Security Validation) and SnapAttack detections around specific threat actors and intelligence reports. Users who would like to learn more about Mandiant Threat Intelligence can try out the free version from Mandiant.
- Detection Field Reference: Creating detections can be challenging when you're not sure the logsources and fields available to you. We've published a detection field reference which provides the fields, types and sample values for each log source and event code supported by SnapAttack. This list will be updated and maintained over time. You can still use custom fields when creating detections; they just will not autocomplete in the Detection IDE.
2022.07.06 Hotfix
- Fixed a routing issue between the statistics and tags backend microservices.
2022.07.05
- Enabled the statistics service to begin collecting historical data for dashboards and reporting purposes. This will allow users to answer questions like "how many detections have I deployed in the last 30 days", "how has my MITRE ATT&Ck coverage improved this quarter", or "what is the time between when a threat/vulnerability was discovered to when we had detections deployed to defend against it"?
2022.07.04
- Created initial written platform documentation (what you're reading now).
- Renamed "Attack Sessions" to "Threats" and "Analytics" to "Detections" in the platform to better reflect our users and use cases (threat researchers, threat hunters, detection engineers, etc).
- CapAttack: improved auto updating, versioning, and the ability to merge configuration changes.
- Added Okta support for captured threats and detections, and 16 captured threats for subscription users based on recent .intelligence and the dorothy framework.
- Added support for Secureworks Taegis XDR
- Improved backend support for Microsoft Defender for Endpoint (MDE) and Microsoft Sentinel.
- General bugfixes and stability improvements to enhance the user's experience.